
How To: Create a simple morph effect with Adobe After Effects
In this video tutorial, Creative Cow Contributing Editor Eran Stern will show you how to create a simple morph effect using time remapping and pixel motion.


In this video tutorial, Creative Cow Contributing Editor Eran Stern will show you how to create a simple morph effect using time remapping and pixel motion.
In this tutorial, Broadcast Designer Jason Brown will show you how to knock out a vector logo from Adobe Illustrator into a 3D logo in Maxons Cinema 4D. The tutorial also touches on basic texturing, lighting and animation.
In this video tutorial, Creative Cow Contributing Editor Eran Stern will show you how to create a fiery iris animation which has laser beams shooting from a girls eyes.

The independent film Juno featured one of the most distinctive opening credit sequences in recent memory. It has a wonderful handmade look - which it turned out was created by hand! Whether you have seen Juno or not, Cow leader Simon Bonner shows a much easier way to create unique, handcrafted looks, without the pain.

Terminator Salvation is the fourth film out in theaters right now, starring Christian Bale as John Connor, the near-leader of the Resistance, and Sam Worthington as Marcus Wright, a mysterious new prototype robot, a one-of-a-kind. It also has a cameo of Arnold Schwarzenegger in it, as the original T-800, Model 101. Well, actually it's just CGI facials.

Shoe Golf is like frisbee golf, but without the frisbee. Just an empty street and your shoes. Our affable host breaks down every part of this brand new game, from scoring to penalties in front of the one of the most beautiful backdrops we've seen. Play shoe golf.

I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

In case you haven't noticed, I absolutely adore video games. Most of my friends don't, so to get my fix of knowledgable video game conversation I have turned to podcasts. They're free, they feature the smartest people in games journalism, and can be enjoyed while doing just about anything. Working. Walking the dog. Crying yourself to sleep. Whatever you're into.

Want to make money by streaming videos online? Here's three steps to success. Find Good Quality Websites to Submit Videos

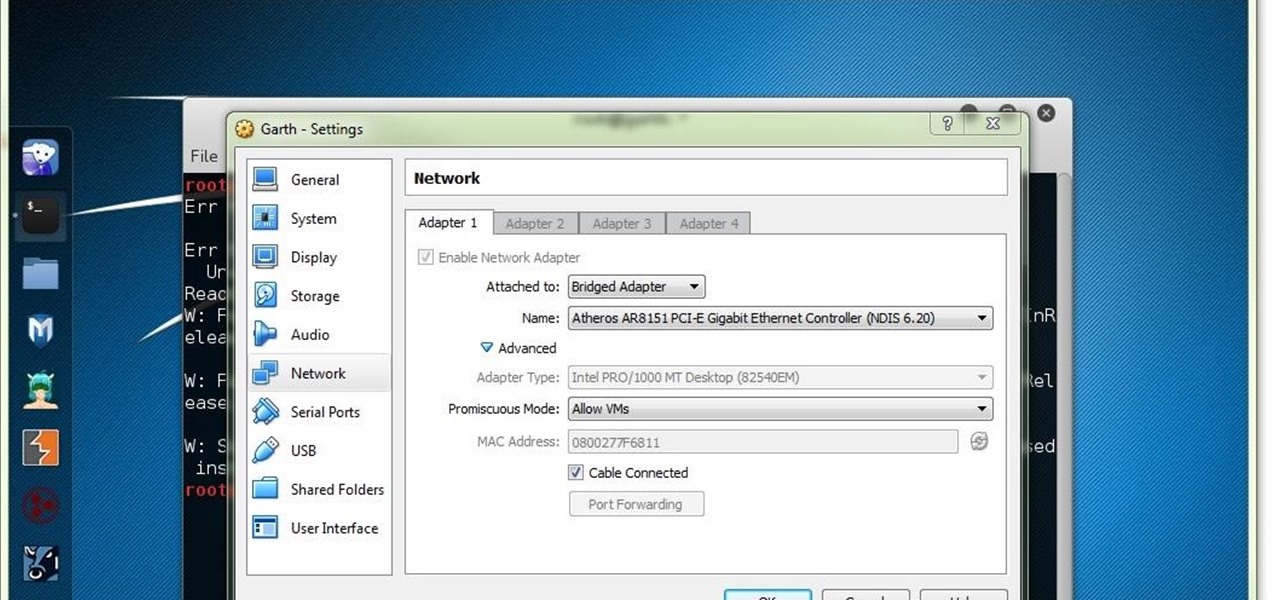
Things You'll Need A fully working operating system that supports VirtualBox (Windows, OS X, Linux or Solaris)

Whether you're training to pursue it as a career or just like to show off your knowledge when you're hosting company, knowing how to pour a well-sized shot is great for tending bar. This method makes it easy for anybody to size a drink. All you have to do it count to 6 and pour. This video will show exactly how to pour accurate shot sizes.

Kentucky Afield: Watch as Tim Farmer hosts the processing of venison, starting in the field and ending in the kitchen. Start with the deer down. Start with the tail and trim around the anus. You want to not break the colon nor the bladder for sanitary reasons. This is a long and delicate process of gutting a deer so that you may bring it easily back to the kitchen to make venison! Field dressing is an important hunting skill. Gut a deer, field dressing.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

With the computer's rapid increases in power and efficiency, computer virtualization has taken the scene by storm. With virtualization software, and powerful enough computer hardware, your computer can run a virtual computer within itself. This effectively gives you multiple OS's on the host OS. This can be used for a lot of cool stuff that your computer would normally be limited by. Let's take a look at a few.

Something that can shy a user away from making the switch to Linux is not having the option to go back to Windows. Luckily, there are solutions like dual-booting, where you can have both OS's installed right next to each other. However, Windows 8 appears as if it will block dual-boots with its neo-space BIOS that have been developed. Sneaky-sneaky. Windows users could still throw in a Linux live CD to try out Linux, but what does a Linux user do when they need something from Windows?

One of the most exciting new features announced by Google+ was the ability to broadcast hangouts live via YouTube, which was recently demonstrated with the very first Google+ Hangout On Air with +will.i.am of the Black Eyes Peas.

Type: Photography, no visual or graphic art manipulation Theme: World's Cutest Pet

Finally, Jell-O shots hit Japan. You would think the land of pop, sickly sweet, and incredibly creative commercialization of endless innovative products would have long ago begun serving an alcoholic drink that is A) candy colored B) candy tasting and C) slides right down the gullet, easy as 1-2-3.

Join host Lisa Bleyaert and her friends in this how-to video on a jewelry making adventure. Learn how your favorite family photos can turn into a cool collage bracelet! You will need 1 piece of sticky felt, photos, velcro, glue, scissors, a ruler, a marker, and colored paper. Follow along with this video activity tutorial and learn how to make a collage bracelet. Make a collage bracelet.
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

When you're baking your cookies this holiday season with the children, try something that's both beneficial to your family and your guests— cookies that also act as sweet party favors. Dani tells you what to do in order to transform your Christmas cookies into beautiful holiday treats— tasty, take-home ornaments. Decorate your centerpiece with them before having guests take their favorite home for an easy, affordable way to be an innovative holiday host! Make homemade Christmas cookies as tre...

In this segment from Lonely Planet, we learn how to throw a boomerang. It's not just a question of getting the boomerang to come back to you. Throw the boomerang the wrong way, and it just might come back to you like a heat-seeking missle! The host in this clip has trouble getting the boomerang to return, calling to mind the old joke: "What do you call a boomerang that won't come back? A stick." Throw a boomerang.

Want to get a lengthier look for your lashes? In this how-to video hosted by makeup artist, TiffanyD, learn all about how to apply false eyelashes. In this tutorial, Tiffany uses MAC #35 lashes and she is using Duo adhesive glue to securely apply them to her lids.

Looking to emulate the make-up of classic Hollywood stars like Audrey Hepburn or Marilyn Monroe? Get adventurous and have some fun with this makeup tutorial hosted by makeup artist, TiffanyD!

Create your own T-shirt design with host Lisa Bleyaert by following along with this how-to video! All you need are a cotton t-shirt and some fabric paint and you’ll be on your way to a totally YOU fashion statement! You will need a t-shirt, fabric paint: green, glittery gold, black, and glow in the dark white, a piece of cardboard, and the step-by-step instructions in this video activity tutorial. Paint a t-shirt.

Want a cool place for all of your favorite bugs to stay? Well then join host Lisa Bleyaert as she shows you how to make a bug motel! You will need 1 oatmeal container, 2 paper tower rolls, a plate, black paint, white paint, a paintbrush, an exacto knife, scissors, twine, tape, ruler, a screen, and the step-by-step instructions in this how-to video. Make a paper bug motel for pet insects.

Hummingbirds are delightful visitors to any backyard and now you can learn how to attract them! Join host Lisa Bleyaert as she shows you how to make your very own hummingbird feeder! You will need white, yellow, and green paint, a plastic water bottle, scissors, an exacto knife, red cord, paint brushes, and one plastic container with a lid. Watch this video activity tutorial and learn how to make a hummingbird feeder. Make a hummingbird feeder.

Beach Buckets can be boring but host Lisa Bleyaert has the perfect way to spice them up. So grab your favorite bucket and get ready to make the Sounds Fishy Sand Pail! You will need 4 sheets of sticky foam, scissors, precut letters, a black marker, and a beach pail. Watch this video activity tutorial and learn how to decorate a sand pail. Decorate a sand pail.

Hey all you yogis and non-yogis out there challenge yourself with this core strengthening yoga pose. The latest yoga challenge is called the double arm headstand. Watch this yoga how to video as our host demonstrates the proper way to move from a bound headstand into a double arm headstand. All you have to do during the yoga pose is release your grasp, sneak your arm in the hole between your ear and your shoulder, sneak in the other warm and grab on to opposite elbows. Practice transitioning ...
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.
On May Day in 1971, the US Army rounded up approximately 7,000 protesters into a stadium in Washington, DC that they treated like a make-shift prison camp. Have things changed in the past 40 years? Now a Department of Defense document has been leaked to the Web that details "Internment and Resettlement Operations." The manual outlines policies for processing detainees in internment camps domestically and abroad and how to "re-educate" unruly activists. Alex Jones, host of the Alex Jones Show,...
Sage Workshops are a series of student run poetry workshops. The workshops are inspired and modeled after the Pen In The Classroom program. The Downtown's Central Library is hosting our workshops. The workshops are in their Teen'Scape department. These workshops will eventually branch out to other organizations or schools. We are currently sponsored by PEN In The Classroom. Part of Sage Workshops is maintaining this world in the wonderhowto website. Please support our project and visit our Fa...
The US judge handling the Megaupload case noted today that it may never be tried due to a procedural error, a comment that has sparked the anger of Megaupload’s founder. Kim Dotcom is furious with the US Government for destroying his businesses and rendering hundreds of people unemployed. According to Dotcom the case is the result of “corruption on the highest political level, serving the interests of the copyright extremists in Hollywood.”
Info Summary: Website: EducateTube.com | Host: Sipski

Info Summary: Website: EducateTube.com | Host: Sipski

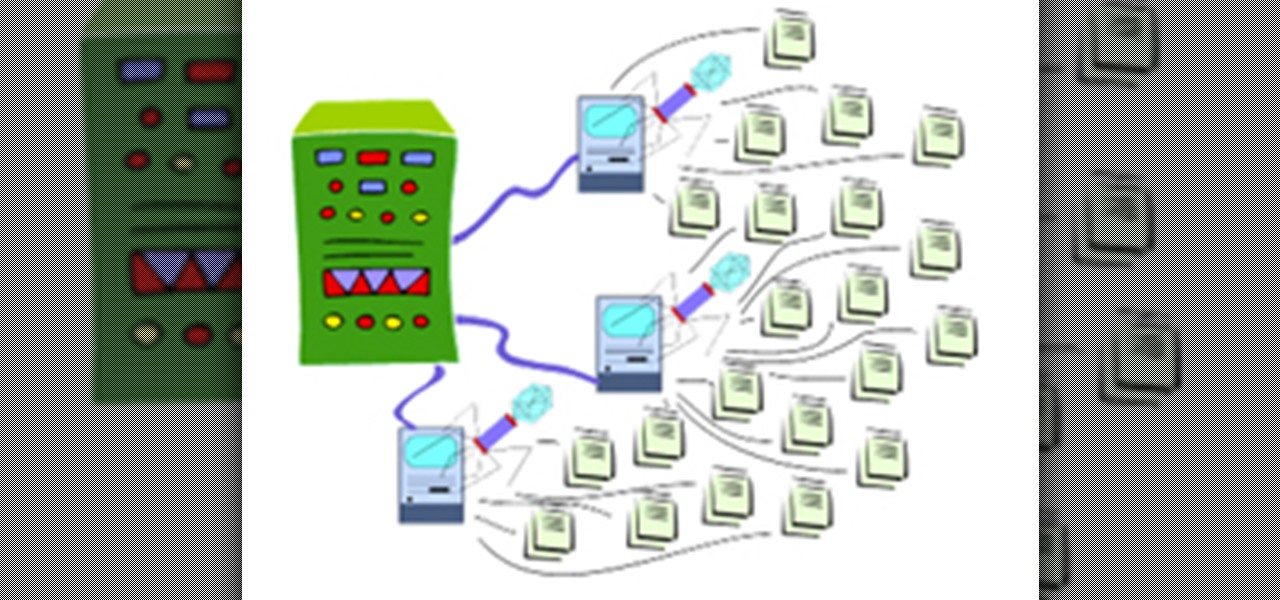
If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...