When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.
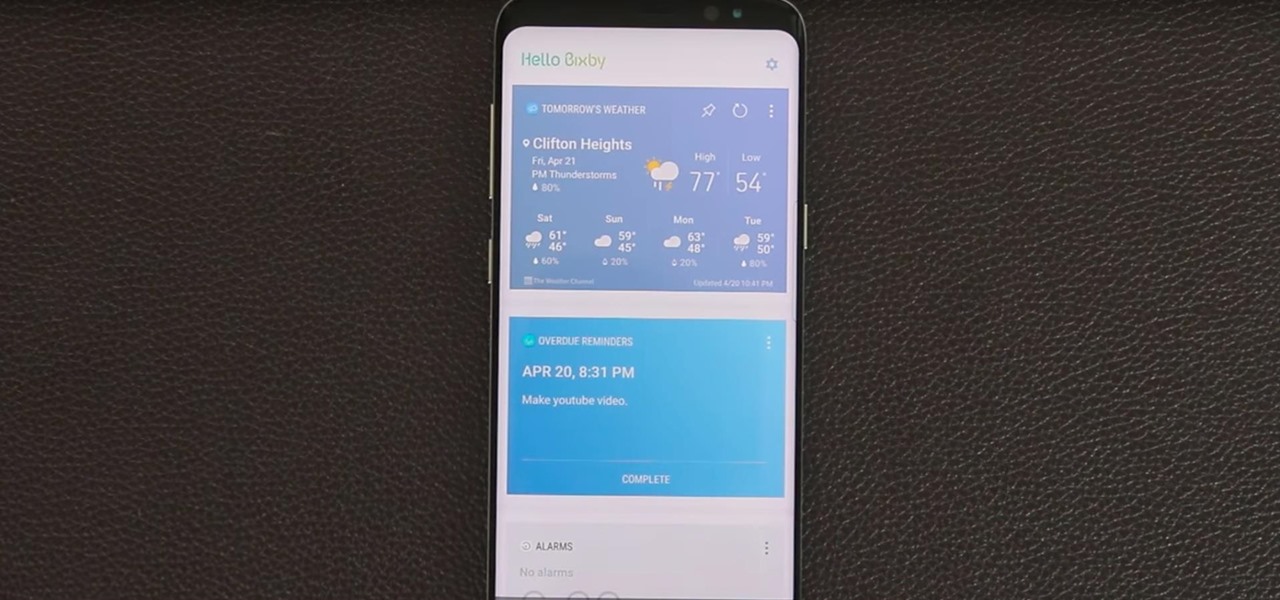
Bixby — Samsung's voice-activated digital assistant — has been delayed again because the software still can't recognize English. Although Samsung claims Bixby can execute 15,000 tasks, it appears it's inability to master English is a major obstacle that's preventing its full release in the United States.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Learn one of the world's most popular games. It's actually good exercise, too! Step 1: Decide who goes first

The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work with the home screen and lock screen widget panels on iPhone, iPad, and iPod touch.

It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

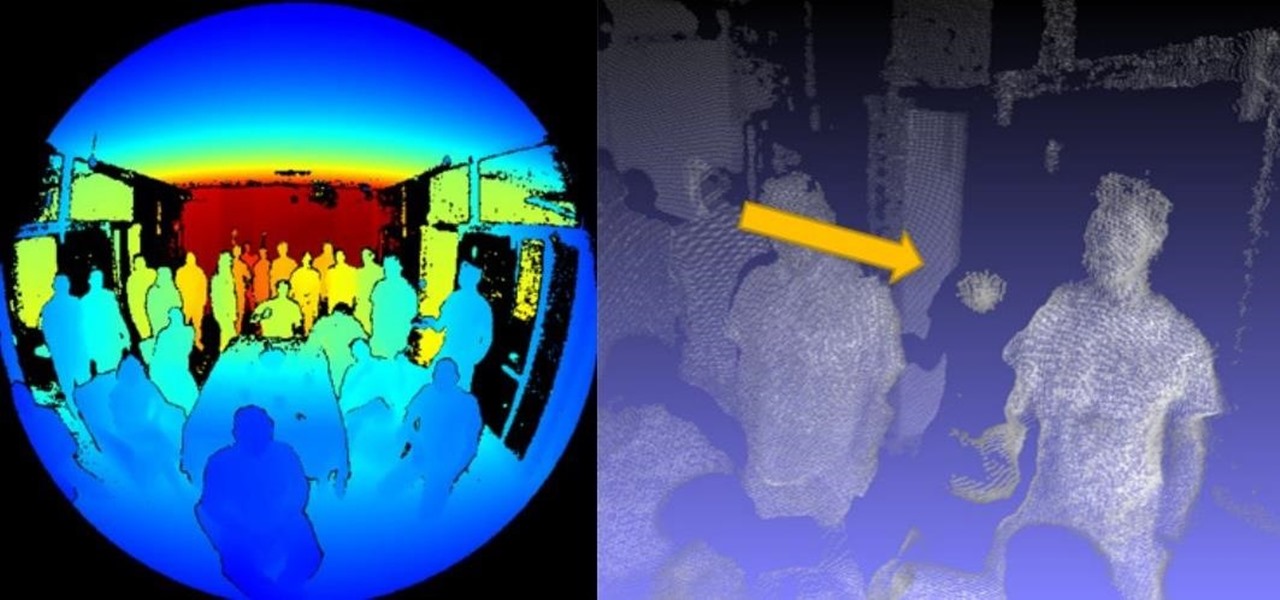
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.

There may be many third-party file managers for Android to choose from, but until now, Google offered no proprietary option. Enter 'Files Go,' which, while initially anticipated for December, is now available for you to try.

Beer pong is a classic game created by college kids to drink and have a good time. However, the process of setting it up is messy and takes a while. Luckily, a demo has introduced an app coming soon where you can play an augmented reality version of beer pong using Apple's ARKit.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Group chats can get annoying real quick if the people in them are sending rapid-fire texts without hesitation, especially if none of them are any interest to you specifically. Luckily, it's easy to mute notifications for specific message threads. You can even leave a group chat if everyone is using iMessages, but that could lead to you missing an important message.

The following video demonstrates and explains a classic physics experiment called a vacuum cannon. Typically these cannons are made on a much smaller scale to fire ping pong balls, but I wanted to keep things interesting with this 4" diameter monster.

Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.

If you played with K'Nex as a kid (or still do), you know that it can take a lot of those tiny little pieces to build something. Just imagine how many it must have taken to make this full-sized, fully functional, coin-operated skeeball machine with a mechanical score counter. Instructables user Shadowman39 (aka Kyle) spent an entire year building this masterpiece. It's the same size as the ones you see in arcades, and it's coin operated, too. But don't try to feed it your pennies, it knows th...

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

There are more ways to finding your missing iPhone than using Apple's own "Find My iPhone" tool in iCloud. If you just need help tracking down your iPhone in your home or at a friend's house, Find My iPhone isn't necessarily the most convenient thing to do when you've got these other options to try out first.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Ralph Waldo Emerson once observed that "the seed of science" was "wonder," and taking a look at this nine-layer liquid tower from Steve Spangler's Sick Science! channel, one can't help but do just that — wonder. How is this possible? Is this magic or what?

Google first introduced Google Home, its latest smart product in the works, at the company's I/O conference in May 2016. It will directly compete against Amazon's Echo, which has so far been a success with over 3 million devices sold, and it was even featured as FBI Agent Dom's only real friend in the second season of Mr. Robot. Google may have their work cut out for them, but we're betting Home will knock Echo out of the water. Google Home is a personal assistant with a built-in speaker and ...

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

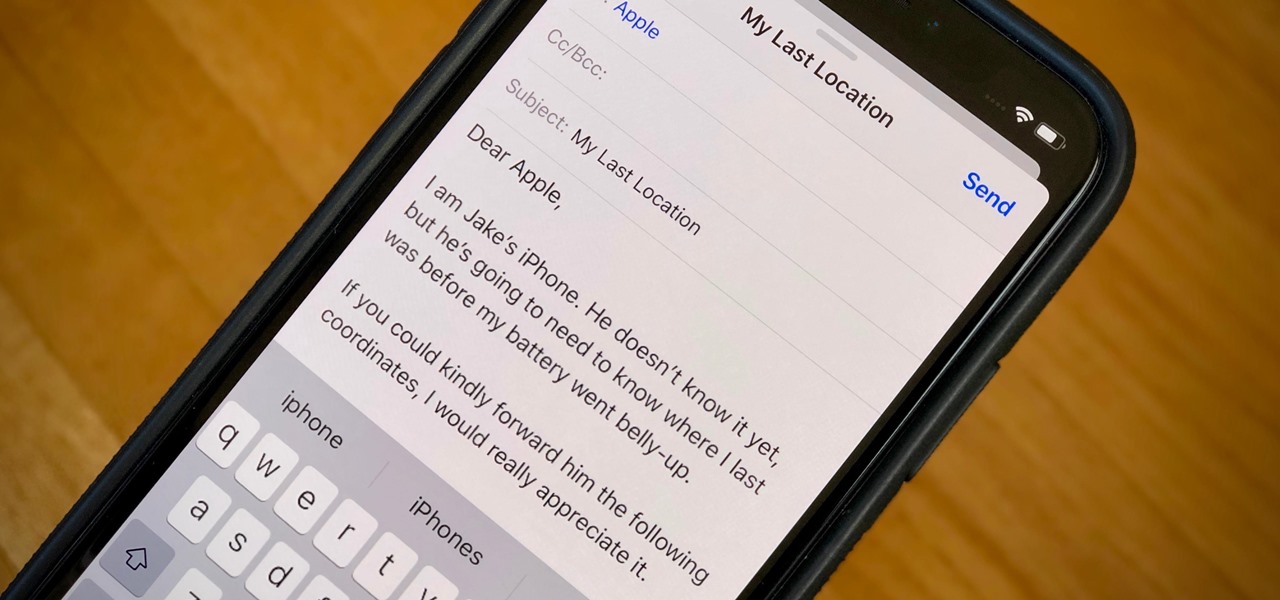
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

This year's NFL playoffs have been nothing short of spectacular. With Super Bowl XLVIII coming up on Sunday, February 2nd, people are already gearing up for another classic showdown between the NFC and AFC, and this time it's the Seattle Seahawks versus the Denver Broncos.

In this online video series, learn judo techniques from 12 time U.S. National Masters Champion Sensei John T. Anderson, as he demonstrates moves such as the compression arm lock, forearm lock, Hadaka Jin rear stranglehold, breakfalling, Juji Gatame cross lock, Kate Te Jume stranglehold, Kisa Katame, straight arm lock, Tai Otosha body throw, passing guard, Ko Uchi Gari major inside reap, leg throw, arm entwining, and Uke Otoshi hand drop.

In this series of educational videos you'll learn how to perform a science experiment using everyday household items that demonstrates Bernoulli's theorem. Expert science instructor Scott Thompson shows you how to use a plastic bottle, ping pong ball, shop vacuum and a golf ball to illustrate the physical force of air pressure on an object. It’s the basic principle of physics that keeps birds and airplanes in the sky.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Another contestant has emerged in the race to deliver a mainstream augmented reality car navigation system, with Silicon Valley-based Phiar picking up $3 million in seed funding to launch its own artificial intelligence-based mobile app by mid-2019.

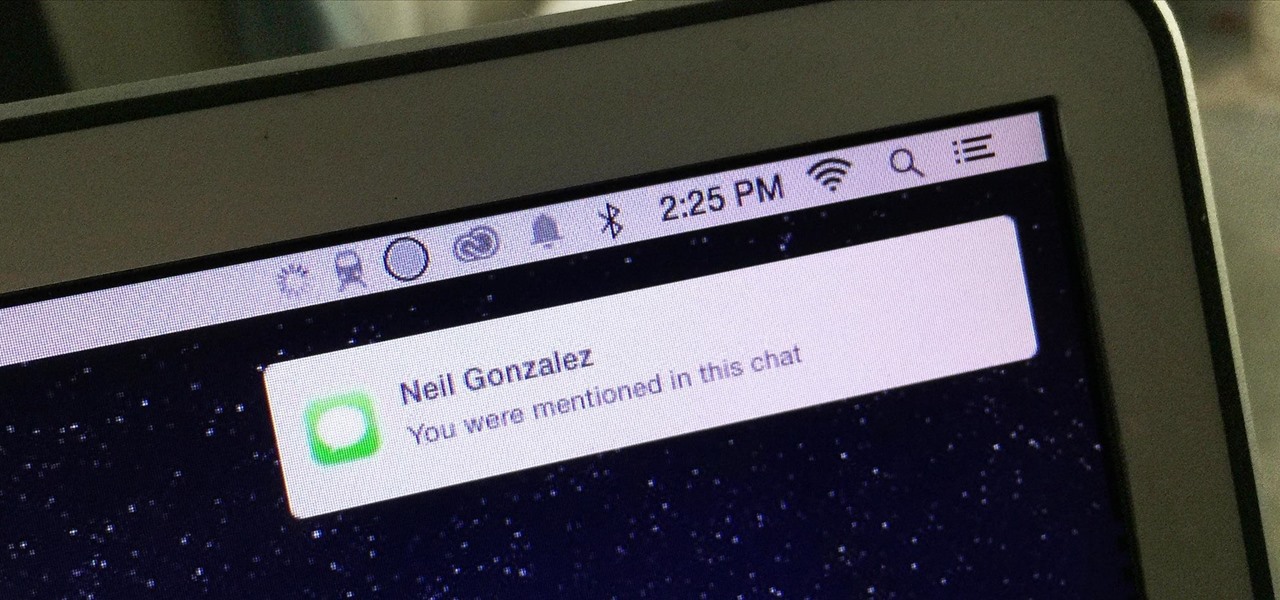
There are few apps or services better than Slack for keeping a team both communicative and productive. But it also makes it difficult to escape your job — after work hours and weekends should be yours, not Slack's. If you want to stop the barrage of notifications and messages on your time off, you should make use of Slack's "Do Not Disturb" and "Away" settings.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

We may not fully appreciate all the important roles wheat plays in our lives until it's gone—or at least, when it's in very short supply. What would a world be like without bread, cakes, cereal, pasta, or wheat beer? If the dire warnings about an impending stem rust fungus come to pass, we may know all too soon.

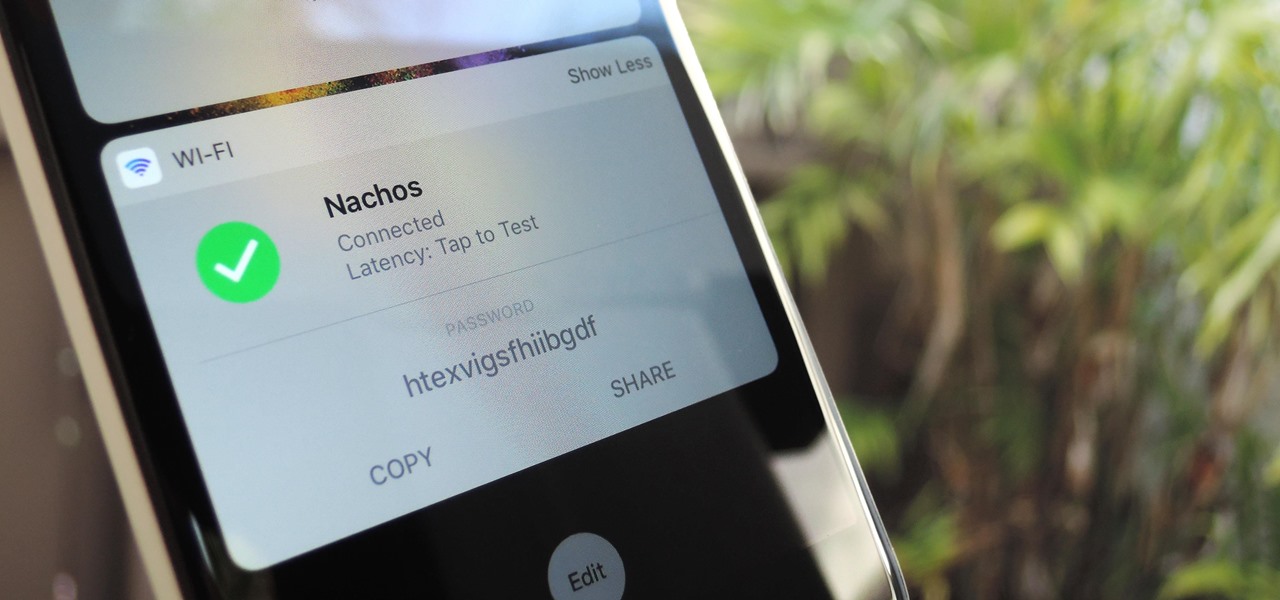
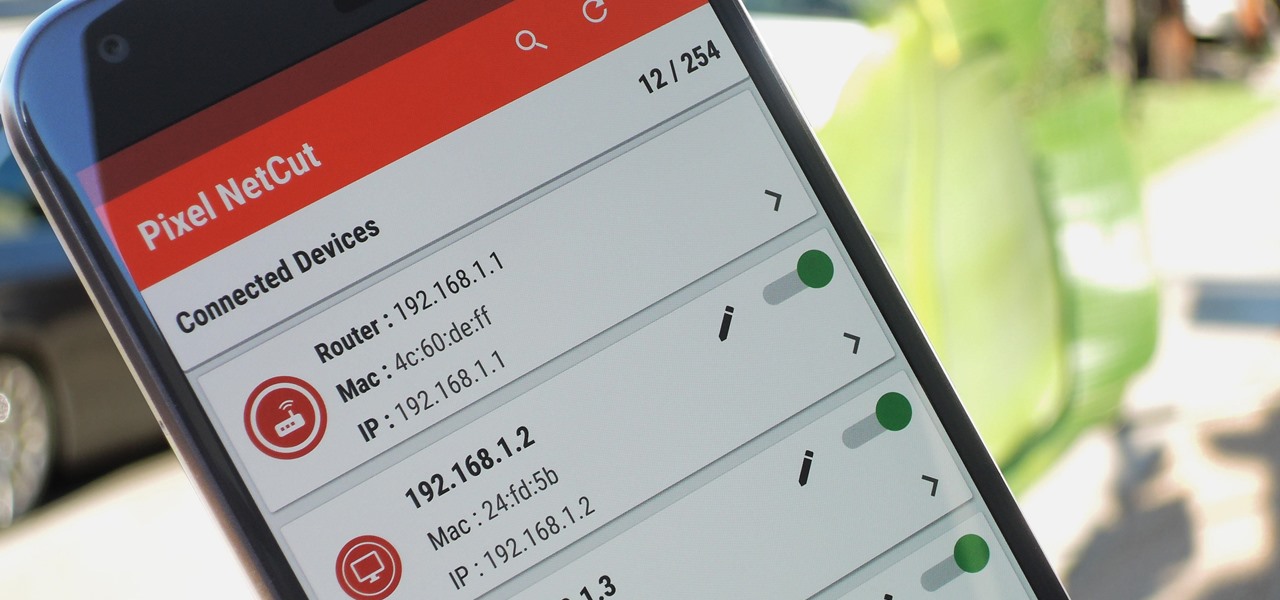
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.