» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.
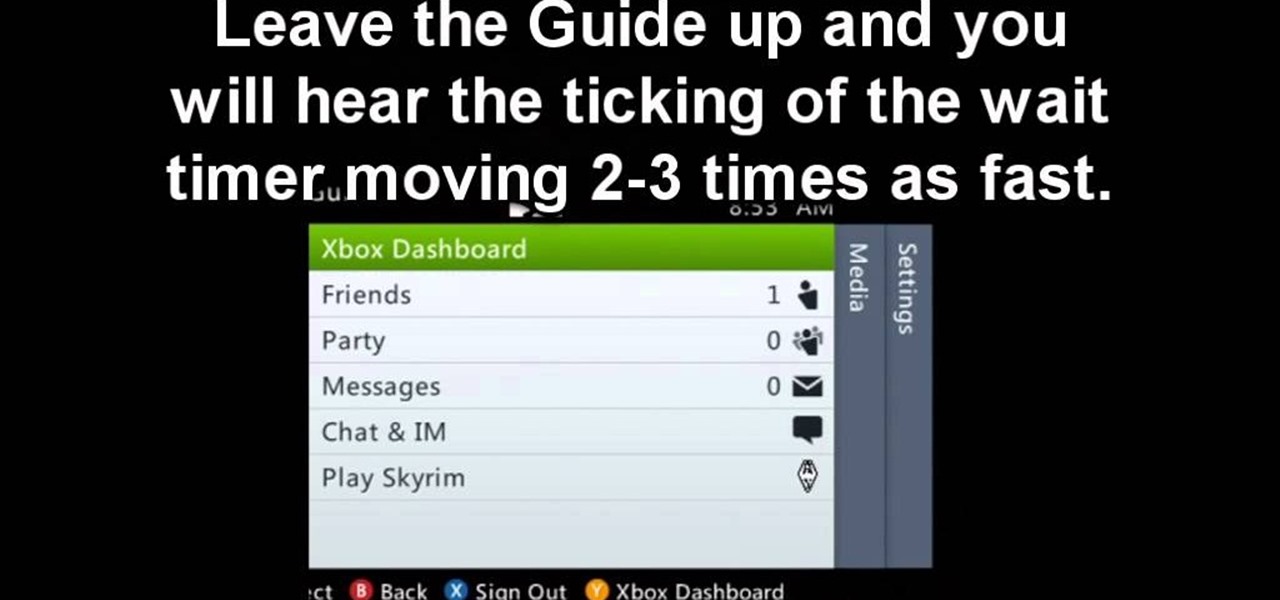
Here's a nifty little exploit for you Xbox 360 people playing The Elder Scrolls V: Skyrim. If you're tired of waiting ten seconds while you wait ten hours in-game, just bring up your Xbox guide by pushing the Xbox button on the controller. It's easy as that!
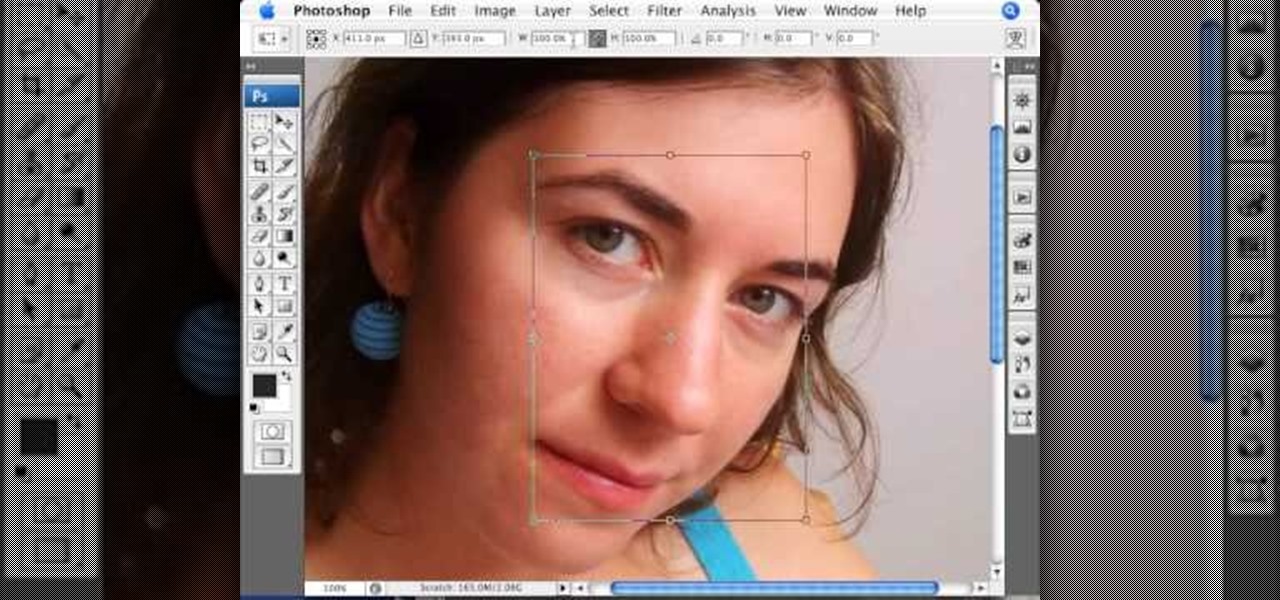
This Photoshop tutorial on performing a nose job using Photoshop contains detailed instructions on the use of Photoshop tools to, depending on taste, enhance the appearance of an individual. The person narrating the tutorial specifies the necessity of subtlety with the modification of the picture in order to remove any appearance of modification. The way described is essentially to select the general nose area, feather the selection by an optional amount, and set it in a separate layer. Then ...

Ever here of the "overworked" defender" chess move? Of course you have, but that doesn't mean you know how to pull it off. See how to do it, right here. A chess piece is overworked when it has more than one defensive job (guarding pieces or squares) to do. Typically, the overworked piece is exploited by capturing one of the pieces it's defending or occupying a square it's defending. This forces it to leave one of its defensive jobs usually resulting in material loss or checkmate.

Unless you really hate your job you probably don't want to hear from your boss about how poorly you're doing at it. Receiving a written warning from your boss at work can be stressful, but this video will teach you how to react to it effectively.
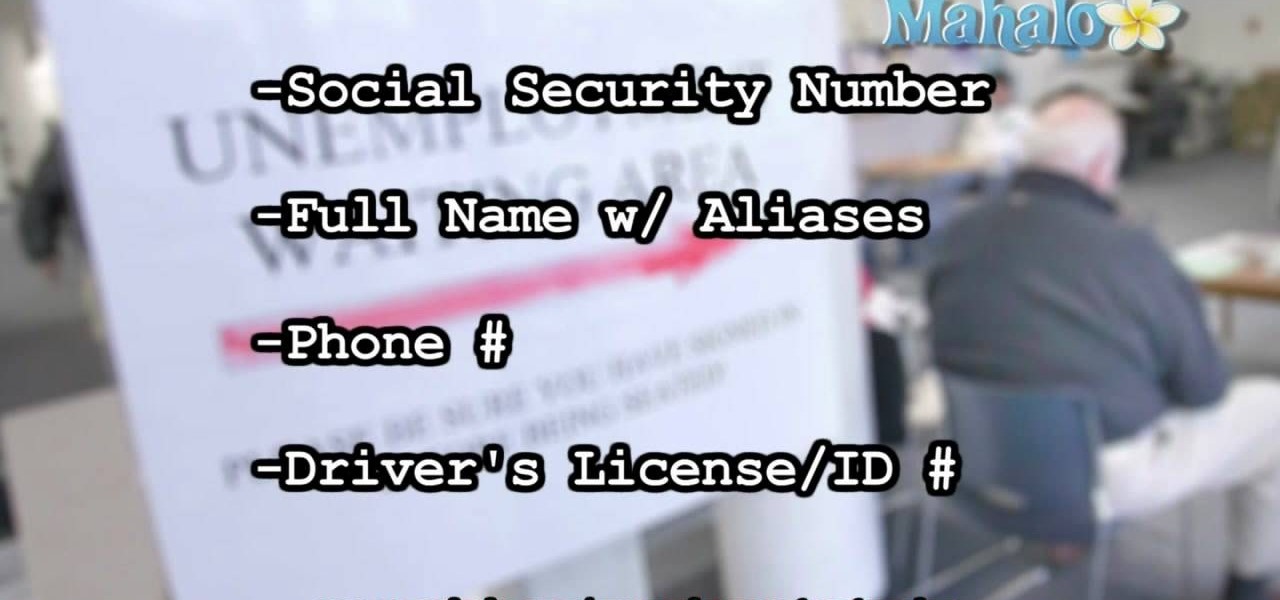
Need some help figuring out how to apply for unemployment insurance benefits after being laid off from your job in California? This video guide is here to help. For the specifics, including detailed, step-by-step instructions, and to get started applying for unemployment yourself, take a look.

In this video, expert resume writer Susan Ireland gives you advice for writing a letter of recommendation - for yourself! She offers you quick tips so that you can get past writer's block and start writing an effective cover letter. Let Susan help you get the job of your dreams.

This video resume-writing tutorial presents two case studies complete with challenges, strategies and sample functional resumes. Resumes are the key to getting into any job that you want. Watch and write a functional resume that will help get your foot in the door wherever you want to work.

This video resume-writing tutorial demonstrates several great examples of resume objectives, summaries and profiles, and how to mix them. Resumes can be challenging to write, harder still to do well, but are the only way to get into the job you want. Watch and find out how to put together a quality resume.

Once you have determined that new salary can be adjusted through negotiations, do your homework. Have a good sound reason for negotiations. This how to video will teach you how you can tactfully ask for a salary and benefits when you have been recently employed.

Brian Krueger, President of CollegeGrad, presents "What to do After Your Interview."

With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...

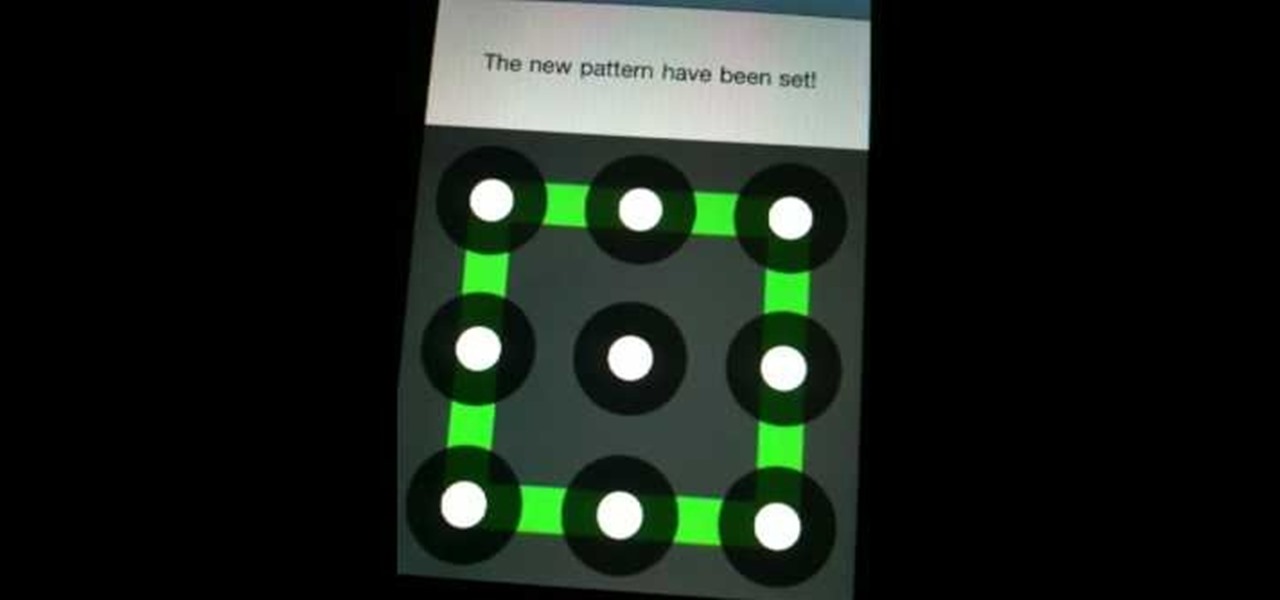
iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.

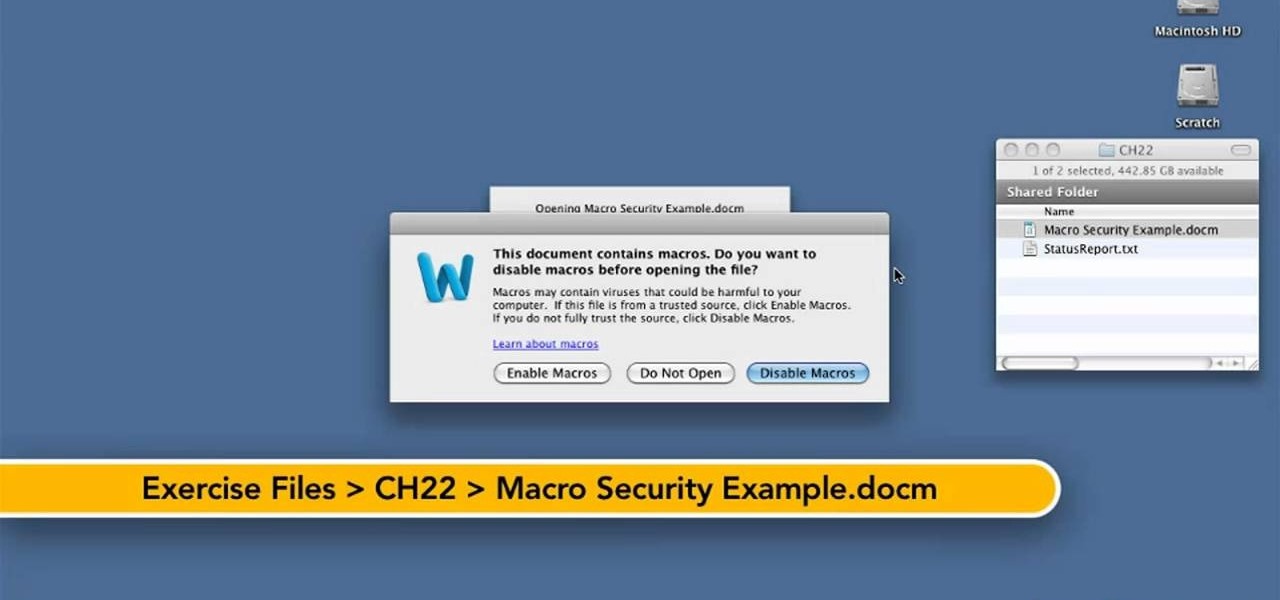
Want to know how to keep safe when using macros in Word for Mac 2011? This video will show you how it's done. Whether you're new to Microsoft's popular word processing application, new to MS Word 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For detailed, step-by-step instructions, watch the video.

If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

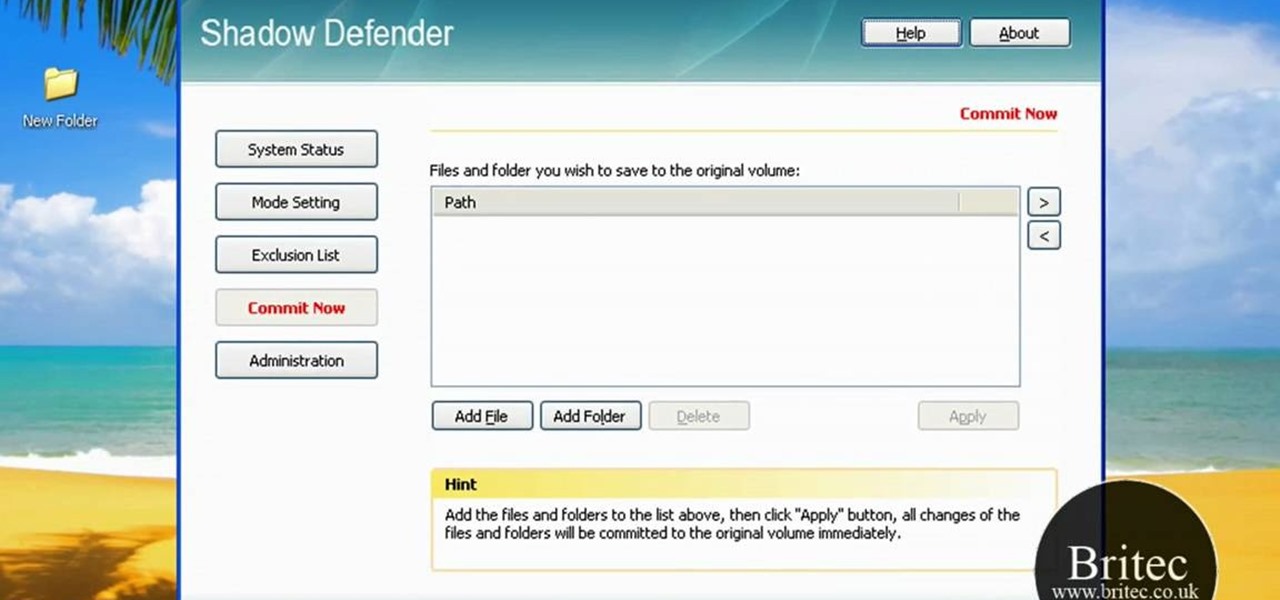
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.

hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52.5th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about macro security. For more information on how to use macros safely, watch this free video guide.

In this economy any job is better than none at all, right? Of course, but if you know you are worth more than you're making, follow this tutorial for tips on how to ask your boss for a raise. You'll never know if you don't ask! Good luck!

Take a folder and organize documents based on the actions required. Actions:

What do you do with a password protected WinRAR archive? You hack it - naturally. And how do you hack it? First, download RAR Password Recovery v1.1 RC17 then follow along with this video to crack almost any WinRAR password. So much for security.

He's not exactly demanding sexual favors, but his flirting is getting really gross. What's a girl who likes her job to do? You will need diplomacy and documentation. Assess his behavior. Now, don’t be offended, but we have to ask: Is he really coming on to you, or is he just a sociable, flirtatious kind of guy? If it’s the latter, just ignore it. Do your part to keep the relationship professional. Don't chat about how your last two boyfriends cheated on you and then expect him to know that di...

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

Did you know that field templates can be applied two different ways? And that the two "edit" buttons on the main interface tie directly into how these field templates are used? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite discusses these topics and how to control such permissions through security roles.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

Dogs naturally want to have a den, so a crate gives him his own space. Puppies will get security and comfort from a crate. Because a dog will not want to go to the bathroom where they sleep, they won't make a mess in their crate, making it useful for housebreaking a dog. Watch this video pet care tutorial and learn how to crate train a dog.

In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwords securely with this tutorial.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

This tutorial gives you a basic overview of how to build a Parabolic WiFi Booster that will increase you router's range as well as narrow the signal path for added security.

Professor of RVing, Jim Twamley talks about lock security and shows you how to replace an RV entry lock.

How to get around your school or home's computer security to view restricted webpages.

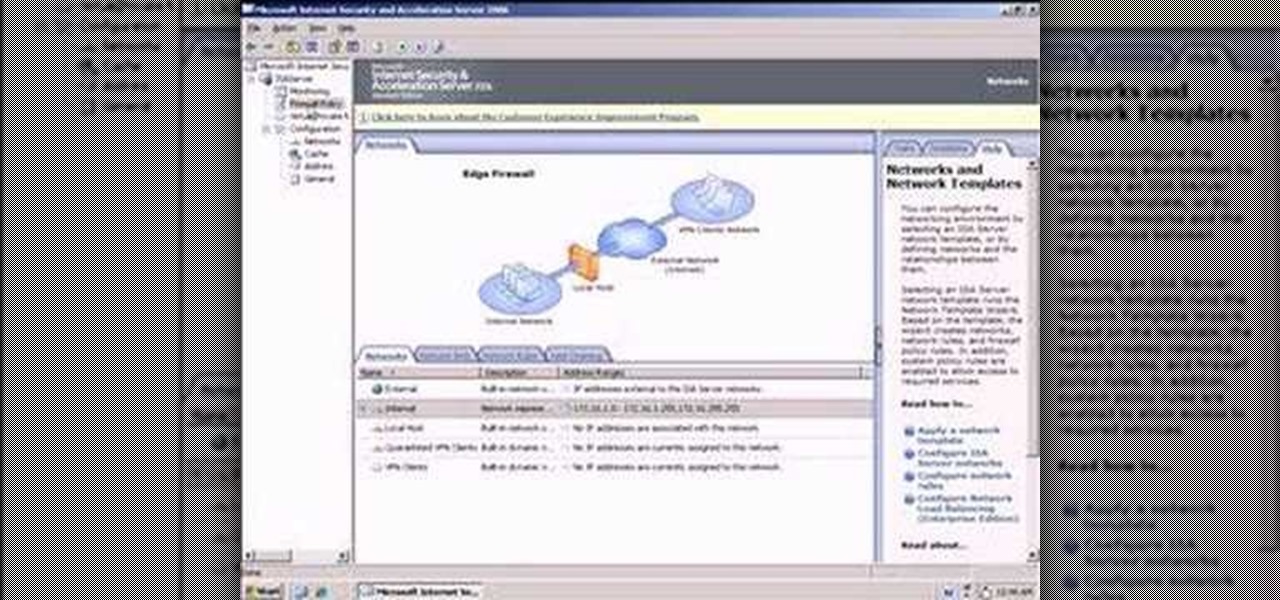
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

This Video demonstrates how to install multi channel (4,8,16) power supply for security camera and CCTV installation.

Watch this video to learn how to make a radio controlled camera rig that can tilt and pan like an expensive security camera. This is an amazing tool for movie making! Stick to your budget.

SalaryExpert.com or Salary.com are two great Websites designated to informing people of expected salaries of particular job fields, so people know what to expect when offered a salary. Know what salary amount to expect when being offered a job in a particular job from a career adviser in this free video on job guidance.

In this tutorial, we learn how to stop procrastinating by rewarding yourself. To do this, you should first select one task you've been putting off for a long time. Then, time yourself and give the task one full hour of your time. Ignore everything else you have to do during this time, don't take breaks and let anything bother you. When you are finished with the task, give yourself a reward for completing this job! This will help you finish your task at hand and get things done more effectivel...

A new paint job can do wonders for any car, no matter how old it may be. It can give a look and feel to the car thanks to paint that may not have been available when it was being produced. But prepping a car, especially one that has been worked on, is an important aspect before any paint touches it. So in this tutorial, you'll find out some easy tips for making sure you get the right paint jo for you classic VW Beetle. Enjoy!

Owning a home can be a great accomplishment for many men and women. Once you own it, you can do almost anything you want with it, even give it a new paint job. Now, painting is a fun and easy way to customize rooms in your home that may lack character, but it can be a tough job. This tutorial, presented by Lowes, will help show you how to properly paint your room using a roller brush and the right equipment. So good luck and try to stay clean. Enjoy!