
In this "bootleg" video tutorial from Adobe Beginner Classes, join Dennis Radeke as he shows you how he pulls a Chorma Key using Adobe Ultra CS3 for his official ABC's show. See how to chroma key in Adobe Ultra. Chroma key in Adobe Ultra.

Hair loss can be caused by genetic factors, certain illnesses or medications like chemotherapy. But you may be surprised to know that your diet can also play a big role in how much hair you lose. Join our experts as they explain why a healthy diet is an important factor for maintaining healthy hair. Eat to maintain a full head of hair.

Join Melissa and Maddie in learning from Mike how to play the harmonica and how it works...and watch them make their own Omelette Song. Play the harmonica for beginners.

Join Magician Ryan Oakes as he reveals step by step a really cool card trick! Grab and audience a deck of cards and get ready to have a magic show of your own! So cool! You will need one deck of playing cards. Sometimes we use materials that require adult supervision... like scissors so make sure you have friends and family around whenever you do magic tricks.

Join the A-TV science superstars and find out how to make a cabbage indicator to determine whether a substance is an acid or alkali.
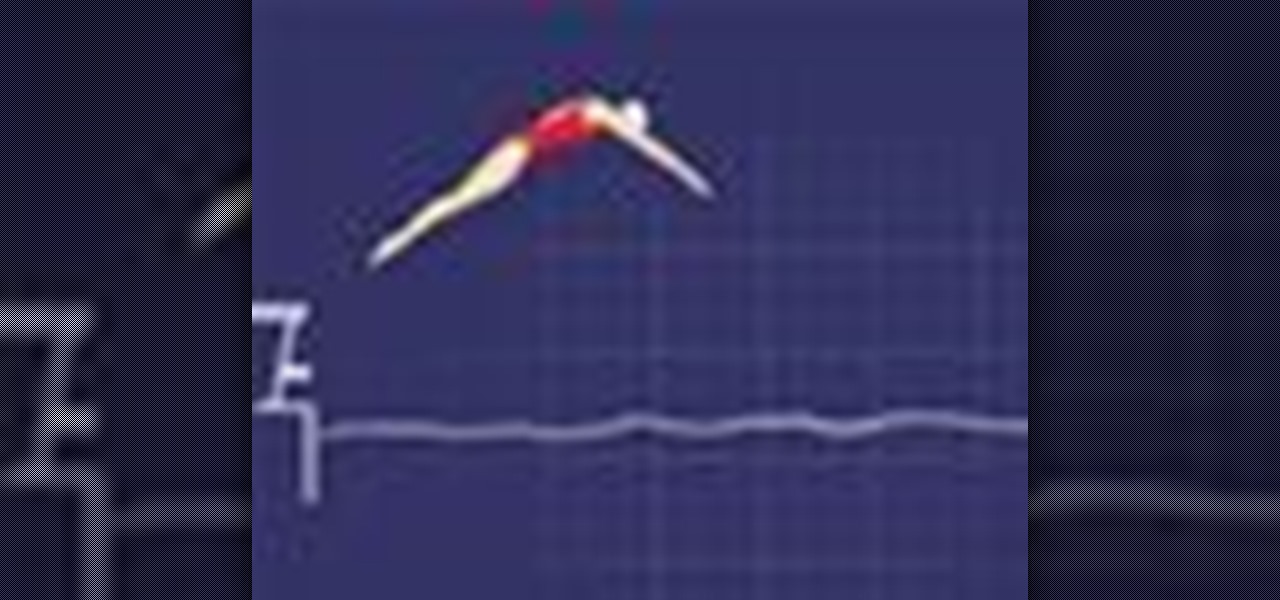
Most top swimmers use the grab start to get their race under way. This gets you moving off the blocks quickly and into the water smoothly. The starter will not begin the race until everybody is ready and still. This is really important because you can be disqualified if you fall in before the start or if you are slow getting ready. Follow along in this how-to animation to learn the best method to power off the blocks in swimming.

All great things of this world have a beginning. In the hopes that this will be one of those things, we here begin.

Yesterday, Mojang announced their next video game project 0x10c, and the response has been tremendous. Discussions have covered everything from the math mystery over the game's name, to creating projects that interpret the assembly instruction code the in-game computers use (more on that later), to the debate over why a monthly fee would be required to play online in the "multiverse". To answer that last one, Mojang wants to run everyone's virtual computers in their cloud, even if the user is...

Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

In this article, I'll show you how to make a simple touch-triggered switch. This is very useful for various electronic projects, from a simple bedside light to a flat panel touch keyboard. The circuit can vary in switching power depending on the transistors you use. For example, if you're looking into creating a 120V light that turns on when touched, you'd need two powerful transistors and an isolation relay. However, a simple flashlight that turns on when touched would only take a couple of ...

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

Words that will help you with your writing Alliteration - The repetition of aconsonant sound. This si important because it makes words stand out, and because it can help set the mood for something.

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Another great Community Byte in the bag! This week was really cool, especially with programming going on twice a week. We transitioned to the new times very smoothly with no one left behind, from what I can tell.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

When was the last time you took some time out of your day to play with your favorite action figure? Or build an entire town of Legos? Well, it’s time for you to dust off that old toy chest for this week’s Phone Snap challenge!

Welcome to the Goodnight Byte for HackThisSite, Basic Mission 4. In Friday's session, we tackled some coding in Gobby. Nothing special, just a few modifications to the NullBot script we made a few session ago, and some education on regular expressions. Apart from coding, we did our scheduled HackThisSite mission. We had to take on some JavaScript, which was a new thing for Null Byte. This mission taught us about client-side HTML manipulation through JavaScript injections. This just means that...

Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exactly what we do! In our sessions, we have started to both code and complete HTS missions. This means that there is something for everyone here, so make sure you join us.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

Undercover Crow -Sage I sit in a dim black bench

Back when I was a Windows user, I know I'm not the only one who has experienced password loss—that moment where you just can't remember your password. Sometimes it happens to the best of us. So, how can we get into the system without paying a local geek or geeksquad to do it? First, we have to look into how Windows stores their passwords.

To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints, though. Firefox has done an amazing job at completely revamping its source code and redesigning all of its engines, making it a more than worthy competitor to Chrome. However, we are displeased with Firefox because eve...

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

PLASTRUM n pl. -S plastron 62 points (12 points without the bingo)

Cheating. It happens everywhere. From scientists faking human ears on mice, to Hollywood thirty-somethings cheating on their quadragenarian wives, to chess players accusing supercomputers of fraud. There's no game or profession out there that doesn't have a cheater or two, but the bigger nuisance is probably those people who accuse others of cheating.

Beginning this week, Null Byte will be hosting a new feature called Community Byte, a weekly coding and hacking session held in the Null Byte IRC. This is a chance for our community to do something fun, and make something awesome together!

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

In a recent episode of The Big Bang Theory, character Sheldon Cooper designed a highly complicated three-person game of chess, with an odd-shaped nonagon board and two new pieces—serpent and old woman. Seemingly pioneering, in truth, three-player chess has been around since the early-1700s, with many different variations, most of which retain the basic game structure and sixteen pieces that each player controls.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.









































