
How To: Choose the right pressure washer
A pressure washer is a great tool for home maintenance, but be careful which one you choose. This hot to video will show you how to choose the best pressure washer for the job.


A pressure washer is a great tool for home maintenance, but be careful which one you choose. This hot to video will show you how to choose the best pressure washer for the job.

This video will teach you how to apply that Bowie inspired glam rock makeup job. Use colorful eyeshadow to make it seem like you're from Mars.

See what to look for in a car's paint job to detect that the car paint has been redone or replaced, uncovering clues about the car's accident history and resale value.

A camp staple. Learn how to make sloppy joes from this very creative filmmaker. We hope he doesn't quit his day job.

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

While most established media brands are satisfied with copying Pokémon GO to jump into augmented reality gaming, at least one property is taking a slightly different approach.
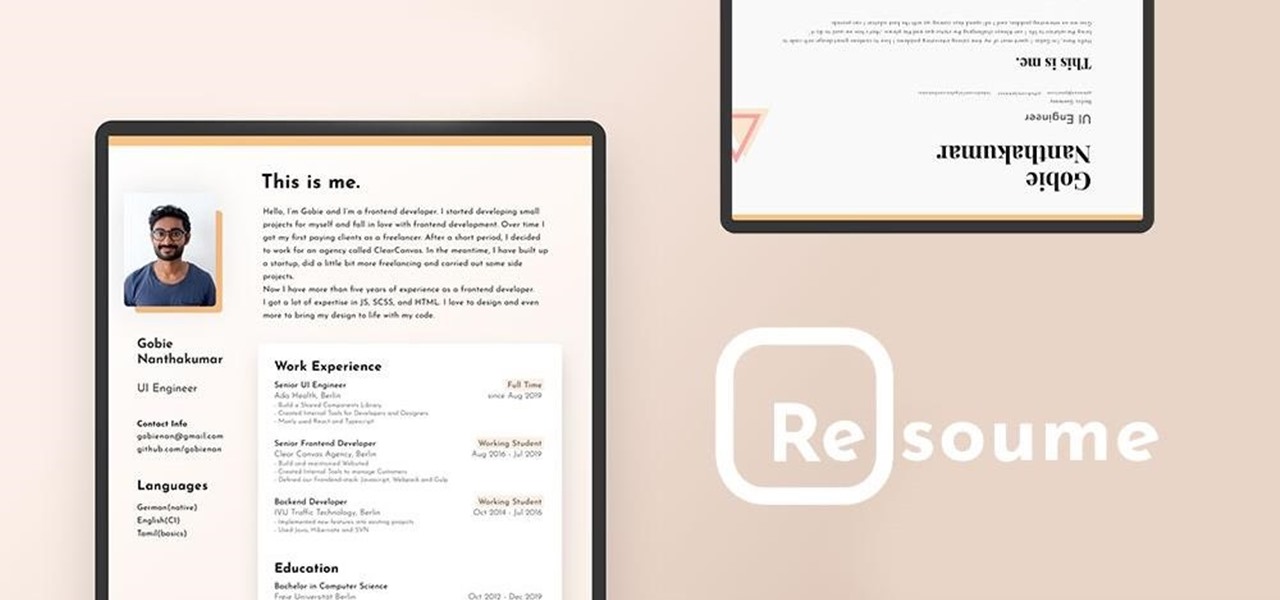
While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.
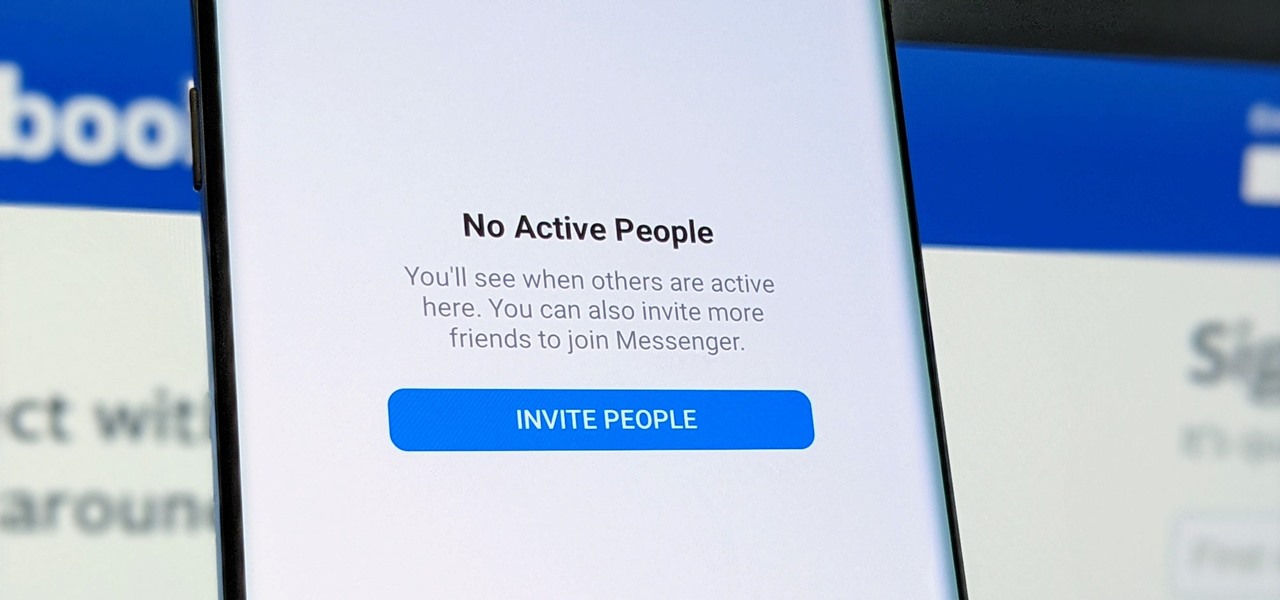
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Despite the cancellation of Mobile World Congress and several high-profile companies pulling out of the upcoming Game Developers Conference, Magic Leap is pushing forward with hosting its own developer conference.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.
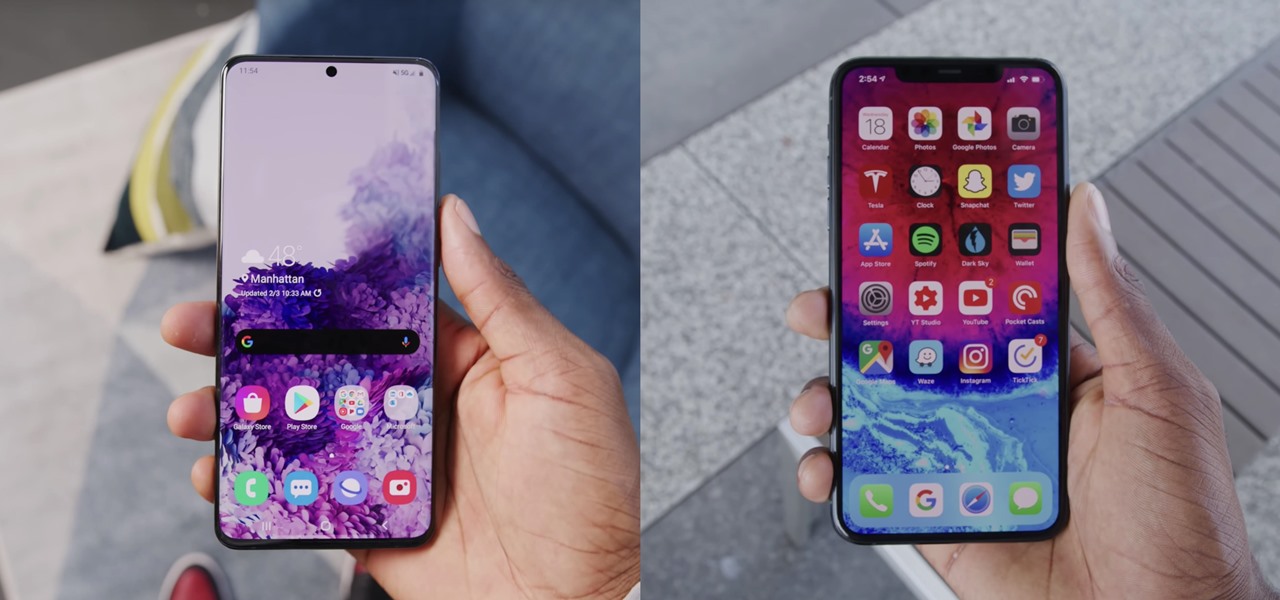
The time to wait for an absolutely killer phone from Samsung is over. They've released a giant of a phone known as the S20 Ultra, and at least on paper, it's a grand slam. But only a few months ago, Apple released its first "Pro" iPhone, and it was giant in its own right. So which is better?

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.

We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future.

With the consumer edition of its Nreal Light headset, scheduled to ship in 2020, Nreal is prepared to bring the entire Android app ecosystem into augmented reality.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.
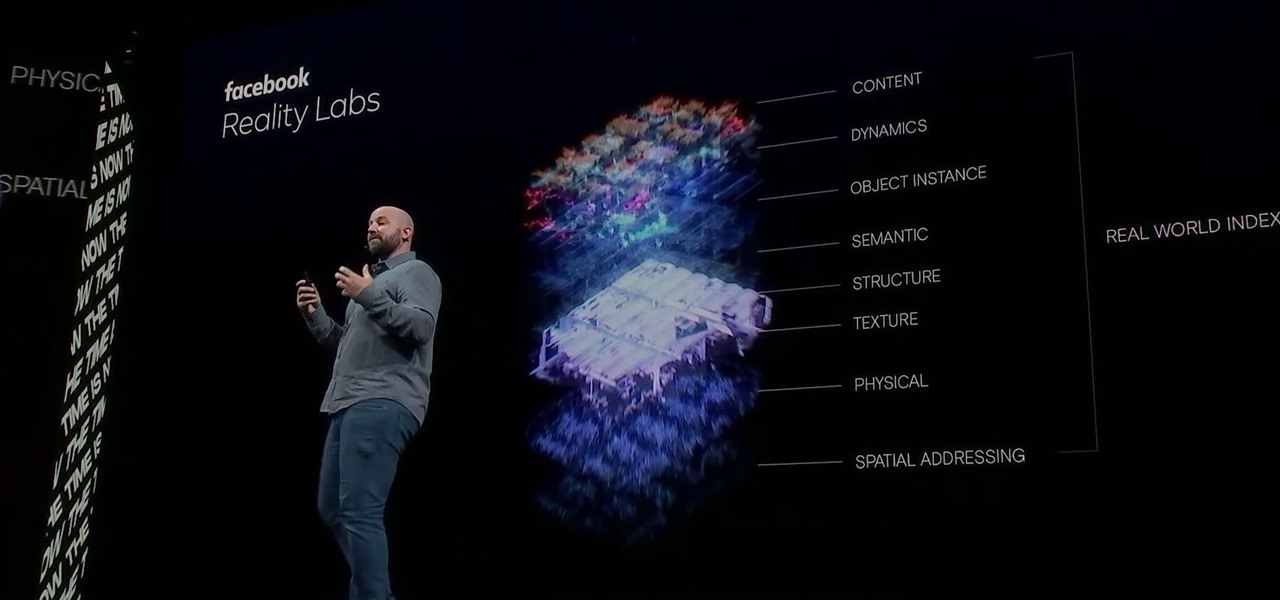
Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

The annual Augmented World Expo (AWE) typically packs the front page of Next Reality with new products and services from companies in the augmented reality industry.

As promised with its teaser from Build 2019, Microsoft has unveiled the details for its augmented reality version of Minecraft for smartphones.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

Tapping on your iPhone's display to pick up an incoming call can be annoying when your hands are wet or dirty. It might even fail to register and cause you to miss your call. If you have a jailbroken iPhone, however, you can get rid of this problem entirely, thanks to a free tweak that lets you instantly pick up calls without having to interact with your phone's screen.

While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.
The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.