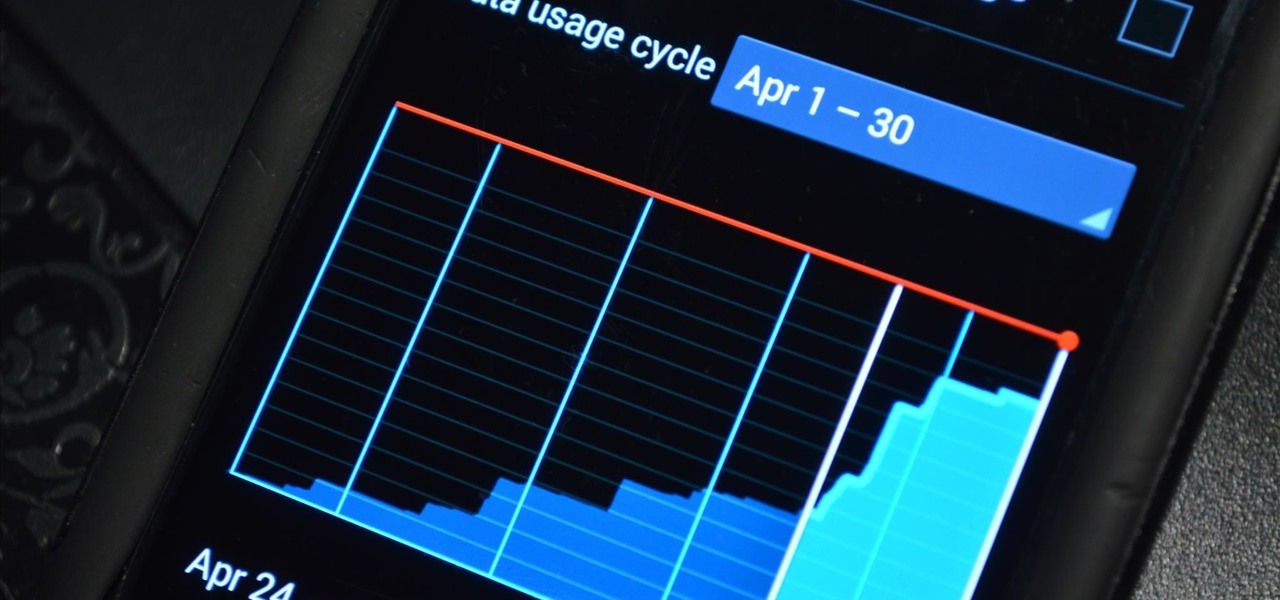
If you tend to go over your data allotment each month, or are constantly afraid you will, Verizon Wireless is giving you chance to relax a little bit with up to 2 GB free data for two months.
I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.
Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.
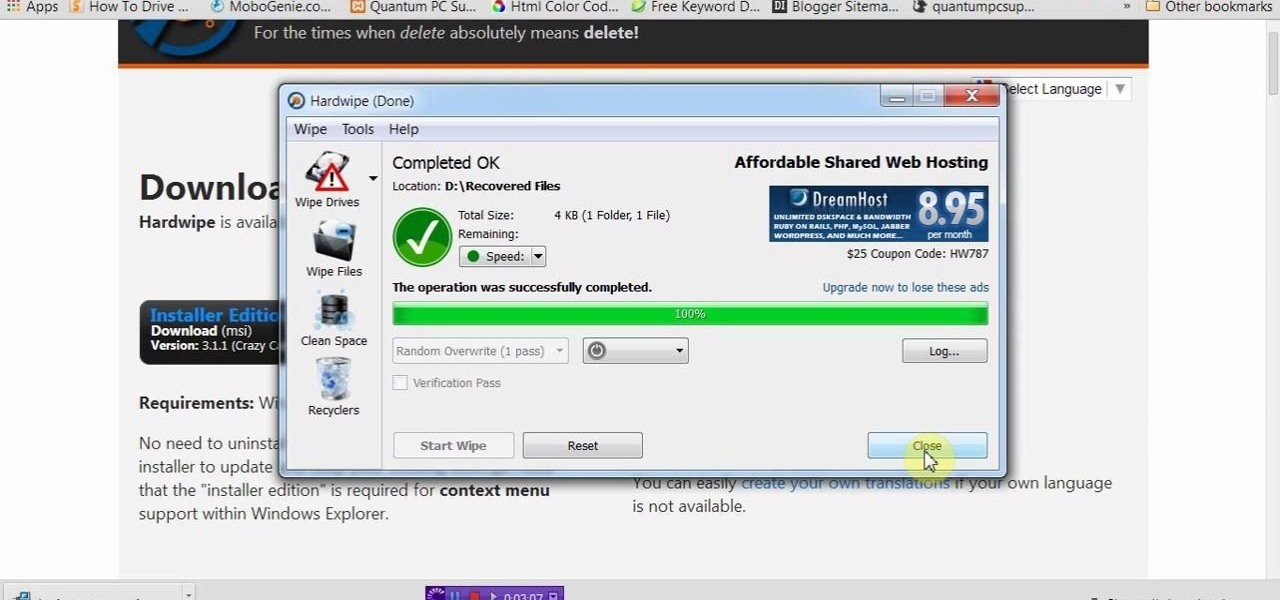
If you delete data by using Hardwipe tool, then it can't be regained by any means. The file or data will be deleted permanently. Watch the video and follow all the steps carefully. Employ the technique in your own PC.
This video will show you how to control and limit data usage in your windows 8 phone. You may want to restrict your data usage and want to set limits for apps also. If you set your usage limit internet will stop automatically after reaching the limit.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest.

Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

In this video tutorial, viewers learn how to use the Slow Keys access tool in a Mac OS X computer. The Slow Keys feature is located under the Keyboard tab in the Universal Access window. Once Slow Keys is turned on, users also have the option of using key click sounds as additional feedback when a key is pressed . Users are able to set the Acceptance Delay to determine how this feature behaves. The delay of the sound can be set from long to short. This video will benefit those viewers who use...

In this video tutorial, viewers learn how to use the Sticky Keys feature in Microsoft Windows 7. To use the Sticky Keys, click on the Start menu and open Control Panel. In the Control Panel window, double-click on Ease of Access and click on Change how your keyboard works under the Ease of Access Center. Then click on Set up Stick Keys and check the option Turn on Sticky Keys. This video will benefit those viewers who have limited dexterity and find it difficult to use complex keyboard shortc...

In this video tutorial, viewers learn how to use the Filter Key features on a Windows 7 computer. Begin by opening Control Panel and select Ease of Access. Under the Ease of Access Center, click on Change how your keyboard works and click on Set up Filter Keys, at the bottom of the window. Now check the box beside Turn on Filter Keys. Users are provided with several options for he Filter Keys such as: turn off the Filter key wen Shift is held or 8 seconds, display a warning message when turni...

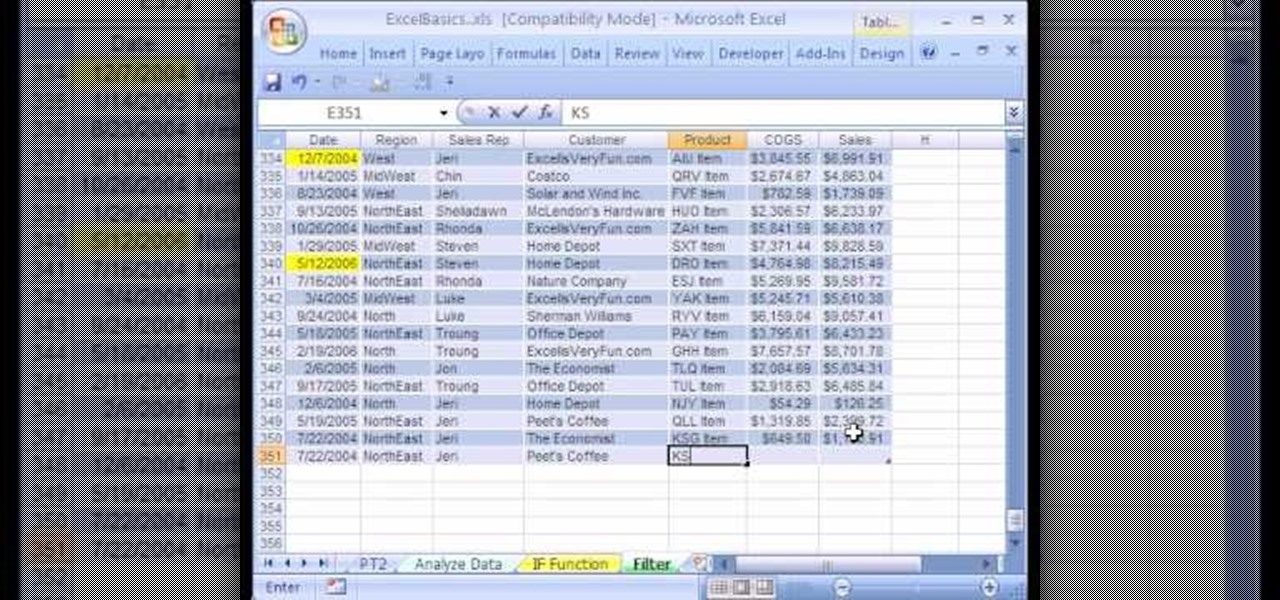
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

In this video, we learn how to find your Windows product key. Start off by going to Magical Jellybean Keyfinder. This website has a download that will find your product key for your Windows program. This is a great and necessary tool if you happened to loose the product key that came with your computer. This is also great for computers that already had Windows installed, and you never had the product key in the first place. Once you install this on your computer, you just open it up on your d...

In this video tutorial, viewers learn how to upgrade a computer from Windows Vista to Windows 7. Users are able to do an in-place upgrade as long as both the Windows Vista and Windows 7 versions are the same. Users will need to export all their data, erase the hard drive and then reinstall all the applications. To do an in-place upgrade, begin by backing-up your data. Then insert the install DVD and select run it. Then click on Install Now and wait for it to install and setup. This video will...

When picking a padlock, the only part you need to worry about is the part where the key goes into the lock. The locking mechanism has pins attached to springs. The key pins are on the bottom and the driver pins are on the top. The key turns when the pins of different heights are separated, flush and aligned. Stick a tension wrench into the keyway and put pressure on it. Take a pick to push the rest of the pins up until they are flush with the shear line. Stick the tension wrench into the bott...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Check out this informative video tutorial from Apple on how to get started using Numbers '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numbers gives you simple ways to make sense of your data. You'll captivate your audience with new and sophisticated features in Keynote.

Check out this informative video tutorial from Apple on how to use tables, color, images and fonts in Numbers '09.

Check out this informative video tutorial from Apple on how to create formulas with Quick Formula in Numbers '09.

Check out this informative video tutorial from Apple on how to hide, filter and sort table cells in Numbers '09.

Check out this informative video tutorial from Apple on how to group rows into categories in Numbers '09.

Check out this informative video tutorial from Apple on how to highlight values with Conditional Formatting in Numbers '09.

Check out this informative video tutorial from Apple on how to print spreadsheets in Numbers '09. iWork '09, the office productivity suite from Apple, is the easiest way to create documents, spreadsheets, and presentations. Writing and page layouts are easy in Pages. Numbers gives you simple ways to make sense of your data. You'll captivate your audience with new and sophisticated features in Keynote.

Check out this informative video tutorial from Apple on how to create and edit charts in Numbers '09.

Check out this informative video tutorial from Apple on how to work with Excel users in Numbers '09.

Learn how to do red eyeshadow with MAC Key Artist Chris D Par. Pursebuzz is a YouTube makeup star. Her makeup tutorials are widely watched and favorited. Pursebuzz delivers beauty tutorials on makeup application and hairstyling. Search Pursebuzz on WonderHowTo for all of of her beauty how to's, including skincare, hair, makeup and celebrity looks.

In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

The video is about how to find the variance of the set of data. They found the variance by using the variance formula. Variance formula was represented by square of S, whereas S is the Standard Deviation.

In this Labrats video tutorial the instructors Andy Walker and Seab Carruthers show how to undelete the deleted files and recover them. When you save data to your computer, the computer stores the data in the binary format on the hard disk. To keep track of the files, the Operating System maintains a file table that shows the location of the data on the hard disk for a specific file. There are many file formats like FAT, NTFS etc. So when you are erasing the file only the entry in the file ta...

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

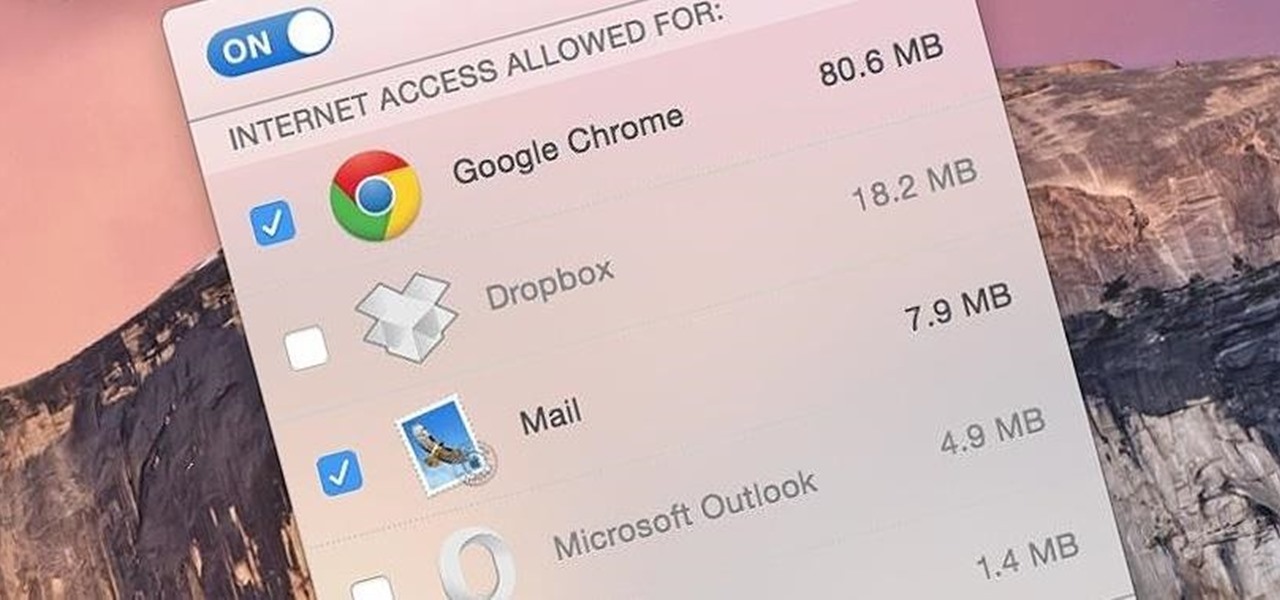
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

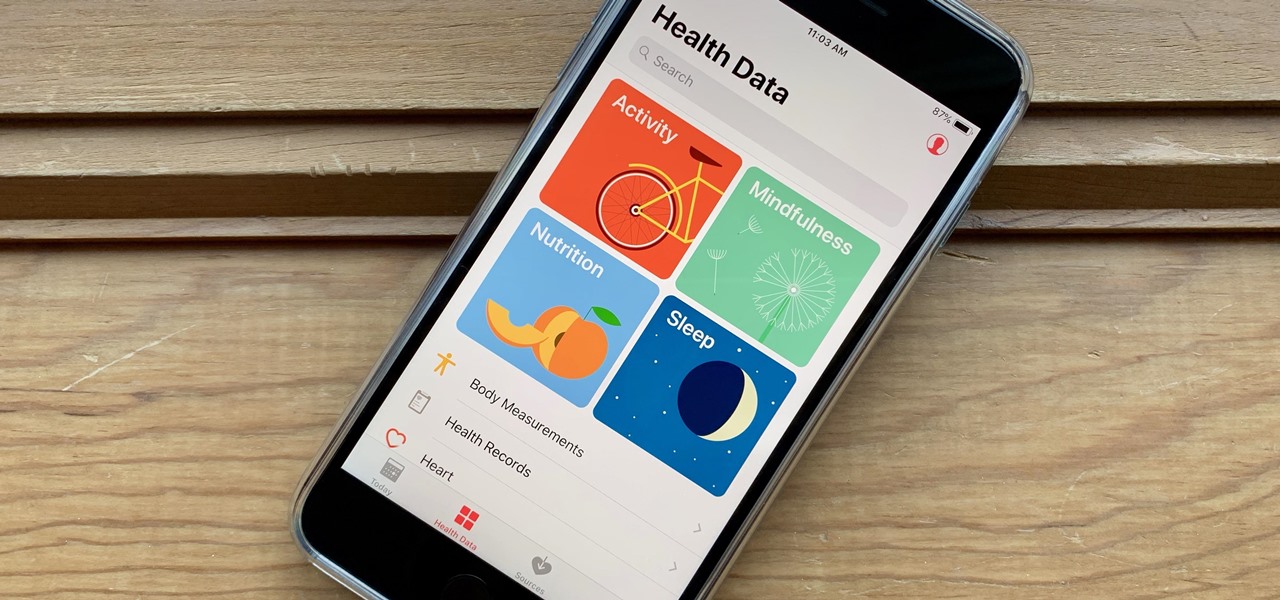
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.