Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

Over 6,500 waterfowl—mostly ducks—have died in Canyon County, Idaho, stricken by avian cholera. The outbreak started in February, and before it's over, it may not only be Idaho's largest outbreak, but one of the largest in the country.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

We may not fully appreciate all the important roles wheat plays in our lives until it's gone—or at least, when it's in very short supply. What would a world be like without bread, cakes, cereal, pasta, or wheat beer? If the dire warnings about an impending stem rust fungus come to pass, we may know all too soon.

Scientists are constantly on the search for new organisms, species, and other types of life. A special group of these researchers, calling themselves "bioprospectors," dive deep into mines to find unique lifeforms with special properties not found anywhere else.

You know the signs—sneezing, fever, nagging cough, no energy, no appetite. It's the flu, but this time, it's your dog who's down and out. Yes, dogs get the flu, too. However, a team from the University of Rochester Medical Center and their collaborators have developed a new vaccine that may make the doggy flu a thing of the past.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

Apple just unveiled the new iPhone 7 and 7 Plus at their September event, which means we're inching closer to traffic jams, parking lot fights, and day-long lines at Apple Stores, as well as those inevitable, dreaded words: "sold out."

Let's say you're with friends at a sporting event, music festival, lounge, or some other fun venue, and you want to create a fun split-screen compilation from all the videos you took independently. It's not an easy task, because someone has to get all the video footage and then use a video-editing program that supports split screens. It's a daunting task most people will just skip.

A stack of light-as-air pancakes can make a weekend morning truly golden. While fluffy pancakes may not seem like rocket science, the reality is that there are many little details that can contribute to a pancake fail that's either too dense or too crumbly.

Often, the most frustrating part of crafting the perfect dinner is feeling like you have to clean every single pot and pan in your kitchen after cooking just one meal. With so many components, it can feel like each step of a single dish requires its very own pot.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

I was bored when I found this piece of literature: ==Phrack Inc.==

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Pain is, for the most part, unavoidable when you stub your toe, break your arm, or cut your finger open. It's instantaneous and, in some cases, long-lasting, but it only feels as bad as you want it to. Yes, that's right—that pain is all in your head.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Why did I write this when they're tons of scanning tools available.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

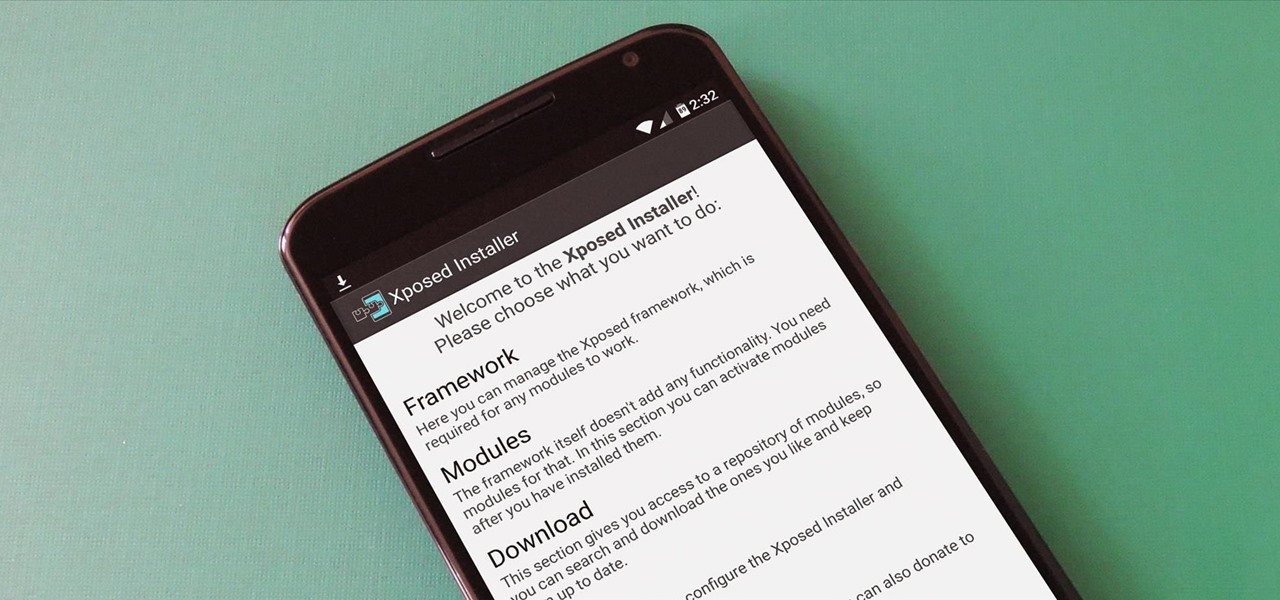
UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

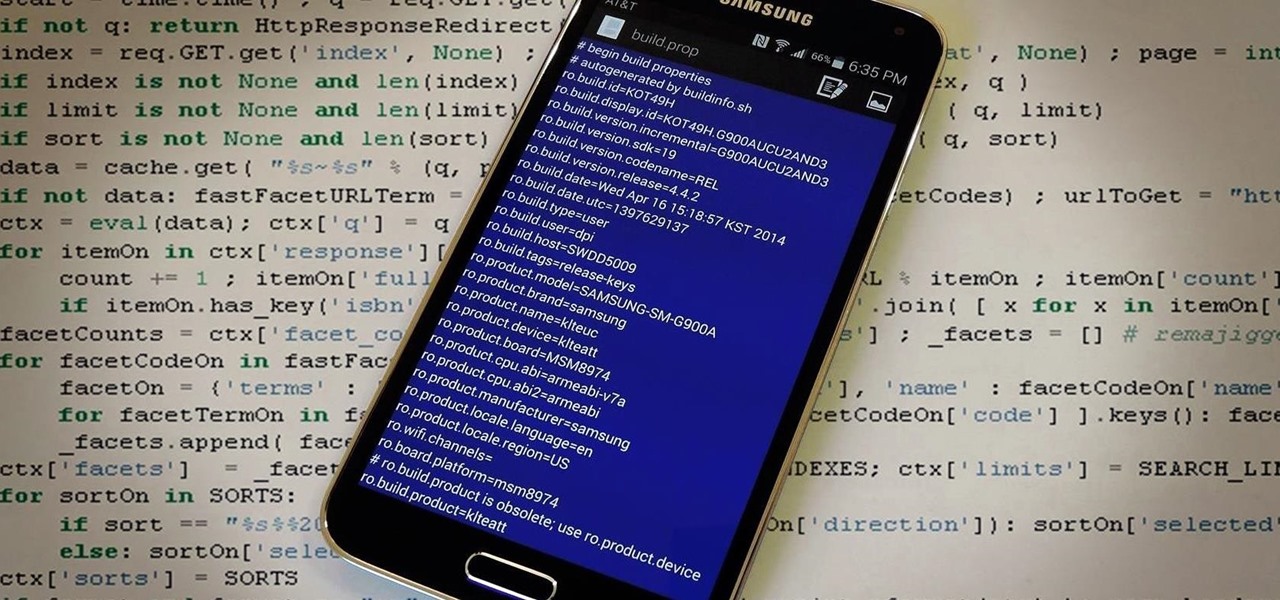
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.