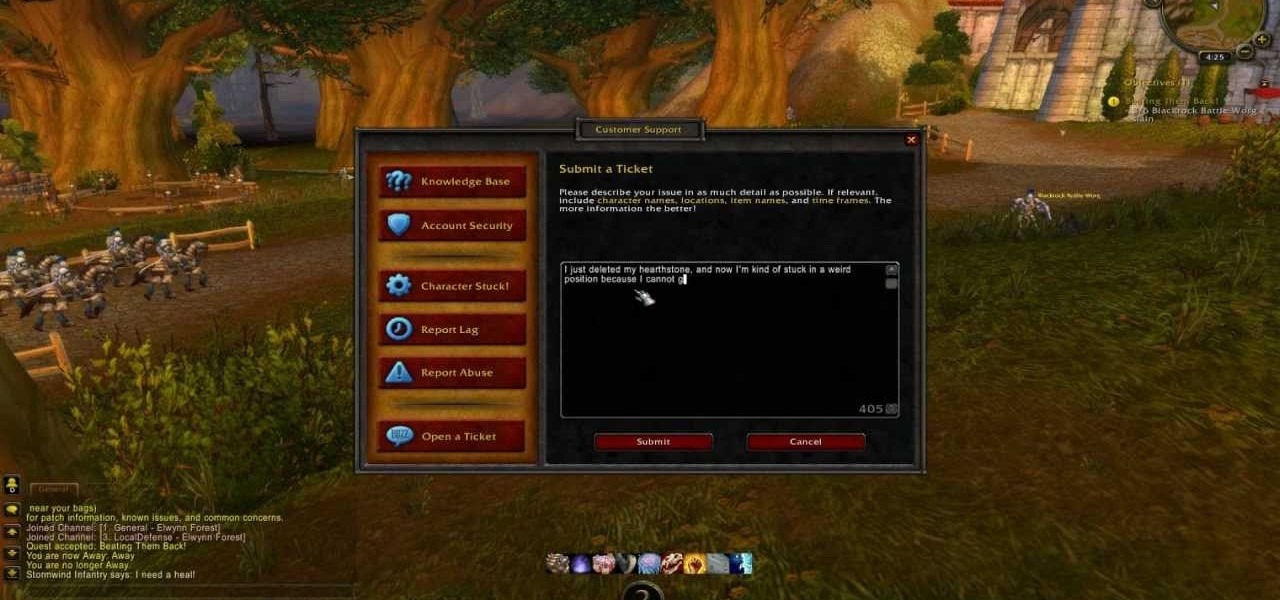
Everyone knows how rough it can be to wait around for a GM while playing WoW. A World of Warcraft Game Master can be fairly busy during peak hours, and you may not want to wait around that long. Take a look at this legitimate trick to lowering a GM wait time to a few minutes.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

Looking for fast cash with no questions asked? There are legitimate ways to get it, if you're willing to pay the consequences. You will need a credit card with unused credit, a tax refund, a car, a small loan company, a signature loan company, or a payday loan. Watch this video tutorial and learn how to get money quickly by finding a loan shark.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Have you ever found yourself calling up a company, only to be denied due to not calling from the number listed on your account? Thanks to a website called Spoofcard, this is no longer an issue! SpoofCard let's you spoof the number you are calling from, as well as modify your voice (Male -> Female or vice versa). Best of all, it all looks completely legitimate.
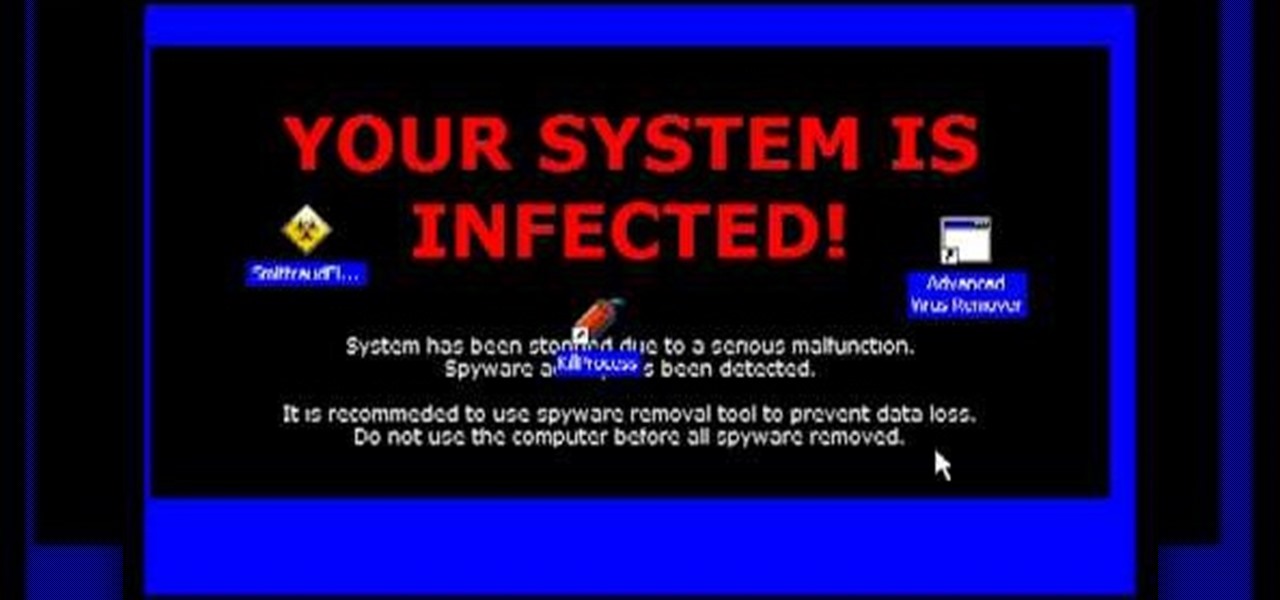
Spyware are programs that infect your system and / or at the same time collect personal information without your consent.

How to Use COD4 Cracked Servers.

In this video, we learn how to change your name on Facebook. First, go to Facebook and log into your account. Once you are on here, click on the settings button. Now, find where it says "name" and click "change". Once you change this, enter in the name that you want to show and then choose the name that you want to display. Once you are finished, click "change name" and then you will have to certify that this is your real legitimate name. Once you do this, your page will refresh and your new ...

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Facebook has been looking to launch a new product for a while now, and it seems they've finally realized what they're best at—being as creepy as possible. If you thought your boss checking out your girlfriend's beach photos was weird, Facebook's new Graph Search has only upped the ante. Now, I don't want to be an alarmist, because I'm sure there are a bunch of great things a Facebook search would find. If you're single, perhaps you could search "Girls that are single that like Goodfellas." Th...

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

In this video from theXBox360GameReview we learn how start and join an Xbox Live party. Once signed into Xbox live, scroll to the friends channel, and select the friend you want to have your party with and press Y. Now that you have a party going, you can play some Halo wars. If you want more friends to join the party go to your friends list using the guide button and tap X to select who you want to invite. If you want everyone in the party join in, select Party and choose Invite Party to gam...

These crochet how-to videos demonstrate how to do flat braid joining to join granny squares. Start by crocheting a border on the first square. Then proceed to join the first and second granny squares with the flat braid joining technique. Watch and learn how simple it is to crochet with flat braiding. Follow along until you have joined all four granny squares.

Disasters can happen at any moment, and when they do, it's often hard to find the right information to help you get to safety as quickly as possible.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

One of the highest rated posts on Spotify's own community forum is titled "Add support for Google Chromecast," a clear indicator of not only how much this feature is desired, but also of Spotify's lack of care for it. Remaining consistent with statements made in the past, Spotify is firm in their decision to not pursue Chromecast support at this time—or maybe ever—thanks to a deal with Sonos and Spotify Connect.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

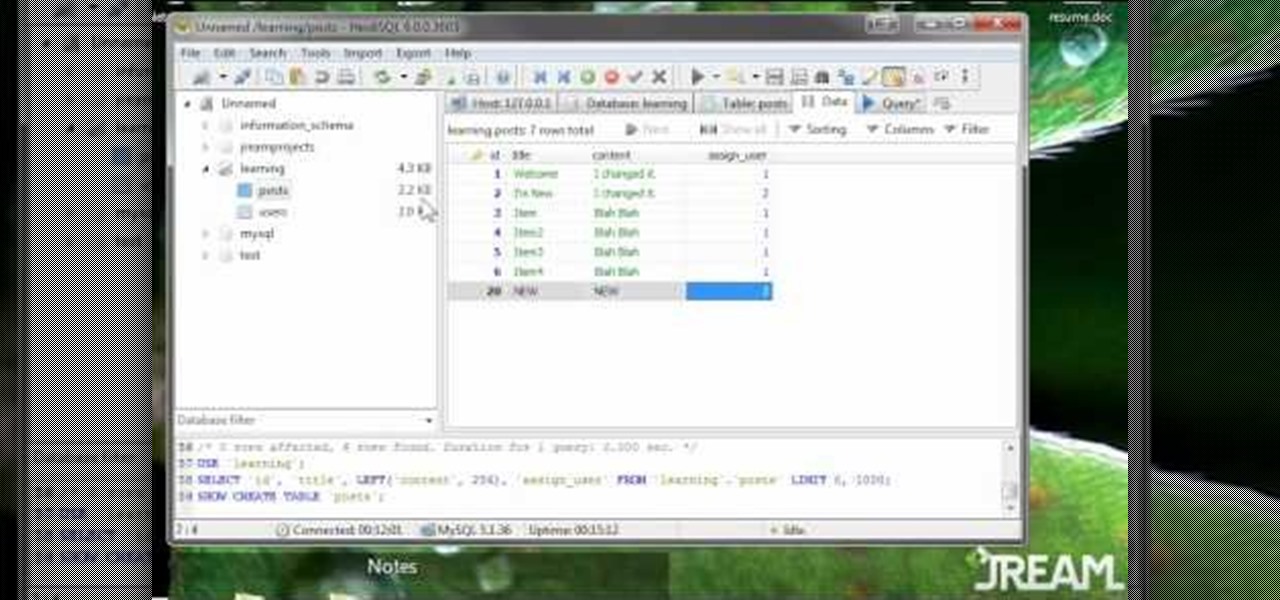
JOIN commands in MySQL can be scary, and a bit tricky to master - but that's where this video comes in. This clearly and succintly demonstrates what a JOIN in MySQL is and how you can painlessly use these commands in your projects.

Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

With the growing popularity of digital downloads, it's important for aspiring musicians to have some sort of download available of their music. If you're an unsigned musician, selling your music on iTunes might seem daunting, but it's actually very easy! Learn how to do it in this video.

Having problems with your anti-virus software on Windows? Learn how to remove the fake virus protector Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer. Personal Anti-Virus is hard to get rid of and is totally annoying. To get rid of it, you don't have to download anything.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

In this video, we learn how to join a crochet round left-handed. First, join with the top level of the crochet. After this, half double crochet of the shell and join with the beginning of the shell. Now, join with the beginning of the double crochet. Go around to the beginning and join with the beginning of the single crochet using a slip stitch. Then, slip stitch between the joining. Now you will want to join with the slip stitch in the beginning of the double crochet. To finish, join with t...

In this video, we learn how to join a crochet round. First, you will join with the beginning double crochet. Now, go to the beginning and join with a single crochet doing a slip stitch. Then, slip stitch between to join the two together. Go in with a slip stitch in the beginning, then double crochet. After this, join again with a slip stitch, then go to the beginning of the whole crochet again. By following these steps, you will learn how to join a crochet round in no time! Practice with seve...

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

The flat braid join is a method of stitching granny squares together using chain-3 loops. This tutorial demonstrates how you can use the flat braid technique to easily and quickly join your own granny squares together for your next crochet project.

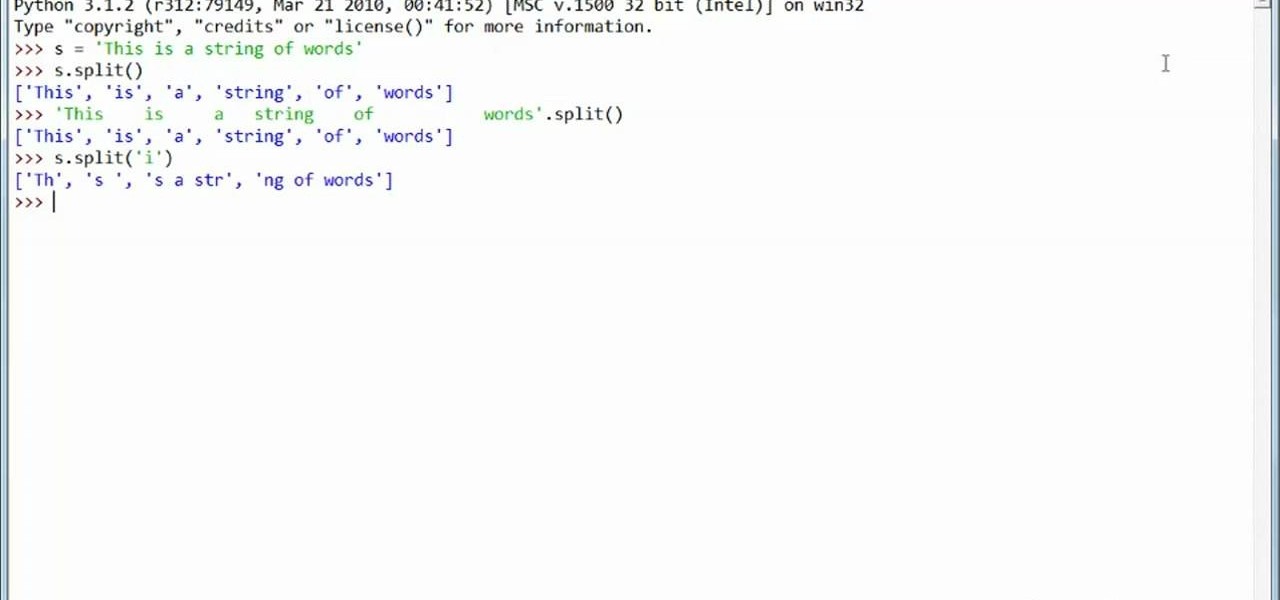
In this clip, learn how to split and join strings when coding in Python 3. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.

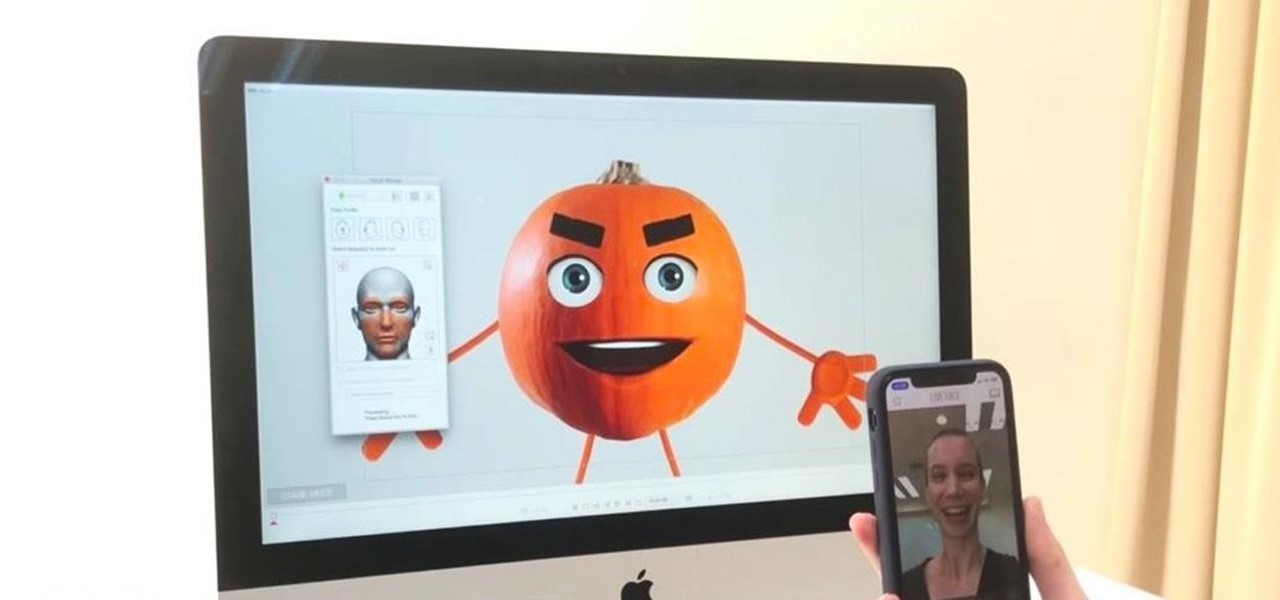
While 3D motion capture via iPhone X is coming soon from Unity, software maker Reallusion offers similar functionality to 3D model animation producers today.

In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

There's been a lot of speculation as to what Apple's next iPhone models will have in store for us. There's a lot of credible rumors about the iPhone 7, but is there also a Pro model in the works? We may actually have a legitimate sneak peek at what that device could look like.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

I can certainly say that I don't like be ignored, and you're probably right there with me on that. Also, if you're like me, you don't like being blocked on an instant messenger, either. There's something about being shafted like that that can really cramp your style.

Xbox gaming has come a long way since its inception over a decade ago. What was once simply a bulky gaming console has transformed into legitimate entertainment hub for the home, thanks to the latest Metro-friendly update to the Xbox 360. Now there's newly-designed Music and Video apps, Internet Explorer, and best of all—Xbox SmartGlass.

For over three years, Facebook users have been able to clog up their Facebook chats with little pictures of smiley faces and red hearts, but now it has finally gone a step further...

To do a join-up with your horse, first drive the horse away from you to keep it moving until it is ready to join-up. A join-up may take a very long time, especially if your horse has never done one before. Keep as square to the horse as you can. Use a lunge whip, lead rope or your hands to drive the horse away but never hit or touch the horse. The join-up method creates mutual respect and communication between the rider and the horse. The horse is ready to join up by turning its inner ear tow...