Everyone floats in the Dead Sea because the amount of salt in water effects the density. Do a hands-on experiment and practice checking density. Here’s a good science experiment to do in class or at home, if you have access to an electronic balance.

If you want to improve your violin technique then this how to video is the place to start. You will learn how to play an exercise that improve your tuning. This exercise, based on the Sevcik System, is designed to help intonation training. You should start at the speed of 40 then gradually move it up to the goal of 16th notes at the speed of 192. This exercise will improve the overall shape of the left hand; train the hand to be more articulate and accurate (no muscles just a twitch); builds ...

In this video series, our expert will teach you how to care for corn snake pets. You will get excellent tips on how to set up a terrarium habitat for corn snakes, how to handle corn snakes, and how to determine the sex of corn snakes. You will also learn about how corn snakes shed their skin, what types of morph varieties are available, and how to breed corn snakes.

In this series of internet commerce videos, our bookselling professional gives you expert advice on how to sell your old books. She tells you how to determine their value using the esoteric language of the rare book world.

In this power tool video series, learn how a fixed base power router works. Our expert will demonstrate how to properly use this woodworking tool, including general shop and tool safety tips, what you need to know before making a cut, installing and removing the bit, setting cut depth, and determining the direction of feed for the router.
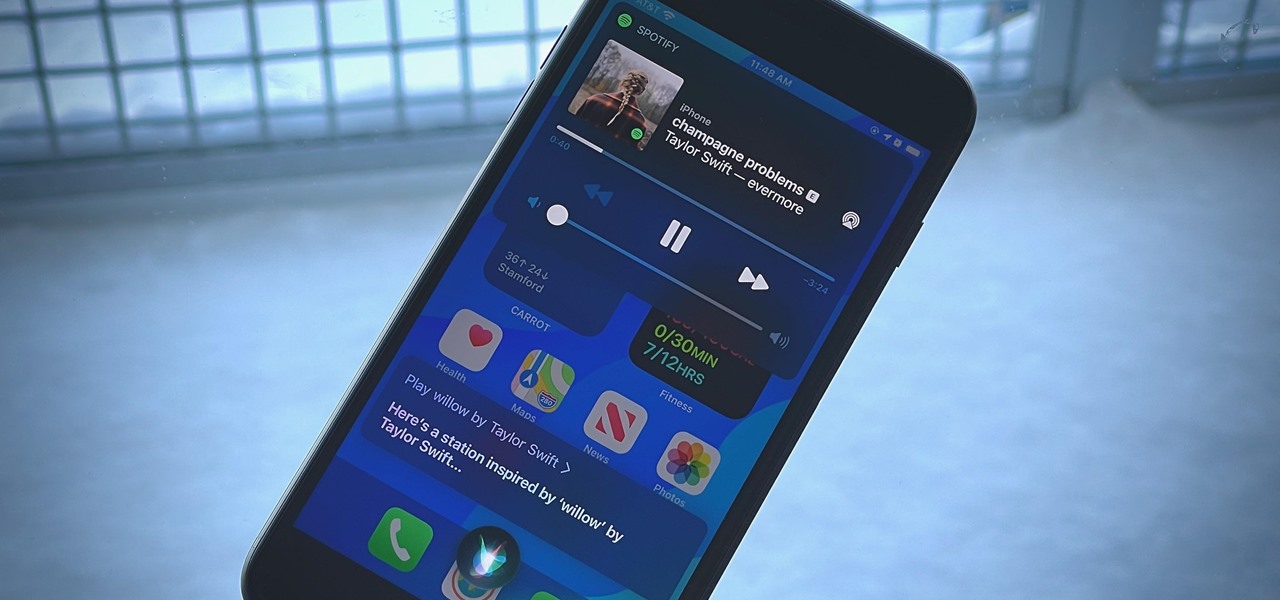
It's no secret that Apple and Spotify haven't exactly gotten along in the past, but things are looking better than ever in iOS 14.5.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Just as predicted (but perhaps with less fanfare than usual), Apple has made the move of adding a depth sensor to the rear camera of its latest edition of the iPad Pro.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

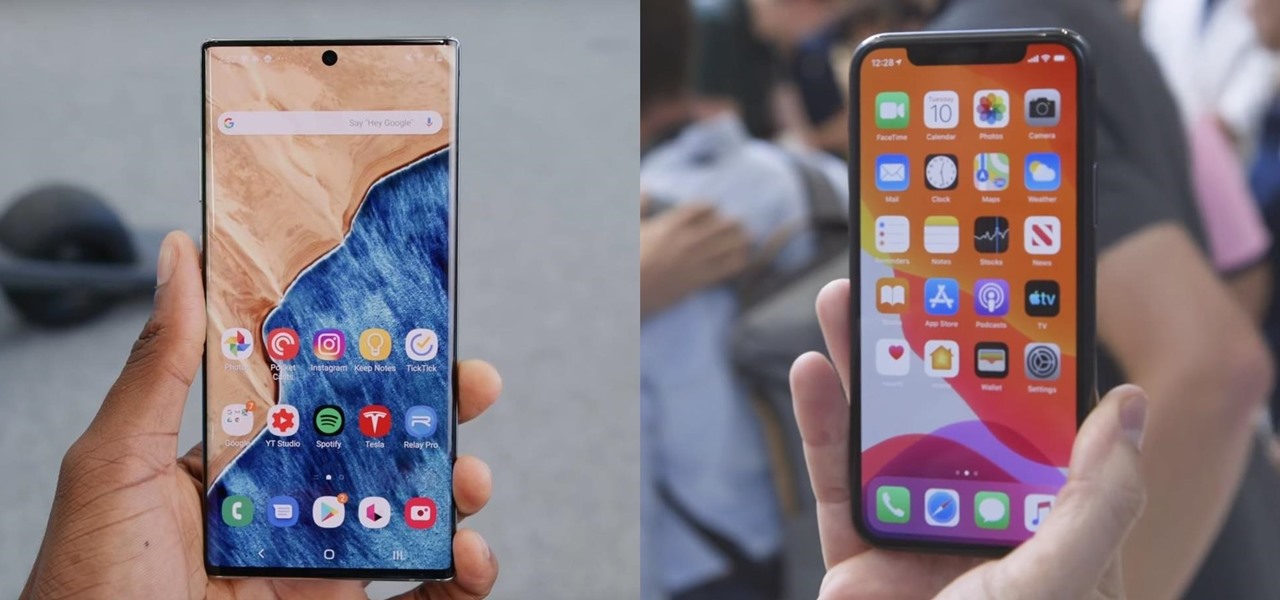
Samsung decided to shake things up this year. In the past, the Galaxy Note series was one large phone. This year, it's two phones: the Galaxy Note 10 and Note 10+. So for the first time in a long time, we can compare the latest standard iPhone, the 11 Pro, to a Galaxy Note device.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Niantic's Harry Potter: Wizards Unite offers players an augmented reality look into the world of witchcraft and wizardry. The Wizarding World and Harry Potter novel series is full of unique and interesting characters, which is why it makes sense that Wizards Unite offers you to take the role of one of three "Professions" — Auror, Magizoologist, and Professor. The question is, which one do you pick?

We've all been there — using Google Maps for navigation and waiting for the app to find our location. As we drive around, we keep hoping it will get a lock in time to make the next turn. Well in the US, we finally have a solution to this problem, and it's the OnePlus 7 Pro.

In a world of seemingly endless streaming services, podcasts continue to offer free, unlimited entertainment for all. When you find a podcast that's just too good to keep to yourself, sharing it with family and friends is inevitable, but how you share may determine whether or not they listen to it or not. Links alone aren't enough. Audio and video clips are how you get them sucked in.

It's difficult to find that perfect lighting when you're taking a photo. You won't always have studio lights — or at all — and you're not always out during golden hour. So how can you combat lighting issues without waiting around for a well-lit condition? Do it in post. Adobe's Photoshop Express makes it easy to fix and even customize the lighting in your photos using the right adjustments.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

The idea of augmented reality isn't new, but the world of smartphones is looking to push it forward in a big way. As with any platform, both product demand and technological advancements have to catch up to the industry before it can become a viable solution for daily consumer life. Apple and Google are working to introduce the smartphone consumer to AR for the first time with basic features for now.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.