Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
Welcome back Hackers\Newbies!

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.
The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

In this clip, you'll learn how to generate admin command prompts on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

In this clip, you'll learn how to explore a hard drive on a desktop of laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

In this clip, you'll learn how to use the Flip-3D window changer application on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

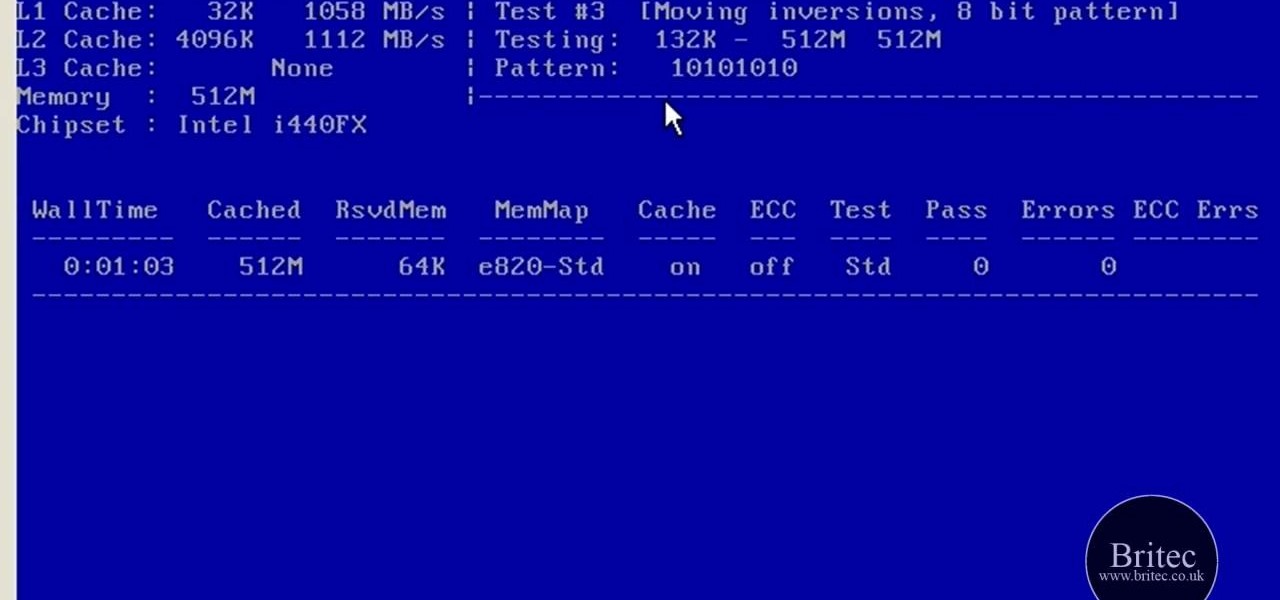
In this clip, you'll learn how to test your system memory with both Memtest86 and Windiag. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

Need help figuring out how to troubleshoot and repair a Missing OS error on a Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

If you just purchased an Android enable mobile device with Bluetooth, then one of the main objectives you'll have on your to-do list is to set it up in your vehicle for hands-free dialing and phone calls. Activating Bluetooth inside your car is easy, and all you need to remember is a little number called zero. Actually, you need to remember it 4 times — Best Buy has answers. The Best Buy Mobile team explains how simple it is to activate Bluetooth settings on an Android cell phone.

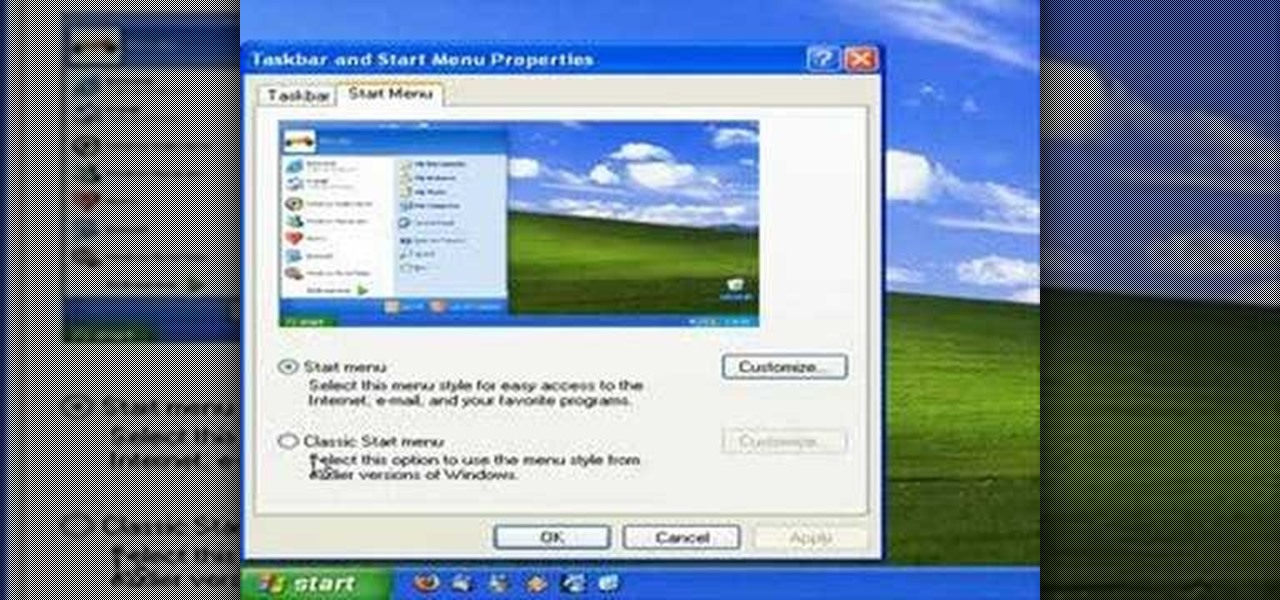
Watch this quick screencast, to learn how to easily set your system to revert to the Classic Start Menu in Windows XP.

Perform cable management to improve cooling and system layout.

Understanding the Binary Numbering System and how to decode binary numbers.

Need to move your my documents folder in windows xp because you have 2 drives for video editing and want to keep files on one drive and the operating system on the other, or maybe you just have an older computer to which you've added a new drive? Find out how to use Tweak UI to change some the hidden settings to move your my documents folder.

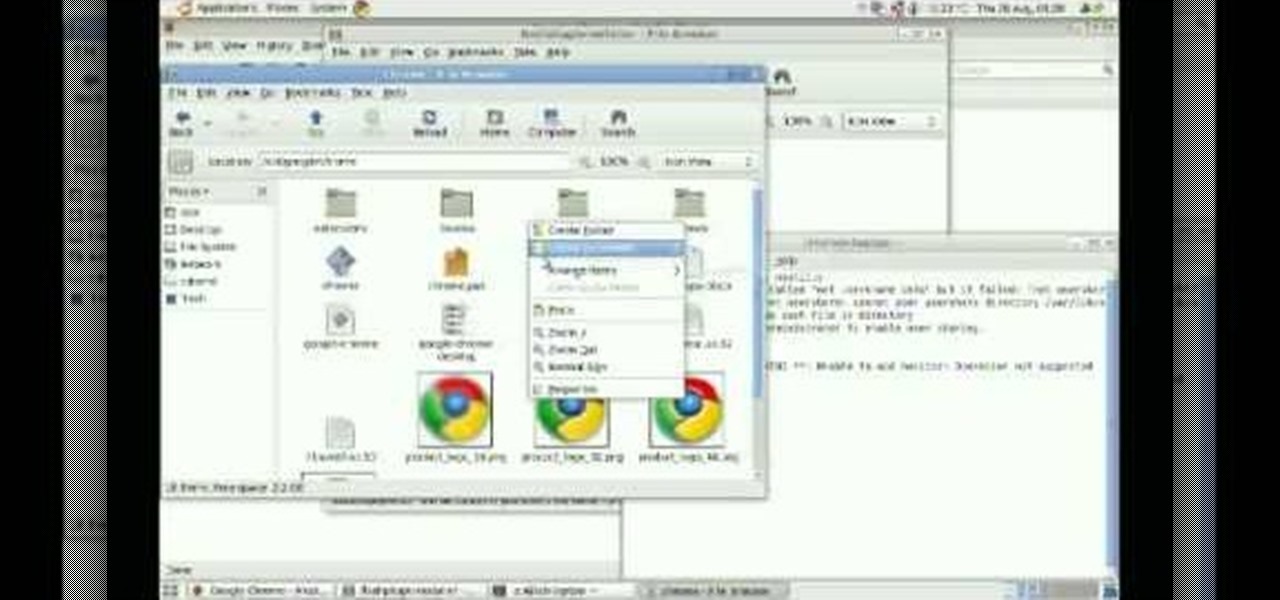
This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

If you want to run multiple windows operating systems at the same time you first need a Windows computer, the installation disk for the operating system you want to run, and Windows Virtual PC 2007. To install this, first type in Virtual PC 2007 to Google, go to the Microsoft link and download and install the program. Now, open the Virtual PC and click next on the wizard. Name your hard disk and click next until you choose where you want this at. Now your virtual hard drive is created. Now, p...

In this how to video, you will learn how get VMWare Fusion on your Mac. This will allow you to install Windows and run them on the same computer. First, go to the mediafire page and download the files. Next, download and install Unarchiver to join the files together and extract the file. Mount this file on to your computer. Run the file and click install. Once that is finished, open it. You will see your Windows partition if you already have one installed. To install a new one, click new and ...

On 4Runners equipped with the automatic climate control system, the left and right hand knobs control the temperature settings for the driver's side and passenger's side. To use it, switch on auto mode by pressing the ‘auto’ switch on the left hand knob so the amber light is illuminated. Then press ‘dual’ on the right hand knob so its amber light is illuminated. Rotate the left hand and right hand knobs to set your temperatures. The system will maintain those temperatures. If you want the who...

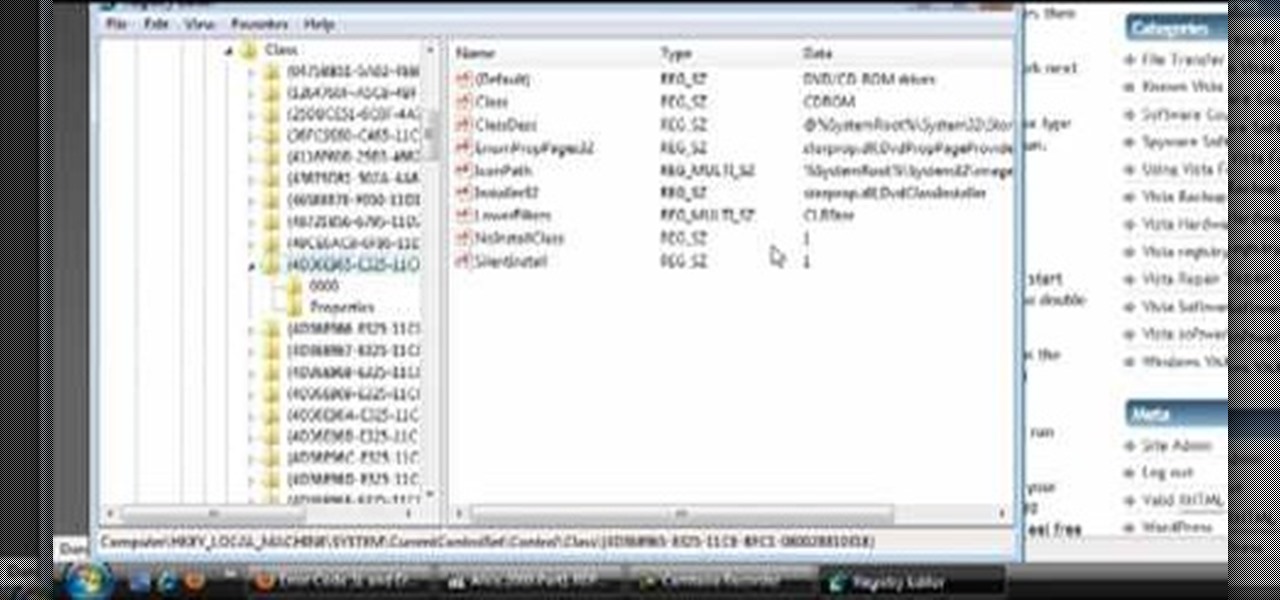
This how-to video explains how to fix DVD/CD player related issues with error code 31,32 or 19 in the computer that is having either Windows Vista or Windows 7 as their operating system.

Warts can be embarrassing – as well as contagious. Help minimize the chance you'll spread them to other parts of your body, or other people.

Check out this instructional RV video to learn how to maintain the LP gas system on your recreational vehicle. Open up the compartment and you will see your LP tank. There is a gauge that tells you how much is inside the tank, there is also a fill station where you fill it up, always make sure the cap is returned after filling it up, so no debris gets inside. There is also a pressure release valve so when you are filling it, the pressure can escape through there so you can get the proper amou...

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

Learn how to mount/install a twinplex CP4 chipset cooler into a PC.