
Today's Top News: GM Plays It Safe with Cadillac Autopilot
General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.


General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

It just keeps getting harder to enjoy all of the benefits of root without sacrificing features. Thanks to SafetyNet, we've lost the ability to use Android Pay, Pokémon GO, and even Snapchat to an extent. But the most recent news on this front is perhaps worst of all: Netflix has already stopped showing up on the Play Store for rooted users, and soon, it may refuse to run even if you've sideloaded the app.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.
The first public beta of Android O, (most likely to be called "Android 8.0 Oreo") was released on May 17, bringing tons of new features and goodies for Android enthusiasts with supported devices. However, not all of Android O's features were available to try out right off the bat. Possibly the single biggest feature announced during the developer preview of Android O, Picture-in-Picture mode, is nowhere to be seen.
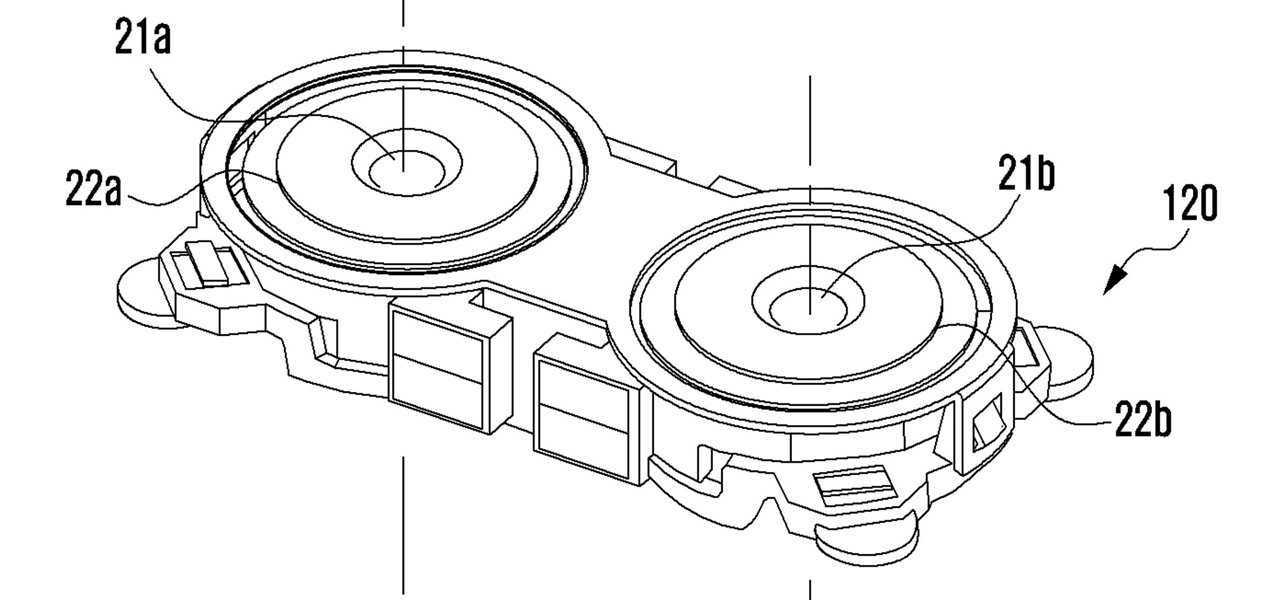
Dual cameras are increasingly popular right now for smartphones, but so far, Samsung has steered clear of all the hype. However, a new patent application shows that Samsung has been working on a dual camera system of their own, featuring tech potentially more advanced than what is currently on the market.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.

In a press event this past week at the Game Developers Conference in San Francisco, California, Unity Labs, the experimental and forward thinking arm of Unity, announced an upcoming toolset for developers in the augmented, mixed, and virtual reality space called the XR Foundation Toolkit (XRFT).

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

Joyce Kuo of Nijie Technology released a video showing a group fighting it out Dragon Ball Z-style in a restaurant, but instead of Goku, Piccolo or Vegeta, we have two horse-headed young ladies shooting fire and other elements at each other.

In recent years, wave after wave of technological advancement has led us down roads that are beginning to look more and more like science fiction stories. In their efforts to bring us from science fiction to science fact, Microsoft Research showed us a new communication medium called Holoportation earlier this year—and now they have found a way to make this highly complex holographic system far more mobile.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.
The Google Pixel and Pixel XL have an exclusive set of navigation buttons that you can't get on any other device without some tinkering. But aside from just being solid, filled-in shapes, the real treat in the Pixel's nav bar is the Google Assistant animation that gets activated by long-pressing the home button. The four colored dots that animate outward give you some visual feedback for triggering the Assistant, but really, it's just a nice little touch.

During the lead up to Samsung's Note7's release, rumors swirled about a leaked "Grace UX" interface replacing Samsung's maligned TouchWiz Android skin. In the end, this seems to have been nothing more than an internal code name that Samsung was using to test a few new icons and a slightly-redesigned Settings menu, because not much else has really changed.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Thanks to the strenuous efforts of our Gadget Hacks development team here at WonderHowTo, the fortified barrier segregating Android from iOS has finally fallen down.
Lollipop brought a complete visual overhaul to Android, and while the vast majority of changes have been met with praise, some UI tweaks missed their mark.
Emojis are a huge part of communication these days. In fact, I'm beginning to think that in a thousand years, historians will come across our then-ancient texts and speculate that we used a writing system that evolved from hieroglyphics.
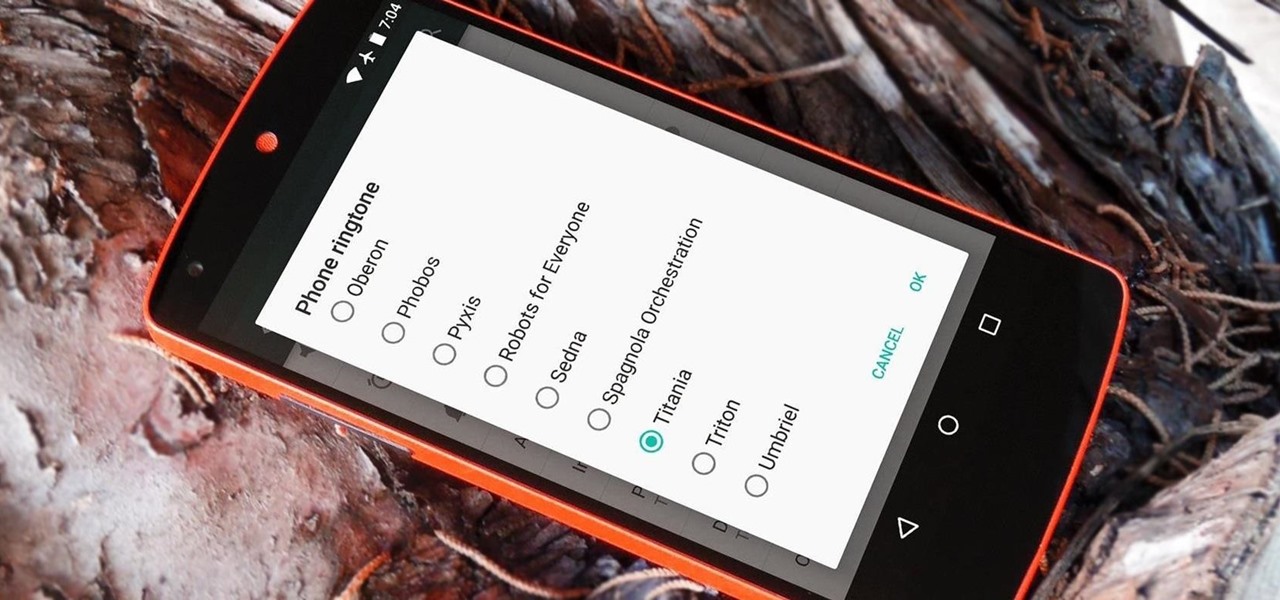
For some strange reason, when the Nexus 5 got its Lollipop update, the new stock system sounds were left out. These include updated versions of all of the ringtones and notifications, which Google revamped with a more mature sound that matches Android 5.0's elegant Material Design.

When Yosemite was released, a more detailed boot screen came to your Mac. So now, just like on Apple's mobile devices, you will see a loading bar telling you how far into the startup process you are. Apple also decided to add a black version of this boot screen to newer Macs, leaving those of us who purchased a computer before 2011 out of the loop.

Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTool. And now, developer Marcel Bresink has updated his app to work with Yosemite, so let's see what it can do now.
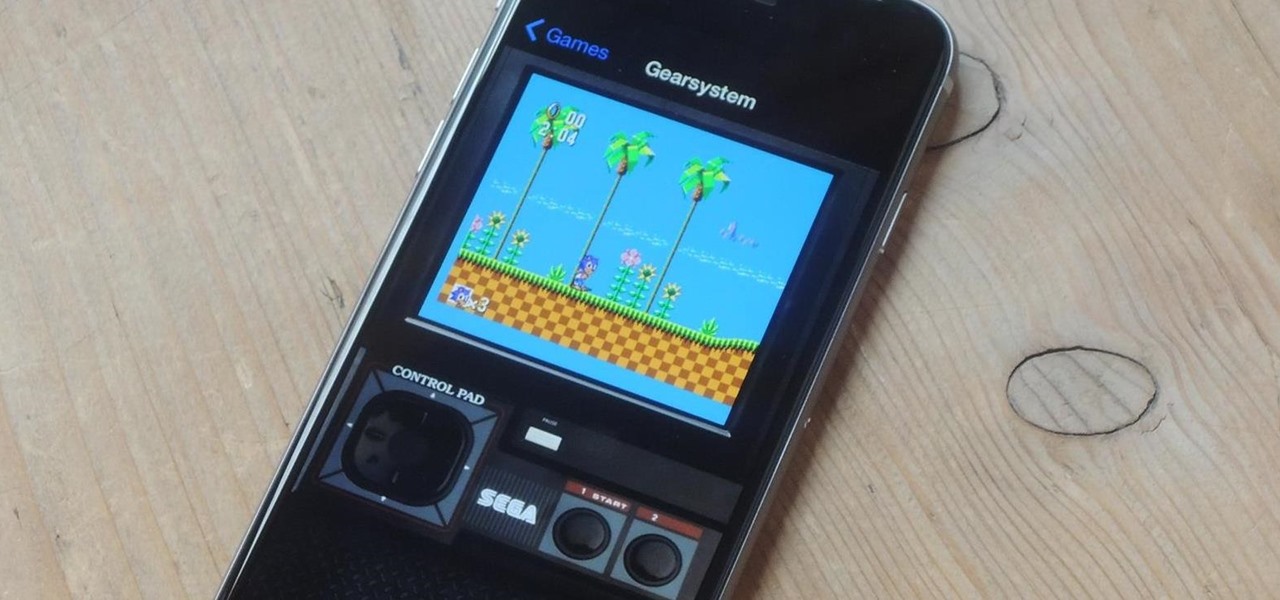
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.
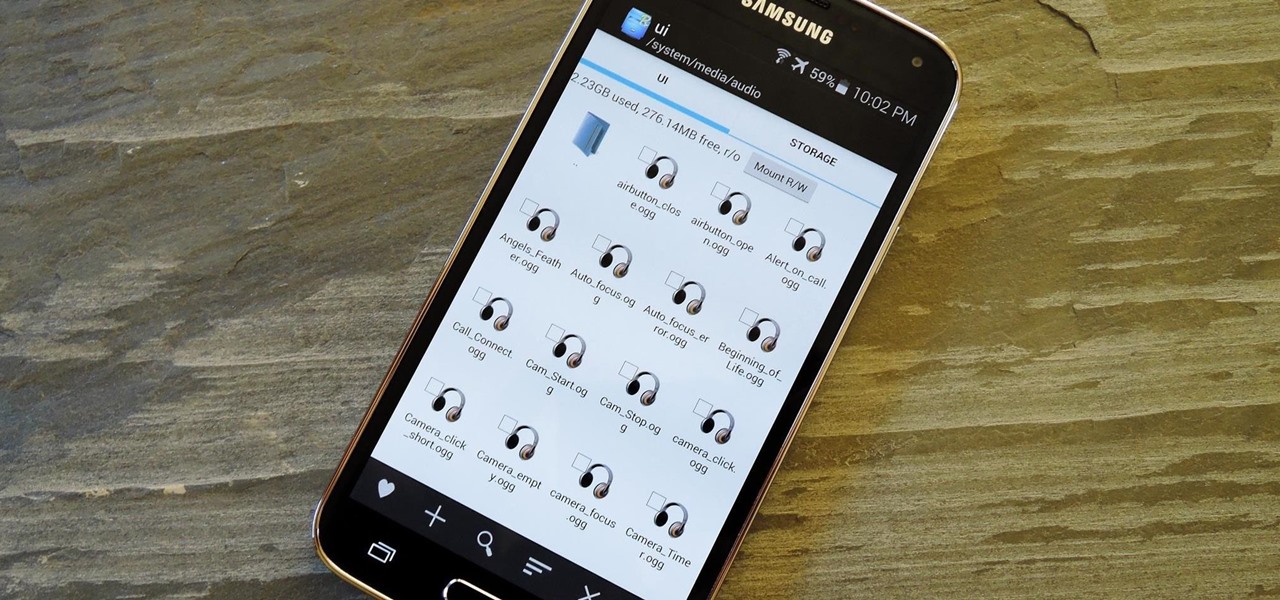
I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this phone, but I imagine they have some sort of equally annoying boot sound.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my aspiring hackers!

The new operating system for your Mac is here, and it looks fantastic—OS X Yosemite. At Apple's WWDC presentation, we were shown the new iOS-like aesthetics, as well as other awesome enhancements to the operating system. Improved Aesthetics