Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

Is this what happens when lightning hits sand? It turns out that when lightning hits sand, it makes little holes in it. Sadly, this picture was part of an internet hoax that circulated in 2013.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

One shrinks their nose when the name of Durian fruit is brought up but are you aware of all the health benefits it can provide? The Durian fruit on its own can help control Blood pressure, blood sugar, Anaemia and depression. Not only this, the fruit has the miraculous qualities that can prevent cardiovascular diseases, better the digestive system, better the Libido and provide instant energy. For all the skin conscious people, here's news for you! The fruit can delay ageing process and make ...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

To play Minecraft with mods you will need to install Forge. Most people think this is hard to do, not so. It is very simple and in less than 5 minutes you can be playing Modded Minecraft.

A man by the name of Marc Kerger is out to prove that he's the number one fan of the game TETRIS by building a playable TETRIS shirt for the game's 30th anniversary.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

This is for people who are already proficient at doing basic pull-ups and chin-ups and want to take their training to the next level. It's also pretty funny for anyone who enjoys a bit of gym humor.

Learn how to make a paper origami teo flower instructions. This origami flower is my improvisation, and I haven't seen any similar flower from the nature. I named the flower to my wife Teofila (Teo) because i gave to her the first model of a complete paper flower :). The model is easy and the stamens make the flower looks one idea more beautiful :)

Say "hola!" to the independent Finnish phone company, Jolla, and its new eponymous smartphone of the same name.

On June 5th, robotics firm Aldebaran and SoftBank Corp., the Japanese giant that owns Sprint (and possibly T-Mobile), unveiled an emotion-sensing robot named Pepper.

Video: . Iconici Tv MMA Host Naiya Marcelo caught up with with Bellator middleweight fighter Brian Rogers "The Professional Predator" at Factory X Muay Thai/MMA/BJJ Gym in Englewood CO.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

This magical, glowing mixture is very strange, with an equally strange name (Oobleck), because it feels like moldable pizza dough in your hands one second, and like liquified goo the next.

Video: . How to Remove a Callous from your Feet.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

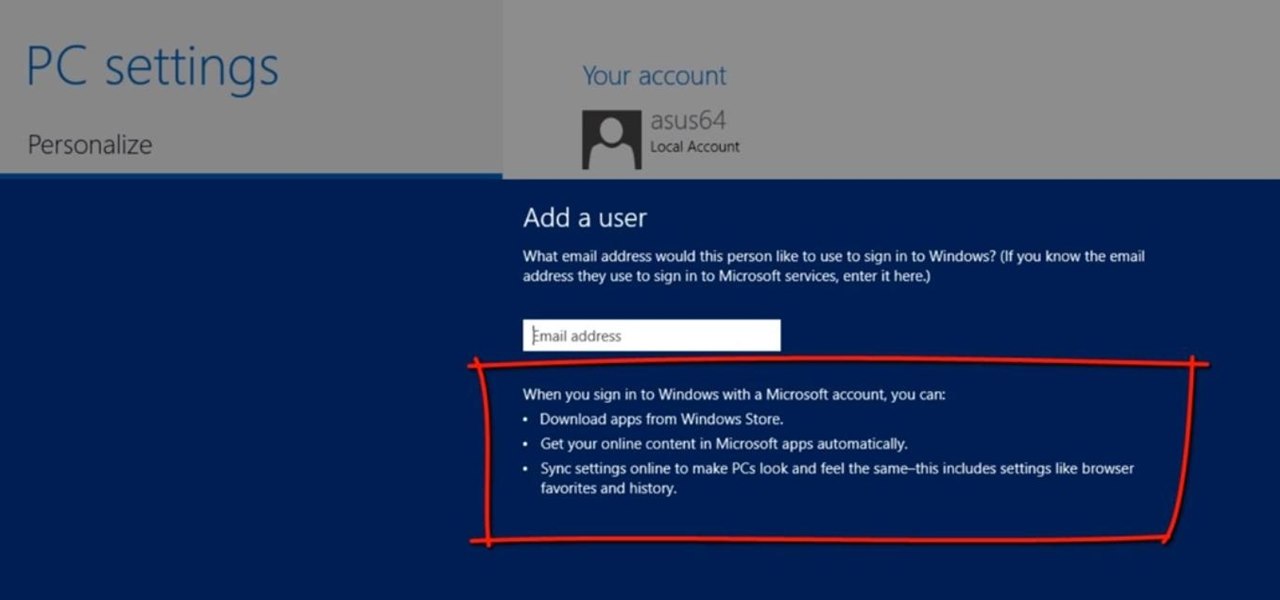
This Windows 8 tutorial will show you how to create a local user account on your PC. When you create a local user PC account, you will only have access to your account from that individual computer. A local Windows 8 user account uses a user name and password to login.

Video: . Steel wool fire Photography

When I started this nail design, I really didnt know what I was going to end up with, and much later till the design was posted, I didnt know what to call it either ! But a viewer noted that it is a very christian style because of the cross and the arches that look like the windows of a church, and lots of others talked about the cross on the ring finger . With a bit of help and lots of ideas, I eventually names this design Christian Dior Nails - Blue Cross Glam Nail Art Design with Easy Abst...

RonyaSoft Poster Designer software includes lots of different ready-to-use templates. You can freely change anything you want in the template or you can just print it as it is, if you don’t want to puzzle over it. Moreover, you can create your own poster from scratch.

In this how to video, you will learn how to convert DVD movies to AVI or any other type of file for free. First, you will need to download DVDx 2.1 and the install it. Next, open the program and insert the DVD disc you want to copy. Go to file and click DVD root. Find the video and select the video_ts folder. You will see the IFO files. Look for the one with the longest time. Click on this one and press select. If you have a DVD already ripped on your hard drive go to file and click open IFO....

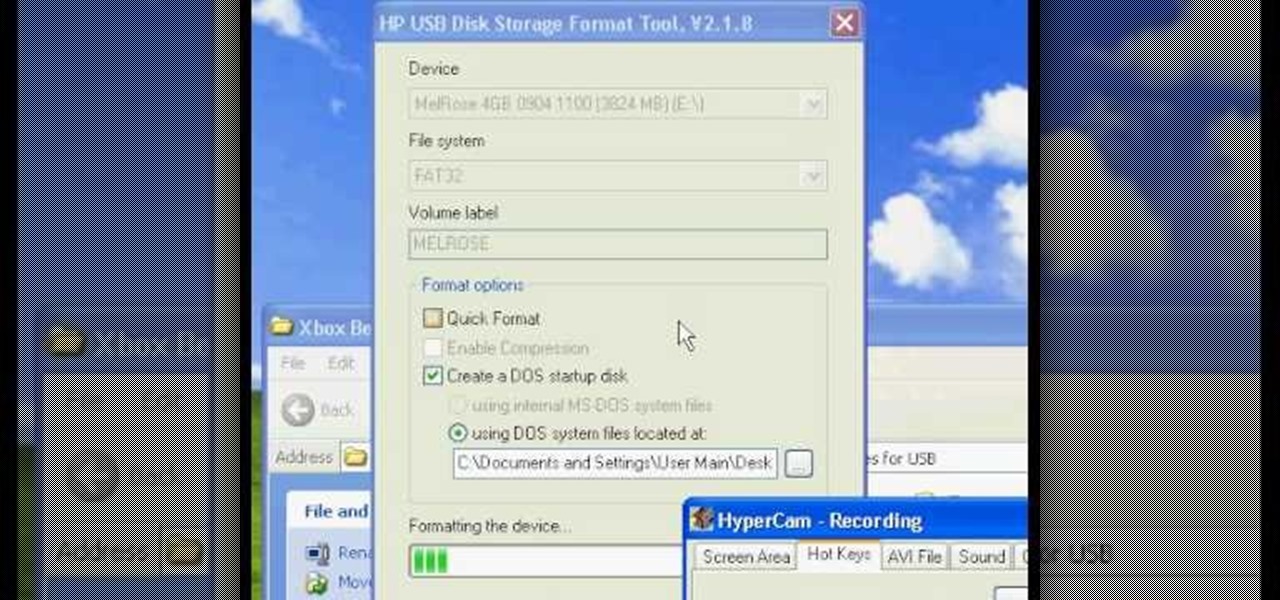
Have you ever wondered how to prepare a USB drive to flash an Xbox 360? Here is the how-to -video on how to create an USB drive for flashing your Xbox 360 benq drive. To make a bootable flash drive and to prepare it to flash XBox benq drive you have to download the “Xbox benq flashing files for USB” folder from the below mentioned link.http://www.MegaShare.com/1721713

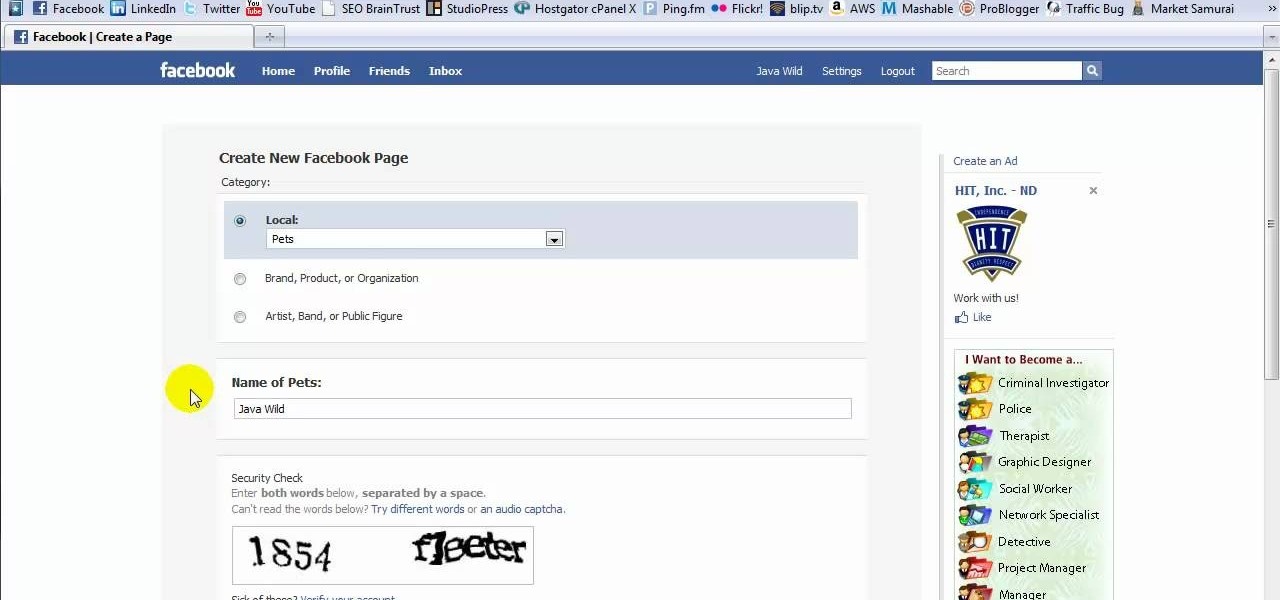
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Some Chinese dishes that sound healthy are surprisingly fat-laden. These tips will help you avoid diet land mines.

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.