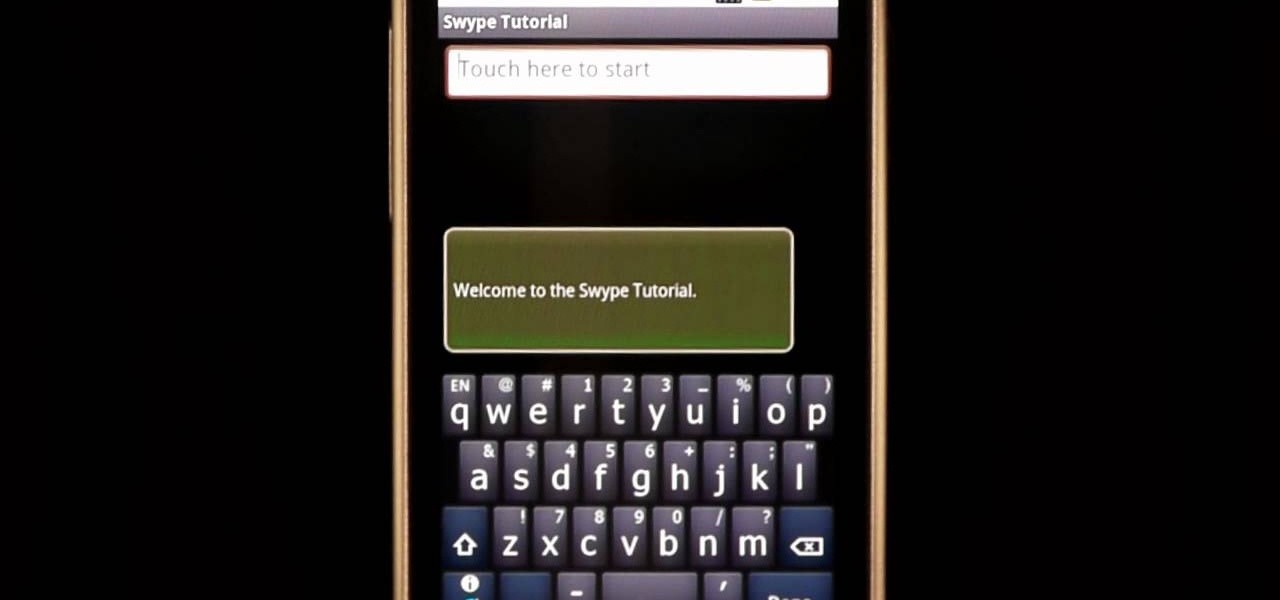
In this clip, learn how to use the Swype Key while texting with Swype on your cell phone. The Swype key is where all of your options are like dictionaries, tips and tricks, help menus and everything else you may need.
If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...
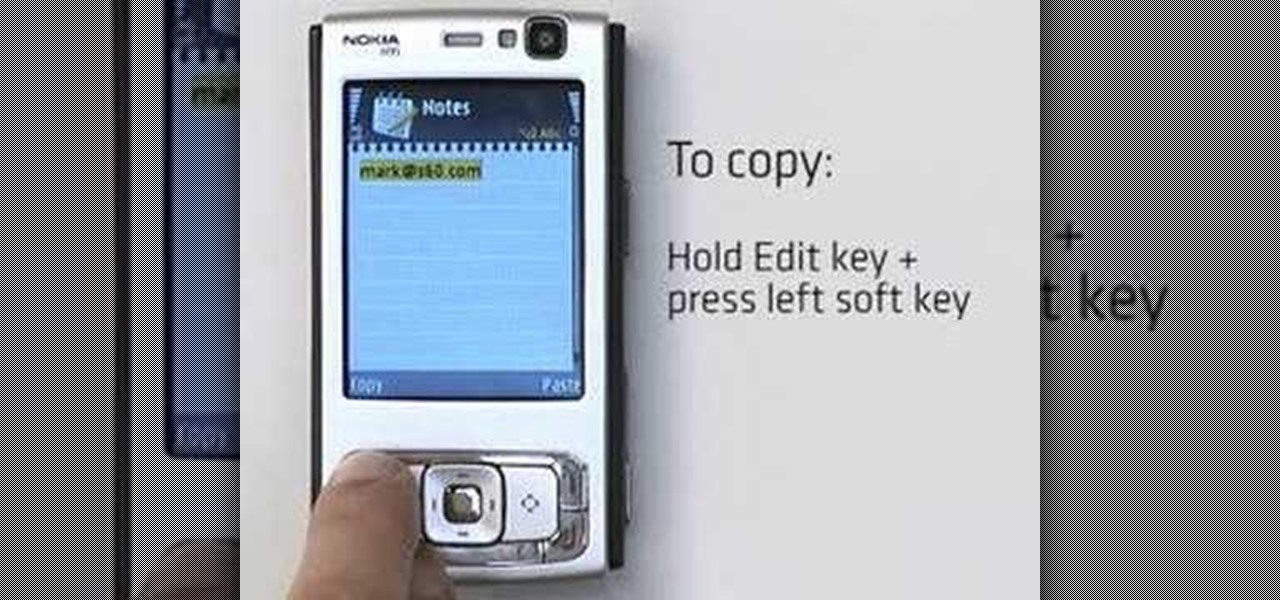
In this video S60 online explains how to copy and paste using your S60 phone. First, have what you would like to past saved on your notes application. Next, when you want to paste it to a webpage for instance open your notes application. When you open the notes, press and hold down the edit key and the directional key to highlight what you would like to copy. Still holding the edit key, press the left soft key to copy the text. Now you can past the text where you need it. Go back to where you...
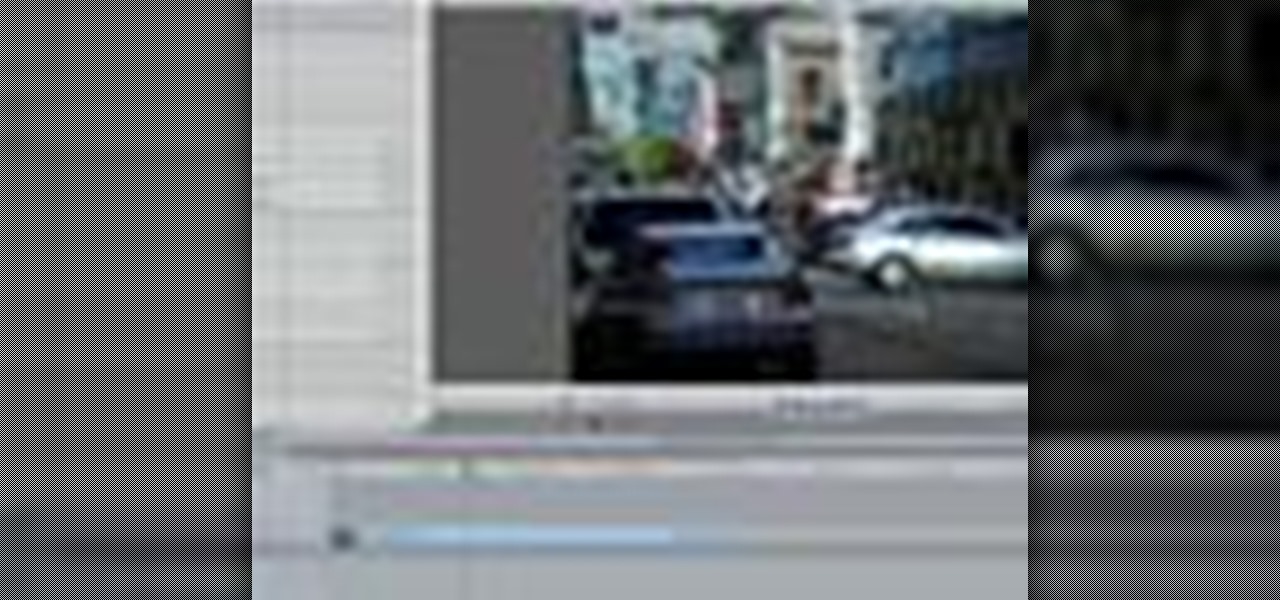
Ever needed to fix a clip where an unwanted or unexpected object appears in the scene? A car is suddenly passing across or a stage hand got in the shot by accident? And re-shooting is expensive or impossible? You would be facing hours of tedious frame-by-frame rotoscoping to get rid of the pesky element in your video...
This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

With the majority of smartphone carriers no longer offering unlimited data plans for the iPhone, monitoring how much mobile data you use is a key element to saving money on your phone bill.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

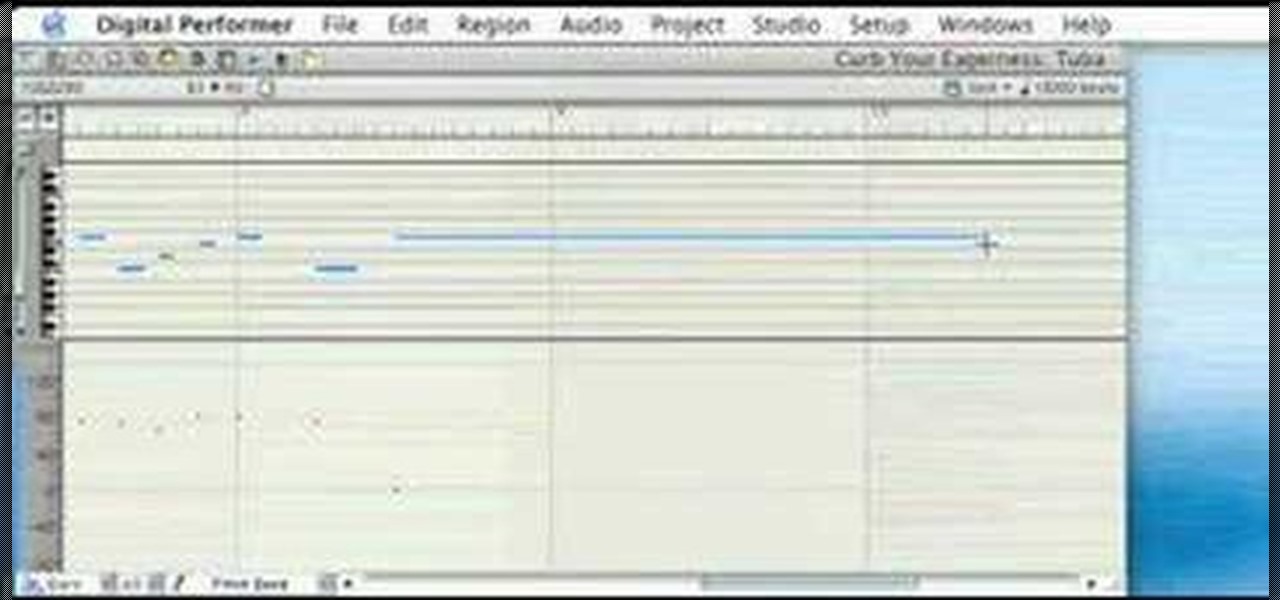
Check out this video from Berkleemusic.com and take your recording in a new direction and change the key of a certain section or the pitch of a note using the Transpose options in Digital Performer music software.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

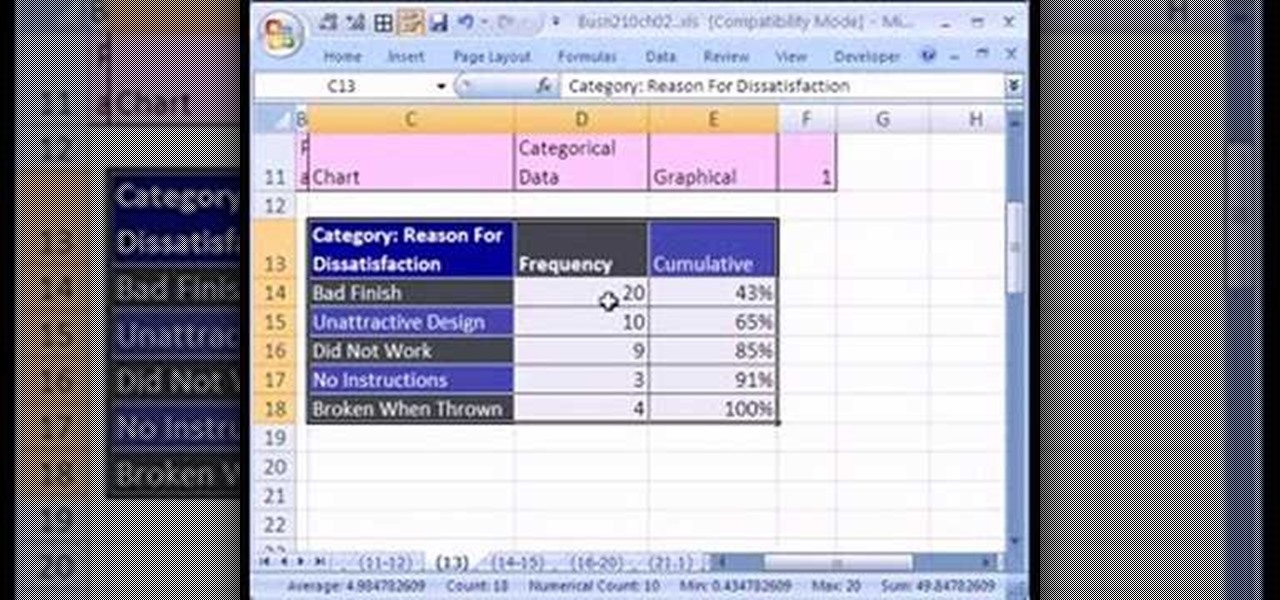
If you want to create a Pareto Chart for categorical data in MS Excel you should first have your data input into Excel already. From your data, you should highlight the cells that you want to count the frequency for and in the frequency box you should type in =COUNTIF and highlight the data you want the frequency for and put in F4 and then press , click on cell to the left and click enter. Now this will work all the way down. If you have not sorted it, you can right click and then click sort....

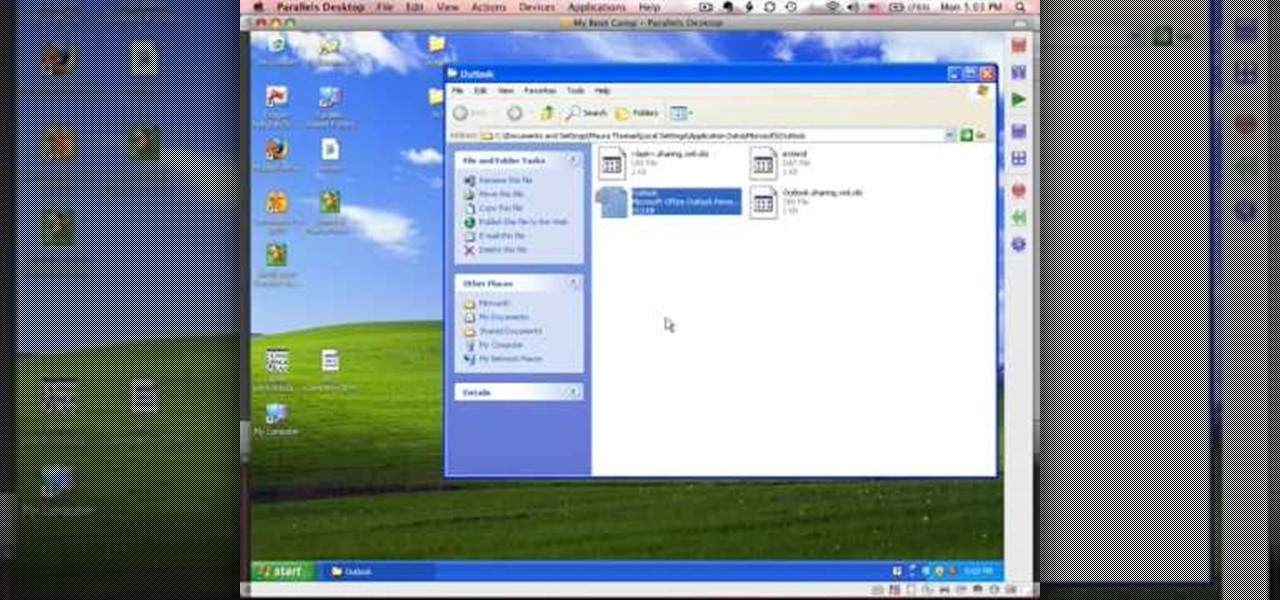
This tutorial describes how to backup the PST file of Outlook.

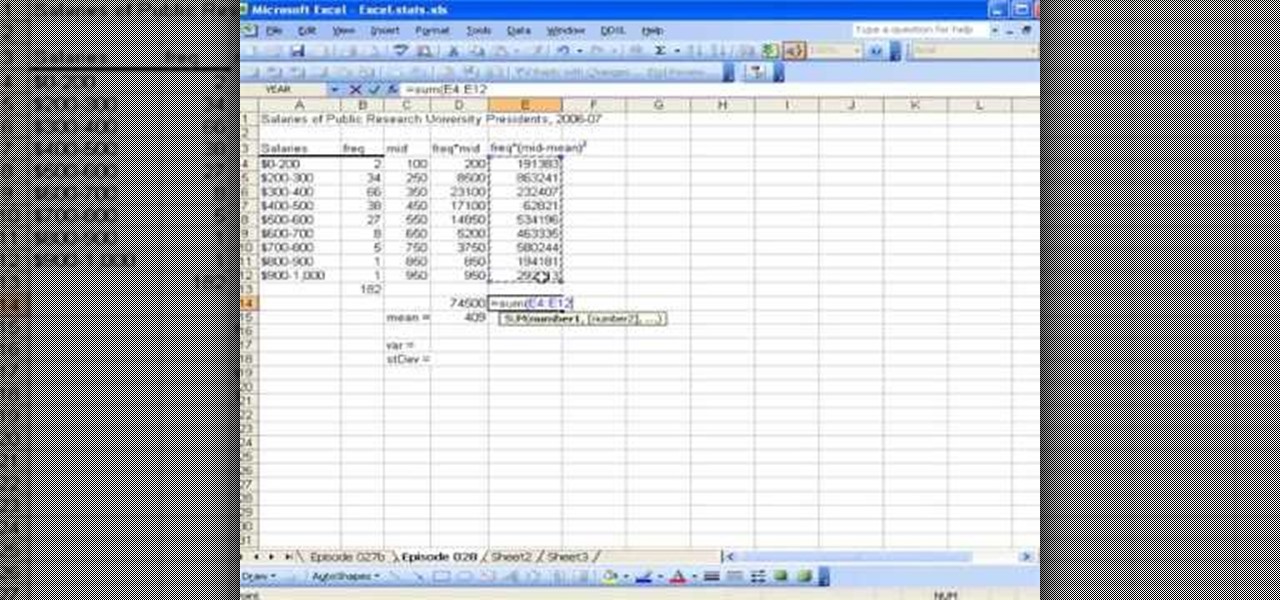
This video shows the method to find the variance and standard deviation using Excel. The variance shows the variability of the data points from the median. We find the difference of the median and the mean. We write the formula using '=' sign. The median and data points are put in it by selecting the appropriate cell. The median is made an absolute constant by pressing the F4 key. This is squared by using '^2'. This is multiplied to the frequency using '*'. The result is found for all the dat...

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Welcome back, my greenhorn hackers!

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

In this video tutorial, viewers learn how to create drop down menus in Microsoft Excel. This task is very easy, fast and easy to do. Begin by highlighting a desired cell. Then click on the Data tab and click on Data Validation under Data Tools. When the Data Validates window opens, click on the Error tab and deselect "Show error alert after invalid data is entered". Then click on OK. Now simply type in the data into the selected cell. This video will benefit those viewers who use Microsoft Ex...

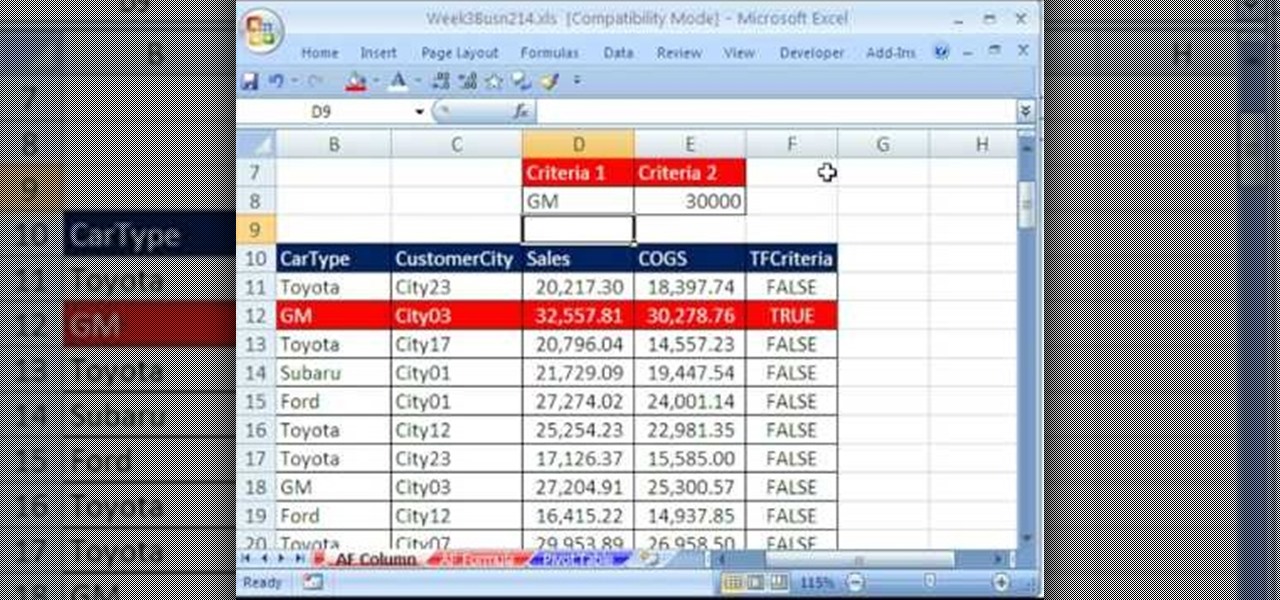
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 19th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about using Advanced Filter to extract data from an Excel List/Table/Database. See these 7 Advanced Filter examples:

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

This five-part series on C# programming covers many things. First, you learn how to save to the Microsoft SQL Server. Then, you'll learn how to retrieve that data. You'll also learn how to navigate the DataSet, edit SQL data, and delete data. If you have Microsoft Visual Studio and SQL Server, give this lesson a try.

Core Data is a powerful data-management framework introduced with Mac OS X v10.4 Tiger. When you take advantage of Core Data, it slashes the amount of custom code you need to write in order to manage application data. Opening, saving and undo management can all be handled by Core Data, freeing you to concentrate on creating unique features for your application. This video tutorial, which presents a general introduction to using Core Data, will walk you through the process of building a simple...

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Even Halo: Reach on the Xbox 360 has hidden collectable items! All in the convenient (for the people hiding them) size of a small data pad! Earlier you got access to the first 9 data pads that you can get on any difficulty. Next, you will get a look on the next 9 data pads that you can only acquire while being on Legendary difficulty!