Apple just released iOS 12.3 dev beta 2 today, Monday, April 8, which follows the first iOS 12.3 beta by twelve days. This update introduces new Japanese Date & Time features as well as updates to Wallet transactions. As a whole, iOS 12.3 introduces Apple's previously announced Apple TV Channels, premium monthly subscriptions with content you can watch right in the TV app across Apple products.
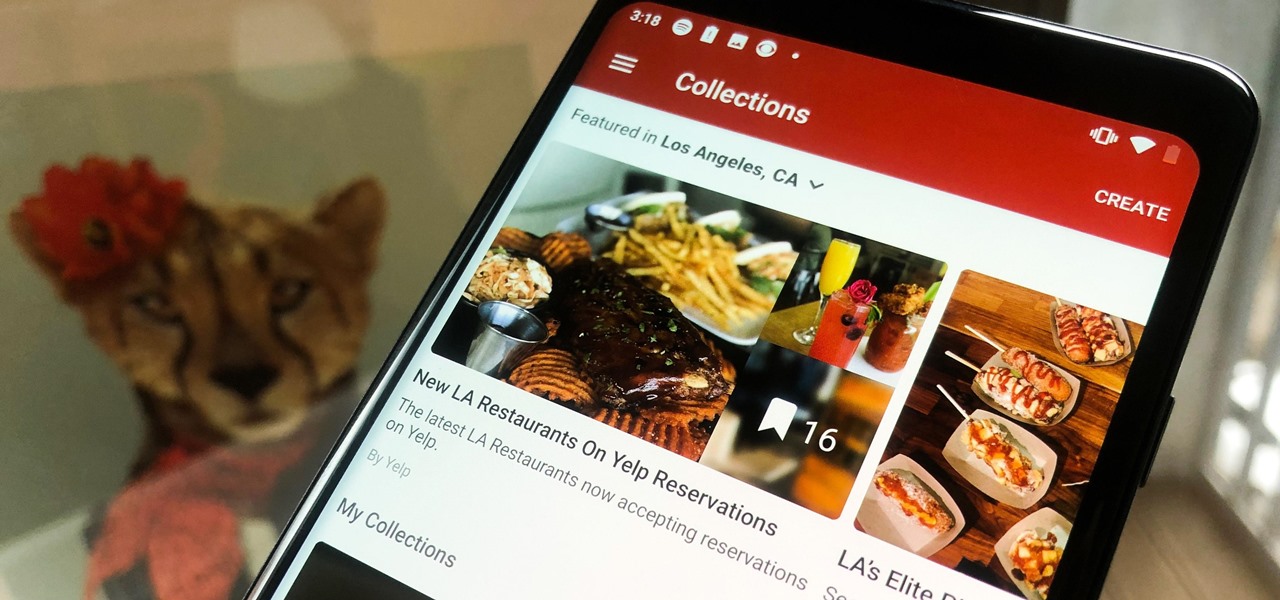
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Public software testers can now run the fourth iOS 12.1.3 beta. Apple seeded this update to testers on Thursday, Jan. 10. Just like with beta 3, public beta 4 includes two resolved issues — a VoiceOver fix for ECG and Irregular Heart Rate notifications, as well as audio improvements for iPad Pros.

Apple pushed out iOS 12.1.3 developer beta 2 to all developers on Wednesday, Dec. 19. It's an interesting and mysterious update, as it follows the sudden release of iOS 12.1.2. That software only had one beta version before its stable release, which would explain why the iOS 12.1.3 dev beta skipped version 1 and went straight to version 2 since it's basically a continuation of the first iOS 12.1.2 beta.

After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time to announce new devices that would attract a different crowd of users. Meet the Pixel 3a and 3a XL.

Who doesn't love a refresh? Samsung's upcoming One UI makes it easier to use your device with one hand and adds a fresh coat of paint to the formally "Samsung Experience" skin. While you're probably looking forward to installing One UI on your phone, not all Galaxies are equal — your device could be one of the first to receive the update, or it could never see One UI at all.

Just six days after the release of dev beta 3, developers now have their hands on the fourth iOS 12.1 beta. While Apple has recently followed a lengthy and inconsistent release schedule with its beta software, the company seems to want to keep testers happy with 12.1 — beta 4 might have come less than the standard seven days after beta 3, but at least it's here quickly.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

Apple has finally released iOS 12 for everyone to enjoy, and there are plenty of cool features to go around. Perhaps the coolest feature, at least, for those of us with an iPhone X, is the return of an oft-used gesture we loved on other model iPhones.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

You've been able to install app updates automatically for some time now, but there was no way to install new system updates on your iPhone automatically. To get a new iOS version on your device, you'd go into the settings, then download the update. It would then either install right away or give you the option to install at nighttime. This whole process is easier in iOS 12.

With PUBG and Fortnite dominating the gaming scene, other companies are making royale-themed games to get in on the trend. Futureplay is no different, as they've soft launched Battlelands Royale in Finland, Poland and Ukraine to iron out bugs before its worldwide debut. If you don't live in one of those countries, you can try this game right now with a quick workaround.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Apple released the sixth beta for iOS 11.3 on Friday, March 16. It comes as a surprise, considering the company released the fifth beta only four days ago — an unexpectedly short time between updates. This new beta, much like beta 5, appears to bring minor patches and bug fixes.

Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Apple released the third developer beta for iOS 11.2.5 on Wednesday, Jan. 3, and public beta testers got in on the action the following day. The update comes two full weeks after the release of the second beta, marking an extended update period of Apple. The second beta mostly brought under the hood improvements to 11.2.5.

Back in November, Essential opened the Android Oreo Beta Program for all users of their PH-1 flagship. We even wrote up a full guide on how to install the beta, if you're interested. They followed the Oreo beta with a Reddit AMA, where they mentioned the second beta software would arrive very soon. That update has just gone live, so you can grab it right now in a few easy steps.

The same approach to augmented reality that some companies use to improve workforce productivity could also make it easier for car owners to operate and maintain their vehicles.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

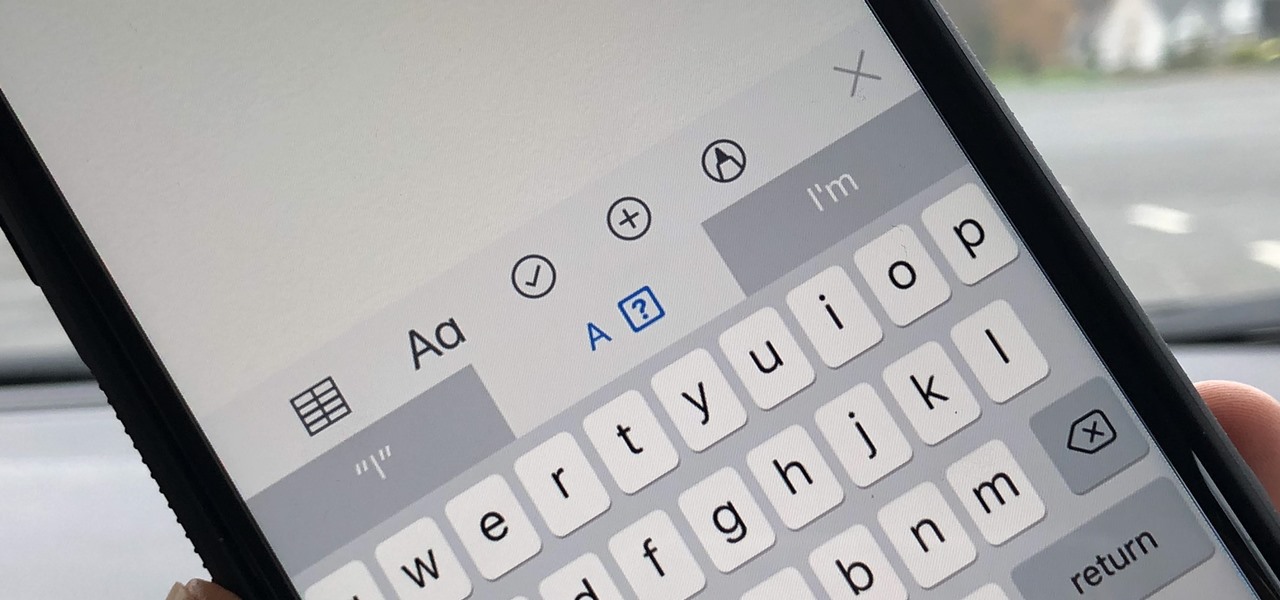
There's an annoying bug in Apple's latest operating system for iPhone, iOS 11, that autocorrects the lowercase letter "i" by itself (which usually turns into a capital "I" pronoun) into a capital "A" followed by a strange question mark in a box "[?]" symbol. There is now an official patch for this bug, as well as a workaround fix if you don't want to update yet.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Zenko Games makes no apologies for its influences. In fact, they cite them explicitly in their own promotional materials for Diamonst AR.

Building virtual portals are popular practice for developers to demonstrate the "wow" factor of augmented reality.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

One of the best features in Super Mario Run is the ability to unlock other notable characters from the classic series on iPhone or Android. Each playable character in Super Mario Run has a slightly different skill set — be it speed or jumping — which can come in handy in certain maps or races.

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

With the release of Apple's ARKit comes endless possibilities for education and learning. One of those possibilities is an AR rotating model of our solar system in your room, another is using AR to instantly know the nutritional value of food items.

Our universe has never been closer thanks to Apple's ARKit. YouTube user Jenil Kansara has been playing around with ARKit features and created a solar system in his room.

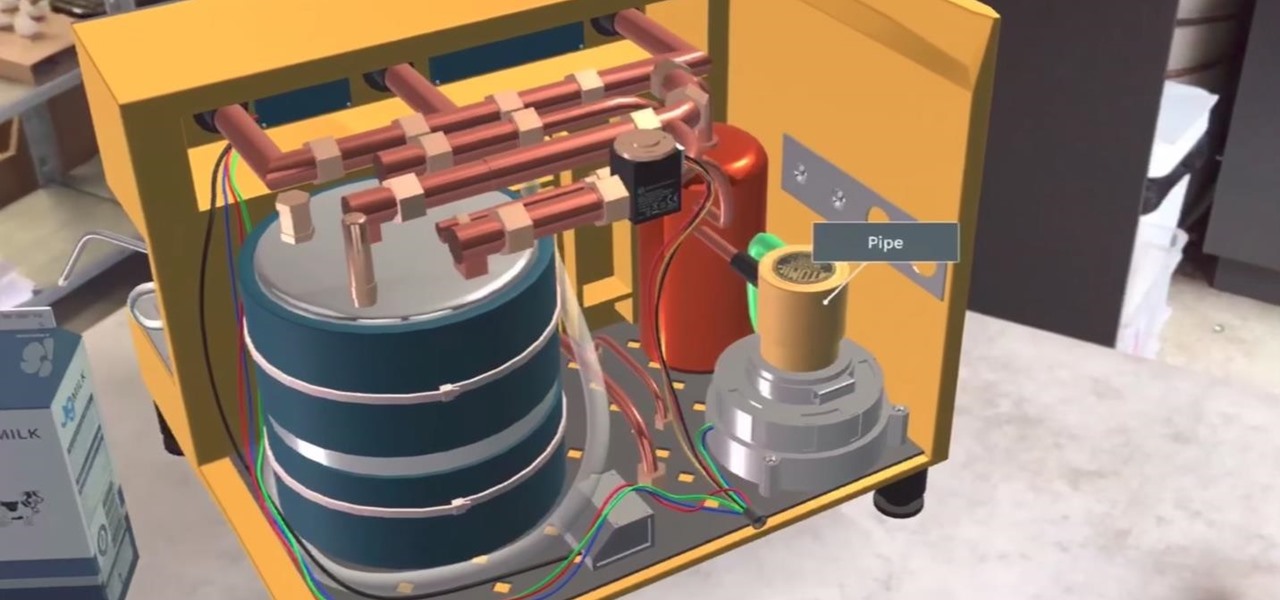
JigSpace, a company that uses 3D renderings to give instructions, showed off a fun new way to learn how things work using Apple's ARKit. The video released shows the anatomy of a range of things, including an espresso machine, an Archer Hb Plus chair, and the manual transmission of a car. Not to mention, they also used ARKit to show a 3D how-to of removing an iPhone's SIM card.

Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

In a recent series of tweets, investor and entrepreneur (and NR50 member) Amitt Mahajan summarized the challenges and opportunities for iOS developers looking to leverage Apple's ARKit for augmented reality experiences.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Tired of all those people tagging you in weird stuff on Instagram? Well, there's an easy way to prevent people from ever tagging you in one of those silly posts again. It's simple, too. It only takes a couple minutes of your time, but will probably save you from years of embarrassment (or however tagged photos make you feel).

If I told you to follow as many users as you could possibly follow, in order to get more Instagram followers, that may seem counterintuitive, right? If I told you I'm trying to brainwash/annoy you with how many times I could possibly say versions of the word "follow" in an opening sentence, that would seem weird, too.

The latest trend in smartphone design is all about the display. Manufacturers want larger screens with smaller bezels. The rumors are heating up about Google's next big release, the Pixel 2, and with that, we may have a clue that shows us Google is hopping on the display train.