With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

In this Video Tutorial I show you five fundamental Steps to find a Job on an Online Job-Platform like LinkedIn.com. If you really follow and create this steps you will land an awesome Job.

You've seen security cameras everywhere in the public space. How many are there? Where are they? This is information that can be difficult to come by. It's not just criminals that are interested in information on this. It's your fundamental human right to be able to go about your daily life without being monitored and watched at every step. You might think that these cameras are for safety, and they can certainly help make people feel secure. Then it automatically follows that these people sh...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

Know the right thing to say – and do – if your loved one suddenly finds themselves out of work. This video will show you how to console your partner if they lose their job.
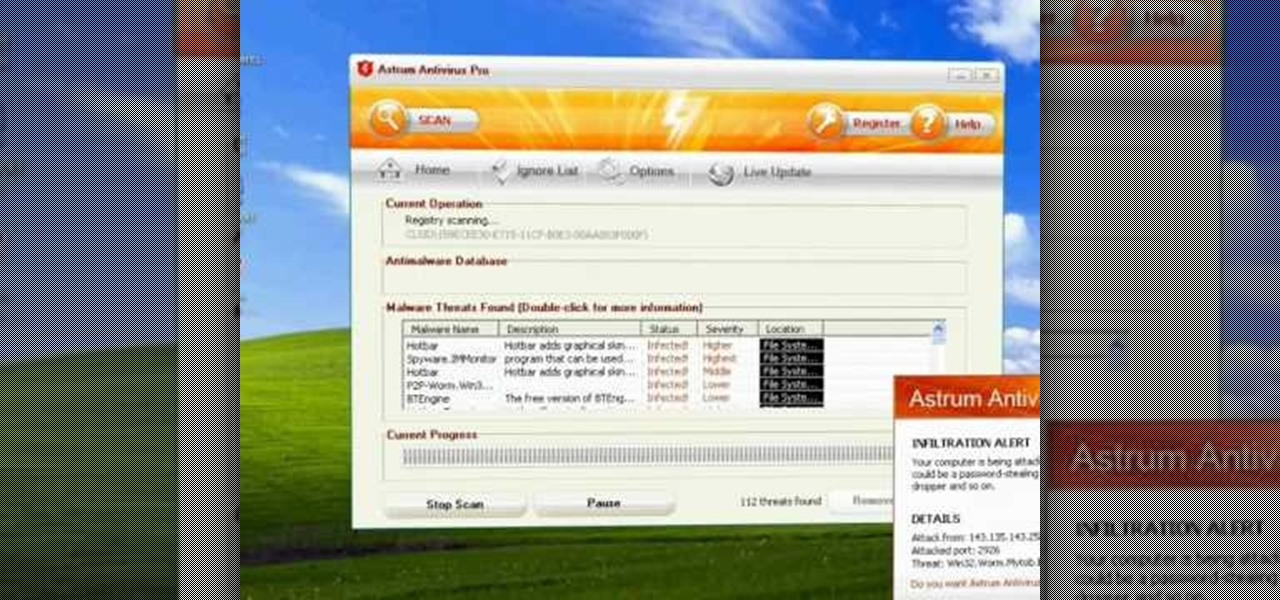
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

Gourmet editor, Ruth, tells us all about the different graters and why choosing the best grater for each job is very important. The classical grater is called a knuckle bleeder. This is because when you're at the end of the item you're grating, you have to get your hand really close to it and you might scrape your knuckles. The hand grater is easier to use and provides smaller pieces which makes it ideal for most grating jobs. A zester grater is also easy to use and provides more volume than ...

With a manual log splitter, splitting logs doesn't have to be such a chore. But a manual log splitter isn't ideal for every job. In this video, Tim Carter, of Ask the Builder, will teach youu about the manual log splitter and what sort of jobs you can use it for.

This step by step video will show you how to reassemble an Xbox 360 Controller after completing a custom paint job or mod. This is integral and the final step of any great mod, paint or customization job.

hcoleman teaches you how to answer interview questions using strategy. When the interviewer asks you to talk about yourself, you should talk about your strengths, abilities, and things that motivate you; things that demotivate you are also important. Your last job question should focus on achievements, leadership, and team skills. Use examples regarding your qualifications. The five years question is about honesty. You should talk about the company you want to work for in 5 years. Identify yo...

It's not a new technique in the auto body industry, but cutting and polishing is a great way to smooth out your paint job. This two-part video will show you the process of sanding and polishing your auto paint. The first video shows you the steps for sanding the painted surface before buffing, which removes the imperfections after painting. The second video shows you some 3M polishes for buffing the car finish. This will polish the surface into a luster shiny paint job.

No one in their right mind would ever volunteer to be one of the Red Shirts, the security officers from Star Trek who so often died during the crew's away missions. Well, it is a pretty easy-to-make and easy to recognize costume, so it might be a good choice for your next nerdy Halloween party or other get-together. This video wills show you how to make a Red Shirt shirt of a long-sleeve shirt and paint.

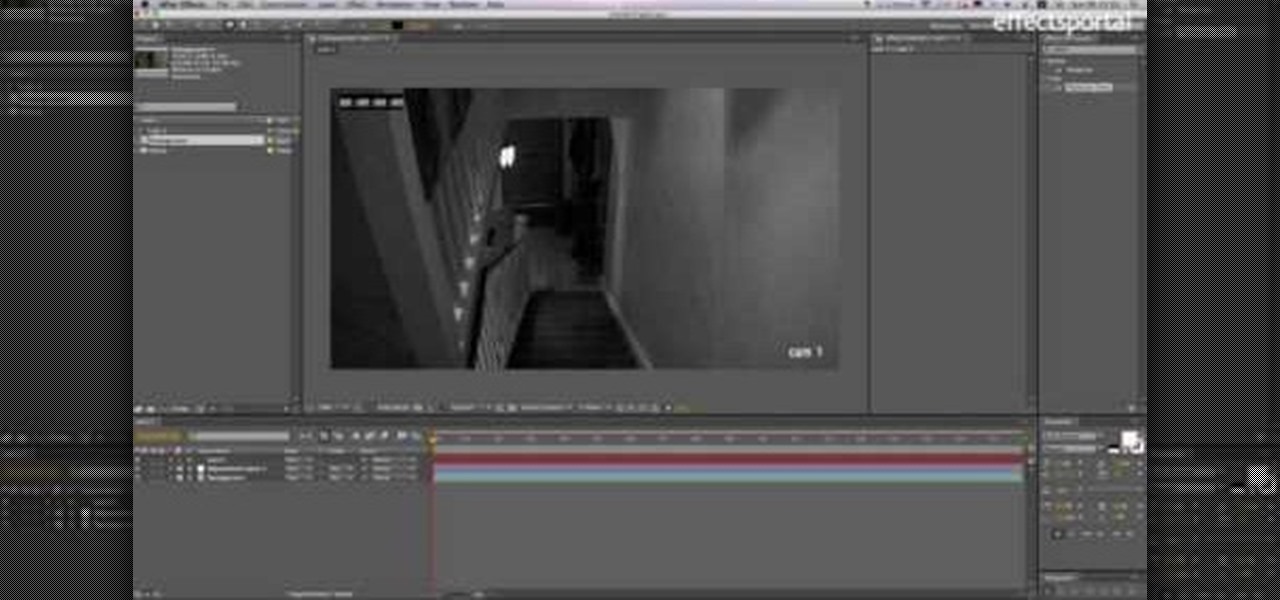
CCTV's (closed-circuit televisions) are more common than ever before, and have become more and more popular to depict in films and in video games like Manhunt. This video will teach you how to create a CCTV monitor effect akin to what a security guard would see on their camera monitor using After Effects. This will work great for any horror movie that you might be shooting, the effect is very creepy.

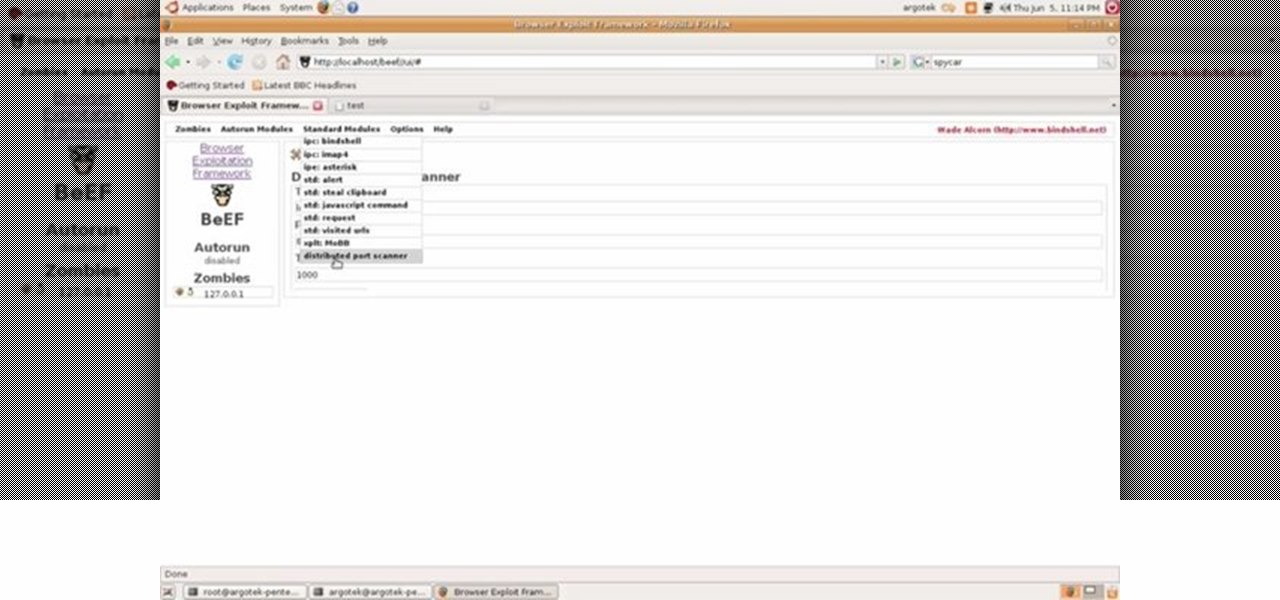
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

If you want to go in to public relations, you may need to dress with a bit of style and edge. This video from Watchmojo.com will show you how you can dress properly for a job interview in order to get that new PR job.

This video gives you a basic understanding of how to use Radio Frequency Identification (RFID) and text to speech modules. Learn how to integrate your home PC with external modules for security and fun!

Kipkay has developed a shoplifting prank, and all you need is a little electromagnetic strip to play this prank at Walmart (or wherever). You also need to bring a magnet. You swipe the strip thirty times with the magnet and this will actually magnetize the strip. Use this as inspiration for one of your April Fools Day pranks!

Want to break into the video game industry? Dream of a career as a game designer? This video shows you how you can become a game designer, in specific for the large game studio Electronic Arts. Find out what's in store for you and the ideal path of study.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Hi again everyone, In this lesson I will be talking about jobs and their meanings in Lebanese Arabic. Enjoy and feel free to ask about other jobs not mentioned here.

For hire! Netflix is looking for someone who loves to watch movies and TV shows in the comfort of their own home for hours on end. Does this sound like what you do on your free time? Then you might want to update your résumé, because this job opening is real.

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

A guy walks into a bank with a shotgun and tries to shoot his way into the vault. It's not a joke, it's the kind of crime that you're standing up against when you play L.A. Noire for PS3 or Xbox 360. Watch this walkthrough video to learn how to beat the Bank Job Street Crime mission.

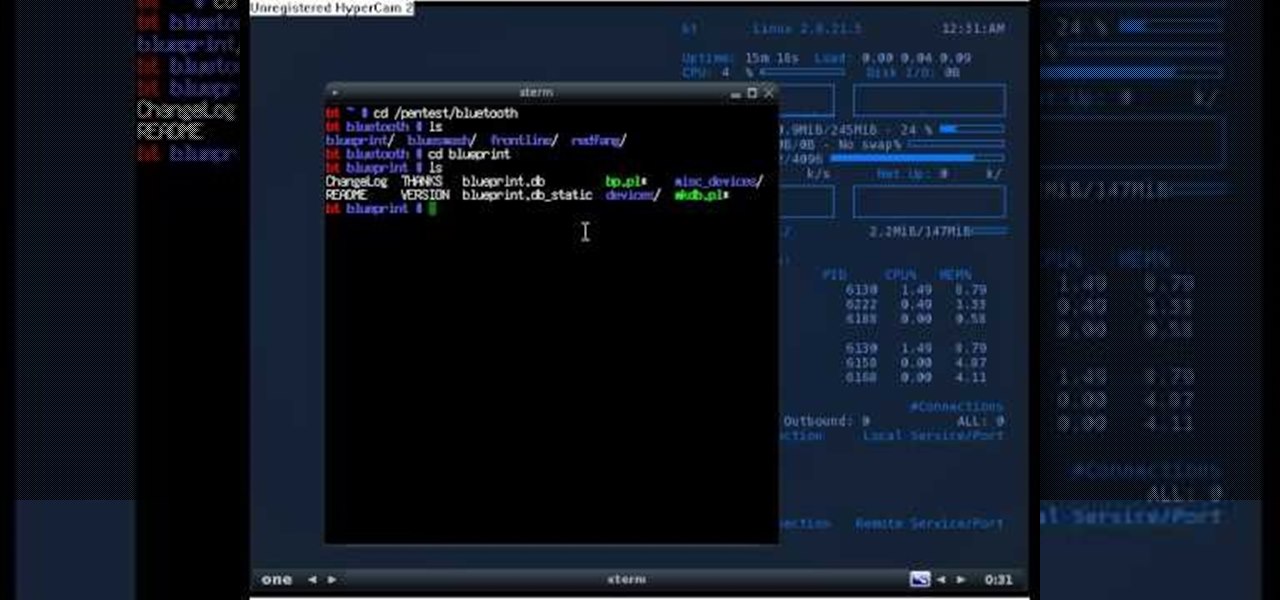
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This piece of code will open up a list of active webcams. Then just surf through your choices and watch whatever you want. You can even change the camera angle and zoom in and out of the picture!

If the paint job for your car or truck has been lightly scratched, this tutorial shows you how to use Scratch Out to remove scratches. Make sure you do this in the sun, and remember to reapply your coat of carwax after you're done.

Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.

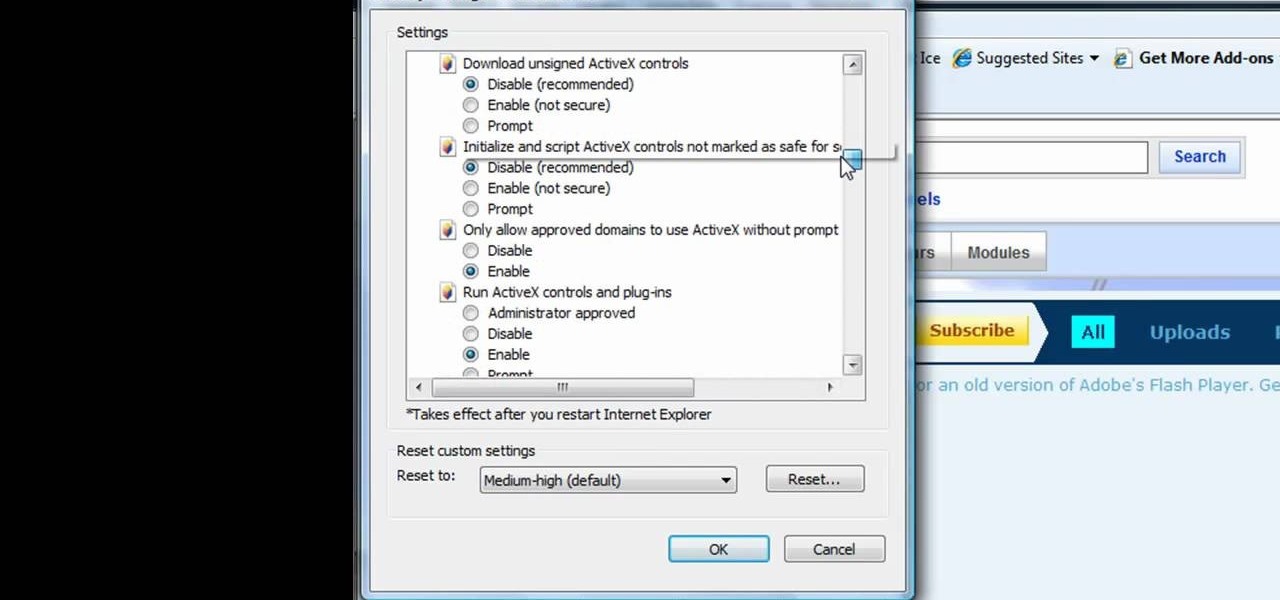
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

The difference between an amateur piece of jewelry and a professional one often lies in the details. Almost anyone can link chains together into a necklace and add small floral baubles, but the professional will take care to make sure the baubles are attached almost imperceptibly and the closure blends in with the rest of the necklace and also won't budge.

If it takes much longer for your dryer to get the job done, there may be a small problem that needs to be fixed. There are several different areas that need to be checked in order to see if anything is preventing your dryer from actually doint its job.

If you've purchased a kit from a place like Allan Block, building an in-ground or below ground pond, can be a tough job for any person. It may seem like an easy job, but it can take time. So in this tutorial, you'll find out how to put together your pond from Allan Block. So check it out and good luck!

Going into sports medicine? Taping up an injured ankle will help keep the ankle supported and on its way to mend. In this video, learn how to perform an open back ankle tape job with these step by step instructions.

Need to know how to tie a necktie for a fancy job interview? Prefer that your knot not be too bulky? Try an old standby—the half Windsor knot (sometimes referred to as the "double" Windsor). This video tutorial presents a careful, slow-motion overview of the knot tying process and will have you tying perfect half Windsor knots in no time at all.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

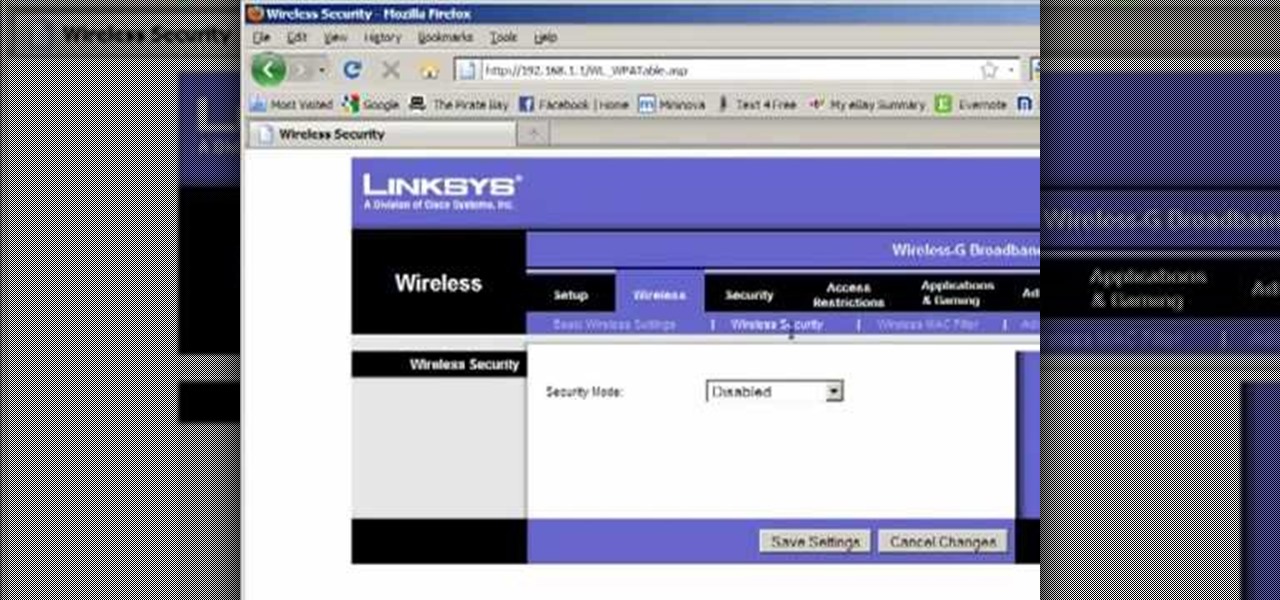
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.