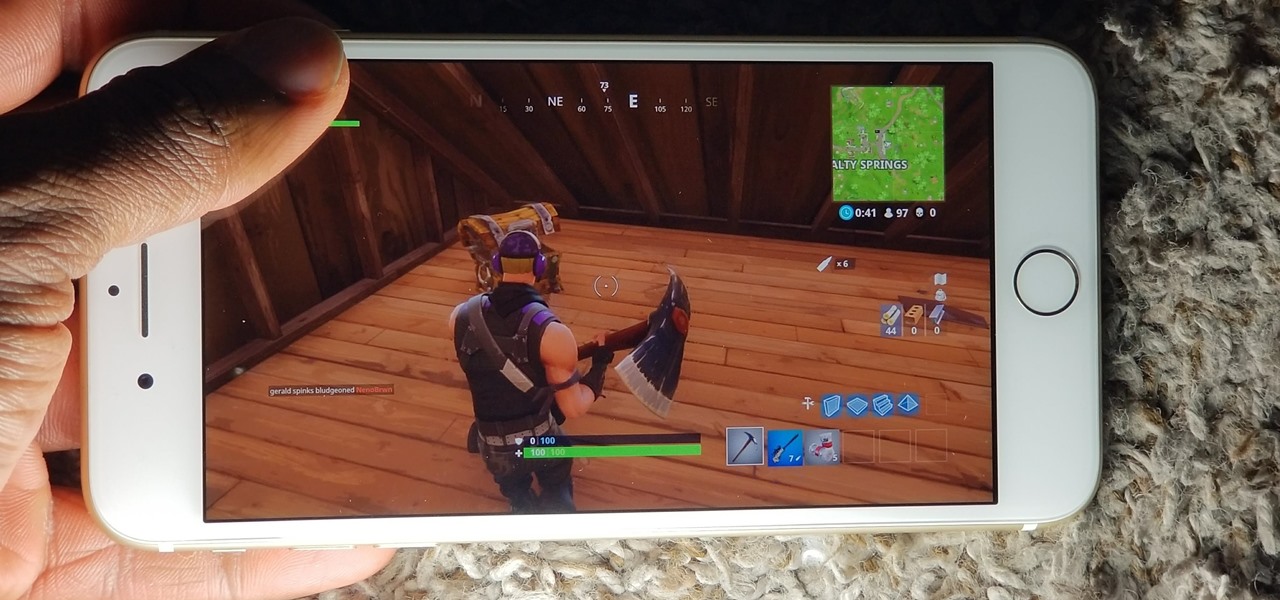
While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

Although The Last Jedi hype has mostly passed, there are still a good number of fans out there dueling Sith lords in augmented reality via their new Lenovo Mirage headsets. Now, thanks to an update on Thursday, those aspiring Jedi have a new AR challenge to engage in the Star Wars: Jedi Challenges app.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

GIFs are awesome, but GIFing from your keyboard is some next-level stuff, and Apple knows this. That's why they've included a way to find and send GIFs in Messages from the stock iOS 10 keyboard. However, iOS 10 is not out for the public just yet, so if you want to easily send GIFs in your messages, you'll have to settle for a third-party keyboard.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

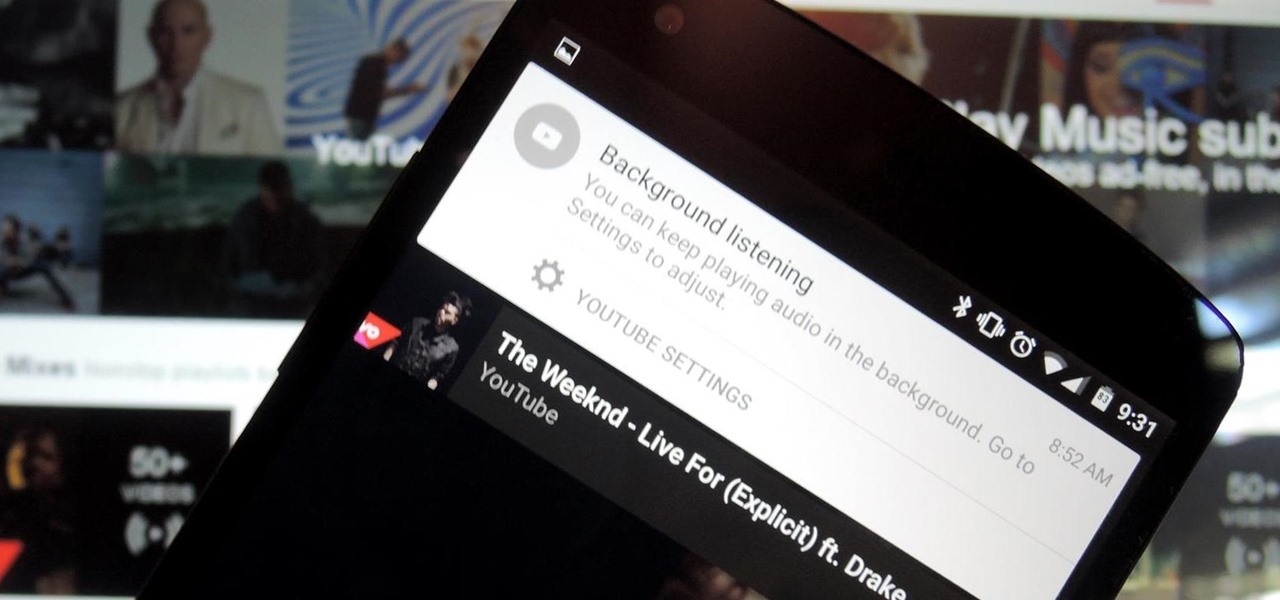
We recently showed you YouTube's new music streaming service, YouTube Music Key, with it's promise of ad-free music complete with background listening and offline play. Well, if you check your YouTube app, there's a good chance that Google flipped on the service for you. Activate the Service

Unlike other Android devices with soft keys, the LG G3 actually comes stocked with a few different styles, as well as the ability to adjust the button layout and combination. But while the customization options are great, the styles you can switch between don't add much flair or personality to your device.

Many of our everyday apps include a menu tab or search bar, like Chrome and Twitter. In fact, a lot of times those are the first things we go for, as search is universal in most apps, and app settings are just about always accessible through the menu.

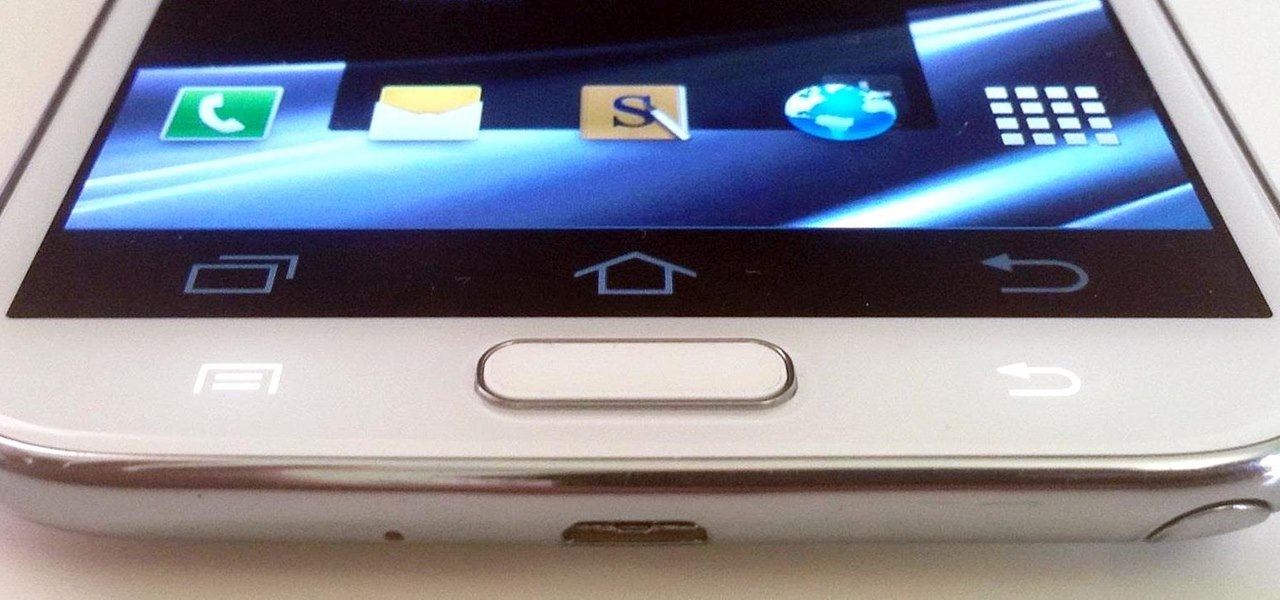
Ever since Android 3.0 Honeycomb, Google has been trying to push phone manufacturers to do away with physical menu buttons. Samsung has been one of the lone holdouts, retaining the menu key up until the Galaxy S5, where they finally replaced it with a "recent apps" multitasking button.

How to make a Lego key holder with note board. Tired of loosing your keys? Well keep them safe and in one place with this fun Lego key holder.

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

There may only be a few hardware buttons on your Samsung Galaxy Note 2, but when they're not working, your phone might as well be a doorstop. A few years back, I was texting while walking to class and a student on a bicycle crashed into me. My phone was flung thirty feet—straight into a puddle. I picked it up and checked for damage, but everything seemed okay. The biker apologized profusely, but nothing was wrong, so I told him not to worry about it and proceeded to class.

Get higher skills in Ninja Saga! This cheat lets you hack into the game and give yourself higher skills in your jutsu. This shows you how to use Cheat Engine 5.6 and increase all your jutsu skills for your play session. As long as you're using Mozilla Firefox, this cheat will work!

Hack Ninja Saga. The flash-based game Ninja Saga is a role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga (06/17/10).

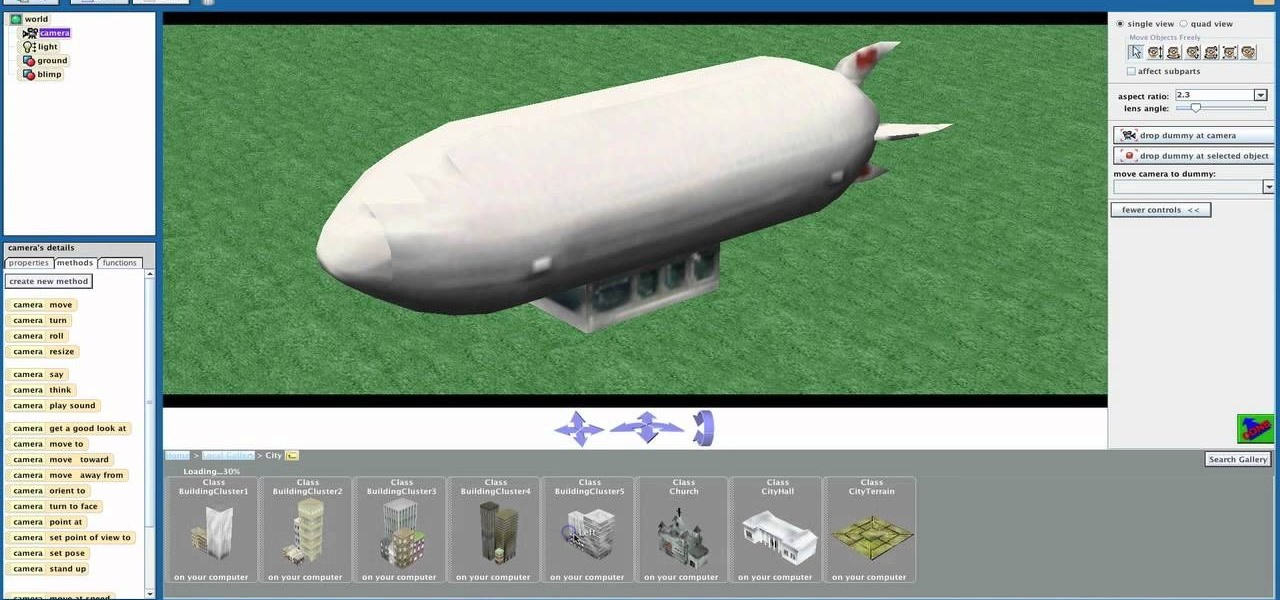
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

The perfect way to avoid boredom at work or in the classroom is with a good old-fashioned prank, and this one is for tech-minded. In the video below, you'll see how to change your coworker's (or classmate's) computer screen to be display upside-down, which will totally freak them out when they return from lunch or the restroom. The best part is watching them try to revert it back to normal!

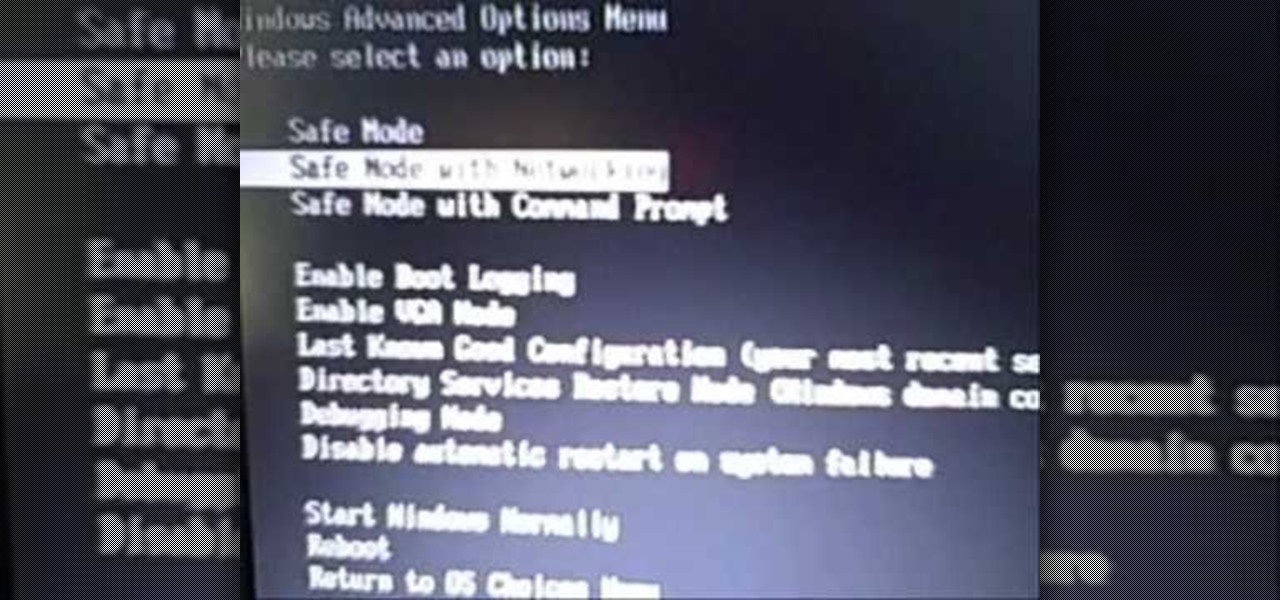
There are times when you must start up your Windows XP computer system in Safe Mode, for example if you need to remove certain viruses, key loggers, adware, etc. that cannot be removed while in standard mode. If you want to learn how to boot in safe mode in Windows XP, you should watch this. 1. Turn on your computer. Make sure your monitor is on and you do not step away from your computer, as booting into safe mode happens within the first minute of when you turn on your computer. You should ...

This is a Computers & Programming video tutorial where you will learn how to take screenshots on Mac OS 10. 5. Andrew Grant says there are several ways of doing this. The easiest way is to hold down the Command and Shift key and press 3. You will get a screenshot of the entire desktop. To take a screenshot of a selected area, hold down the Command and Shift key and press 4. The cursor now changes into a target. The figures next to it are the values of the pixels from the left hand top corner....

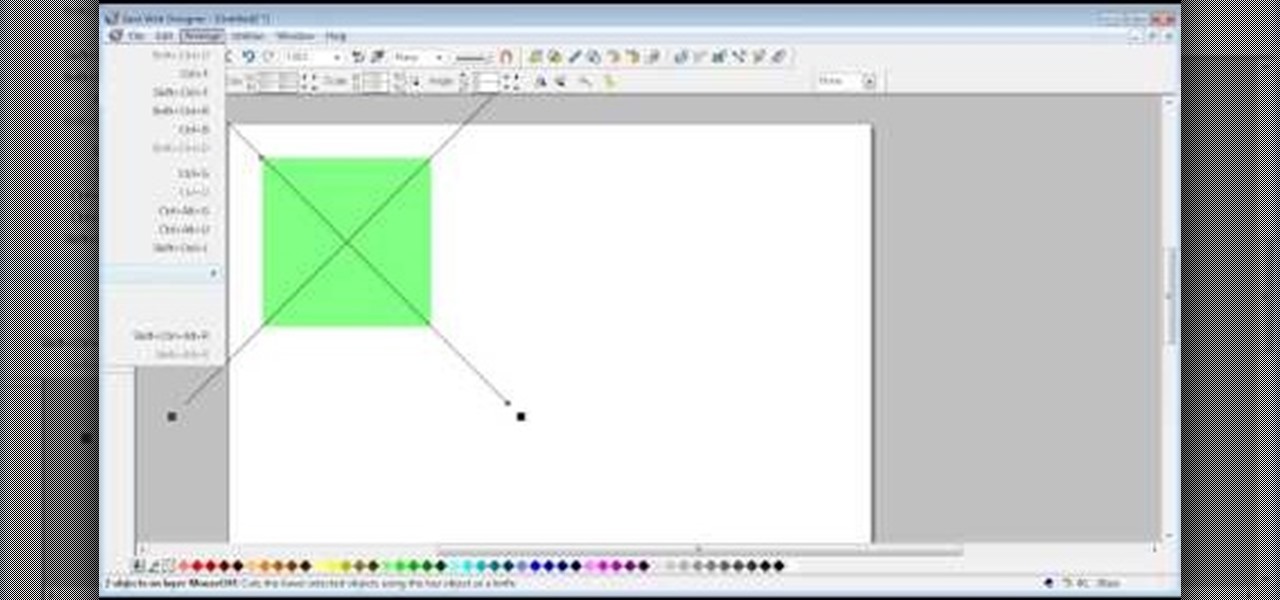
The video shows us how to create bevels in Xara web designer. Firstly using the rectangle tool hold down the Ctrl key to create a square. The problem with the Xara web designer is that it hasn't got a convert to edit the shape features which actually means that you cant select individual nodes with the shape editor tool which may create some other line. However you can select individual nodes by going to arrange/combine shapes/add shapes with selecting the rectangle. And by doing changes the ...

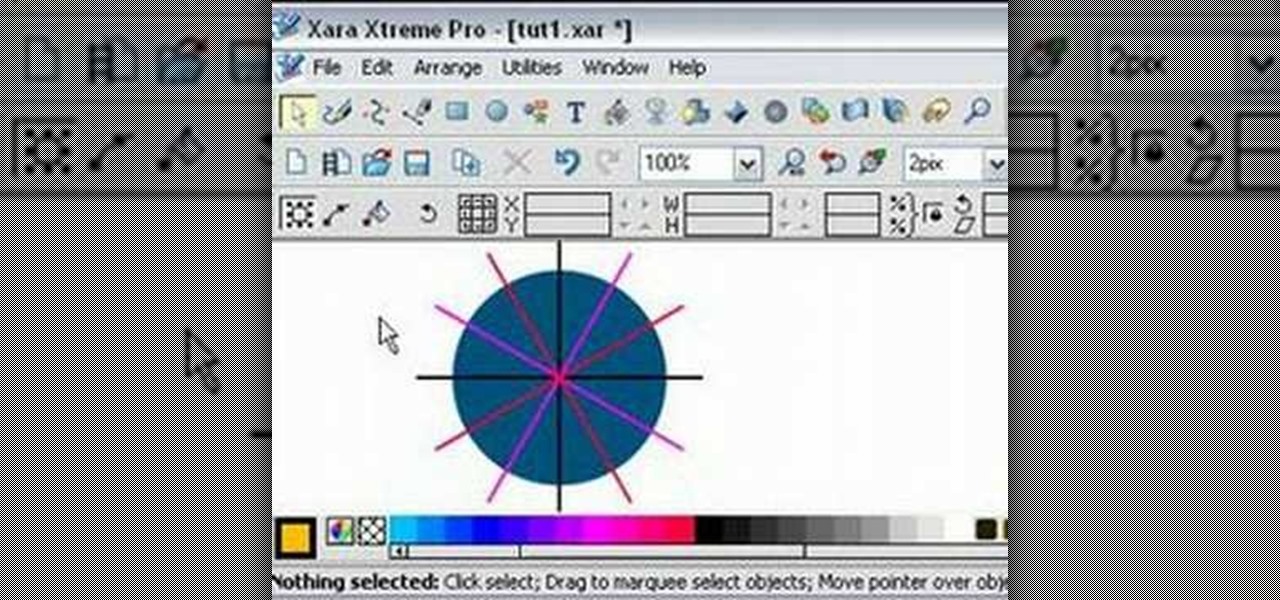
Learn how to split a circle into segments with Xara Xtreme. First select the shape editor tool. Drag the tool to the circle. The dialogue at the bottom communicates what steps to choose next. Holding the Ctrl key drag a straight line within the circle, click on the selector tool (yellow arrow on the left of the middle row) to enable the option of selecting. This saves 1 line on drawing layer 1 also and enables the marquee (flexible box) that you want to manipulate around the circle encasing t...

Craving key lime pie? Make one at home! Who knew those tiny little limes could make a pie with so much flavor? Your friends will love this easy to make, tart treat. Learn how to make a homemade key lime pie with help from this instructional video.

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack levels and gold in Ninja Saga (11/11/09).

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga EXP (11/07/09). Download Cheat Engine.

As most of you already know, the White House is the seat of the Executive branch of government in the United States. Constructed in 1792, it is one of the oldest buildings in the U.S. During the War of 1812, it was burned down and later rebuilt. The White House was inspired by a few foreign government buildings and is somewhat Greek in appearance.

The new Harry Potter movie is in theaters today, but while most of you are eating popcorn and enjoying the first flick of the last part in the series, others will be home getting their Harry Potter fix with the new video game, appropriately called Harry Potter and the Deathly Hallows, Part 1. Just like the movie, it's based off the final novel written by JK Rowling.

Even though this project seems easy for you, your kids will find it a challenge… a wonderful challenge that will keep them being creative. Their love of animals will keep them wanting more, and this lion stick puppet will give them tons of fun. See how to make the paper lion in this video. The materials needed are:

Opening doors with keys is boring and for the lockpicking illiterate. Inject some mischief into your life by watching this video on how to open a lock and break into a house using everyday objects you have lying around.

Looking for an easy, impressive magic trick that can be performed most anywhere? Look no further. In this free video magic lesson from YouTube user experthowto, you'll learn how to perform the

Three point lighting is the key to MAKING videos look professional. Tom Skowronski, the associate editor of Videomaker, guides us through the process of three point lighting. Three point lighting involves the use of three types of light to create a professional appearance when video taping. First, a key light is used to provide bright illumination of the subject. Then, a fill light cleans up the dark areas on the face. Lastly, a backlight fills serves to separate the subject from the background.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Android apps check your system locale settings to determine which language they should display. For the most part, it's a seamless experience—except for those times when an app has not been translated into your language of choice, in which case the app will usually default to English.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

It has happened to everyone at one time or another, but if you work in an environment with cars, it may happen much more often.