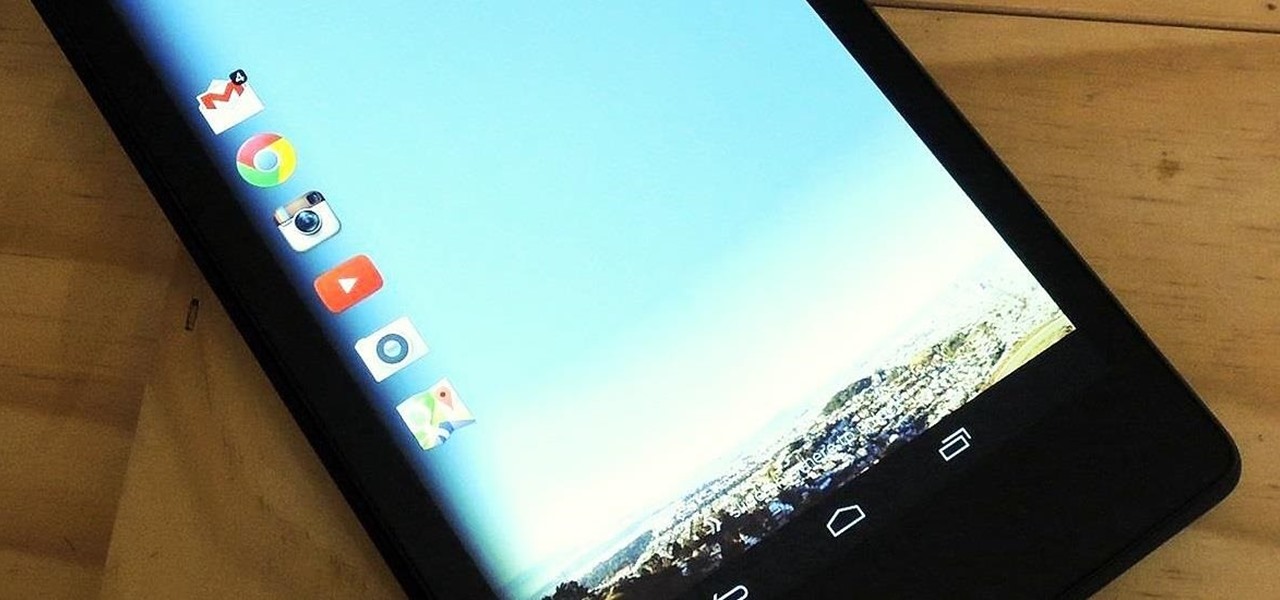
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Once when I was a kid, my dad used a glue trap to catch a mouse in our basement. The result was so awful for the mouse that my mom and I made him promise to never use that kind of trap again. Call me a softy, but I'm a firm believer that you don't have to kill pests to get rid of them.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does, which measures ambient temperature and humidity.

There is a substantial number of helpful tools at your disposal in Microsoft Word when it comes to writing; grammar check, word count, dictionary, thesaurus, and tons more. One tool that doesn't necessarily make itself obvious is testing your document's readability. With this built-in tool, you can not only check your spelling and grammar, but also the reading level of your document.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

Last year, Lytro released their first light field camera to help photographers have more control over focusing. This innovative and revolutionary camera allows users to change the depth of focus of a photograph after the picture is taken.

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

This is an awesome little science trick that has to be seen to be believed. Simply by emptying a bottle of "supercooled" water into a glass, you can watch it turn into ice right as your pour! It's no magic trick or chemical craziness—it's normal water and you can try it yourself right in your own home.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

You don’t need a camera to recreate a picture you see. Choose and object and with only a pen and pencil you can recreate that object as a sketch. Take your time, and choose somewhere quite where you can focus on your creation.

Buying a home is a big step so find out just what is involved when you are ready to bid for the house of your dreams. The whole process can be bit nerve-racking but as long as you stick with it you’ll be a home-owner in no time.

Need to figure out the area of a trapezoid for a household project? Even if you just want to sound smart, there is a simple formula that can be used every time you need to find the area of a trapezoid. Try the formula and see how good you are at geometry.

In this video we will learn about algebra SCIENTIFIC NOTATION and STANDARD FORM. Watch the above math video to learn how to change large numbers from standard form to scientific notation.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Bud Brown explains how to know when to use a voltage adapter in the Philippines. The United States and the Philippines have different voltage systems. In the United States 110 volts are used, and in the Philippines 220 volts are used. If you plug something from one system into the other system, it will not work correctly and may ruin your equipment. Consider that computers and phone chargers are equipped to handle both systems. Check the labels on your electrical equipment to determine if it ...

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

In bar routine work refers to high bar exercises that are close to the hips. Learn how to perform in bar routines from a professional coach in this gymnastics video tutorial.

If you're looking for an easy way to determine if a number is divisible by 3, then look no further than the divisibility rule. It's a shorthand way to tell if any given number can be divided by 3, without actually performing the division. Take the number in question, and if the sum off all the digits is divisible by 3, then the original number will be, too. There are four examples in this math video.

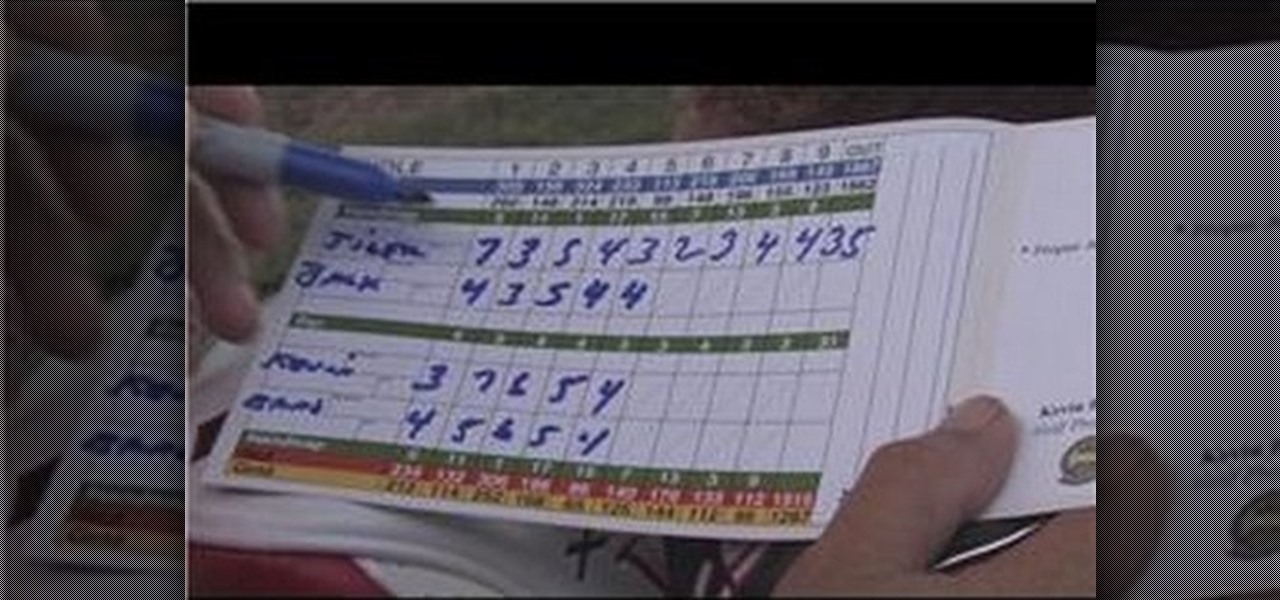
In this Sports video tutorial you will learn how to compute skins in a golf game. Kevin in this video illustrates how to calculate skins in your golf game. Skins are determined by the winner of each hole. A clear winner gets a skin for that hole. If there is no clear winner, the skin is carried over to the next hole. And the next clear winner of any hole will also get the skins for the previous holes where there was no clear winner. In the video Kevin wins the 1st hole and he gets the skin fo...

Use a simple mathematical formula to find the circumference of a circle. The circumference of a circle can be determined by using the formula 2 times pi times the circle's radius. Pi is equal to 3.14. If a circle's radius is 10 centimeters, first multiply pi times 2. Pi, or 3.14, times 2 is 6.28. The next step then is to multiply 6.28 times the circle's radius. Since the circle's radius is 10 centimeters, multiply it by 6.28. This gives you 60.28. 60.28 inches, then, is the circumference of t...

Let's try the Ken Burns effect. First Google photo story 3 and download the second link and install it. Now open photo story 3, select a new story and import pictures. Then click customize motion under preview and determine the start and end position. When done customizing, click next and select the music required with the desired genre and then save the story with a appropriate name. This will help in creating presentations, good memories as well as slide shows.

This video is pretty fast paced. There is no audio. It explains with video and text how to install Linux in a virtual drive from SUN. It includes the various needed steps including to First install the Linux or Windows CD into your CD/DVD Drive in your PC. Creating your new drive partition and then determining how much ram you want to add to the installation. It shows you how to work with Debian GNU/Linux and passwords and touches on installing Kubuntu.

This video is about a particular pool or snooker game shot technique called "Shooting or Going around the Angles." The presenter, with a alias name of 'Forcefollow', first describes a particular 9-ball pool game situation that would require this technique, using a computer generated picture image to show an overhead view of the pool table, with the pool balls in question placed at certain locations within the table and showing the various angle trajectories paths of the desired ball to be str...

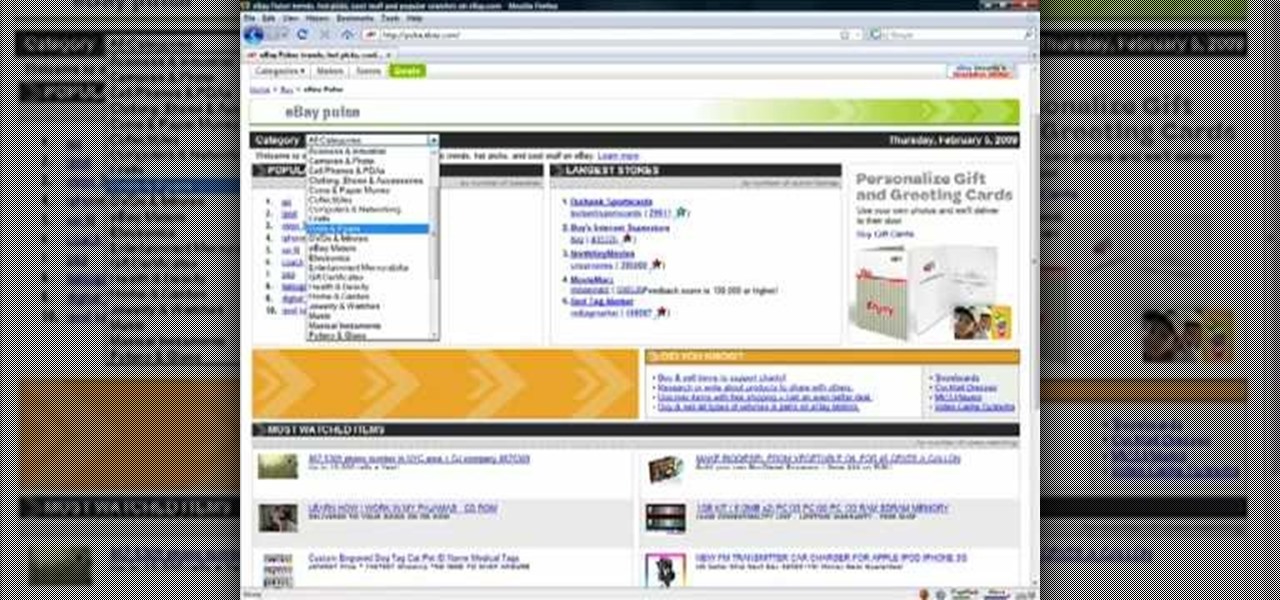
Do some niche research for your eBay affiliate site in these video tutorials, and see how to build an eBay affiliate partner site from scratch. Learn how to drill down into eBay Pulse and search for untapped niches. Finding a niche for your eBay affiliate site might seem daunting, but it's not. Also, learn about the Google Keyword tool and Wordtracker keyword tool along with a basic Google search to determine traffic levels and how easy it is to rank for a given keyword.

Before the calculator and even the abacus was invented, there was a little instrument called the human brain that we used to do math. Remember that? While most of us turn to our trusty Ti-84s to do calculus homework or whip out our cell phone calculators to determine how much we should tip at Johnny Rocket's, it can often be much faster to use our own brains, along with a piece of paper and pencil.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Picture this: You finally get that awesome angle, the perfect selfie. You can't wait to post it on your Instagram, except there's one problem — it looks a little flat and the colors just seem off. Maybe it's the lights? Or maybe your new smartphone camera isn't as good as you thought? How are your friends getting those beautiful photos they've been posting on social media?

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

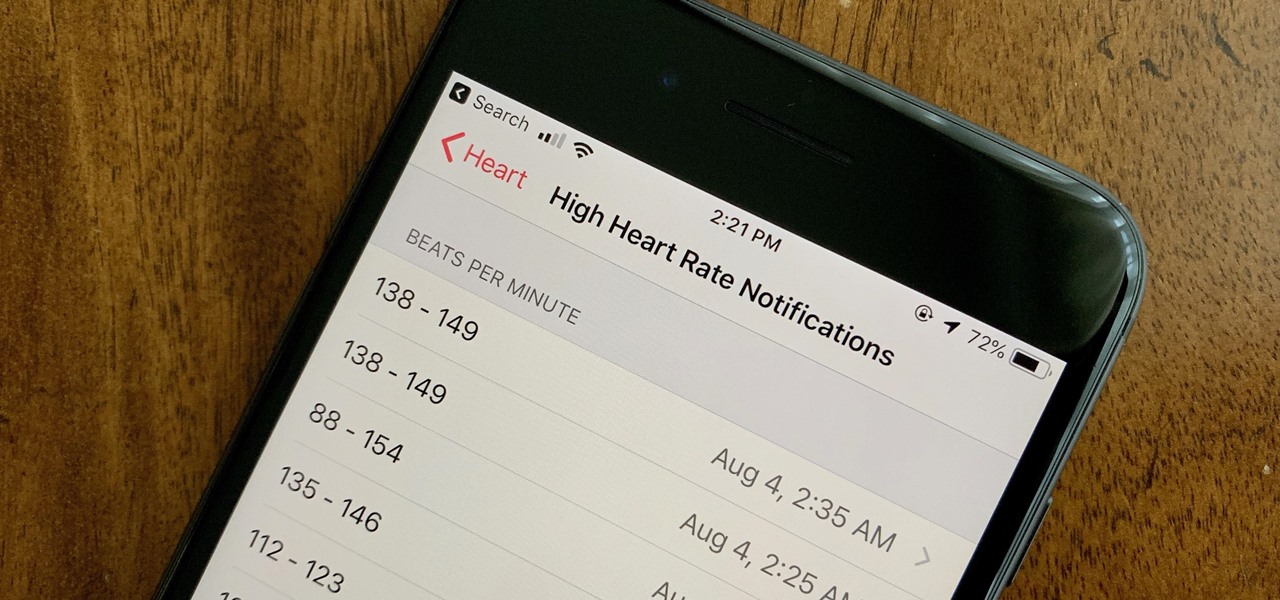
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

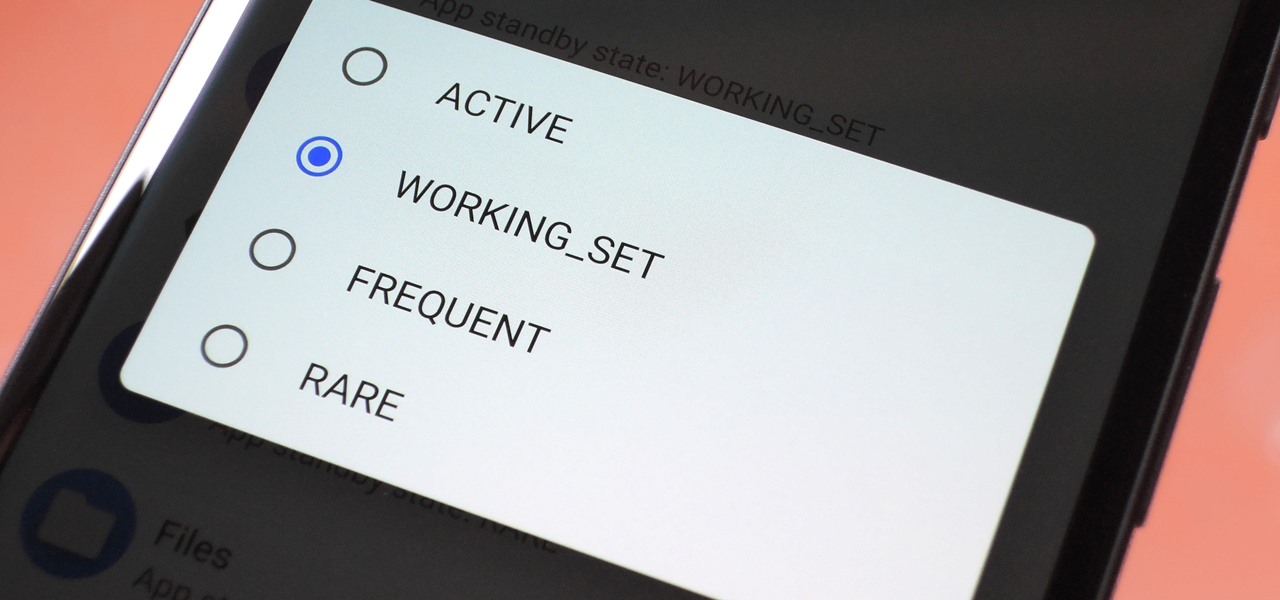
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.