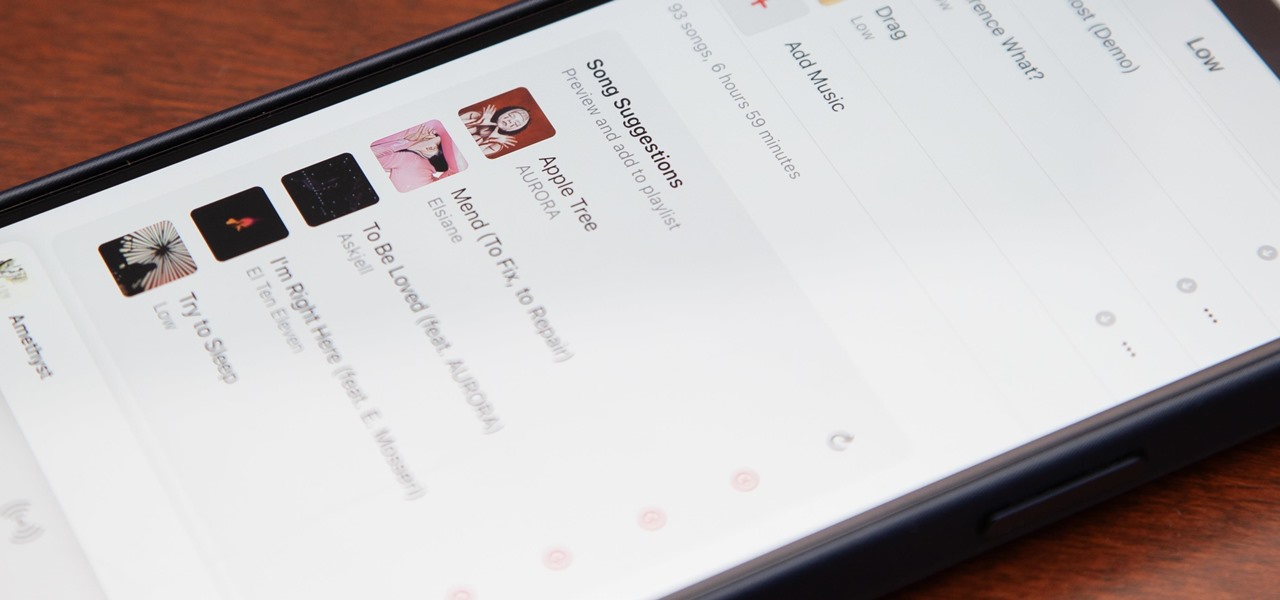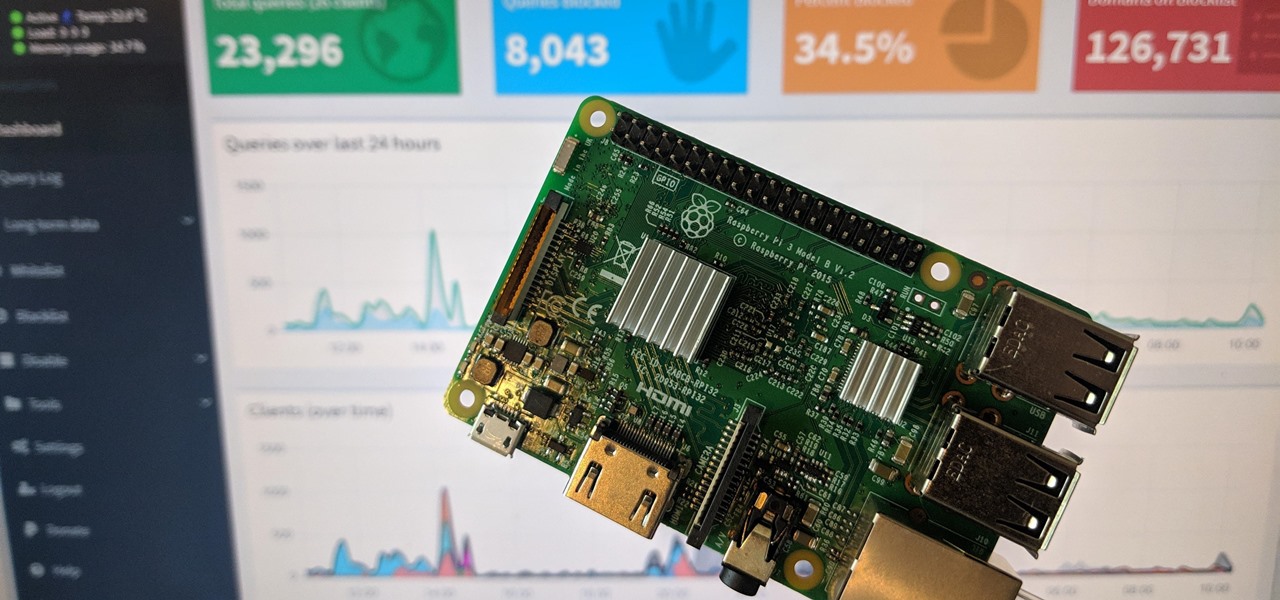
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.
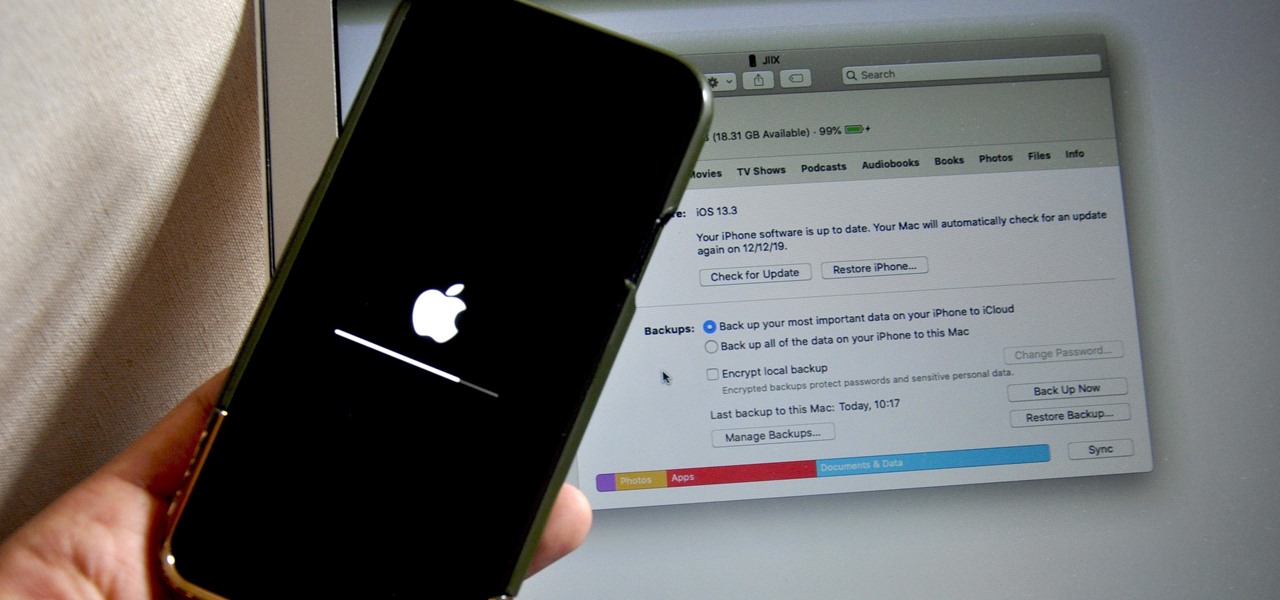
Restoring your iPhone from a previous backup is still a simple process using your Mac, but the way it works has changed since Apple killed off iTunes with the macOS Catalina update. Now you must use Finder to both back up and restore your iPhone, which can take a little getting used to.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Autism affects 1 in 68 children in the US, and that means it affects at least 1 in every 68 families. More boys than girls are diagnosed as being on the autism spectrum, and it's estimated that almost 60,000 12-year-olds in the US have autism. That is a 37-fold increase from the 1 in 2,500 children diagnosed just 30 years ago.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Does executing a perfectly timed, no-scoped headshot, followed by a well-choreographed teabagging ever get old? No, no it doesn't, and neither do custom emblems for Call of Duty: Black Ops 2. How else are we going to kill time until Black Ops 3 arrives?

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

Thought I would cross-post a piece I did a while ago.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

In recent years, Apple has made it much easier to customize the Home Screen on your iPhone or iPad, and some of the newer tools are perfect for neat freaks. Nonetheless, a tidy Home Screen can still feel cluttered when iOS and iPadOS force widgets, apps, and folders to have names — but a few workarounds can help you remove some of those icon labels for good.

Over the past few weeks, Google, Snap, and Facebook have all taken their turns to show off their new augmented reality technologies. This week, it was Apple's turn, with new AR features for iOS 15 along with new capabilities for developers.

Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you stop it? Not officially, but there are workarounds.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

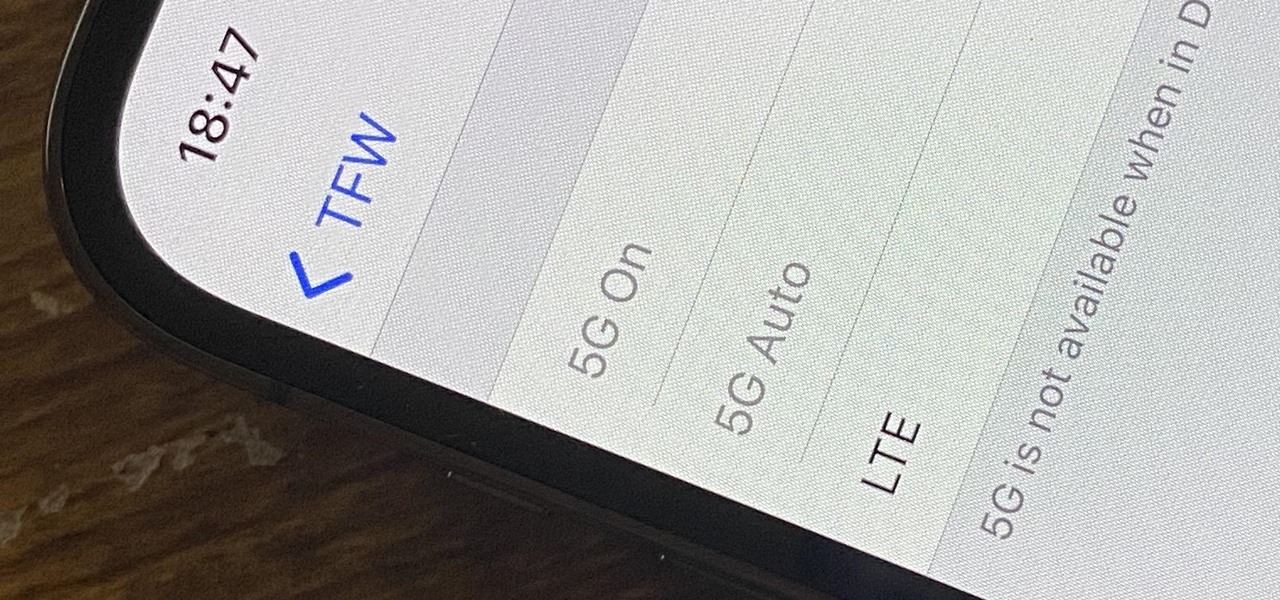
One thing you can expect from Apple is that big features work right out of the box. The company designs its products to be easy to use for any experience level, so you might expect the same to be true for 5G, one of the biggest selling points for the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max. Yet, you might have trouble getting 5G to work on your brand new iPhone. Here's how to avoid that.

Wearing masks and social distancing doesn't sound like a fun movie night with friends, but you can still be comfortable and watch films together remotely. Services like Discord and Netflix Party make it possible to watch movies simultaneously from different parts of the U.S., and now you can do it with Movies Anywhere too.

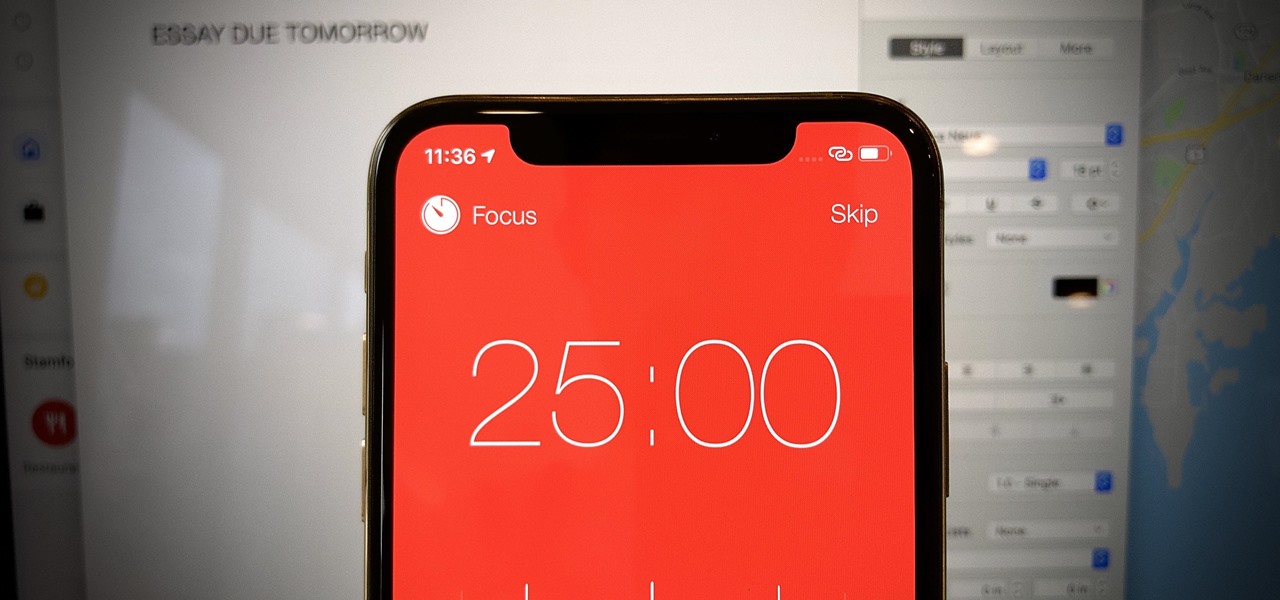
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Many lazy cooks skip rinsing off their grains before they cook 'em, but that's a big mistake for a few reasons. Some grains have coatings on them that need to be rinsed off to cook properly and taste good.

The very first banknotes were used by the Chinese in the 7th century, during the Tang Dynasty. Before it was used as an actual currency, paper money was part of a deposit system in which merchants would leave large amounts of coins with a trusted associate and receive a paper receipt for the transaction. The reason was simple — the copper coins used as currency then were heavy.

Tomorrow's the 1st of April which means it's the one day of the year you can put aside the daily grind, and go at it Dwight Schrute and Jim Halpert style. Yes, there are easy apps to do your dirty work, but if you're old school and you like to do it the old fashioned way, here are 10 simple pranks for torturing your co-workers.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

Killstreaks: Advantages and Disadvantages 3 Kills – Spy Plane: Advantages: This lets you see enemies on the radar in the upper left hand part of your screen. Though it is one of the lowest killstreaks, it is very beneficial and gives you a huge advantage. Disadvantages: It can be shot down and it will not detect enemies who use the ghost perk.

This video will teach you how to kill bacteria in dirty water, in the wild, with only a plastic bottle, a string and a lighter or match. Kill bacteria in dirty water.

All right women are you sick of playing games like GTA where you kill hookers? In Hey Baby you get to kill all the men who've been harassing you on the streets!

In this how-to video, you will learn how to make a kill shot in racquetball. Do not worry about hitting the floor first. Many players new to the game will worry about hitting the floor and hit the ball too high. Practice aiming an inch off the floor. It is generally easier to work your way up rather than down. Aim about a foot into the floor before the front wall. If you are aiming too high, keep this in mind. By watching this video, you will be able to make better kill shots and improve your...