This masterful drawing session from idrawgirls instructs us how to draw a mysterious girl specifically the facial figure, face, hand and upper body front view. First you will establish, very lightly, the facial shape, direction of the eyes, and the shoulders and upper body. The key here lies in the direction of the eyes, casting the face slightly downwards, creating that ineffaceable mysterious effect. Another important factor specific to the female face is keeping the nose close to the eyes ...

Hello! My name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss the game can you read my mind. This game has a little bit of mystery flavor to it. You'll see what I mean. In this game, you need to utilize 2 rooms. In the first main room, you have all the guests of your party. Then later we'll instruct the guests we're going to play a game called can you read my mind and the goal...

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

As the year comes to a close, we've invited some of the leaders of the AR industry to take the time to look back at the progress the AR industry has made while looking forward to what's ahead in 2020. A report on the top apps of 2019 — and the decade — also offers some insights on the progress and direction of mobile AR.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

The hype around augmented reality has risen to a fever pitch over the past two years, and if this week's selection of business news stories are any indication, the din is about to get down right deafening.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Sorry Samsung. I know you really wanted Bixby to be the next Siri, Google Assistant, or Alexa — but it just isn't. Burying the option to disable the app won't change that. Sure, Bixby has some redeeming qualities, but there are many of us who don't want it shoved down our throats. We'll show you how to disable the app to prevent it from launching every time you try to access just about anything.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

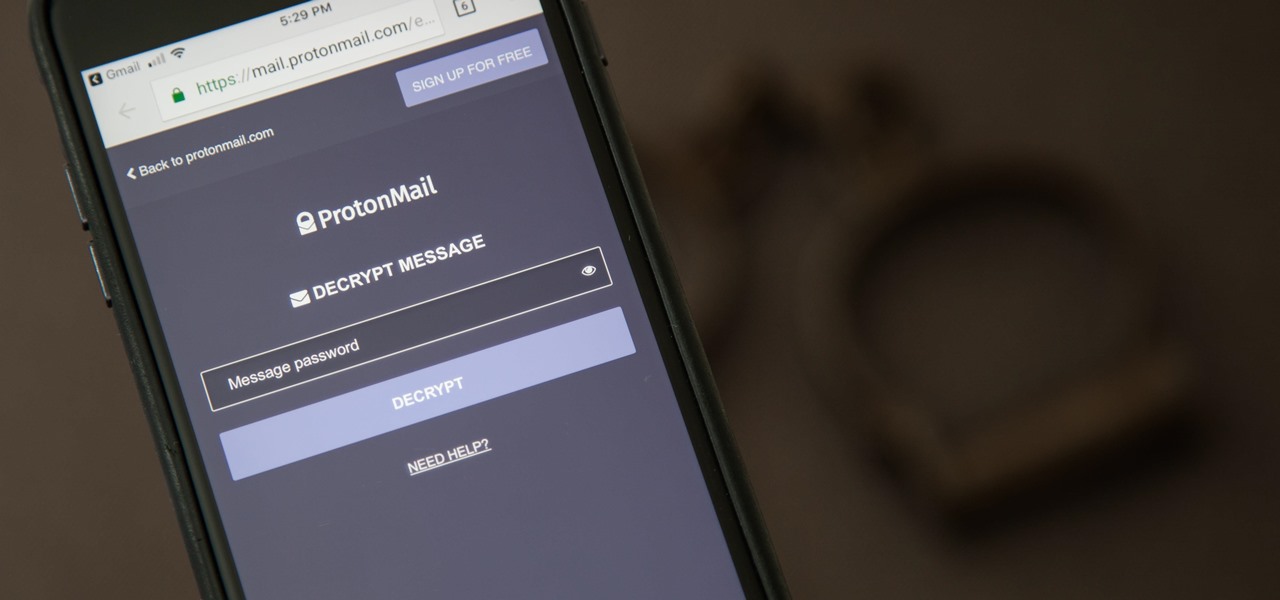
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

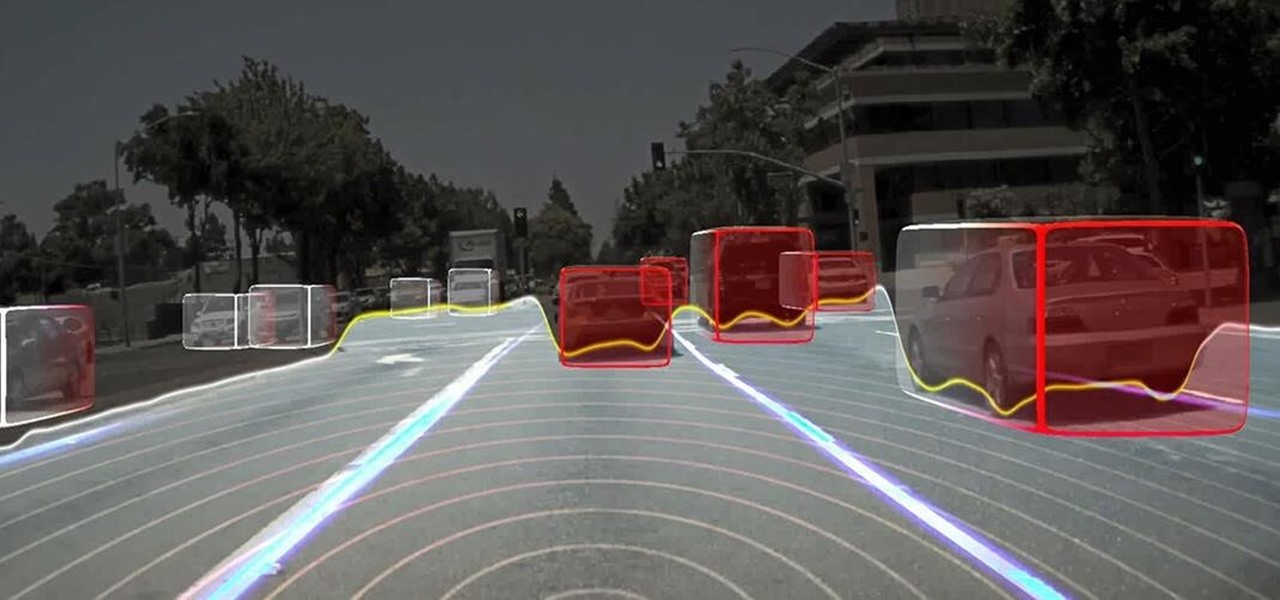
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

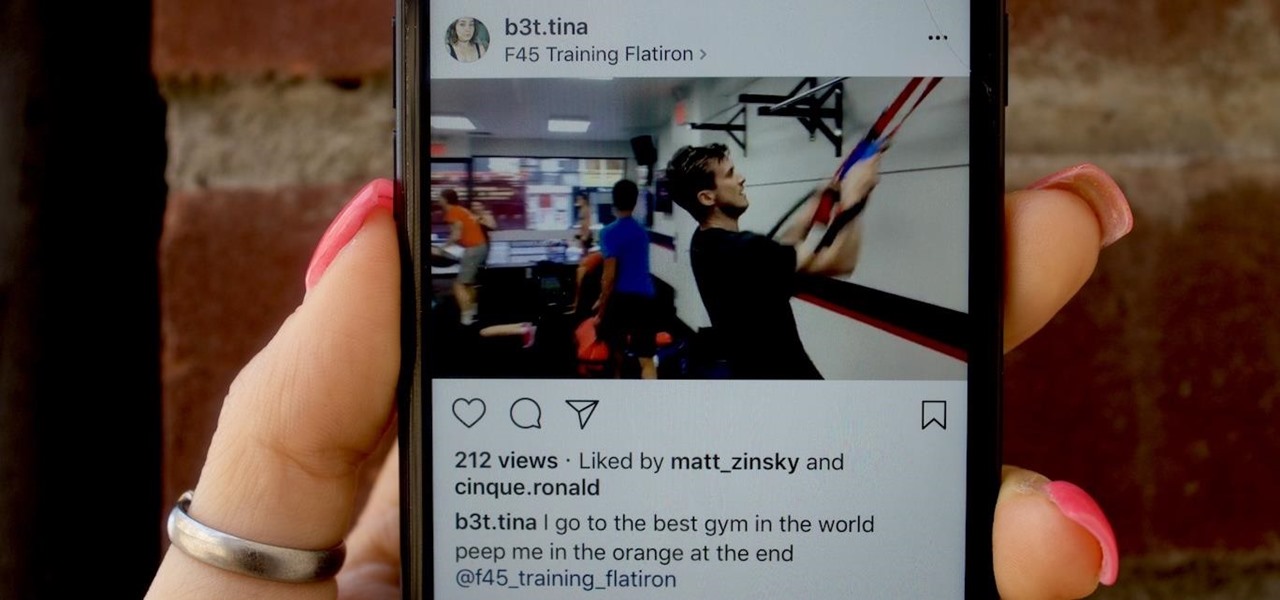
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

With many of the companies working in augmented and mixed reality focused on the Augmented World Expo, the finance side of the industry has been relatively quiet.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

With the death of Google's Nexus line, the market for phones with top-notch specs at midrange prices is now wide open. OnePlus is apparently ready to fill this void, as they've just announced the OnePlus 3T, an iterative update to their OnePlus 3 flagship only five months after initial release.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

You've likely seen light-up musical keyboards that teach you how to play a song with visual cues, but few of those devices exist and have a limited number of songs you can actually learn. But Karl Baumann and his HoloLens Hackathon team figured out that in mixed reality, you can learn music with visual cues with any piano.

It looks like Apple is finally going to do something to address all of the complaints about their unremovable stock apps clogging up people's home screens. While bloatware is a bigger problem on Android where you have to deal with apps from Google and carriers, an iPhone can still get pretty cluttered with all those stock Apple apps. I mean, just look at all this crap... AppAdvice noticed two new keys in the iTunes metadata that strongly suggest that you'll be able to get rid of stock apps on...
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

As your Galaxy S6 lies on your desk while you're hard at work, it's difficult to resist from periodically pressing the wake/lock button to check the weather or glance over any notifications you may have on your lock screen. While pressing the hard key is easy enough, there's an even easier method where you simply hover your hand over the device to wake the screen.

If you don't like watching YouTube videos on your computer with your hand glued to your mouse, the next best thing is using keyboard shortcuts. They may not seem any easier than clicking, but once you get them down it's a whole other story. Plus, there are some features you might not otherwise use (I'm looking at you, speed control) unless the shortcuts existed.

The new Nexus 6 and Nexus 9 models will be shipping with Android 5.0 Lollipop preinstalled, and the Nexus 4, 5, 7, and 10 will be getting the new OS update from Google very soon. But where does that leave the rest of us?

Pie controls are navigation soft keys that can be displayed by swiping up or from the side of your screen, allowing you to navigate, search, call up the power menu, take screenshots, and a lot more. Not only are pie controls functional, they make using Immersive Mode a breeze since the regular nav bar was no longer required.

The new HTC One M8 has only been out for a few hours, but it's apparent that some people had their hands on the device before the announcement. And well, one them decided to drop the thing in water.

Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

Keyboards tend to get overlooked as we rapidly text or type up emails, but when we do find the time to look at it, it's pretty bland. That's why we showed you how to spruce things up with a dark keyboard on your iPhone, which served as my default keyboard...until now.

The iOS 7 release brought with it many new aesthetic upgrades, from new flat, vibrant icons to a sleeker text messaging interface. Another small, yet noticeable, difference is the minimal and clean lock screen, which removed the overbearing "Slide to Unlock" background bar in lieu of just the text.

It feels like someone just overheard me talking shit about my iPhone. I really hate when I need to edit an email, text, iMessage, or whatever because of the way you have to select words and phrases. You either hold down on the screen where you want to bring up the menu, or double-tap to highlight a word. It's crap.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.