First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Hey guy's, hope everything's going well! Here's a snippet of a few cool things and the latest news on Minecraft.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Greetings my fellow hackers.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

This video will show you how to easily find out what your IP address is. In your windows computer, you should go to the start icon and find a button which says "Run". After clicking on this button, type in "cmd" and a black box will appear. In this black box, you should then type in "ipconfig". In the data that appears after you type this in, you will see a section which says "IPv4". The numbers that follow this section is your IP address. Viewers might need to know their IP address for vario...

In this video from iPT2gGeec we learn how to control an iPhone from your computer. You need a jailbroken iPhone to do this and use a program called Veency. Open Cydia. Search for Veency. Install it. That is all you need to do with your iPhone.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

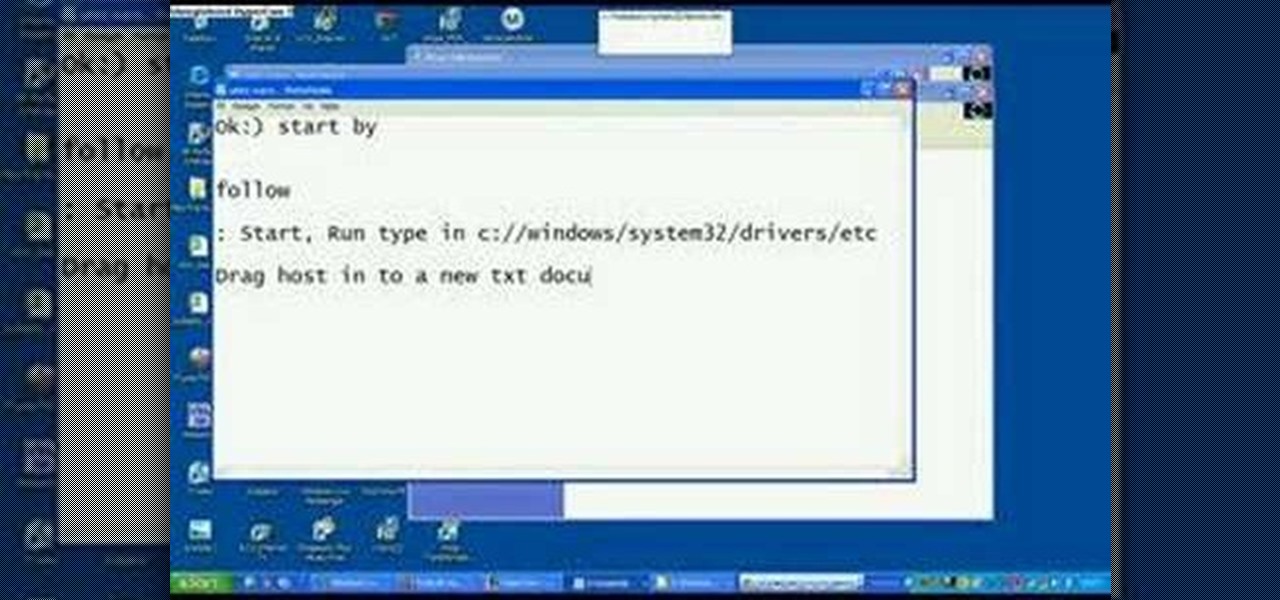
In this tutorial, we learn how to block a website. First, you will start by going to the start menu then go to "run". After this, type in "c://windows/system32.drivers/etc". After this, a new window will pop up on your screen. With this, you will drag the host into a text document. Then, type in the website that you want to block inside of this document. Once you are finished, type in the IP address of your computer next to that and save it. This will finish up the blocking of the website and...

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...

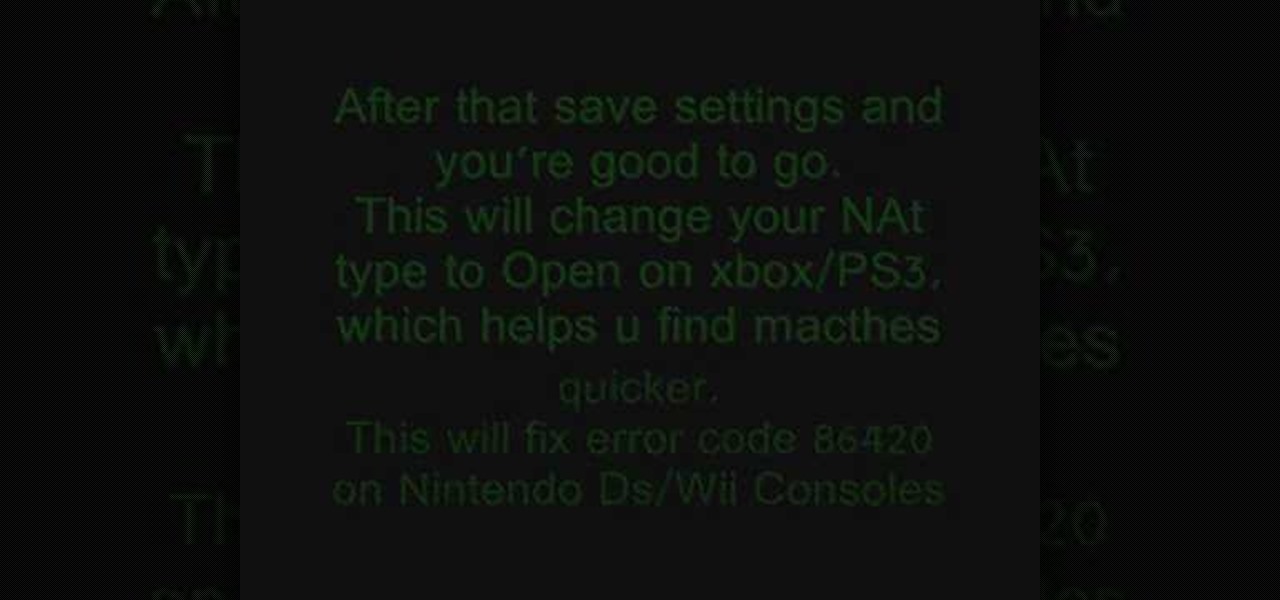
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

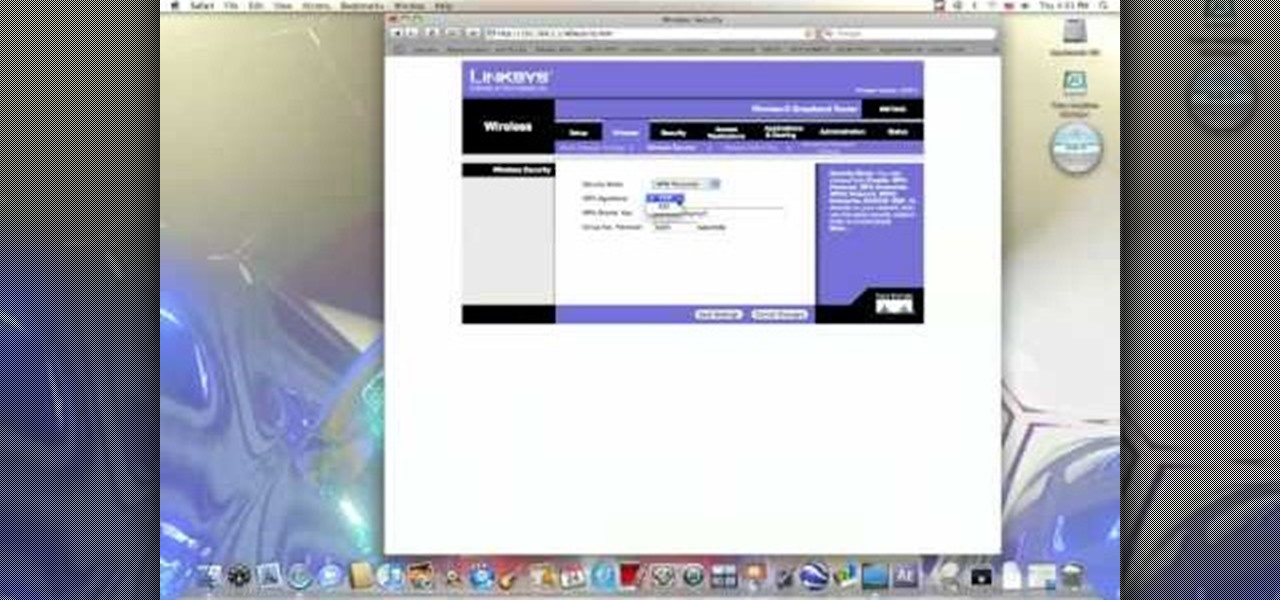
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

This tutorial will show you how to view your iPod or iPhone screen on your desktop. First of all, you need to have a jailbroken iPod for the applications necessary and secondly you will need Wi-Fi. You will need to download the application RealVNC for your desktop and Cydia for the jailbroken iPod or iPhone. Within Cydia you will search for the program Veency and go to the homepage. From there you will go into settings Veency. Now you have down everything on your iPod or iPhone. Now on your c...

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...