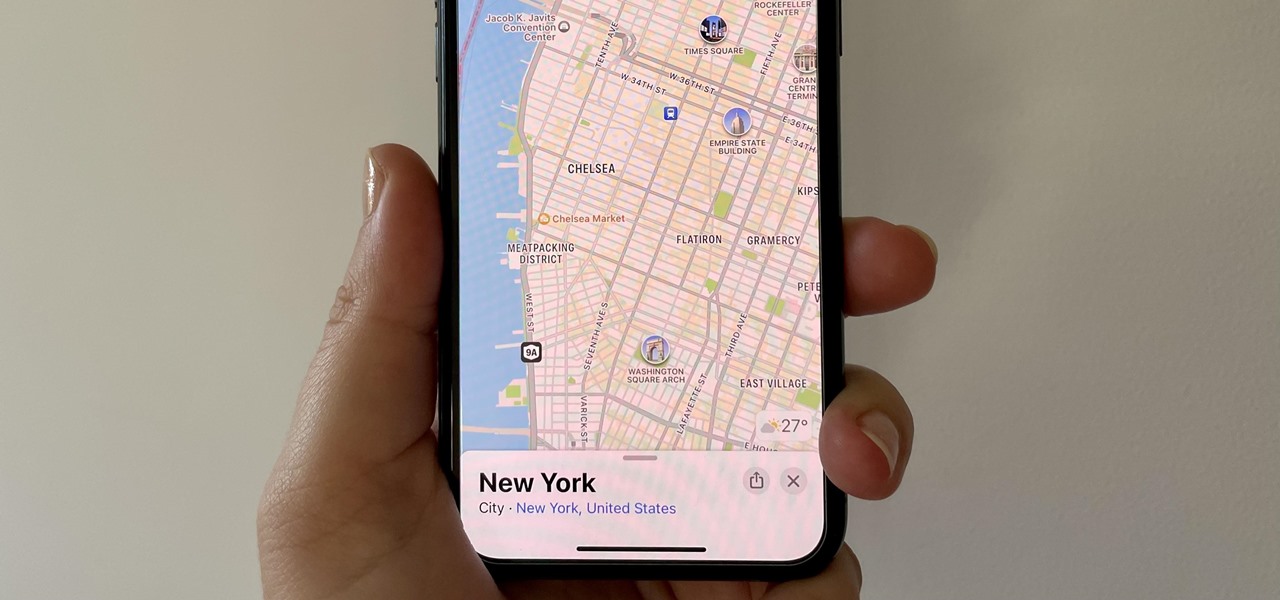
While the Maps app hasn't received as big an update in iOS 16 as Books, Messages, Photos, and Weather did, there are still quite a few exciting new features to enjoy on your iPhone.

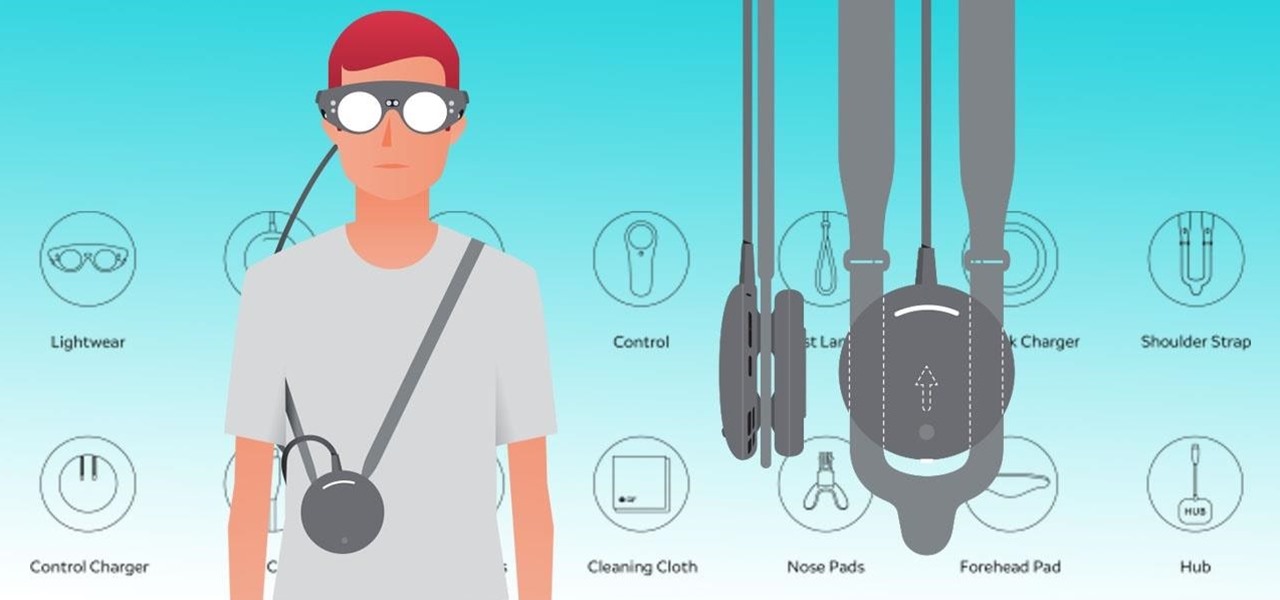
From the front lines of mainstreaming augmented reality smartglasses comes the latest update from Snap and its Spectacles wearable.

After a postponement of the Summer Olympics for a year due to the COVID-19 pandemic, Tokyo is set to host the games this summer, despite a surge in cases in the city.

The remake of the Warner Bros. classic animation meets live-action movie Space Jam, this time starring LeBron James instead of Michael Jordan, hits theaters today.

If you thought Snap's Spectacles were limited to a couple of demos, you haven't been paying attention.
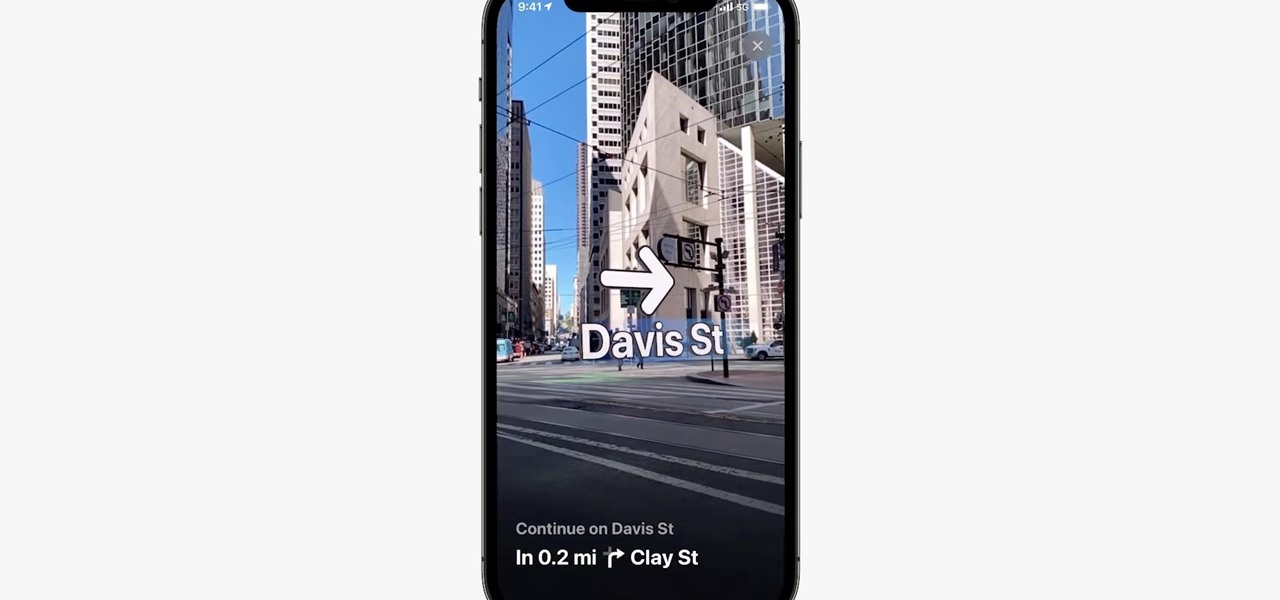
Mobile augmented reality for iOS typically comes through apps via ARKit, but Apple is borrowing a few pages from Google's playbook and bringing AR directly to iOS 15.

Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio.

Apple's big iOS 14.5 update adds over 60 new features and changes to your iPhone, some of which are upgrades that audiophiles and even casual music listeners can appreciate. Whether you subscribe to the Apple Music streaming service or simply use the Music app for your own library of tunes, iOS 14.5 has a few things you should know about.

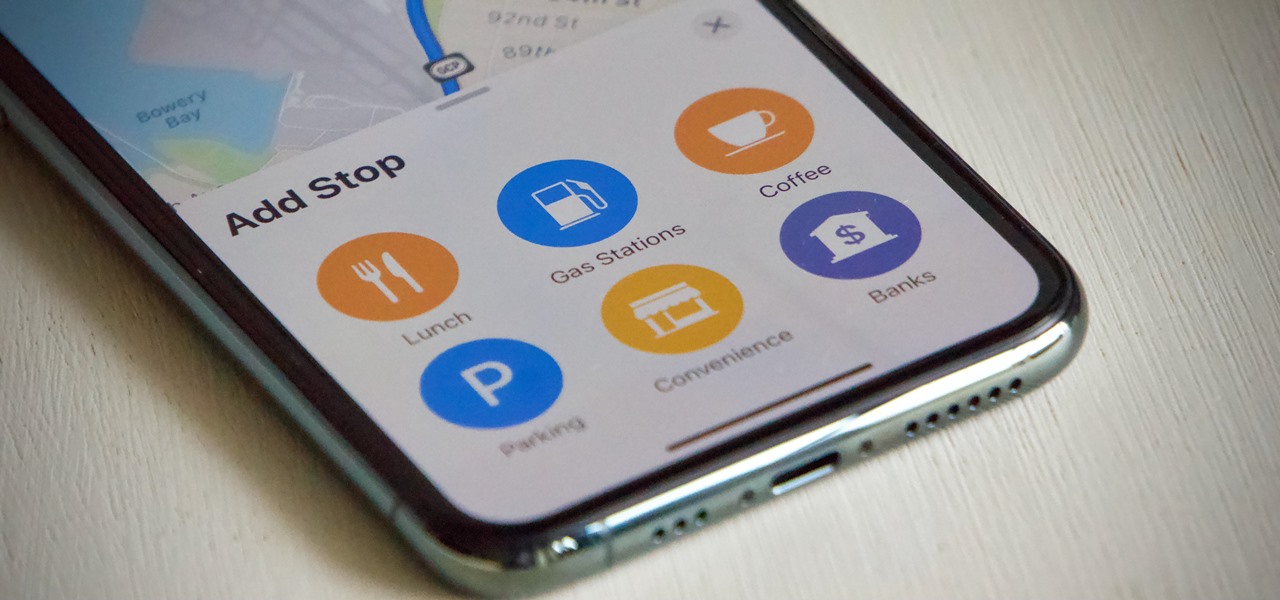
If you rely on Apple Maps to get around over other navigation apps, there's a lot you can do. Look Around lets you tour cities up close, restaurant reservations make dining less frustrating, and 3D view gives a new perspective of a neighborhood. While there are many more where that came from, iOS 14.5 just added six new features and changes you need to know about.

The year 2020 sparked a trend of people moving out of big cities, with some opting to buy mobile homes and vans to travel rather than be cooped up in a tiny apartment during quarantine.

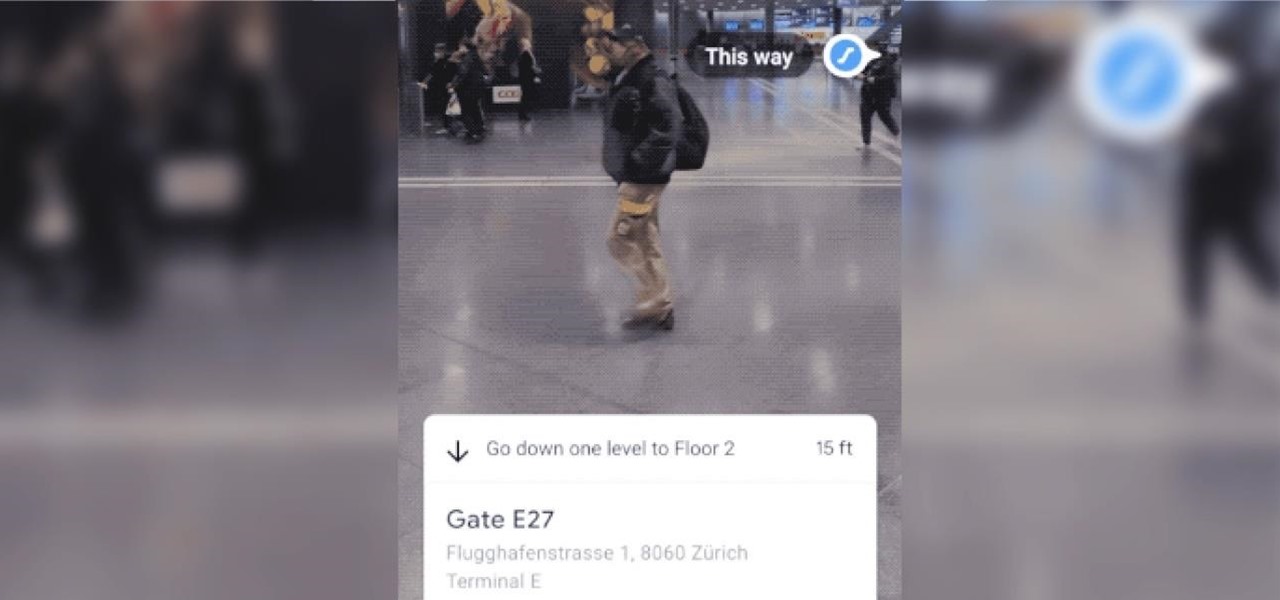
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

Good time-lapse videos capture cities, nature, and other long-running events in a way normal photos and videos simply can't. Your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max can make time-lapses look even better, thanks to Night mode. But it isn't exactly intuitive or even clear on how to enable the feature since, unlike with Video mode, you won't find a Night mode icon to use.

Sure, you could leave a random monolith in Utah and get some notoriety for your street art. Or, you can let others put your art anywhere they'd like with augmented reality so they can appreciate it where they are.

Last year this guy made his own smartwatch from scratch, so in 2020, naturally, he decided to give making smartglasses a try. And it worked!

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

5G is here. Well, not everywhere. All three wireless carriers have turned on their 5G networks, but only in select markets. Like 4G, each carrier is doing things a bit differently, which means your 5G experience will not be the same across the board.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that the barrier to entry is relatively low, so even if you're not a celebrity or media luminary, you can still get your voice out there by starting a podcast.

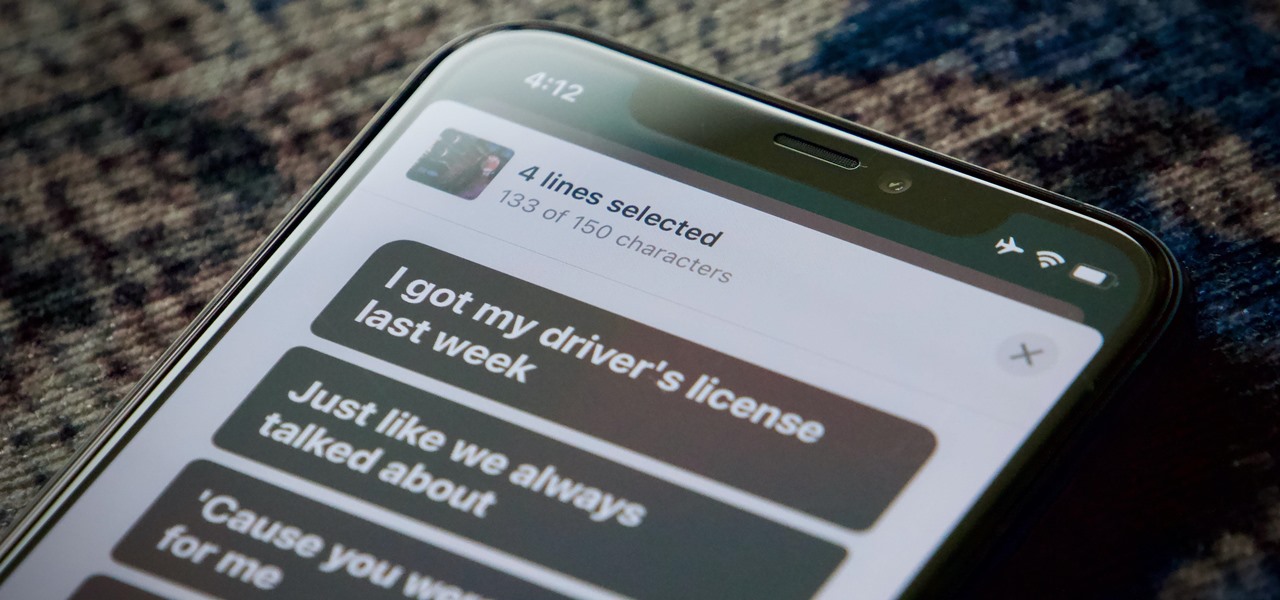
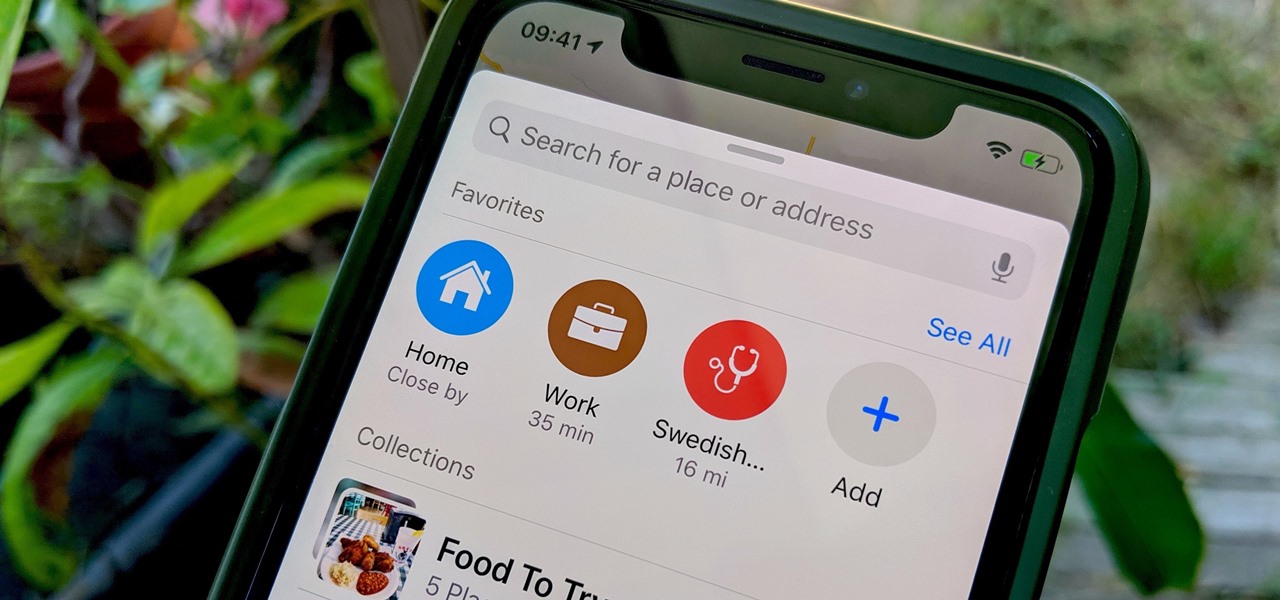
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

On Yelp, you have the option to check in to a business you're visiting. For you, broadcasting who you're with and where you're at is fun for social purposes, but for business owners, you're basically giving them free publicity. Well, almost free publicity. Since there's incentive to get you to check in, some businesses reward customers with special deals, such as 20% off your first visit.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

So while it is the weekend of San Diego Comic-Con, and it should not be a complete surprise — without a word of warning hitting my feed — the trailer for the upcoming film, Ready Player One was released today. And wow it looks amazing.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Crazy Taxi continues to be a favorite among gamers of all ages, from those who played the game in late-'90s arcades to those who discovered the game later on consoles. This weekend, Sega announced their mobile version of Crazy Taxi would now be available for free. What a time to be alive. So does the arcade classic still hold up in 2017? Let's find out.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?