Master Chief, the star of the Halo franchise before it's most recent iterations, is one of the most recognizable and beloved protagonists in gaming history, and that's without players ever actually seeing his body through his inconic and intimidating armor. If you want to dress up as Master Chief for a Halloween costume, film, or other purpose, watch this video to learn how to make your own DIY Master Chief armor for cheap.

There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to determine what model of drive you have. It is very detailed, and should have you well on your way to hacking you beloved XBox 360 and maximizing its potential.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Although pasta is a remarkably simple dish, I find it to be one of the most aesthetically appealing foods. The noodles—especially thicker iterations, like linguine and fettuccine—are graceful and luxurious. Add in some sauce coating the noodles, and a sprinkle of Parmesan or a drizzle of olive oil, and pasta single-handedly reminds us of a basic tenet of cooking: sometimes keeping it simple is the perfect way to go.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

The original iterations of the Terminator film franchise have served as the inspiration (via the heads-up display of the T-800) for future augmented reality dreams, so it is fitting that the current crop of AR gives the latest installment in the series a promotional boost.

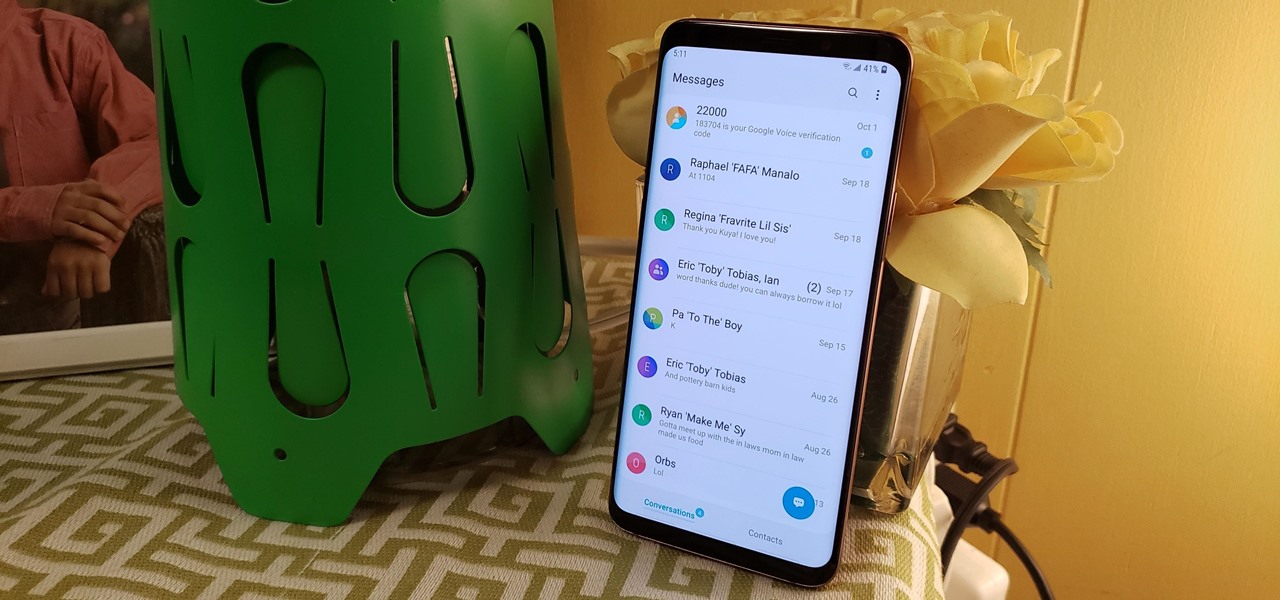
Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

With numerous insider reports, patent awards, acquisitions, and hires over the past few years, augmented reality smartglasses from Apple appear to be an inevitability.

Not all remakes of video game classics turn out well, but a new augmented reality take on Super Mario is likely to draw in fans of the Nintendo hit.

Instagram Direct is fast becoming the end-all-be-all messaging app, and it just added some incredibly convenient features that should make it a bit more practical. These new additions have a clear purpose: To help Instagram Direct grow its base and take on more feature-rich messengers like Snapchat or WhatsApp.

Australia is looking to the future and finding driverless cars and other autonomous vehicles to be a top priority. Spacial Source reports that the state government has put AU$10 million into their Future Mobility Land Fund "to drive local development of autonomous vehicle technology."

Computer cables tangle and get in the way, but Mobile Accessory Project hopes to solve that with CONNEX, a flat cable shaped like a credit card which expands up to 1.5 feet.

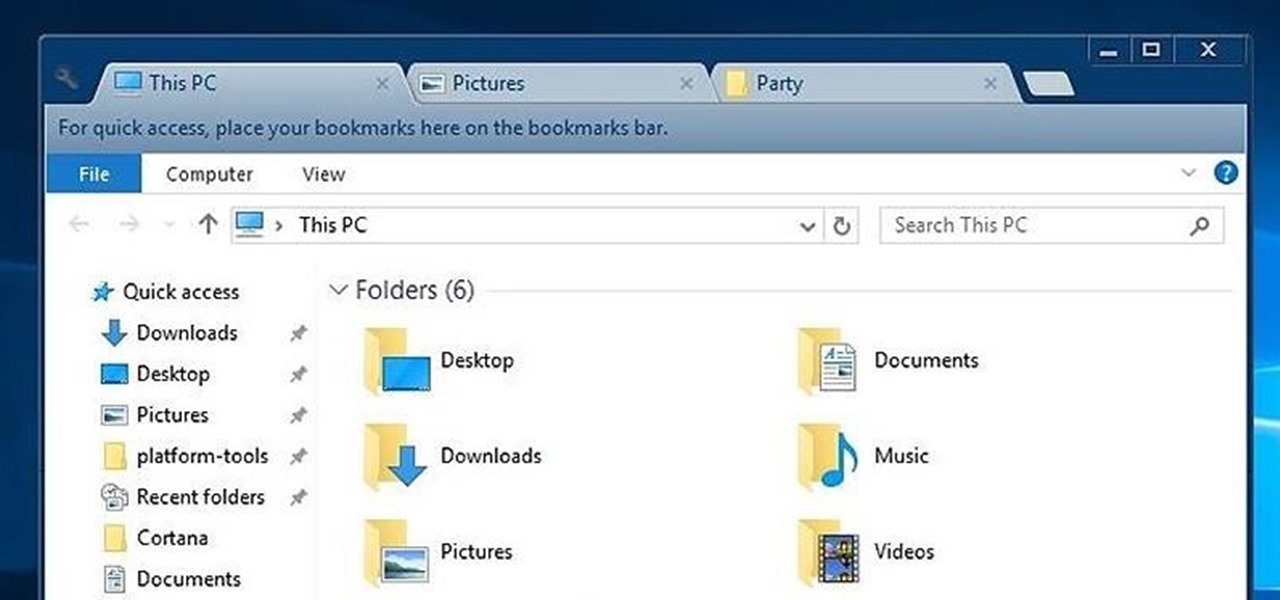
While Windows 10's new File Explorer is just as, if not more, useful as it was in previous iterations of Windows, it could definitely still be better. Two features that would greatly improve File Explorer are tabbed results and a customizable user interface, similar to how they are in Google Chrome.

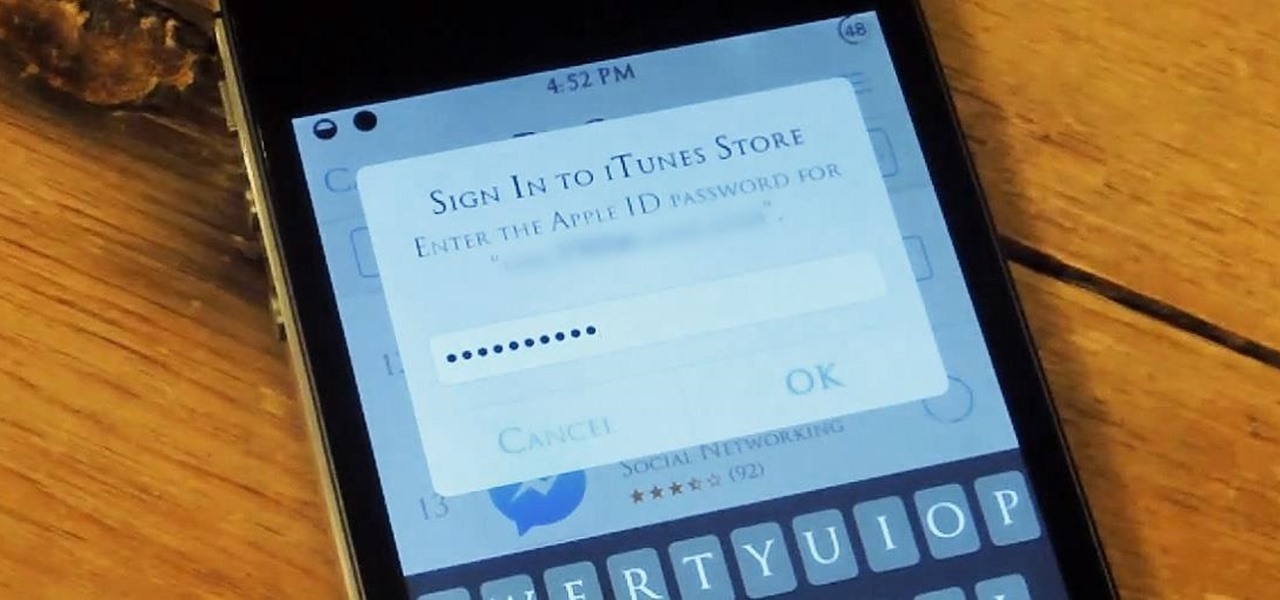
I hate typing in my password every time I want to install an application on my iPhone. My fat fingers make it so that I rarely get it correct the first time. If you're like my mom, you might not even remember it. Keyboard shortcuts are not a viable option either, since they are disabled for passwords.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

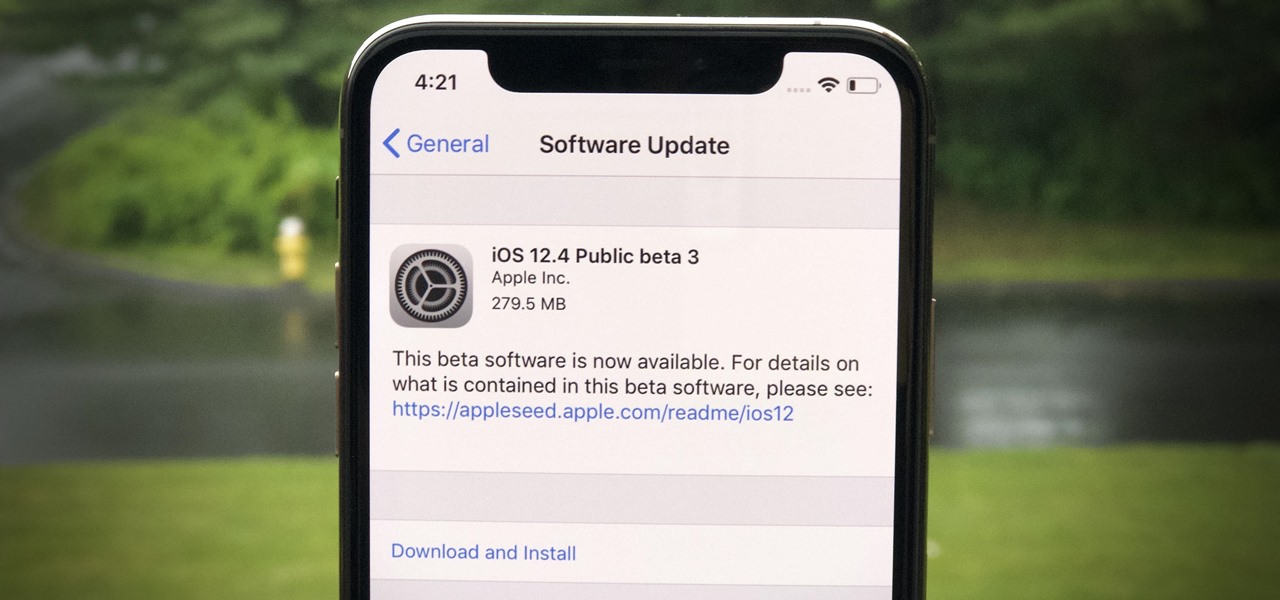
Apple released the third public beta for iOS 12.4 on the afternoon of May 28. The update arrives roughly three hours after Apple published 12.4's third developer beta, and eight days after 12.4 public beta 2. At this time, it seems beta 3 is a minor update for 12.4, which itself is a small upgrade to iOS 12 as a whole. We expect iOS 12.4's shining feature to be Apple Card support.

On Thursday, Epic Games released Unreal Engine 4.20, which finally includes support for the latest iterations of ARKit and ARCore, as well as Magic Leap One early access.

Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

Digital imaging company OmniVision Technologies and the Hong Kong Applied Science and Technology Research Institute Company Limited (ASTRI) entered the CES fray this week with a new reference design for an augmented reality headset capable of 60 degrees field of view (FoV).

For all of its drama, Uber's driverless program has states like Arizona excited for the future of self-driving vehicles. But it's not Arizona alone that supports the driverless craze; the Illinois House of Representatives will hear a bill that would allow driverless cars on the road with or without human operators.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

On the whole, Windows 10 is vastly different than its predecessors, but there's not any one big change that distinguishes it from Windows 7 or 8. On the contrary, it's a series of small tweaks and optimizations that makes this version such a departure from previous iterations.

If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basics."

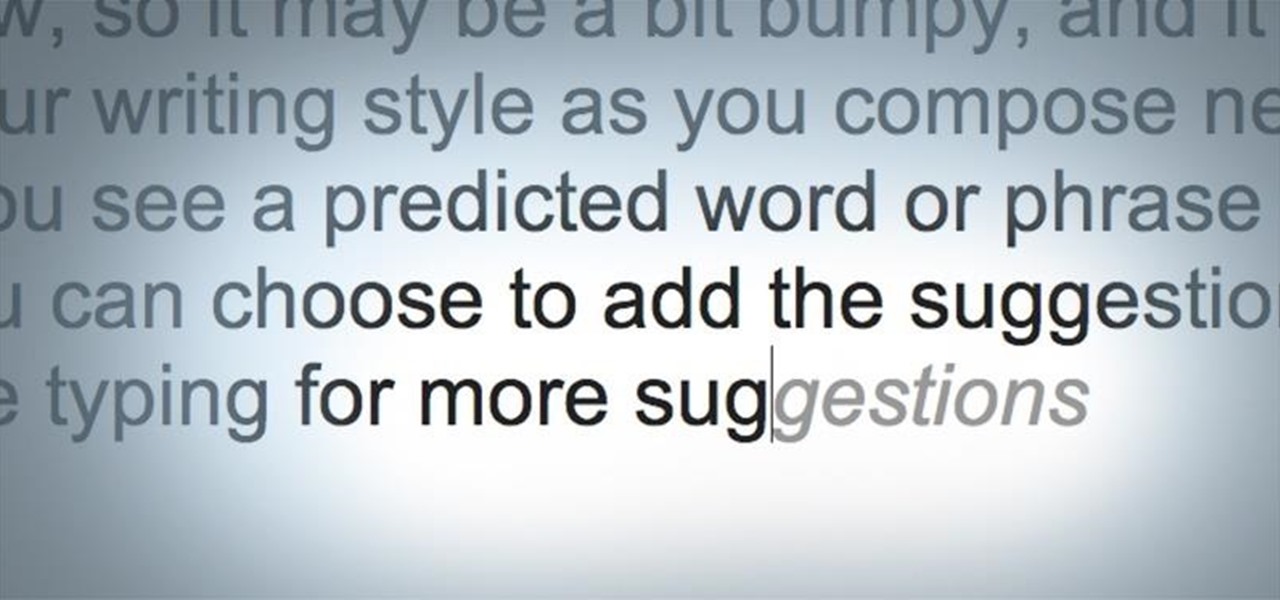
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

It's been over three months since iOS 7.1 came out, but your wait for jailbreak is now over. If you're still running iOS 7.0 iterations to maintain your jailbreak, you can now finally update to the latest and greatest thanks to a Chinese team of developers, who recently released their untethered jailbreak for Apple devices running iOS 7.1, 7.1.1, and even 7.1.2.

One draw that Samsung's Galaxy S line has had over the Google Nexus 4 and 5 and the HTC One (though the M8 appears to be following suit) is expandable storage. Pop a microSD card into the slot and you have extra storage for music, photos, and even apps themselves in some cases.

At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

One of our favorite email apps, Edison Mail, just got even better. In versions 1.17.0 (iOS) and 1.12.0 (Android), the app introduced a new Assistant, a powerful tool that makes organizing travel, packages, entertainment, bills, calendar, and more a breeze over email. The best part? You can customize it to your liking, so the Assistant works precisely as you need it to.

After several iterations of the product, Snap is focused on making sure the world knows that its smartglasses can be fashionable.

While Magic Leap has remained mostly silent regarding its plans for its Magic Leap One successor, the software team continues to makes strides with improvements to the device's Lumin OS and SDK.

Almost half a year after we broke the story about the demise of Meta Company, there's good news for fans of the augmented reality startup — a rebirth is at hand.

If you're not impressed with the current crop of AR content, and you're worried this may put a damper on the industry's growth, these stories should give you cause for some optimism.

If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up.

Both the Galaxy S8 and Galaxy Note 8 have Oreo beta software available in the wild at this point. We devoted a number of articles to covering what's new in Oreo and went into detail about the bugs and hiccups on both the S8 and the Note 8. Still, many people are left wondering — what's the difference between the Oreo builds on these two phones?