Everyone's faced the dreaded "Tell me about yourself" question in a job interview and it's also probably a common thing to freeze up and not know what to say. In this video courtesy of Denham, learn how NOT to answer this question in an interview and how to get the job you want!

Do you think you're well in your business venture but you can't get clients and don't know why? Perhaps the issue isn't in your work itself, but how you present it. Knowing how to write a great bid letter is a valuable weapon in that cutthroat business world. This video from Freelance Writing will show you how to write a bid letter for a job.

This is a presentation of how to face toughest interview questions. During most of the job interview, the interviewer is trying to find out your capabilities if the job. They want the client to explore why they want to be working here. They know that you want a job. But more specifically they need to know why you want to work in their firm and also your capabilities. So, you must be prepared to answer for this common question for most of the interviews. First of all you should understand why ...
In this video, John Heaney gives advice on how to answer a simple but difficult question during a job interview. If interviewers ask job seekers to tell them about themselves, they can be put on the spot and be unable to even begin to answer the question. Heaney puts this question into perspective from the employer's perspective. For instance, he reminds you to remember that you are applying for a job and your answer should be related to your technical abilities rather than your personal inte...
This video goes over cover letter formats, specifically in Full Block Style. Cover Letters accompany resumes in job applications. They should be sent ahead of the resume. They go over your experience, desires and objectives. The cover letter is important to both employers and employees. A human resources or HR department often receives thousands of letters that it must review before granting a job candidate a job interview or even reading their resume. This is a LIAD Production for World of W...

Any truck driver who breathed a sigh of relief when US Secretary of Commerce Steve Mnuchin recently stated that driverless cars "will not affect jobs in a meaningful way for roughly 50 to 100 years" can go back to being anxious about job security again.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

In this clip, you'll learn how to quickly set a security pattern on an LG Droid Ally Google Android smartphone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started setting up your own security secreen, watch this helpful video guide.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to bypass security wafers when lock picking.

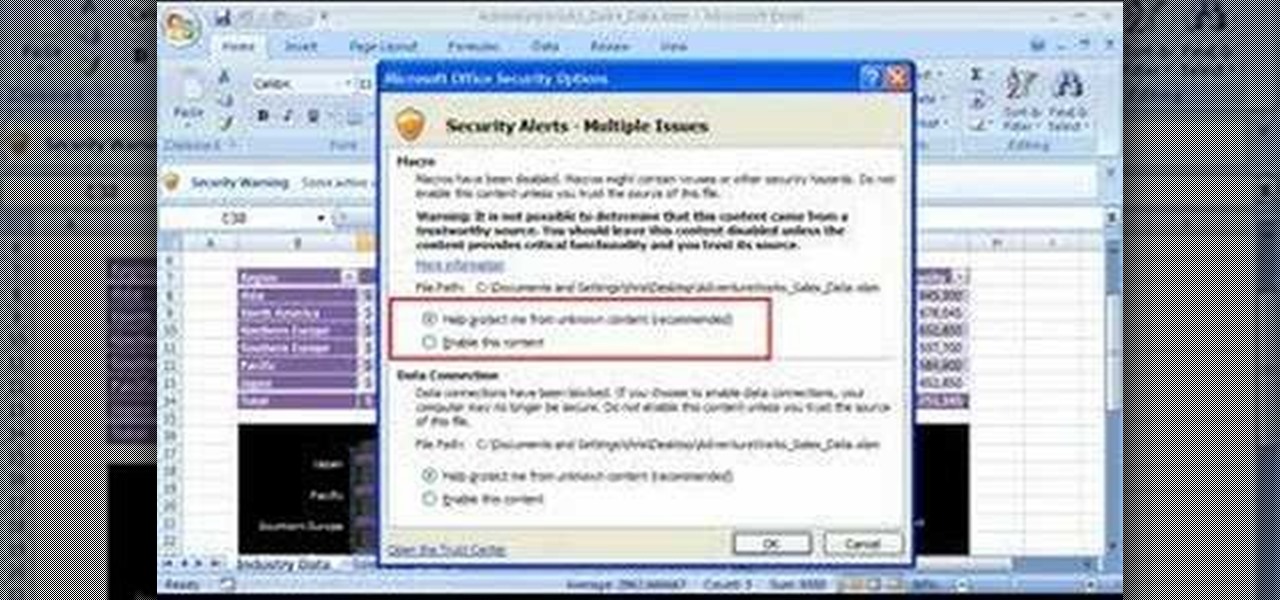
Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

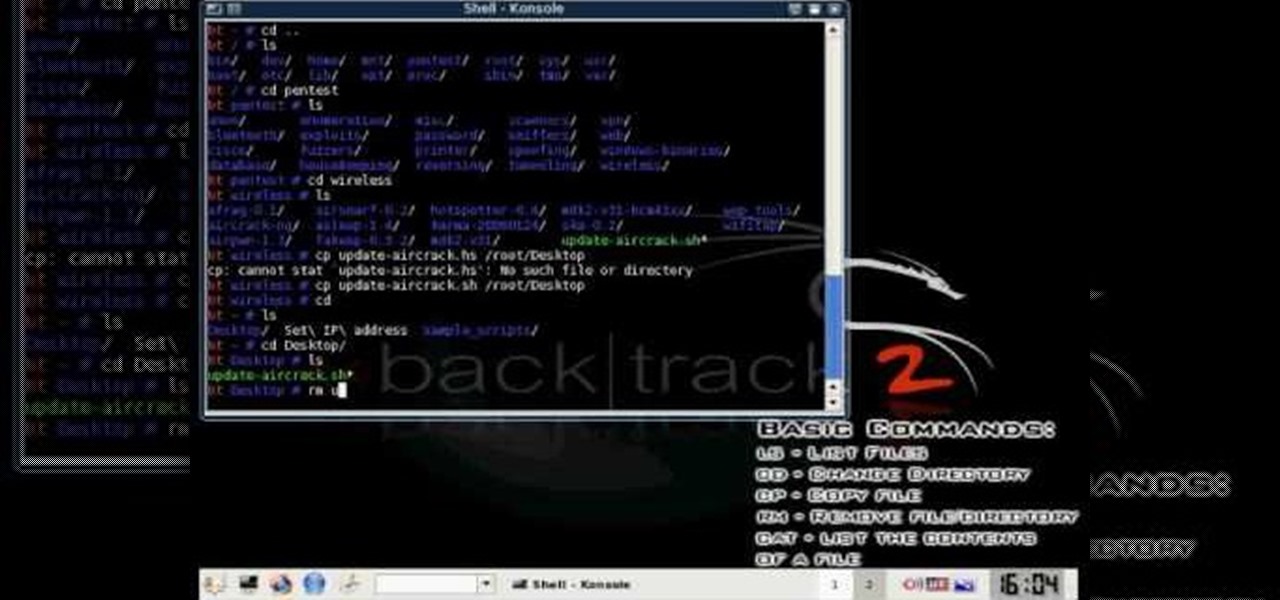
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

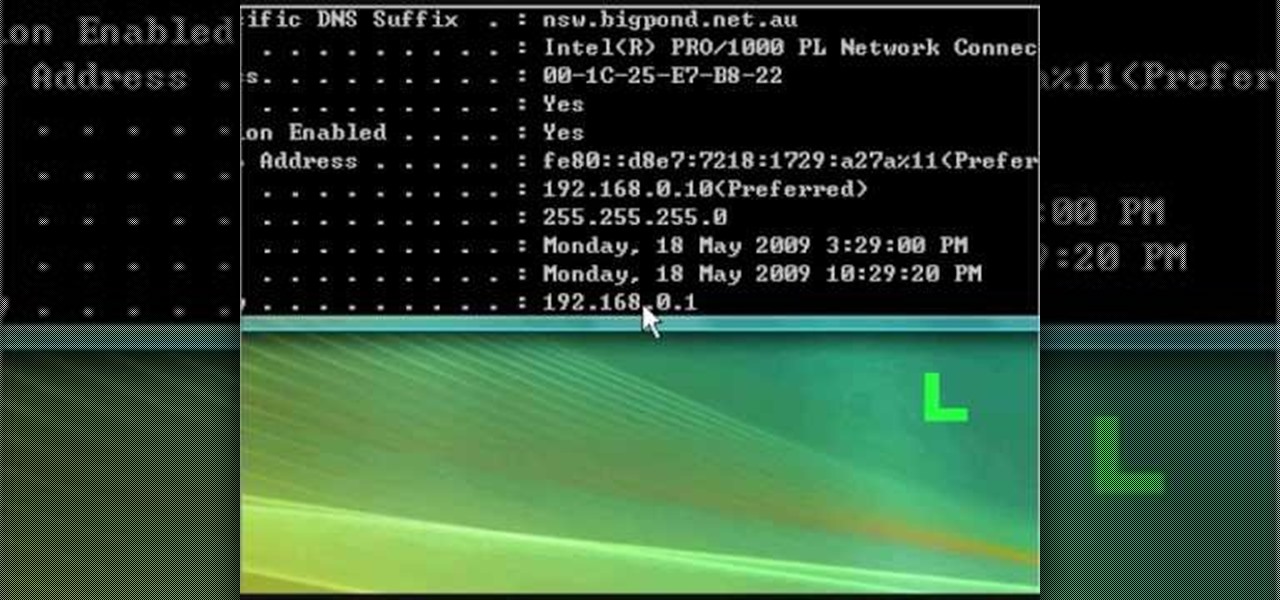
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...

Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would be to turn it off. So in this tutorial, you will learn how to easily change the security settings to INternet Explorer 8. So sit back and enjoy!

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

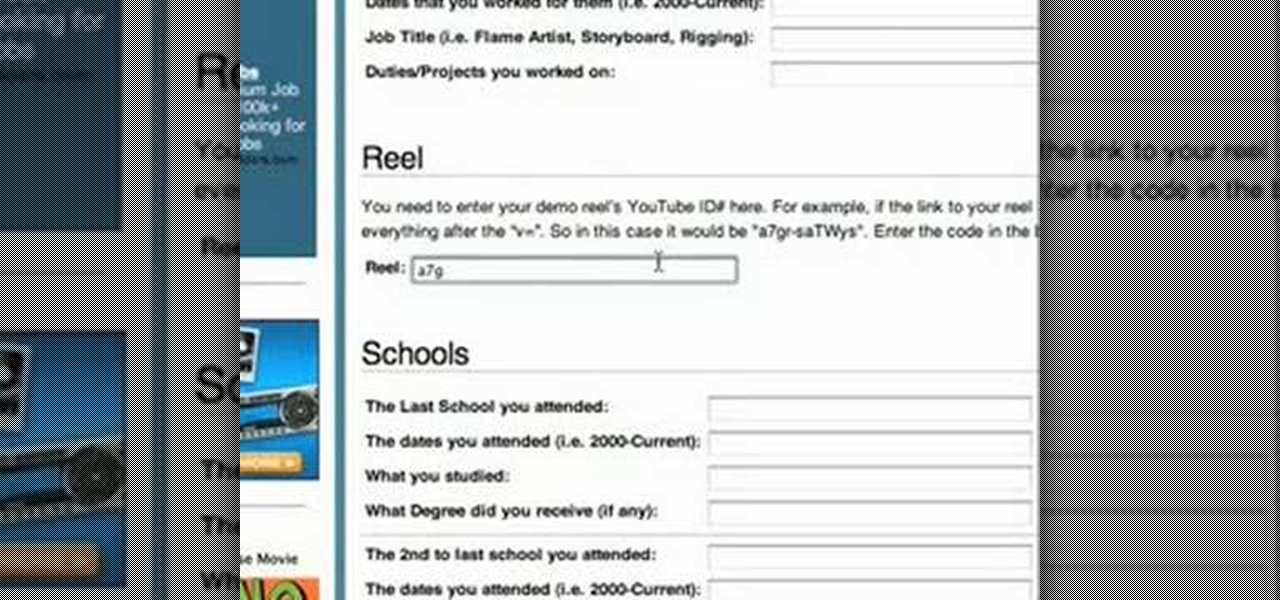
This video teaches the simple steps to make an animation resume at Ani-Jobs. An excellent summary is given below. First click on the Resume cafe tab on the top menu, log in or create an account if you don't have one. Select a suitable category like 2d Artist, click the Storyboard sub-category. Add your name to enter the resume building page and start to input your details. In the reel column give the number that comes after "v e" in the link. Upload your résumé, artwork and your comments, lea...

This video resume-writing tutorial offers a powerful overview of 12 important aspects to consider when preparing your resume. A bad resume won't get you any job interviews, not matter how great your experience. Watch and learn how to put together a quality resume and get that much closer to your dream job.

Testing products for a living is a bit more complicated than it sounds. You Will Need

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need

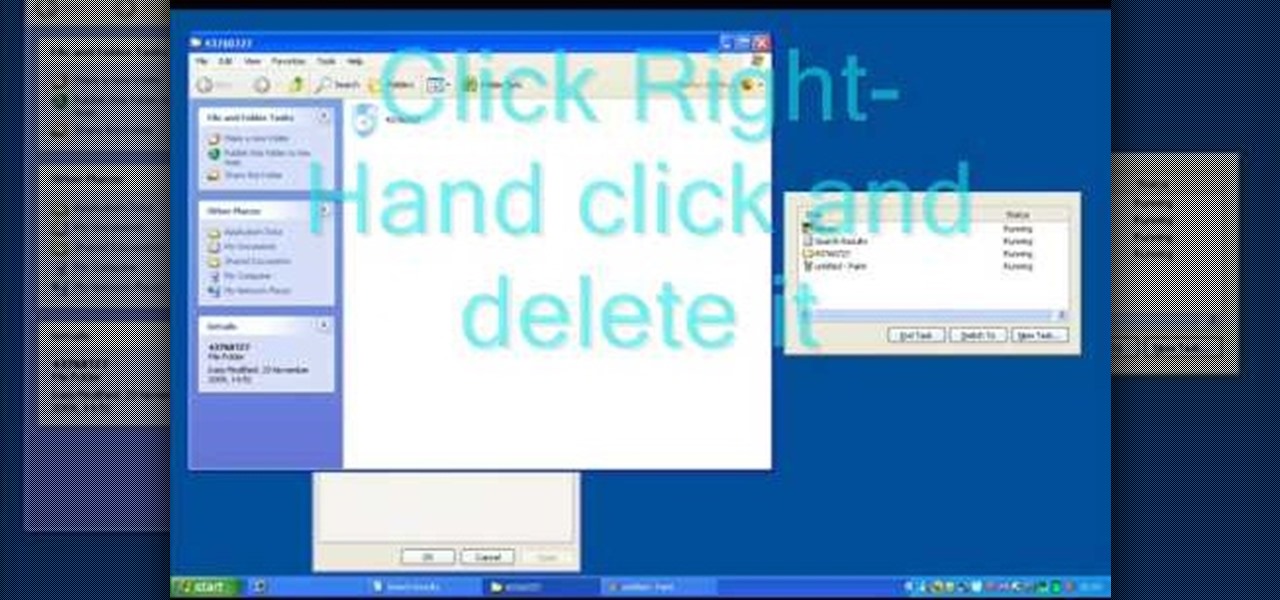
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

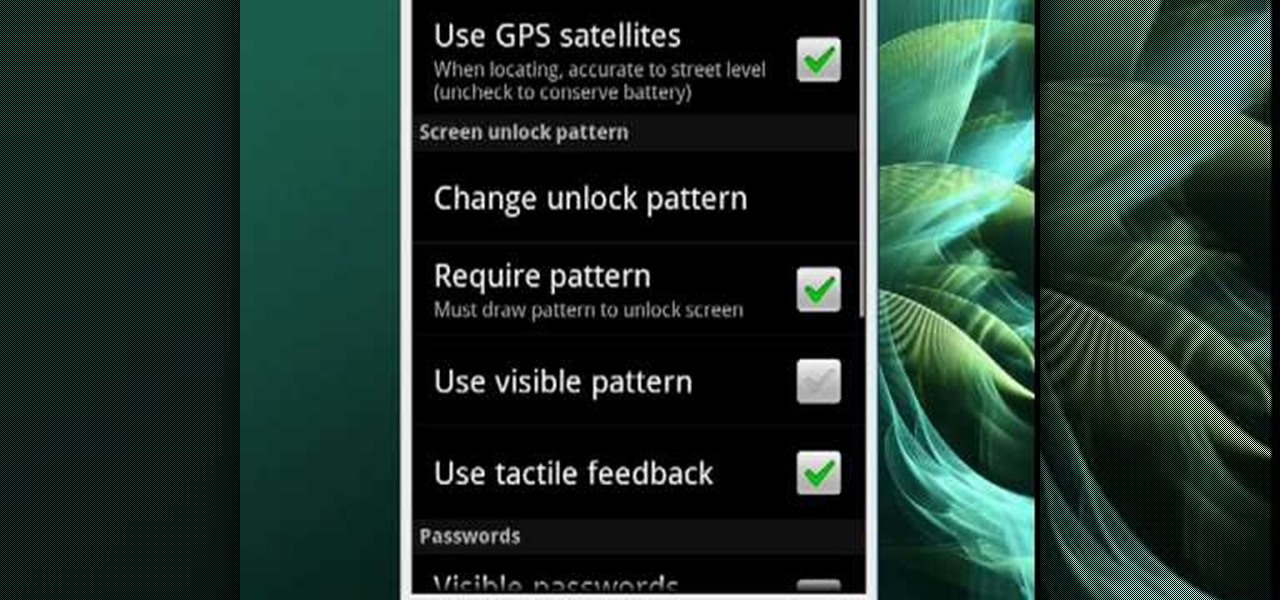
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.

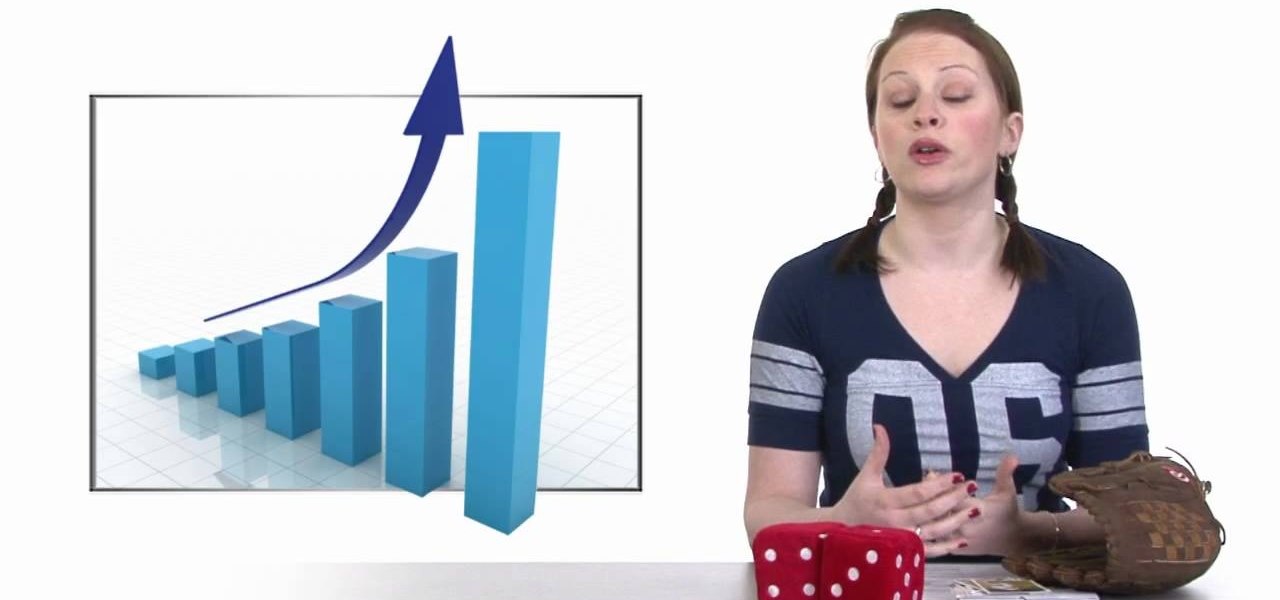
In this video, we learn how to improve your resume with valid statistics. You need solid numbers to back up the information you are writing on your resume, not just words written on the paper. Most applicants look qualified on paper, but don't land interviews because they don't offer proof to validate their claims. When you provide proof of what you are stating, the person who is viewing your resume will be more likely to call you for an interview. Make sure to provide supporting documents an...

Learning to highlight transferable skills on your resume is good for recent college graduates or if you are new to a job field because it shows that you have good characteristics that can be applied to your new job. For example, showing your communication skills is very important. Research planning is also critical. Show that you set goals for yourself and that you have clear ideas. Also, giving examples of when you used teamwork in past work experience in your life or in your career is benef...

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.