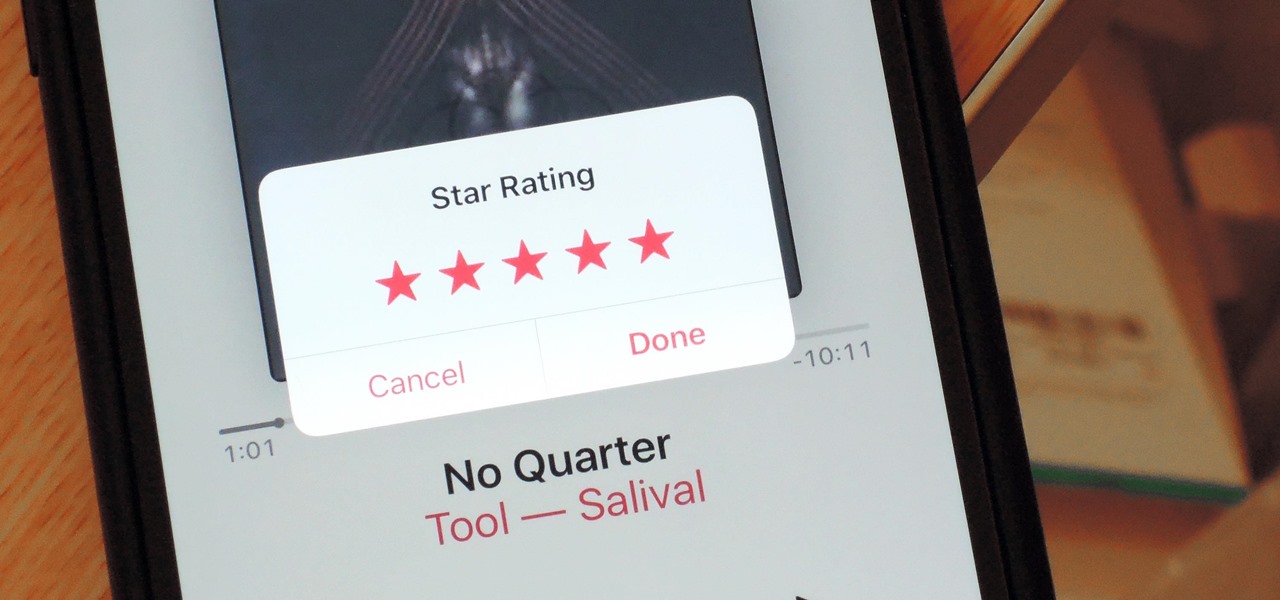
When Apple released the iOS 10.2 update to the public on December 12, 2016, iPhone users got a slew of new features, including new emojis, a brand new TV app, the ability to save camera settings, and more. But out of all of these new features, the one that interests me the most is something they didn't even include in the release notes—star ratings are back in the Music app!

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Thanksgiving.

Take one down, pass it around, 99 bottles on which to play classical music? As someone who has studied music extensively, I've seen many interpretations of famous pieces of music played on glass bottles, but hearing these four interpretations of famous pieces (not all classical) completely blew my mind.
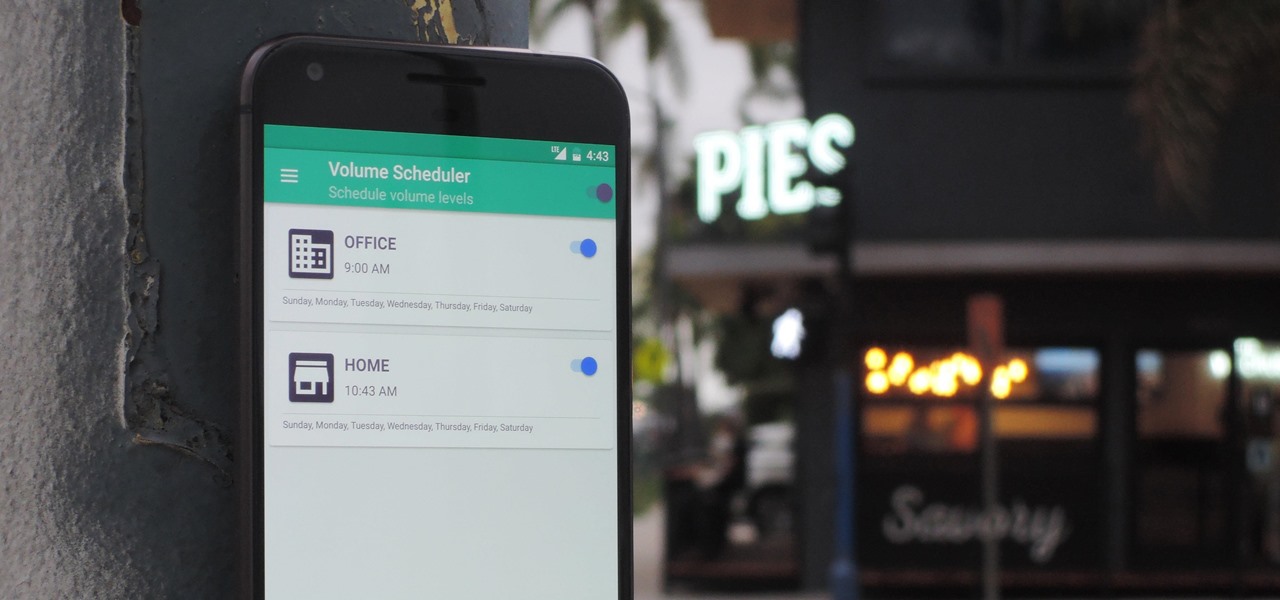
Different times call for different ringtone volumes. When you're at work or school, you need your phone to be quiet so it doesn't make a disturbance—but when you're at home or out and about, the volume should be turned back up so you don't miss any important notifications.

Apple is famous for keeping a tight grip on the look and feel of iOS (a grip so tight it may even change the future of patent law), but the clever folks over at heyeased found some neat tricks to put the control back in your hands.

A 2D film can show you something, but a 3D film in virtual reality can make you feel it. If done right, you'll feel immersed in a new world that surrounds you. If done wrong, you'll get nauseous and uncomfortable. SilVR Thread, a 360-degree VR video company, figured out a few important ways to get the feeling right.

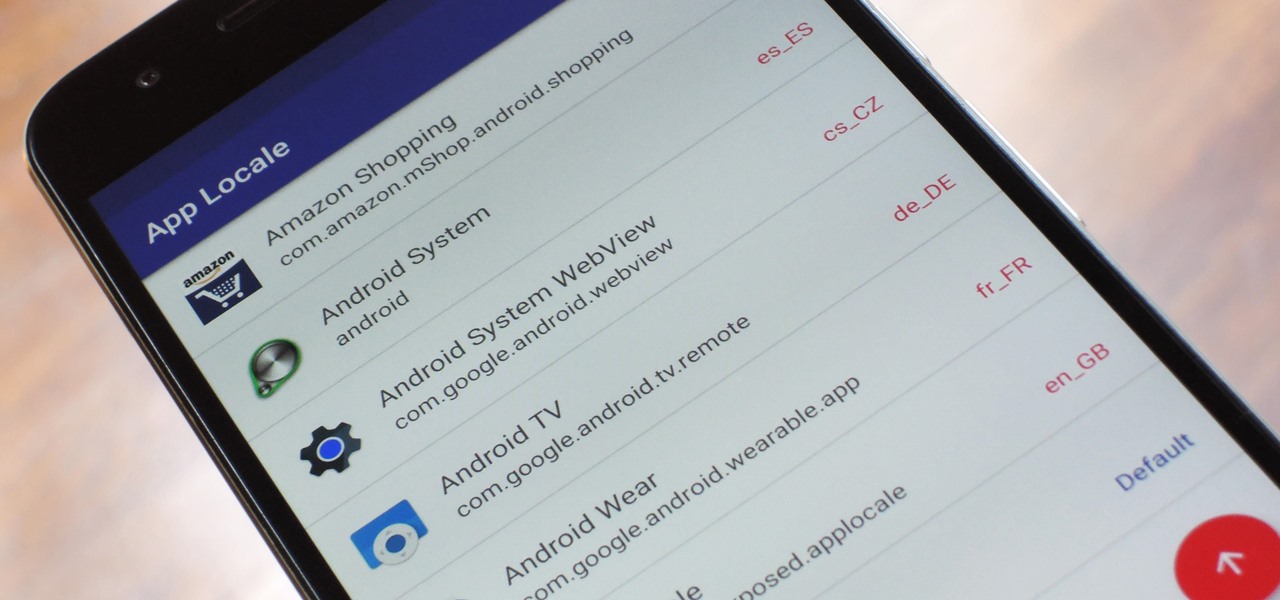
Android clearly wasn't made with bilingual users in mind. When you set a default system locale, every app on your phone uses that region's language—and there's no granular control here. This really becomes an issue if you use social media or news apps that are primarily in a different language, because apps are generally written in the developer's native tongue, then poorly translated to all other languages.

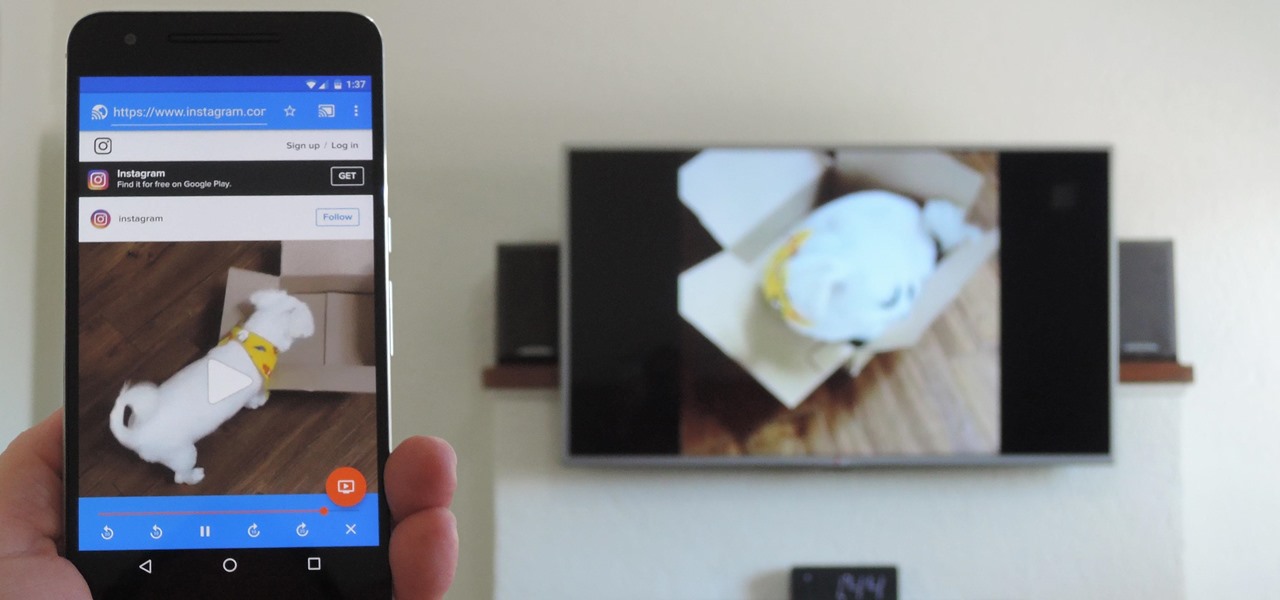
The Google Chrome browser for Android allows you to cast quite a few different videos from the web to your TV, but some sites actively disable this functionality, and others have outdated video players that won't allow for it. For example, Instagram's mobile website won't let you cast any videos, and the official app doesn't support Google Cast.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

Smartphones tend to struggle when it comes to recording video in low light situations. Danish phone manufacturer Lumigon included a good camera capable of shooting 4K video on its latest phone, The T3, but the real interest lies in the second camera, which is a dedicated night vision shooter.

Since I recently had this problem and fixed it, I might as well share the solution. This is actually REALLY simple to fix but will impact your cards' performance.

Google first introduced Google Home, its latest smart product in the works, at the company's I/O conference in May 2016. It will directly compete against Amazon's Echo, which has so far been a success with over 3 million devices sold, and it was even featured as FBI Agent Dom's only real friend in the second season of Mr. Robot. Google may have their work cut out for them, but we're betting Home will knock Echo out of the water. Google Home is a personal assistant with a built-in speaker and ...

The biggest problem with plastic wrap is also its most useful trait: its incredibly clingy nature. Plastic wrap seems to stick to itself or you before you can get it over the plate, bowl, or food you're trying to preserve. And once you do manage to get it in the right position, it never sticks as well as you need it to. Fortunately, you can combat these inconveniences with two extremely helpful methods—a change in temperature or a bit of added moisture—as Jenny Stewart of CHOW explains in the...

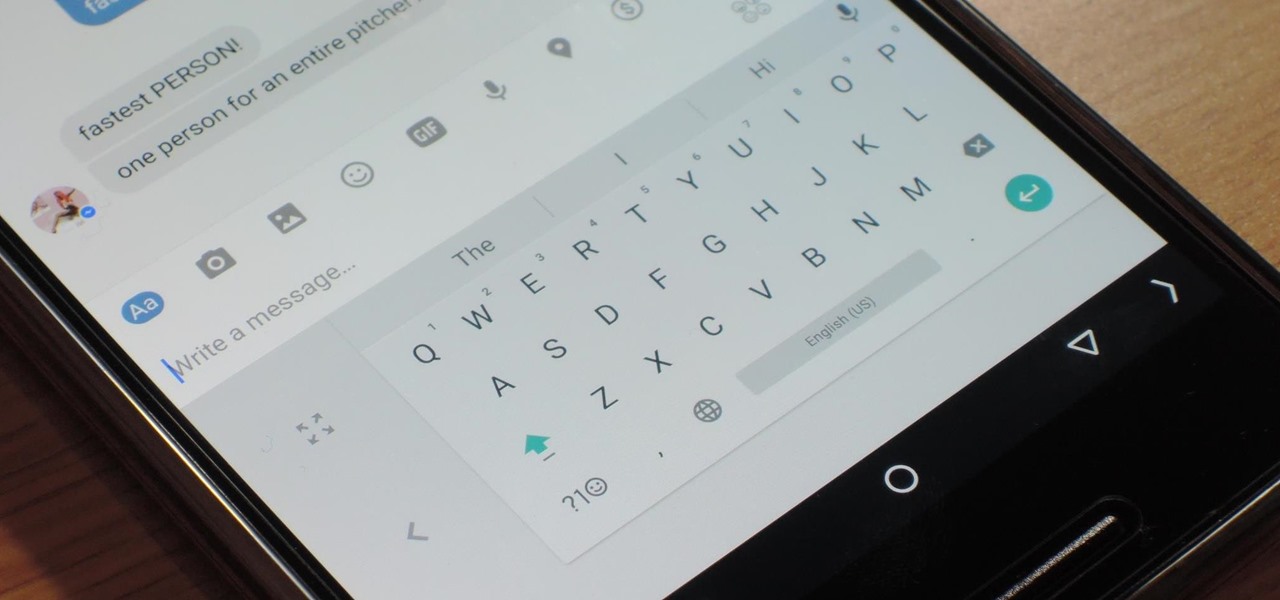
Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

The Galaxy S7 edge comes with a feature called Edge Apps that lets you quickly launch your favorite apps by swiping in from the edge of your screen. It's a natural and intuitive gesture, and as a result, we've seen a recent influx of apps that look to emulate this feature.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Google has been working on its voice recognition technology ever since the days when you had to call a phone number with a Silicon Valley area code to dictate your query. As you can imagine, things have come a long way in the decade or so that has passed, to the point where we talk to our phones as if they were a person nowadays.

Much like the Chromecast, Android TV devices such as the Nexus Player and Nvidia Shield TV have always had those beautiful background images as their default screensaver. However, unlike the Chromecast, these "Backdrop" images, as they're called, weren't always customizable on Android TV.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

New technologies in current-generations smartphones allow for much faster charging—Qualcomm Quick Charge 3.0, VOOC Flash Charge, and USB Type-C, for instance, can charge a phone up to 4 times faster than traditional methods. However, the majority of phones on the market still don't support these standards. So for the rest of us, I'll go over an easy tip that can charge any smartphone as much as 25% faster.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

When you click a link from Google search, the link itself turns purple to let you know you've already visited this page. But let's say you're searching for something similar a few weeks from now and you see one of these purple links—you'll probably think to yourself, "What was I reading about on that site?"—and if you don't remember, you'll end up clicking the link again. And if you're a frequent Reddit user, you know this pain all too well.

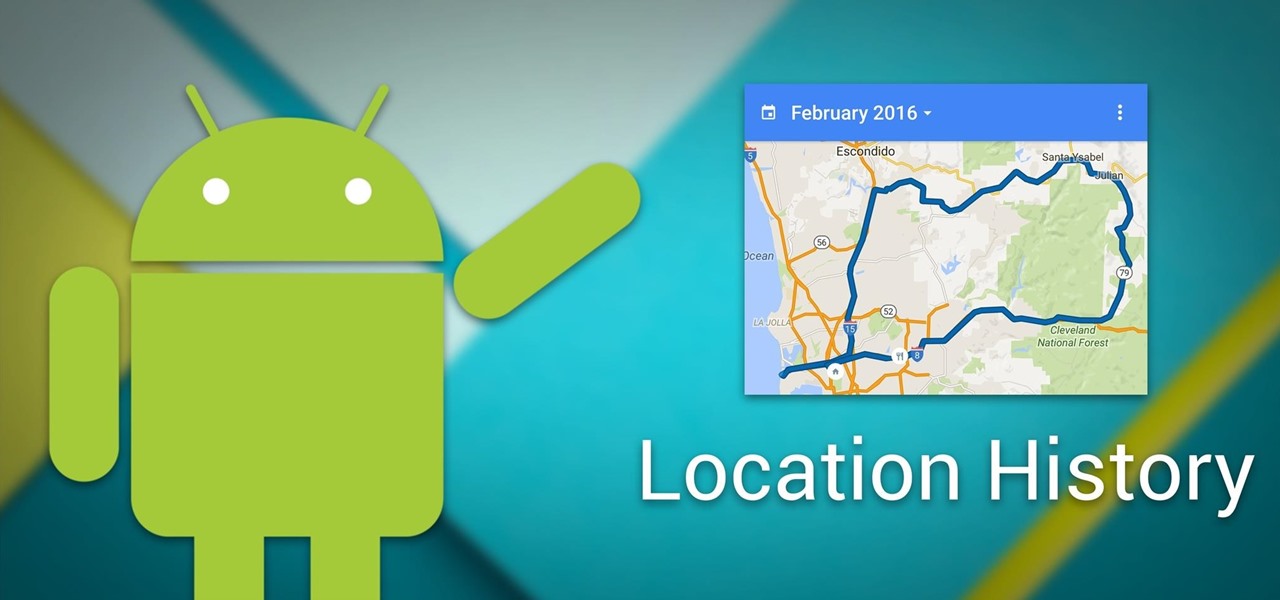
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Hello there Nullbyte users! This will be my first article here.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

The Creative Lab at Samsung, also known as their C Lab, is trying to make wearable fitness devices more inconspicuous with its wearable smart belt, the WELT, but that might not be all.

Three smart devices shown at CES 2016 are making it easier for you to make stupid decisions. PicoBrew, Somabar, and 10-Vins demonstrated their systems for beer, mixed cocktails, and wine, respectively, and each one is attempting to change the way we enjoy our favorite potent potables at home.

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.