
How To: Speak Elvish, created by Tolkien
Attention Tolkien fans... Ever wanted to learn to speak Elf? In this video, learn the vowels, consonants, numbers, and how to write your name in "Elvish".


Attention Tolkien fans... Ever wanted to learn to speak Elf? In this video, learn the vowels, consonants, numbers, and how to write your name in "Elvish".

Get some tips on using watercolor for your art drawings. This video tutorial will show you how to use draw leaves for a nature journal. If you're new to drawing with watercolor pencils, like the Prismacolor Watercolor pencils, this will help you out, especially to help you learn the leaf part proper names. Also, see how put the leaves in a plant press.

This instructional how-to video walks you through the step by step process of the dancing warrior yoga asana. An asana is a more common name for a yoga pose. Follow along and learn how to do the dancing warrior pose.

Take note of these tips when developing your own unique cartoon characters. Your drawings will turn out much more interesting if you think about the details of their personalities. Take inspiration from your own life. Give your character a name. Figure out what your cartoon character likes and doesn't like. Keep a sketchbook of all your invented cartoon characters.

Learn how you can play your Dm 3rd positions licks over 11th position in Bbmaj. This demonstration uses a C diatonic harp. Watch this how to video and you will be able to play licks in the 3rd positions and 11th position on the harmonica.

Vinegar and baking soda (and red food coloring if you're going all out) combine to make quite the little explosion. After you've made a little paper volcano, watch this video tutorial and learn how to carry out a really easy science experiment. You've probably made a volcano before, but you're never to old to make a mess in the name of "science."

Watch this guitar tutorial video to learn how to play "Som Sarn" by Sek Loso on electric guitar. Instruction includes names of chords. Beginners will have no trouble learning how to play Sek Loso's "Som Sarn" on electric guitar by watching this helpful how-to video.

Watch this guitar tutorial video to learn how to play "Hluas Nkauj Hmoob" by Destiny on acoustic guitar. Instruction includes names of chords. Beginners will have no trouble learning how to play Destiny's "Hluas Nkauj Hmoob" on acoustic guitar by watching this helpful how-to video.

Watch this guitar tutorial video to learn how to play "Sometimes You Can't Make it on Your Own" by U2 on electric guitar. Instruction includes names of chords. Beginners will have no trouble learning how to play U2's "Sometimes You Can't Make It on Your Own" on electric guitar by watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Shout to the Lord" on piano. Instruction includes names of chords and an overhead view so you can learn by watching. Intermediate pianists will have no trouble learning how to play "Shout to the Lord" on piano by watching this helpful how-to video.

Watch this piano tutorial to learn how to play "This is How We Do" by the Game and 50 Cent on the piano. Instruction features chord breakdowns and individual melody note names. Beginners will have no trouble learning how to play the Game and 50 Cent's "This is How We Do" on piano after watching this helpful how-to video.

Watch this dance how to video and learn the Charleston Variation: Savoy Kicks. The Charleston is a dance named after Charleston, South Carolina. The dance became popular in the USA after the swing jazz 1923 song "The Charleston" by composer/pianist James P. Johnson came out. The Charleston soon became one of the most popular hits of the time period.

In this English language tutorial we look at fear and being afraid. There are many words to convey the emotion of fear and anxiety. This ESL lesson teaches you how to talk about your fear and the names of some common phobias.

The cobra footwork is a straight line footwork speed skating technique. This trick was named after the "Cobra" snake for its snake like movement, or slither across the ice. Skate like a cobra. Fast and furious!

A meze is a Greek term for small plates of food served with wine at parties. This delicious pork meze gets its name from the wine that is used to braise the meat, resulting in rustic Greek cooking at its best.

Learn the names and patterns of some typical Greek buzuki (bouzouki) rhythms like the tamiko, kalamatiano, zembekiko, and ipirotika.

An opening strategy used by Black to have a strong attack against White queen/pawn openings. The Benoni Defence and variations have been used by the likes of Bobby Fischer and Kasparov, to name a few. Learn it!

Can’t remember names, dates – or even why you walked into a room? Luckily, there are lots of things you can do to increase your memory power.

Cupid teaches everyone how to do the Cupid Shuffle from the song of the same name.

This is 20 gauge, dark, annealed wire. The common name is stove wire or you can use something you have probably heard more of, safety wire. This video shows you how to use it to make a bolt leader in case you messed up the one that came with your trailer.

According to Japanese legend, folding 1,000 paper cranes in one year will guarantee your wish will come true. A young girl named Sadako did just that in 1955 and wished for world peace—the origami crane has been an international symbol of peace ever since.

Benny from askbenny.cn teaches you the names of some common pieces of stationary and office equipment in Mandarin Chinese and how to talk about them.

Takanori Tomita shows you how to write in Japanese using katakana. Find out what Katakana is, and how to write names or non-Japanese words in Japanese by using Katakana script.

In After Effects 6.5, Adobe introduced Incremental saves. Rather than waiting for the auto-save to catch the latest revision to your project, incremental save allows you to manually save a new file, incrementing the name of your project in numeric integers. CINEMA 4D does the same. And with a little configuration, you can make it act exactly the same as in After Effects.

The name may be a bit of a tongue-twister, but we're sure you'll think this healthy dish is a taste-bud twister as well! Patricia Fine, MD gives step-by-step instructions how to make non-dairy penne with fennel pumpkin pasta sauce and gives you some secret tips for keeping the sauce creamy.

Follow along with an overeager young magician named Dergen Brown as he teaches you how to do a classic pass card move. If you can ignore the comedy effort in the beginning, you'll learn this basic technique.

Is the emoji you're using really the one you think it is? While you can use any emoji that looks like it fits what you have to say, it may have been created for a different purpose. On an iPhone, it's easy to find that purpose by retrieving the actual name of the emoji in Apple's operating system.
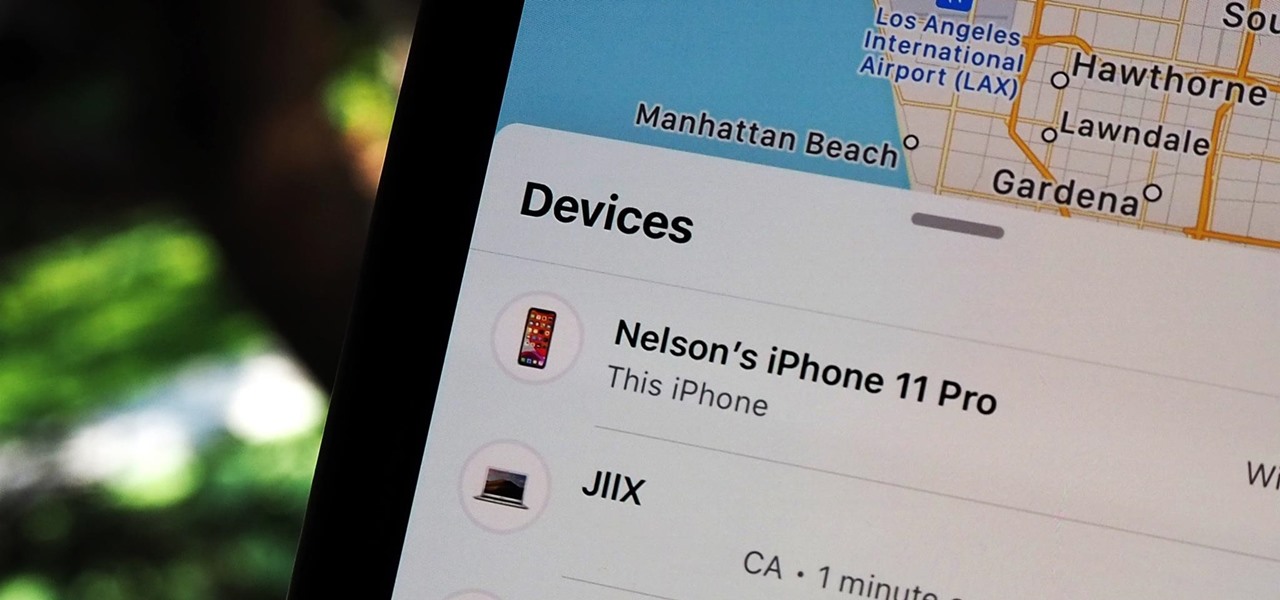
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.
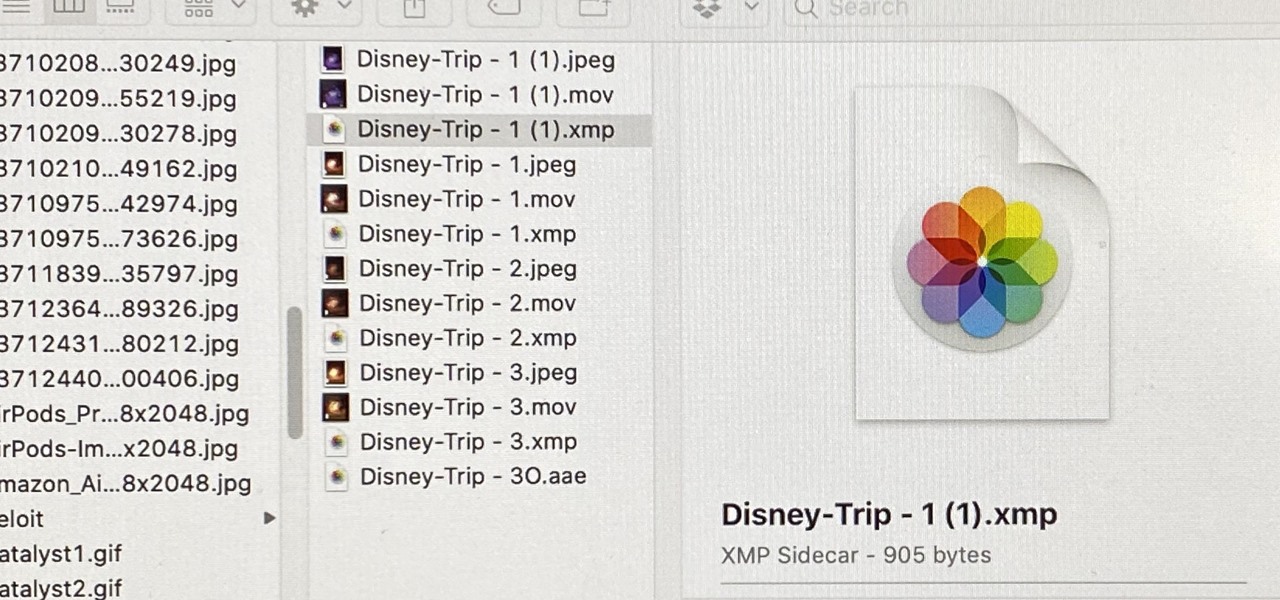
When you export an image from the Photos app in macOS, you may not be getting the whole deal. In the export menu, you need to select either JPEG, TIFF, or PNG, and if you don't make any adjustments to the quality settings, it'll likely be compressed. If you need the original full-resolution file or want to get the video that's attached to a Live Photo, there's a simple way to do it.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.
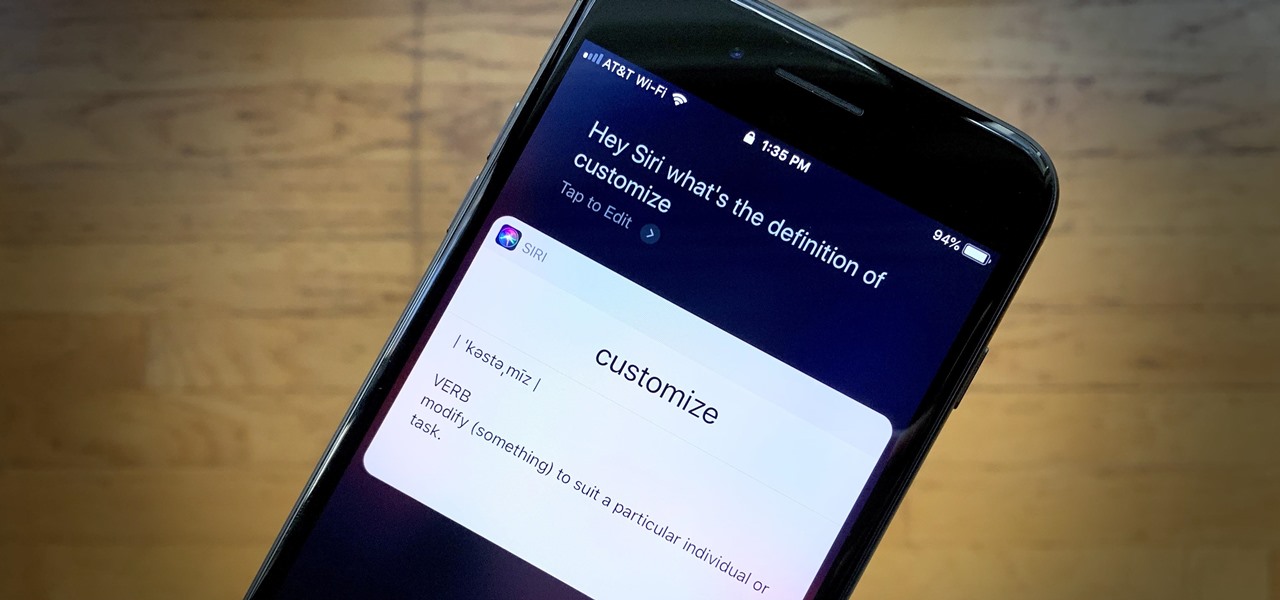
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Instagram stories are a great way to share your day-to-day experiences with your followers. However, it can be disappointing to see them go after 24 hours, especially if you shared something really special. Now, Instagram has a way for you and your followers to relive those great stories you've created with a new feature called Story Highlights.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.