This video demonstrates the technique to setup a Yahoo email on an iPod Touch. You start going into settings and then clicking account. On the next screen you will click "Other" and then click on "Pop". At this point you enter your name and email address that you use for your Yahoo email account. Incoming server or host name is "pop.mail.yahoo.com", next is the username (which is your yahoo email address without the @yahoo). You will then enter your password and the out going smtp server whic...
Open an image and on the layers panel add a new layer by clicking on the fifth icon below the layers panel. A new layer is created with the name 'layer 1' and your previous layer would have the name 'background'. These names can be changed by you. For now we'll leave them as they are.

Vampire make up on a man by M.J. It starts by saying an introduction by him that his name is Dracula and her girl friend name is M.J., takes a white powder to set a white makeup to the face with the help of brush then use the color flam able apply the color all over the eye, takes eyes shadow color called electro-red by applying to the eye by brush then applying the color MAC night divine with eyes shadow brush. To be perfect while applying and finally take red lipstick and apply to the lips ...
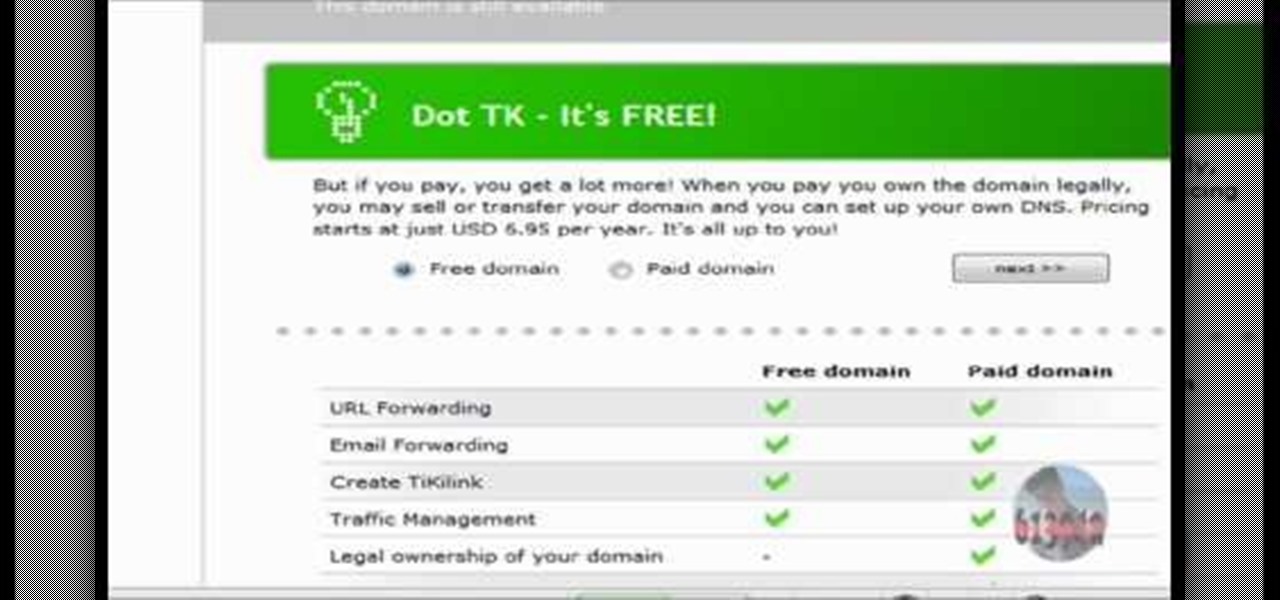
In this tutorial the author shows how to use a proxy at your school and get on the blocked site like MySpace etc. Now he points to the Dot.tk website and how to access it from Google.com. Now if you want to access any website you just need to copy the link and paste it into the pointed field in the Dot.tk website and now you can choose a new domain name for the website. Now you can choose the free domain option in the next page where the new website is setup. Now he shows how to go through th...
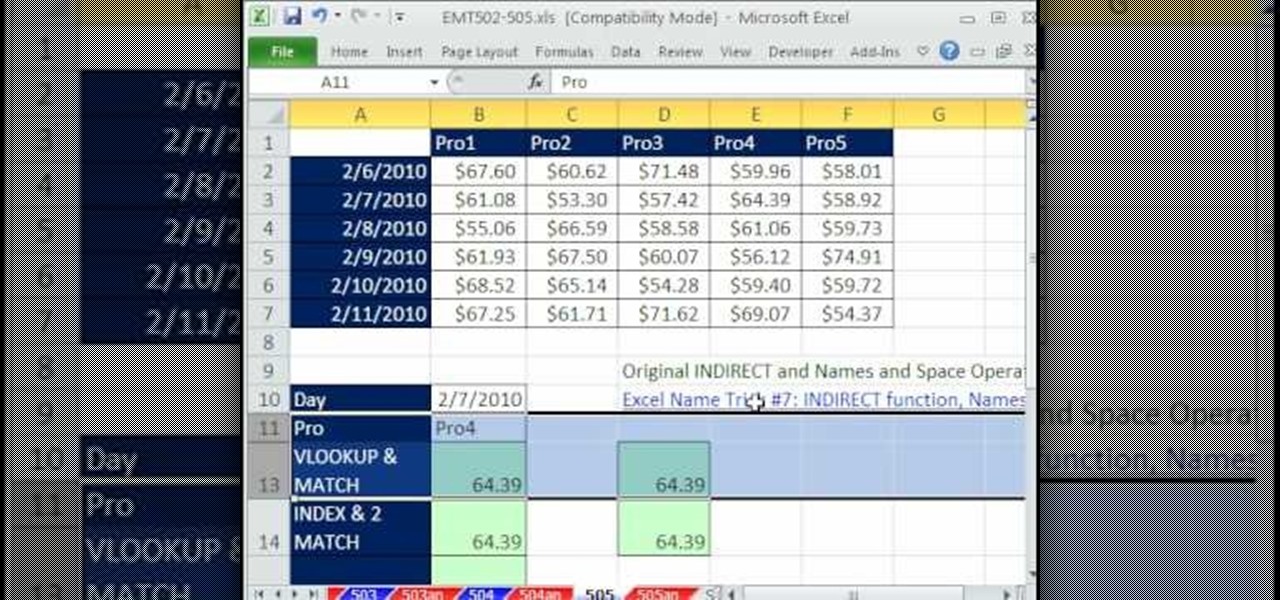
ExcelIsFun will show you how to use indirect text and substitute in Excel. Select any date and product and create an intersession. Use Vlookup to look up your columns. Use the match function to find the value range. To do the same thing with dates, highlight the dates and names. You then let the name look for indirect. Your space operator tells you two ranges to find the intercept. Take the text and substitute for the dashes. Use the text function on the value and format it.
1. On the browser, type www.weebly.com. If you are a new user, then sign up. Write your username, email, password, and click on Sign Up and Start Creating.

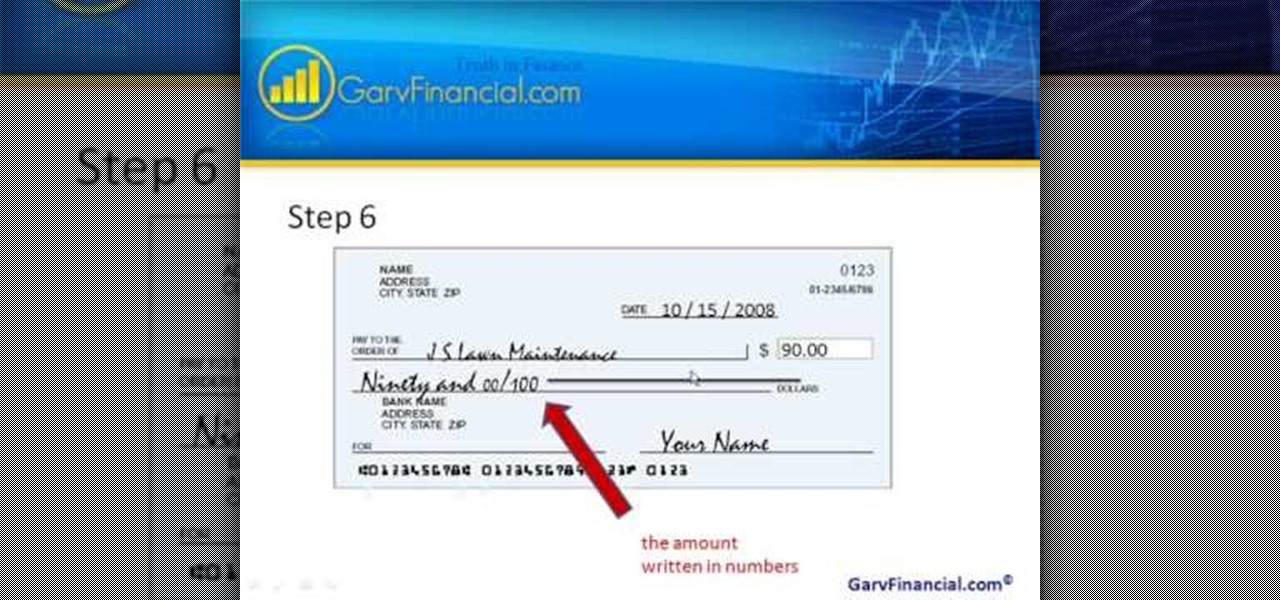
Here are step-by-step instructions on how to write a check. 1. Date the check, and ensure it is dated for the day you intend the recipient to cash it.

Many videos out there tell you about how you need to SSH into your iPod touch or iPhone in order to do certain things. But what does this mean? This video explains how to SSH into the iPhone or iPod Touch using WinSCP.

Researchers have found that there are simple things anyone can do to appear more appealing. You Will Need

Having problems with your anti-virus software on Windows? Learn how to remove the fake virus protector Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer. Personal Anti-Virus is hard to get rid of and is totally annoying. To get rid of it, you don't have to download anything.

What would be cooler than showing up at your prom with a famous celebrity? It's a long shot, but here's your best chance to make it a reality.

If you get looks of exasperation whenever you stammer out a drink order, take this crash course in bar-speak.

It's time to discover how fun art and drawing is! Learn how to draw the anime and manga character Tsunade the 5th Hokage from Naruto. Drawing is a way of creating and expressing ourselves, and therefore the result is always beautiful.

Learn how to play "The Way I Loved You" by Taylor Swift, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Learn how to play "Gamma Ray" by Beck, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

The origin of this classic sandwich is uncertain but legend has it that it comes from the 1930's Conti's Grocery out of Patterson, N.J.. The sandwich got it's name "Submarine" from the Groton Navy Submarine Base in Connecticut. During World War 2, this huge sandwich was fed to returning sailors and solders because it was quick to prepare and inexpensive to make! This classic sub is essentially a 12 inch Italian bread stuffed with cold cuts including salami, prosciutto (dry cured ham), capicol...

Watch to learn how to say the names of things that have to do with school, like books, paper airplanes, and soccer balls, in French.

Watch to learn how to say the names of things you use in the kitchen, like plates, colanders, and the stove, in French.

Watch to learn how to say the names of the types of things you find in an antique store or at a flea market in French.

Watch to learn how to say the names of some types of beverages in French. une boisson au citron - lemon drink

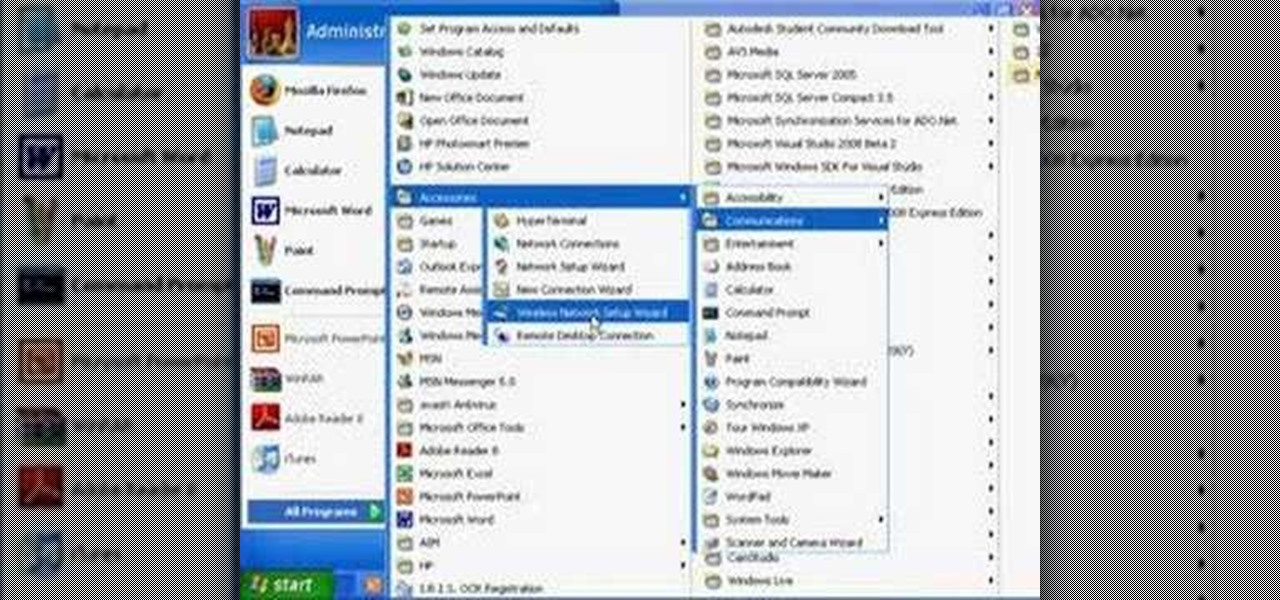
Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

I have always favored a neat and tidy Home Screen on my iPhone, and one of the best ways to achieve that is by removing all the app, folder, and widget names. With a few workarounds, you can do this on iOS 17, but Apple finally just gave us an official feature on iOS 18 to hide app, folder, and widget names on the Home Screen. And it also works for iPad on iPadOS 18.

Many streaming services offer user profiles for different people in your household, some of which also include profile images. In most cases, you can set a custom profile image to better differentiate and personalize your account from the others, and HBO Max lets you do the same, albeit, with limited options.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

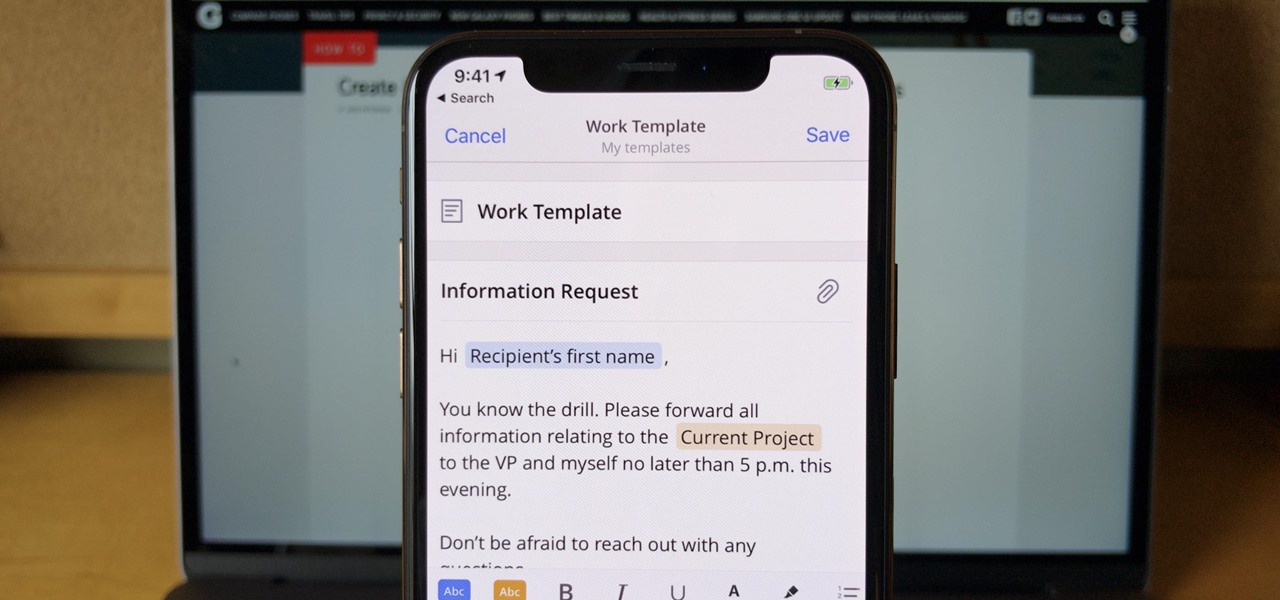
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced to label them? Technically, we're not, since there is a workaround in iOS 12 and iOS 13 to make those labels disappear for good.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

In case you missed it, you don't have to chat one-on-one anymore in Snapchat. The company added group chats back in 2016, and they are increasingly gaining new features such as video and audio chats, so communicating Snapchat-style with all your friends at once is better than it's ever been.

Along with the awesome early-2018 addition of Giphy GIFs in Snapchat, you can now share other people's Snapchat handles and tag them in a way that lets others reach those people easily — something you couldn't do before in the app.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

It looks like Magic Leap is getting its ducks in a row to launch its Magic Leap One: Creator Edition as the company's name is once again showing up in US Patent and Trademark Office (USPTO) filings.

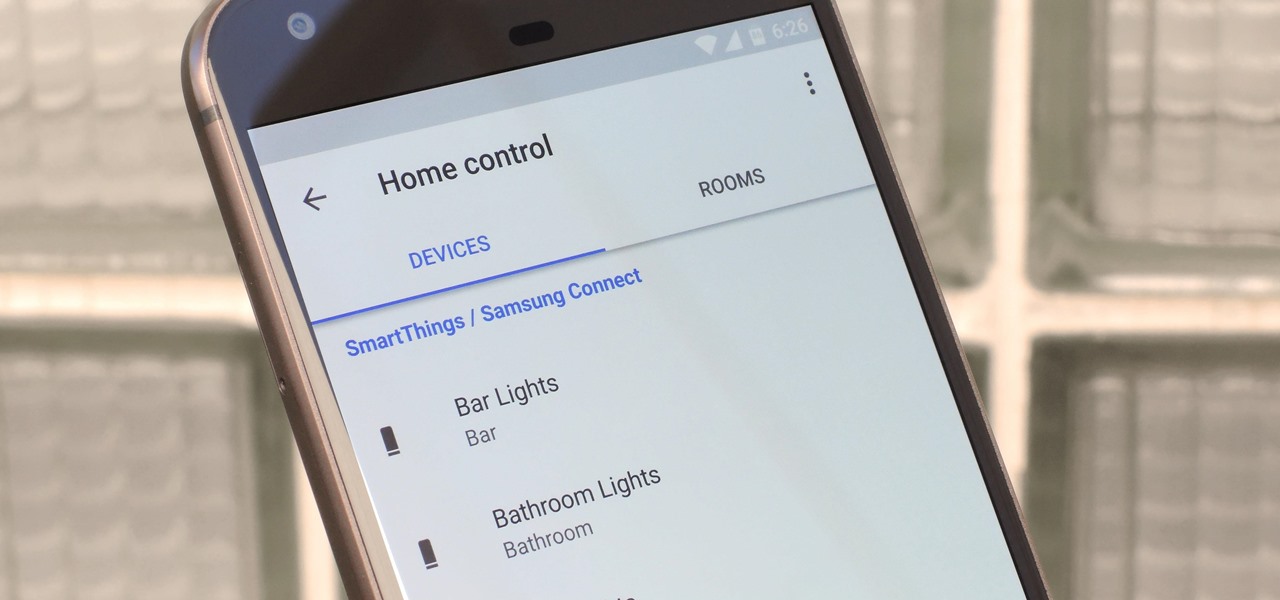
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

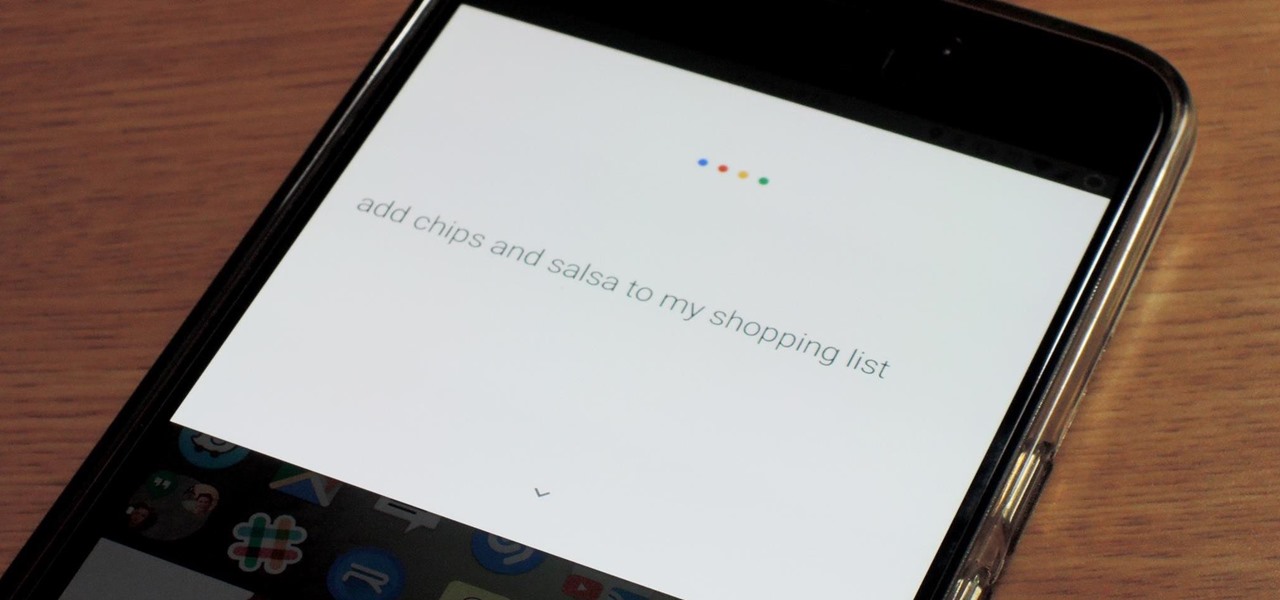
If you use Google Keep, you'll be happy to know that you can add items to lists and even start new ones with "OK Google" voice commands on Android, and it works fairly well. (Hat tip to Reddit user rambantu for finding this trick.)

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

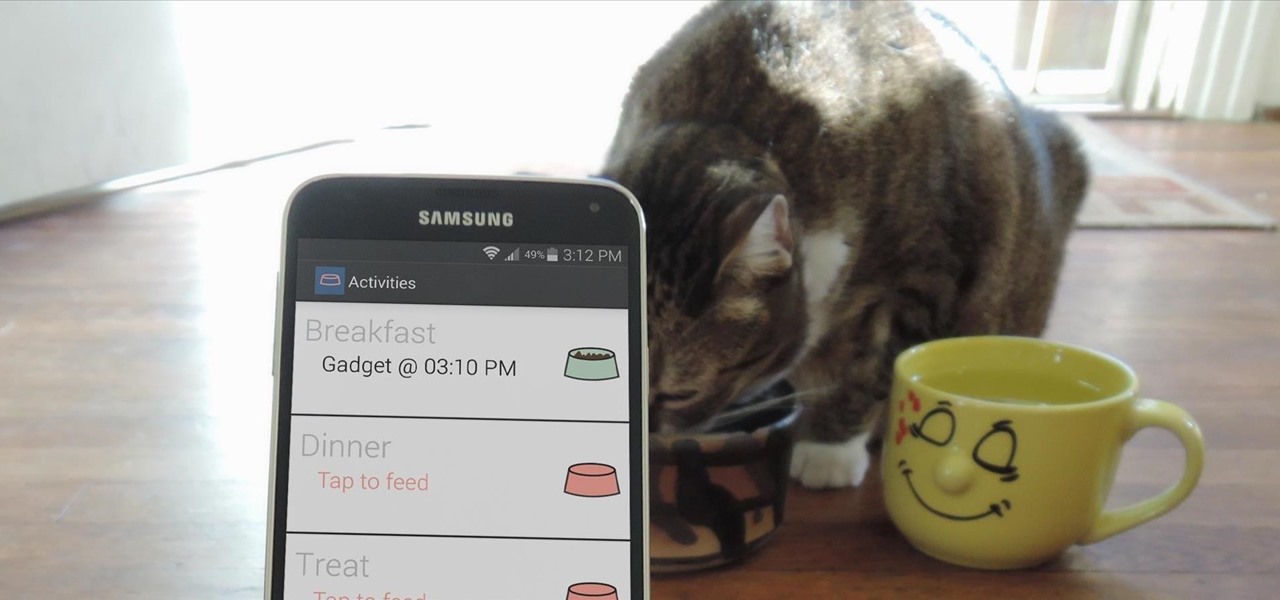
Pets are one of the biggest sources of joy in life, but keeping track of their daily activities can easily become a chore. When you have a roommate or spouse that also likes to feed the cat or walk the dog, miscommunication can lead to double-feeding or an under-exercised pet.