LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

You might be familiar with the use of zucchini blossoms in cooking and maybe even know how to make herbal simple syrups. But if you really want to show off as someone who knows how to use flowering plants in food, try adding some flower water to your cooking/baking repertoire.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Pain is, for the most part, unavoidable when you stub your toe, break your arm, or cut your finger open. It's instantaneous and, in some cases, long-lasting, but it only feels as bad as you want it to. Yes, that's right—that pain is all in your head.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

As glorious as a good drink (or five) can be, the aftermath of alcohol on the body is one of life's least enjoyable features. A few hours of fun can come at the expense of a day or two of feeling dead to the world, with an upset stomach, an aching body, and a headache that makes it feel as though your friends used your head for a piñata.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Sometimes it's hard to remember that lasagna, pizza, cannoli, and other dishes are actually Italian in origin; they're so much a part of the American culinary landscape at this point. Wherever they come from, Americans of all kinds love to eat 'em. This guy was released from a North Korean prison, and after two years, the first thing he wanted to eat was fast-food pizza.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

In this video series, learn how to prepare your garden for winter. Our experts, John Guion and Arnetta Francis, show you everything you need to know about winter garden care. Learn how to fertilize your lawn for cold weather. Also, learn tips for preparing your faucets for winter.

In this series John explains how to read spark plugs, how to diagnose when they are bad or need replacing and then how to replace and test them. It's a pretty simple task, and it'll save you money if you learn to do it yourself. Please make sure to check your car's repair manual as specifics may be different.

In this video series, our expert John Carstarphen will show you how to use walls, windows, and spline objects. He will also show you how to use the NURBS loft, copy and scale objects, use floor trim, and add a backdrop. He will also show you how to texture the trim, add a background image, and tile the floor before showing you how to light with luminance and create fake radiosity.

In this video series, our expert John Carstarphen will show you how to integrate 2D and 3D, add geometry, place geometry, do frontal mapping, alter image distortion, and match lighting. He will teach you how to place a tube object, fine tune the animation, and about keyframes.

In this video series, watch as graphic design expert John Moore teaches how to design a logo. Learn what software you need for logo design, how to prepare for logo design, the importance of text, the importance of color, the use of different fonts, how to manipulate graphics, how to use filters to enhance text, and how to use wingdings to design a logo. Coming up with a recognizable brand and logo is essential to the success of any company or small business, so let the experts at Expert Villa...

In this series, learn about the different types of Native American flutes. You will be amazed by the various sounds and pitches that these instruments can produce. Let Werner John show you some different styles of Native American flutes. He also plays these flutes so that you can hear their distinctive sounds and pitches. So, start learning about wondrous world of Native American flutes today!

When Werner John was introduced to a small wooden flute at age 11 it was love at first note! He has been playing for over 40 years. The Native American flute is a wonderful instrument, it sounds great, it's physically beautiful, but the best part about it is how easy it is to play. I've sold about 800 flutes to people all over the northeast in the last 16 years or so and no one has ever came back for more than three lessons. That says a lot about an instrument that people just pick up and mak...

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

Two of the three entities behind Pokemon GO, the reigning champion in mobile augmented reality gaming, are joining forces again to see if lightning can strike more than once.

The movie theater business is hurting due to the pandemic, but that hurdle is actually the perfect set of circumstances for movie studios to lean hard into augmented reality marketing.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

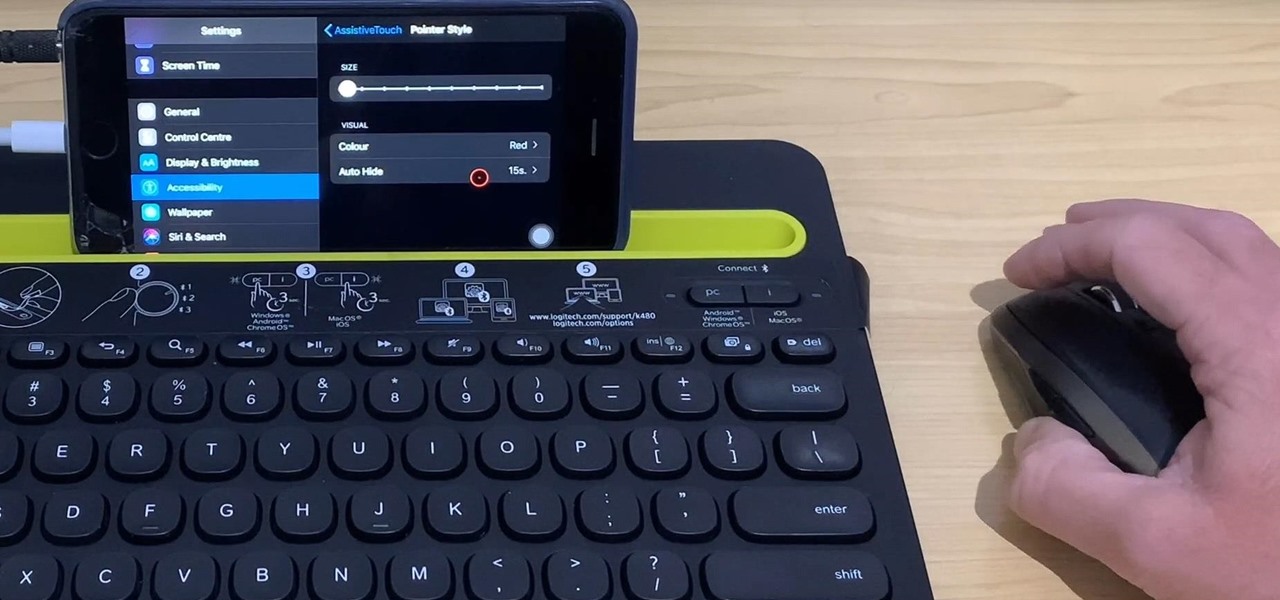
With stay-at-home orders for most of us in the US because of the new coronavirus, many of you are likely struggling to be productive and efficient when working from home. Unless you've worked from home before, it can be challenging to separate work from personal life throughout the "workday." But your iPhone can help make the transition easier and more successful.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.