Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware behind.

REVENANT n pl. -S one that returns 61 points (11 points without the bingo)

Last week's Community Byte we got off to a great start! We had a few people build our IRC bot, and all went well. We had some great contributers, ideas, and people willing to learn. So, needless to say, we will be having another. Let's try to get a few more people involved this time!

There’s nothing like a great horror movie to really get the adrenaline pumping during the Halloween season. I don't know about you, but the sight of blood dripping into a pool of even more blood creeps me out, so you can imagine my reaction to harrowing creatures that go bump in the night and rip people's faces off. It's intense, but I love it.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

Things have been a bit quiet on the Google+ Insider's Guide this week. With the launch of the new Facebook, Google+ is finding itself a bit on the defensive. However, recent data shows that by making Google+ available to the general public, their traffic has jumped 13-fold, according to Mashable. With the new growth also comes the introduction of cool new features, which further enhance sharing.

It's one of the greatest fears among parents and politicians the world over—video game violence spilling out into reality. The shooting at Columbine and the more recent tragedy in Utøya, Norway have touched deep nerves in Western consciousness. And that's why there's a giant pink, juggling elephant in the corner of every production meeting and press conference for each shooter game that comes out.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

The UK print media has been yellower than the middle traffic light for a long time now. The News of the World scandal has cast that into particularly sharp relief of late. The Sun, one of the biggest newspapers in the United Kingdom, demonstrated it again last week when they ran the front-page headline "DEATH BY XBOX".

Google+ is the most exciting new social network to come around this decade, and the only product with a chance of challenging the monopolies we know as Facebook and Twitter. As an Internet addict, I've joined every major social network there is - from Friendster (who?) to MySpace (so ugly) to LinkedIn (yawn) to Twitter (irritating) and Facebook (annoying to manage). Competition is delicious, especially between well-financed monopolies. Google+ really seems to have identified an Achille's heel...

Is that House? Built in Minecraft? Well, time to cross out one more item off my bucket list! As inspiration for this week's Minecraft-themed Tuesday Giveaway (enter here to win an awesome Minecraft Pickaxe!), I present a roundup of amazing things found in Minecraft.

American whiskeys tend to get an undeservedly bad rap from Scotch whisky snobs. Prove haters wrong by inviting them over for an American bourbon tasting with your favorite Wild Turkey varieties.

You've had a hard day at work and need to get out of the house, have a few drinks, but you don't want to go just anywhere—you want the right crowd and the right bar. For those nights, barhopping just isn't the answer, it's SceneTap.

George Plimpton may be one of the most interesting Americans ever. Foremost a sports journalist, he was also a novelist, Fireworks Commissioner for New York City and host of Mouseterpiece Theater. Some of you may also recognize him as one of the men who tackled Robert F. Kennedy's assassin, Sirhan Sirhan. But most of you probably remember him as the pitchman for products like Pop Secret Popcorn and the Intellivision video game console. Actually, his most appreciated work would probably be a s...

Japanese people are into many things Americans find weird—like YouTube's beloved canine-hosted cooking show or Daito Manabe's light up LED grills or even more insane, a vending machine that distributes live crabs. In light of these cultural oddities, the Japanese phenomenon of visual novels (NVL, or bijuaru noberu), seems relatively normal. A meeting place of books and video games, visual novels are a sort of "Choose-Your-Own-Adventure" for the new generation.

INTRODUCTION If you are a part-time blogger and owns a blog which is hosted on blogger, then the first thing which you could want to do is to convert your blog layout to a professional looking website. You can either edit the XML file yourself or you could choose to use a template designed by others. If you have no idea of XML editing and neither you want to use a template created by other, then hopefully there's a way to convert your blog into a website.

Chris Burden's latest piece is a portrait of L.A.'s hot mess of traffic, entitled Metropolis II. The artist has constructed a miniature highway system, complete with 1,200 custom-designed cars, 18 lanes, 13 toy trains and tracks, and a landscape of buildings made with wood block, tiles, Legos and Lincoln Logs. Burden tells the New York Times:
Videos Marketing is always going to grab a hold of any individuals interest and attention a good deal faster and more effectively in comparison with any kind of written copy or even photographs would or could.

FOXBORO, Mass. - The New England Patriots Alumni Club (NEPAC), announced that more than a dozen former Patriots players are gearing up to host a "Football for You" youth clinic in Worcester on Saturday, May 29 from 12:30-5:00 p.m.

Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more.

Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and is home alone tonight so they are going to seize the opportunity(while she’s still scared) and have him dress up as Satan himself and go to her house late at night and “appear” to her in her bedroom. (Don’t be overly des...

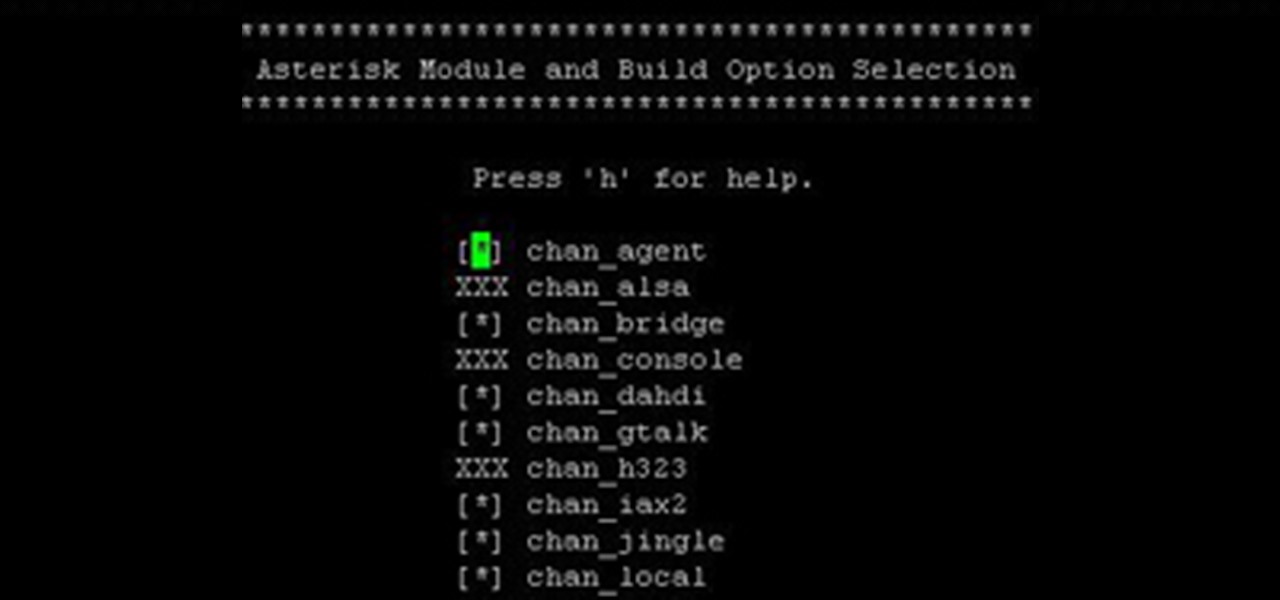
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Want to celebrate New Year's Eve, but haven't a clue how to do so? Maybe some of these New Year's Eve pa

Despite the recent problems with the 1.04 update for PlayStation 3 gamers, Call of Duty: Black Ops remains a juggernaut for Activision in the gaming community, and its sales alone prove it.

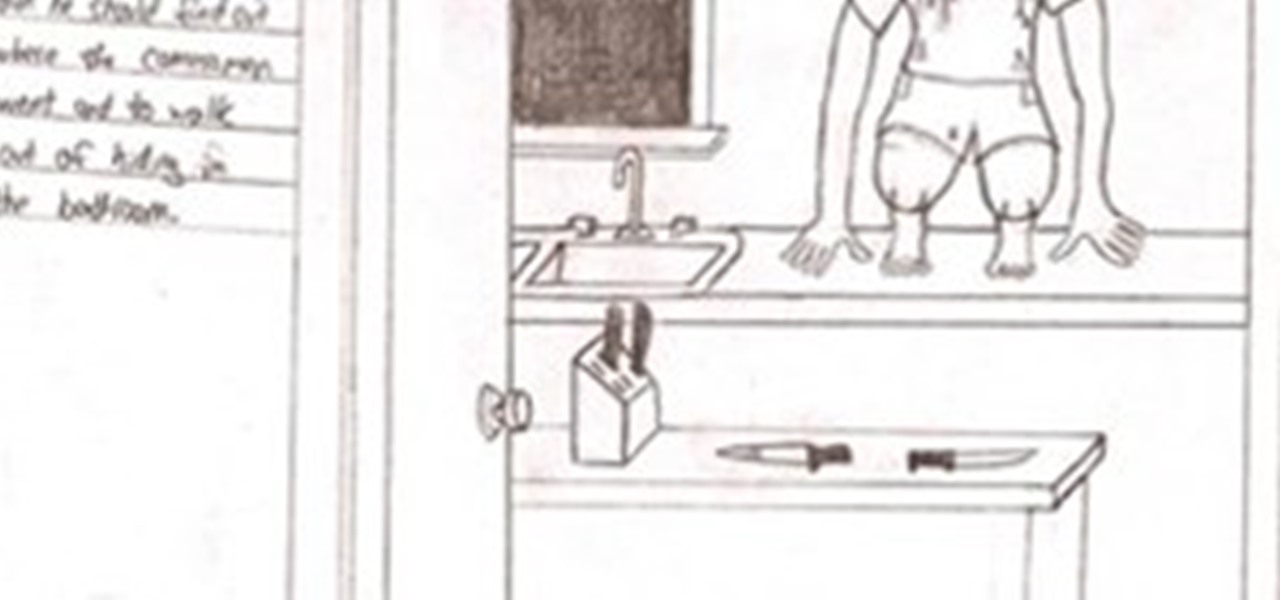
invite someone to a new nice home show them round but first give them chocolate (laxetive) or some sort of greeting of cookies or insist them to use the batroom or check it out if they dont accept, They go and do their buisness or if they were just washing their hands checking the sink while then the host leaves and locks the door and they cant get out and say hold on i might have to fix the door. but he floor in the bathroom is not connected to the house and the walls fall down exposing the,...

How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this tutorial helps you learn to use uTorrent.

Posted with permission via HereComeTheYanks.com

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...