The hidden shrines in Assassin's Creed Brotherhood can be very difficult to access, but very rewarding once you do. If you're having trouble finding them all, watch this video for a guide to entering the Cloaca Maxima Shrine and earning the Plumber Achievement / Trophy.
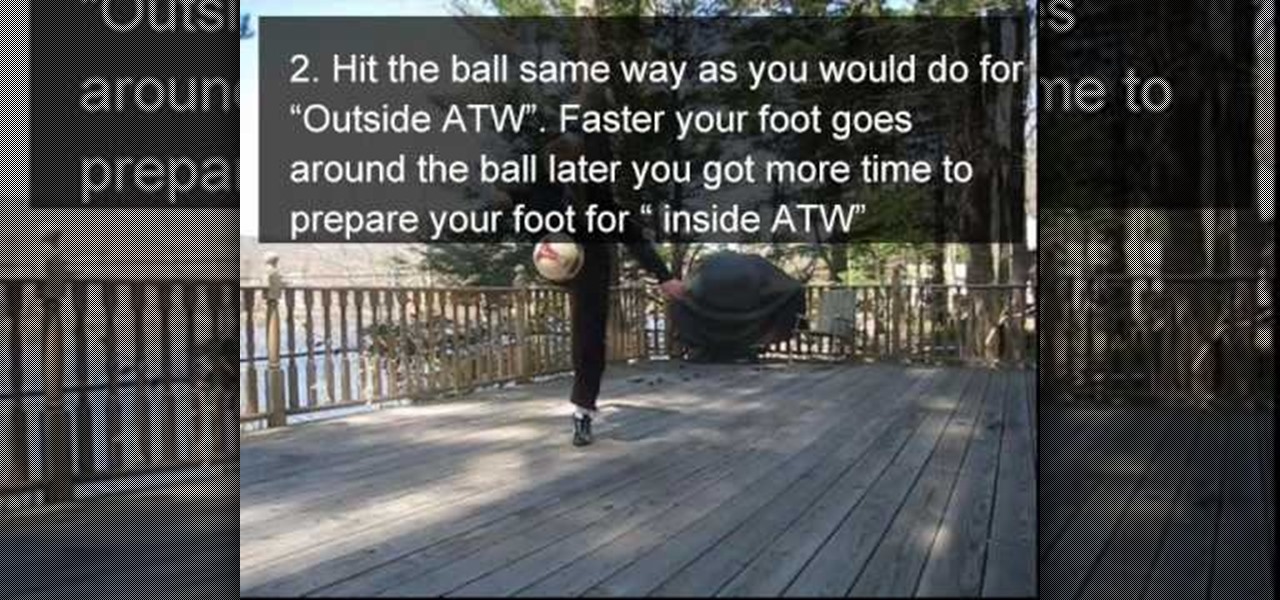
Are you good enough at freestyle soccer that you've already mastered the Around the World? Well then welcome to the next level of tricks. Think you've got what it takes for a Mirror Around the World? This trick is like a double around the world, in which both legs take turns swinging over the ball before it is finally caught. This one is tough, but beautiful and rewarding.

Hitting up antiques stores or flea markets every now and then engenders eccentric rewards of odds and ends, pretty semiprecious stones that look dazzling but have no home.

Post-mount brakes are just one of many types of brakes that can be installed on a mountain bike. This video features detailed instructions on how to set up a post mount brake on an IS mount, making your mountain bike stop like Deepwater Horizon spill refuses to. It is a complicated process, but a rewarding one.

Popularized by artists like Son House and Skip James, Delta blues is not only one of the oldest forms of blues music, it is among the most stylistically distinct and technically rewarding to play. In this video guitar lesson from YouTube user deltabluestips, you'll learn how to play Tommy Johnson's "Canned Heat Blues" on the guitar.

Rewarding as it may be, knitting a sock can be quite time consuming, so you want make sure you do everything right the first time around. When finishing your sock, you want to decrease the size at the toe and seal it up so it fits snugly on your foot. This video will show you to decrease the toe.

If you want to house train your puppy or dog by yourself, this video is for you! It will show you the best tips to make your puppy learn how to live in your house without creating any problems!

When you've mastered the single crochet and have gotten a hang of the double crochet, it's time to really step up your knitting game and start the triple crochet, a more difficult but rewarding type of stitch that creates a very tightly woven fabric.

Mmm...barbecue pork shoulder. This oven "smoked" barbecue pulled pork will melt in your mouth. Watch this video to learn how to make a succulent, tender dish, that's great for dinners and parties. All you need to do is put the ingredients in a Dutch oven, and place in the oven for a few hours. You'll be rewarded with the delicious smell and taste of flavorful, tender pulled pork.

Who says you can’t play fetch with a cat? You just have to make it worth Fluffy’s time. You will need a cat, patience and rewards. Tip: Don't yell! Cats don't respond well to loud noises. Don't use "no" during training, as this should be reserved for important things like not shredding furniture.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

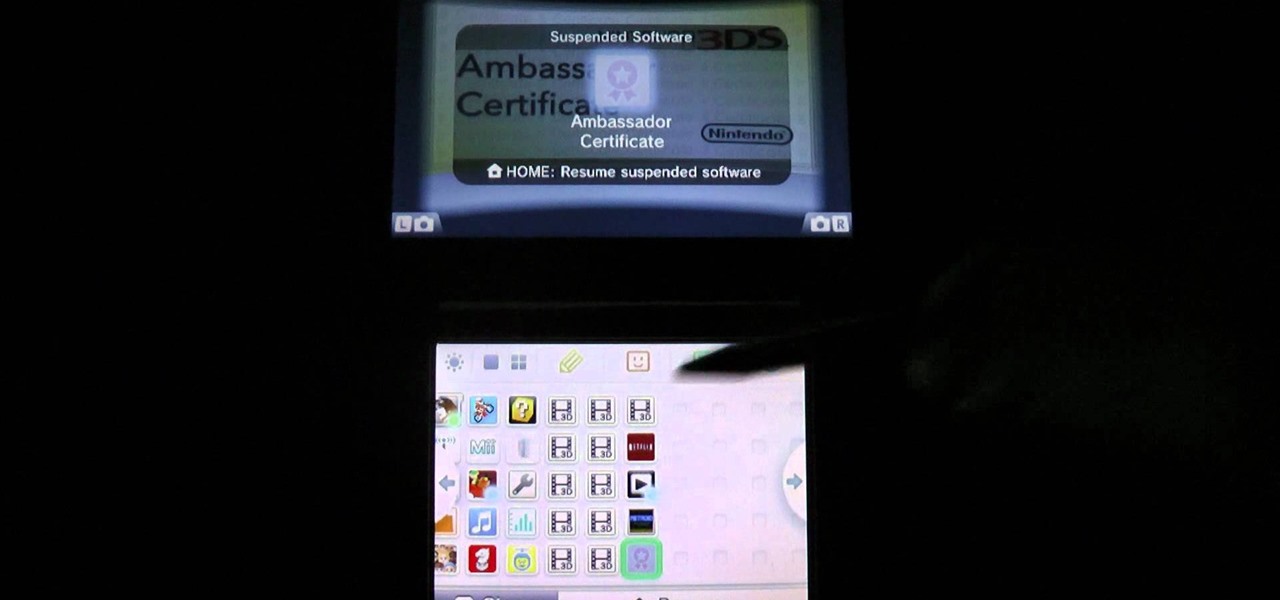
If you're one of the lucky members of the Nintendo Ambassador Program on the Nintendo 3DS, take a look at this walkthrough of the perks available through the eShop on your 3DS. You'll be able access and download an Ambassador Certificate, Metroid, and more. Just enter the eShop and head to the 'Your Downloads' menu to start loading them up on your handheld.

Passed out roommates and guests are some of the most fun and rewarding people to pull pranks on. They'll never know what hit them! This video will show you how to do a couple of awesome pranks on passed out people, some old and some new. Especially creative is the match-in-the-foot trick from the beginning of the video.

if you've been playing the game Risen and are having a hard time finding Scordo the Bandit Chief, this tutorial will help. It's really easy to find him after watching this tutorial.

This next tutorial is a rather easy one to follow and complete. It shows you where you have to go in order to get the Overkill achievement in the game Brutal Legend. To get this achievement, you must complete all the hunting missions and then meet up with the Hunter. Once you've had a chat with him, you'll be rewarded with an awesome weapon and 20 gamerscore. Good luck!

When you've mastered the single crochet and have gotten a hang of the double crochet, it's time to really step up your knitting game and start the triple crochet, a more difficult but rewarding type of stitch that creates a very tightly woven fabric.

Volleyball is a very challenging, fun, and rewarding sport. This video demonstrates some drills that you can do, or have your athletes do, to improve their volleyball skills. It includes an explanation of the different volleyball positions. It follows this with some training techniques including having players play their unnatural positions and how to serve properly.

Hard-working, request-taking graffiti artist Wizard spits his game all over this design, a script tag of the name of viewer Serk. It bears all the earmarks of Wizards clean, traditional style, and as with all of his work would make a very rewarding exercise for any aspiring graffiti artist.

Jazz guitar is one of the deepest, most challenging, and most rewarding kinds of playing. This video by Justin teaches us an jazz guitar exercise designed to work on I VI II V I chords. Some skill is definitely required, but if you're an experienced jazz player this exercise should very much help you improve your skills.

A Northern CA beekeeper introduces the honeybee, shows slides of her small operation, and shares lots of personal beekeeping tips on things like hive placement and discouraging bears. Beekeeping can be a rewarding way to get your own fresh honey and beeswax. Watch this video insect farming tutorial and learn how to care for bees and practice beekeeping.

This video shows how to train a guinea pig to do a circle trick. The same reward method is useful for teaching a guinea pig to do any trick also.

This video walkthrough shows you how to beat The Croft Manor Library on Tomb Raider: Legend for the XBox 306 and PC and find all of the hidden rewards on hard difficulty.

This video walkthrough shows you how to beat Bolivia redux on Tomb Raider: Legend XBox 306 and PC on hard difficulty and find all of the hidden rewards.

This video shows unrivaled faith in Chef Paul by unplugging his bread machine and allowing the master teacher to reveal the best way to make bread. Chef Paul rewards such resolve by crafting Lean Italian Bread, Braided Rich-Egg Bread and Sausage and Cheese Bread. Tom’s only complaint? The lack of preservatives will force him to make bread again real soon. "Cooking Key" Focus: Yeast «

Finally free to make his "famous" grilled cheese sandwich, Tom quickly realizes there’s a big catch: He has to milk a cow. The cooking novice takes one for the team and is rewarded with taleggio prosciutto grilled cheese sandwich, My favorite grilled cheese sandwich and cream of asparagus soup.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

The eBooks scattered throughout Deus Ex: Human Revolution will allow you unlock the 'Doctorate' achievement and this three part Achievement Hunter segment will help you track them down. There are 29 of them hidden throughout the game and you'll be rewarded with 200 XP each time you find one.

You know what's effective against zombies? Armored tanks are effective against zombies.

Whether you're the kind of gamer who likes to fight the law or fight for the law, you probably shouldn't pass up this sidequest line in Dragon Age 2. Accessible after completing the 'Birthright' quest you can pursue 'Magistrate's Orders', which these videos will give you a walkthrough of.

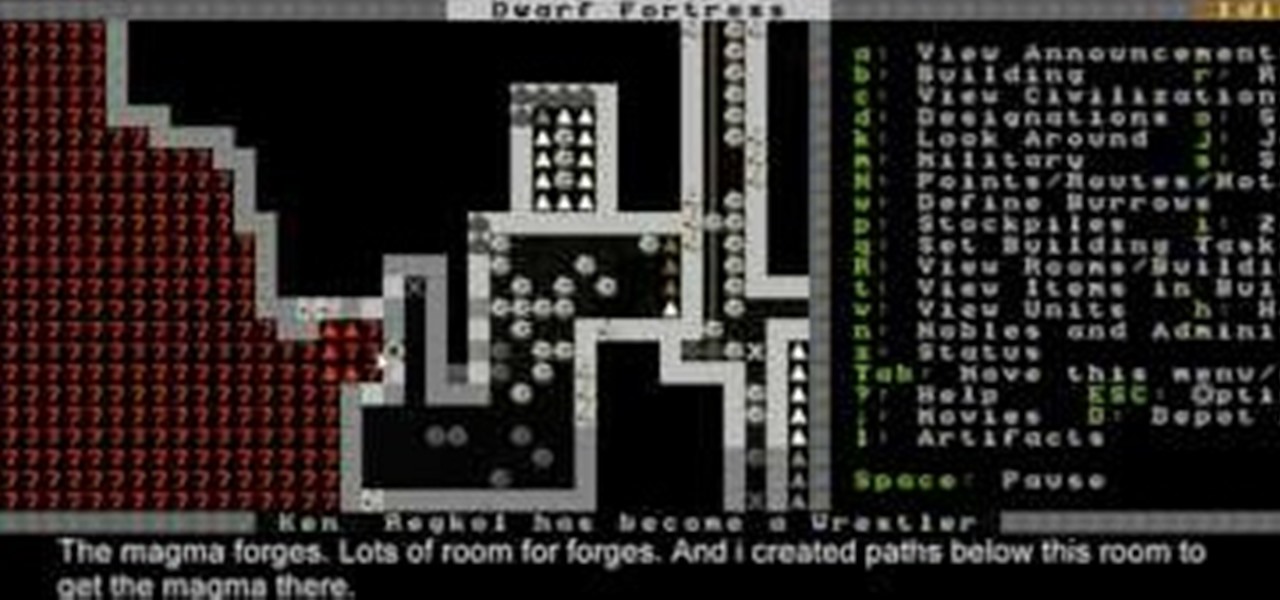
One of the new areas that you can access in Dwarf Fortress 2010 is Hell itself. This video will show you how to get there and what to do when you do.

This video will show you how to build and use hospitals to take care of your dwarves in Dwarf Fortress 2010. It also discusses what happens when you abandon and then reclaim your fortress.

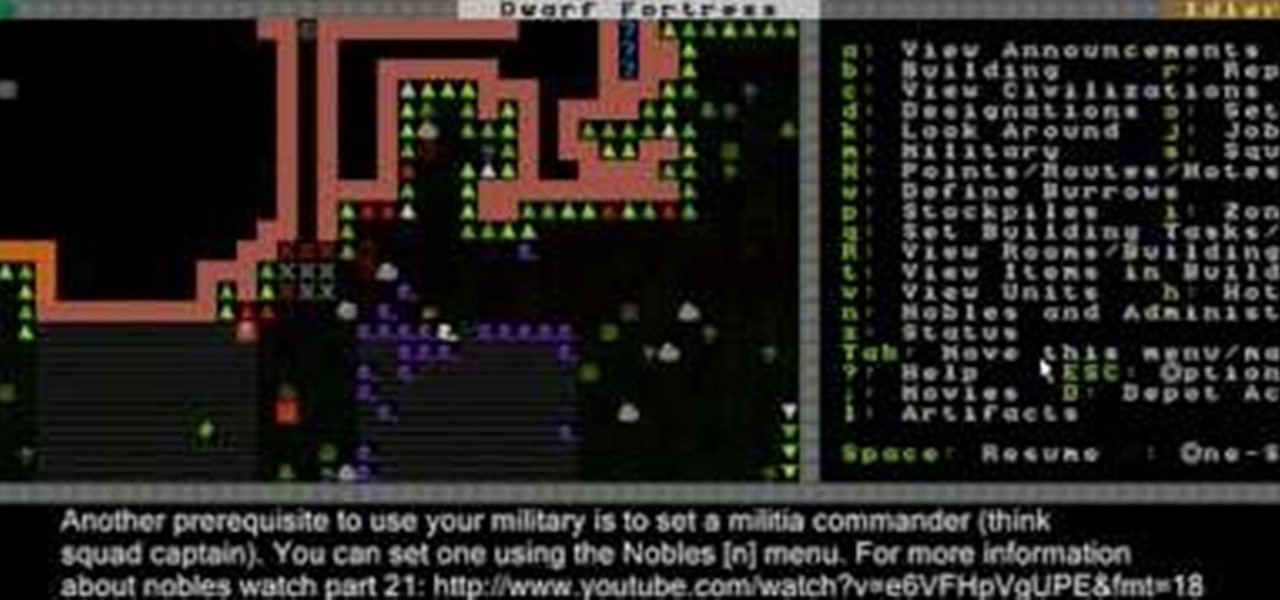
In this video, you'll learn about the basics of using your military to defend your fortress, in this case against a dinosaur attack, in Dwarf Fortress.

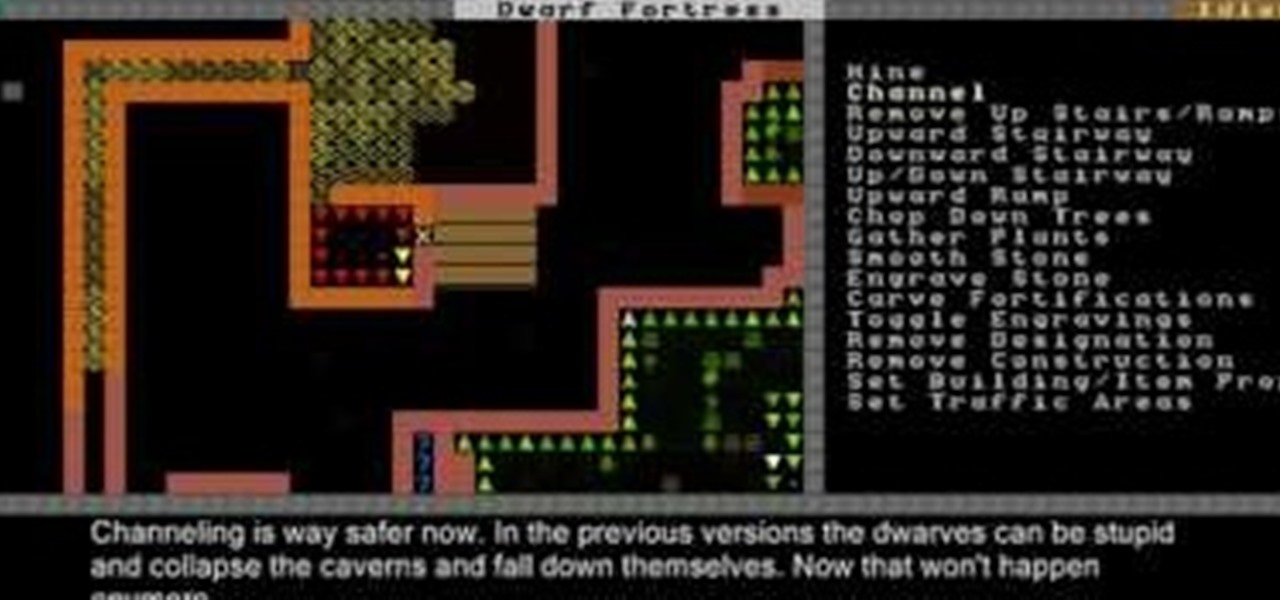
This Dwarf Fortress 2010 video will show you how to design a basic, effective fort, and also explain how channeling and farming work.

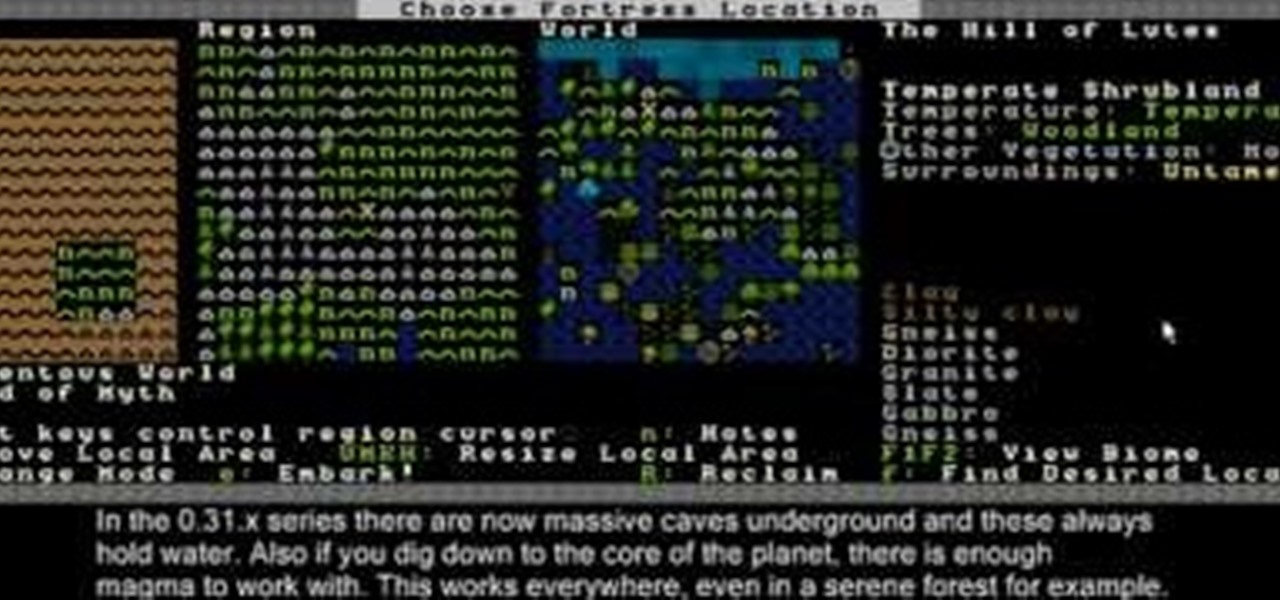
The release of Dwarf Fortress 2010 introduced many great changes to Dwarf Fortress, and this video will bring you up to speed on them. It also covers the beginning of a game, including preparing your dwarves, choosing a fortress site, and getting into caves.

This video will give you an overview of a successful endgame fortress from Dwarf Fortress, giving you tips on achieving a similarly successful fortress throughout.