Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.
Apple just released the third beta for iOS 11.3 on Tuesday, Feb. 20, which comes exactly two weeks after the release of iOS 11.3 beta 2 that brought battery health data and performance-throttling controls. At first glance, iOS 11.3 beta 3 seems to be mostly under-the-hood improvements, but we'll know more as we dive into it.

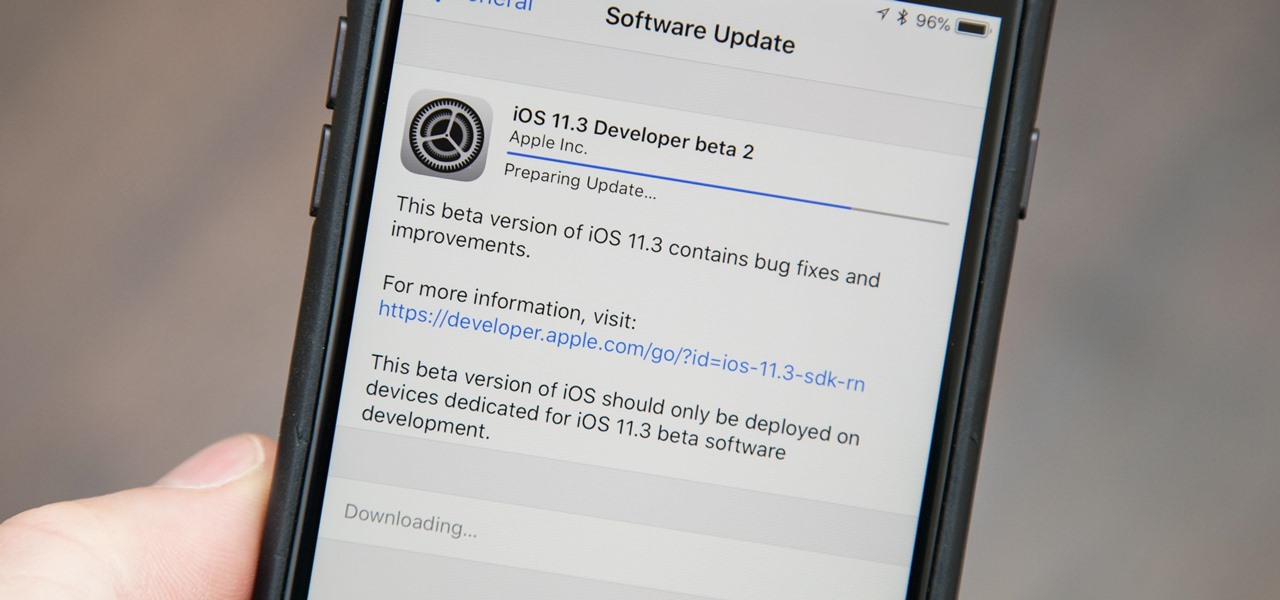
Apple released the second beta for iOS 11.3 on Tuesday, Feb. 6. The update comes two weeks after the original announcement and release of the iOS 11.3 beta, which brought new Animoji, Messages on iCloud, and Apple Music Videos, among other features. One glaring omission was the promised battery health tool, but iOS 11.3 beta 2 just introduced it.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

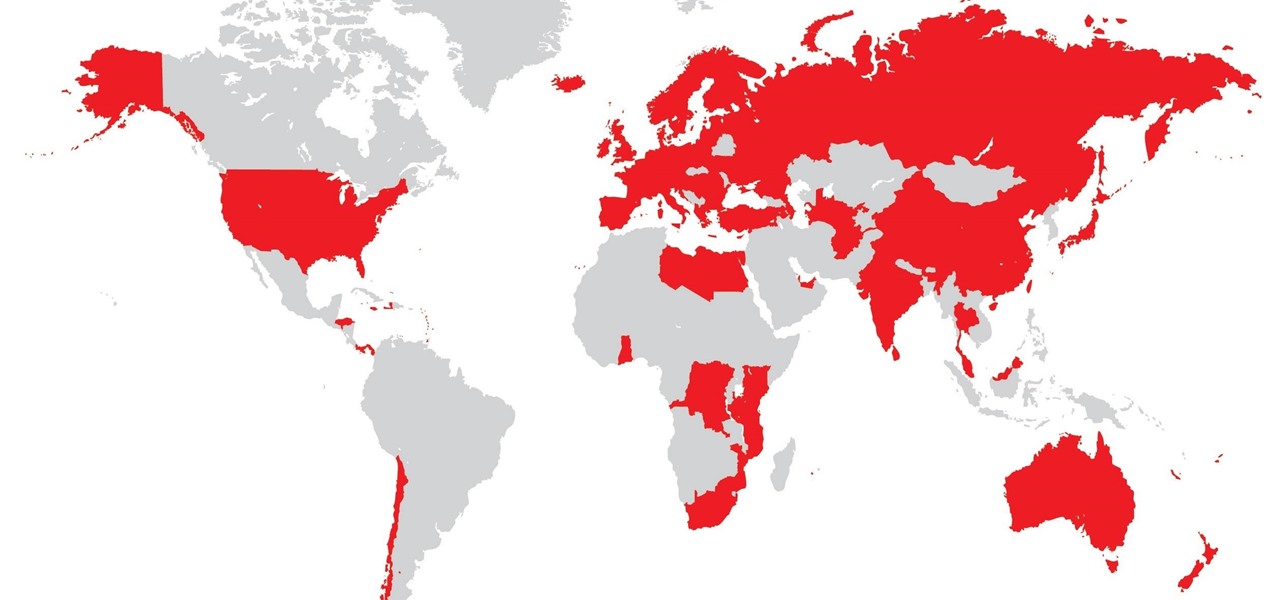
Just days after announcing the launch of two new mixed reality studio facilities, Microsoft is extending its mixed reality reach even further with the announcement that the HoloLens will now be offered in 29 new markets.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

A new survey shows that the majority of companies have an interest in using augmented reality, though adoption remains low. Meanwhile, two companies with support roles in the augmented reality industry are seeing positive financial results.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

While the technology continues to mature, businesses from various industries continue to adopt augmented reality to improve the efficiency of business processes. In this edition of Brief Reality, as conference season continues, we see examples of augmented reality applied to logistics processes and marketing of industrial supplies, as well as the topic of discussion at another trade show.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC filing.

Mercedes-Benz's parent company, Daimler, announced their intention today to put self-driving taxis on the road in three years or less in a partnership with Bosch.

Apple is in the process of developing its own graphics processors for future iPhones, according to recent reports.

Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Welcome to another Handy One Minute Stud Wall Framing Tip! How to frame a stud wall is a reasonably straight forward job to do but knowing a few extra framing tips is always a Bonus! Blocking out your walls to provide somewhere to screw a fixture to is one of those handy tips. You no longer need to look for a stud as you have a solid block to attach to!

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

When you search for a specific location or business with the Google app, a Knowledge Graph card is usually the top result. This card displays a handy mini-map and offers a quick link for directions to the location of your query, but it has one irksome flaw—these links can only be opened by the Google Maps app.

Who says you have to cook on Thanksgiving? If you need a break, have surprise guests in town, or simply don't want to be in the kitchen cooking all day long, never fear: you have options.

In the past few weeks, the internet has been abuzz with nightmarish horror stories of Comcast's questionable decision-making and downright terrible customer service. The central theme of many of these disputes with the nation's largest cable provider is that without evidence, the conglomerate will refuse to acknowledge its mistake and place the burden of proof on the customer.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Video: . Do you find annoying to have to spend 1 hour cooking a delicious brownie to have to taste it? Are you tired of those horrible mug recipes?

Get noticed at your next social function or at work with a different and new way to tie your tie. I will be covering amazing and unique knots as well as traditional knots. If you're a man, and you probably are if you're reading this, the odds that you will one day have to ironically wrap a tie around your neck are really high. Like, sky high. It might be for a job interview or for your own wedding, and you'd do well to put one on at the funeral of anyone over the age of 60.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

Sure, "normal" is cozy and safe, like a glass of warm milk before bed. It gets the job done, but there's no pizzazz, no flair. We wake up, slug back some okay coffee (not good, certainly not great, but just okay), and we're shunted off to a gray cubicle in a gray building. Sure, we can't all be stuntmen and rock stars, but there is a way to inject a little zip into your day.

Do you like candy corn? Do you like vodka? Well, then this candy corn vodka cocktail will be a huge hit at your Halloween party (at least, with you).

Watch as job candidates at a career fair discuss how they set themselves apart from the crowd. This is some great information. You'll learn that dress is important along with a few other tips.