
How To: Chroma Key with Color Range in Photoshop
This Chroma keying tutorial shows you how to use Color Ranger in Photoshop to remove a solid background.


This Chroma keying tutorial shows you how to use Color Ranger in Photoshop to remove a solid background.

Learn how to play this boogie woogie blues lick in the key of C on the piano or keyboard.

Learn how to use the low key lighting technique to take darker pictures.

With tips from this video, play a Hawaiian hula tune on the ukulele. Start with the key

Chef John and his mother show us how to make her key lime pie.Here is the recipe:it will make enough for two pie crusts. You need salt, flour,shortening,ice water.The filling requires 3 eggs,3 limes, sweetened condensed milk, green food coloring whipped cream, and lime zest.

Israel Hyman shows yow how to use the sun as a key light for film, video, and photography, including how its angle affects your subject’s look.

This is a tutorial on basic chroma keying with Adobe Premiere .

Learn how to make a cool monogram key chain that holds post-it notes.

See how to use chroma keying in Photoshop. This technique is most often used to remove green screen backgrounds from images.

This tutorial tells you how to use pitch and speed in GarageBand '08. In GarageBand '08, they work independently from each other to allow for greater control of key and tempo.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

Learn a stunning effect by just remembering one card. The key card! Follow along as our British headless magician teaches you how to perform this basic magic trick.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.
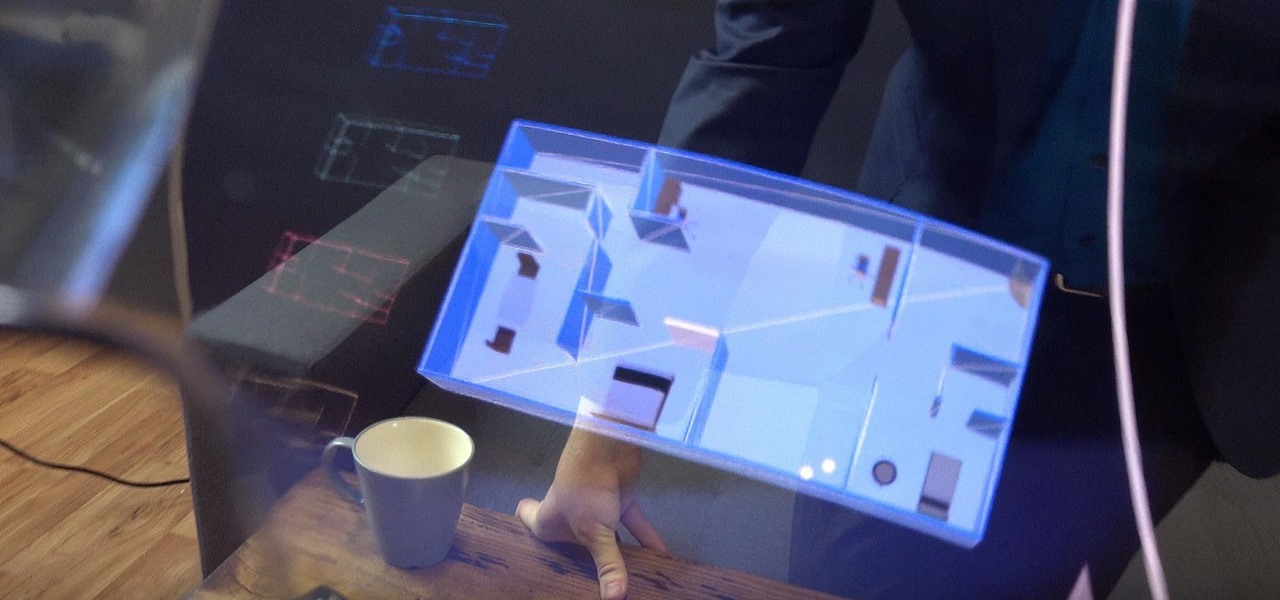
In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.
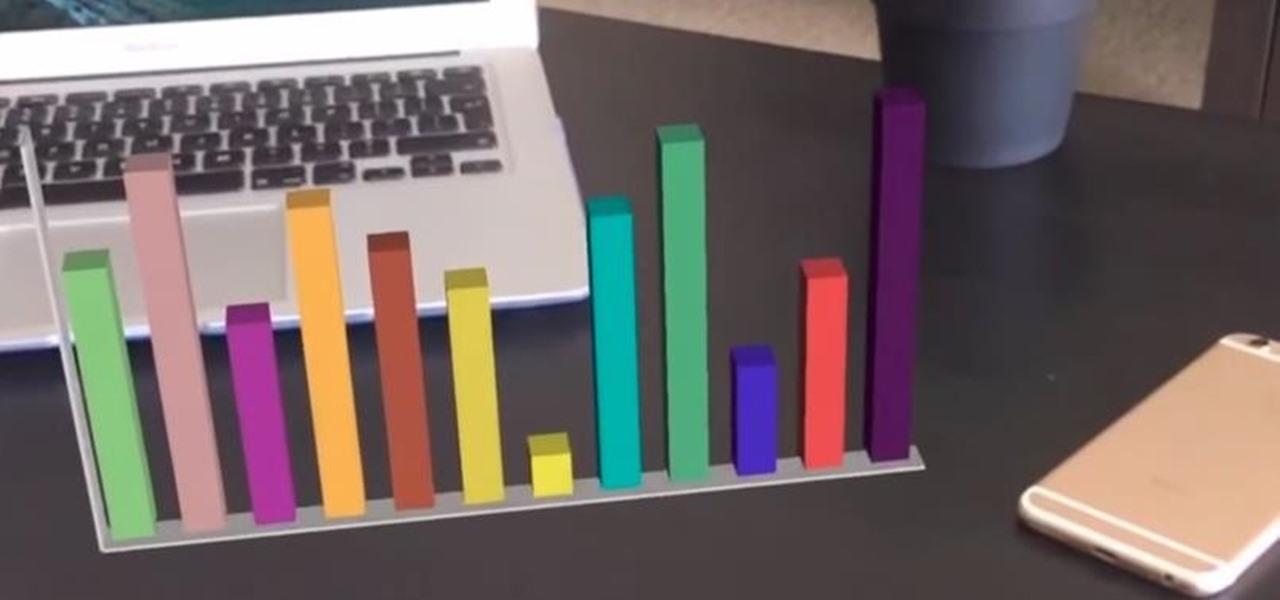
It's certain that the release of Apple's ARKit is going to be game changing for businesses. This demo video was created by YouTube user hdsenevi who used the ARKit to create a simple bar chart. The chart has adjustable settings, allowing the user to make each bar larger or smaller and change their colors. Not only that, but there is an "animate" option.
Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

In the wake of Google Glass' failure, we can expect other companies to fill the void in due time. Perhaps unsurprisingly, Snapchat may be one of the first.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!
First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.
This video will guide you top 10 windows shortcut key which is very useful in everyday computing. Watch the video and follow the steps to know top 10 windows shortcut key.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Macrame Owl - Decoration for keys / key ring or necklace / How to / DIY Video: .

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Video: . In this tutorial I show you how to get a perfect Chroma Key using After Effects.

It has happened to everyone at one time or another, but if you work in an environment with cars, it may happen much more often.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.