With the iPhone XS, XS Max, and XR, Apple introduced dual-SIM capabilities to iOS, made possible by eSIM technology. If you recently picked up one of these three new iPhones and need to utilize your eSIM while traveling abroad, you might want to take a look at the data plans offered by GigSky.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.
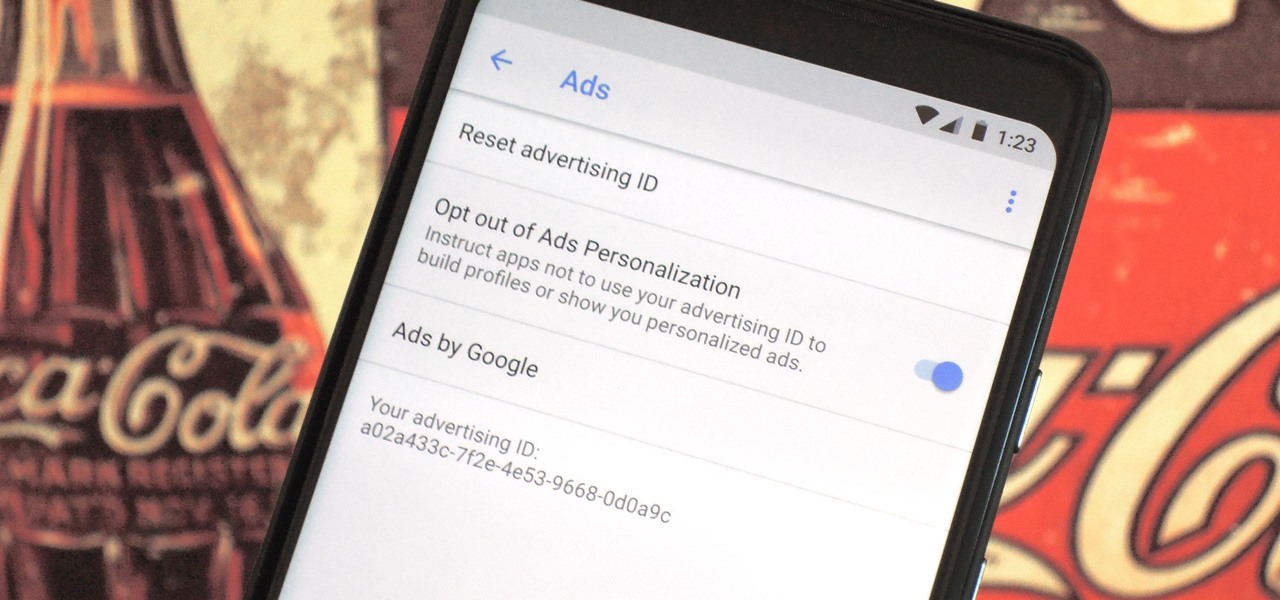
Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

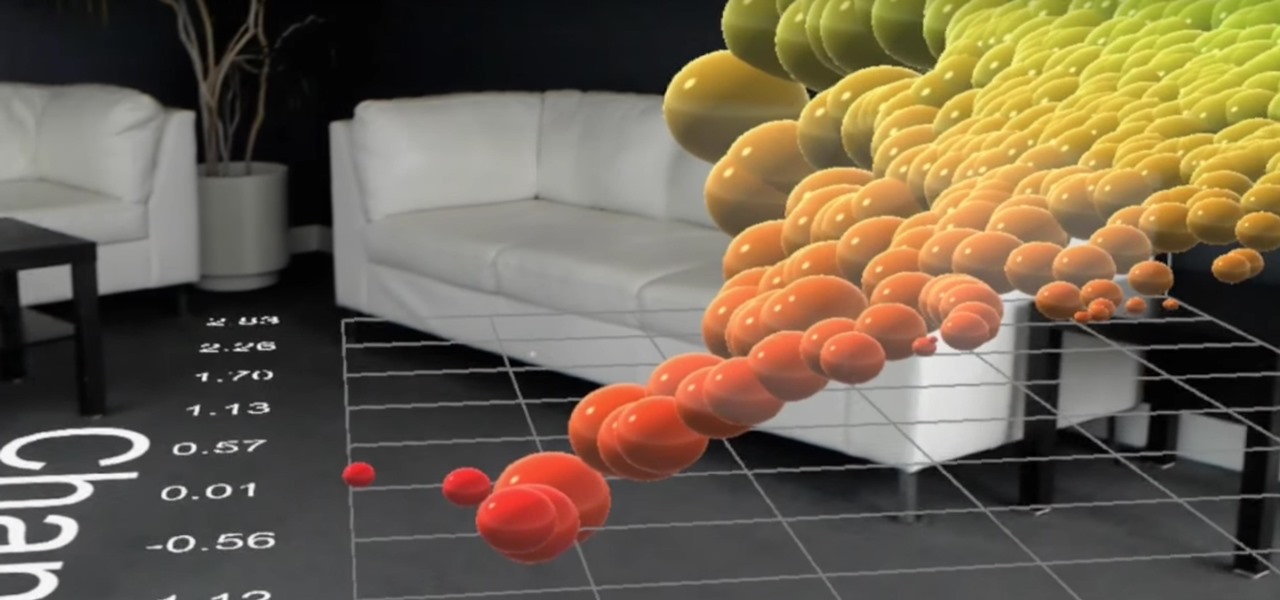
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

In this video DavidDaGeek shows how to clean your keyboard by removing your keys, but to be careful when doing this. Put your finger underneath a key and just pull it off. Don't break the piece that holds the key in place though! he starts at the shift key and works to the left with the ? being next. Then remove the hair or dust with your fingers. Don't remove them all at once because you might forget what order they go in. To put the key back in, put it in its spot, and click it back in. You...

In this tutorial, we learn how to use the feature keys for your Cricut machine. There are six feature keys on every cartridge. The first is the shadow feature key that create a matte to highlight your letter. The shadow blackout key creates a solid matte that doesn't cut out the holes in between the letters. The charm feature key puts a charm top on the top of letters. The sign feature key puts letters inside of a small sign post, making it one inch from top to bottom. The slotted feature key...

In this video tutorial, viewers learn how to replace a key on a Samsung notebook keyboard. This task is very fast, easy and simple to do. Begin by placing the small retainer clip into the small areas of the key. Make sure the retainer clip is aligned on top of the keyboard and is securely placed on. Then simply place the key over the retainer clip and press on it. Hold the bottom of the key with one finger and press down the key with another finger. to secure it in place. This video will bene...

If you need to add some decoration to your keys, a key fob is the way to go. Key fobs are decorative items that many people carry with their keys. There are many different ways to go when creating a key fob, but one of the best ways is to make your own using fabric from the store.

Popularized by artists like Son House and Skip James, Delta blues is not only one of the oldest forms of blues music, it is among the most stylistically distinct and technically rewarding to play. In this video guitar lesson from YouTube user deltabluestips, you'll learn the how to play blues standard "Key to the Highway." While this lesson is geared more toward intermediate and advanced guitarists, this means beginning players merely have all the more to learn. Get started playing "Key to th...

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how you can mix tracks in the right key. Ever wondered why the mix sounds a little dodgy even though it is perfectly beat matched? It could be because the two tunes playing are not in the same key or of a key that is suitable. Watch this two part DJ tutorial and ...

A video tutorial on how to use the wiimote to control a Lego NXT robot. Link to download GlovePie: http://carl.kenner.googlepages. com/glovepie_download

When life gives you limes, make a key lime tart! Harnessing the tartness of limes, a key lime pie offers a surprising and delicious contrast to savory summer foods like BBQ ribs and french fries.

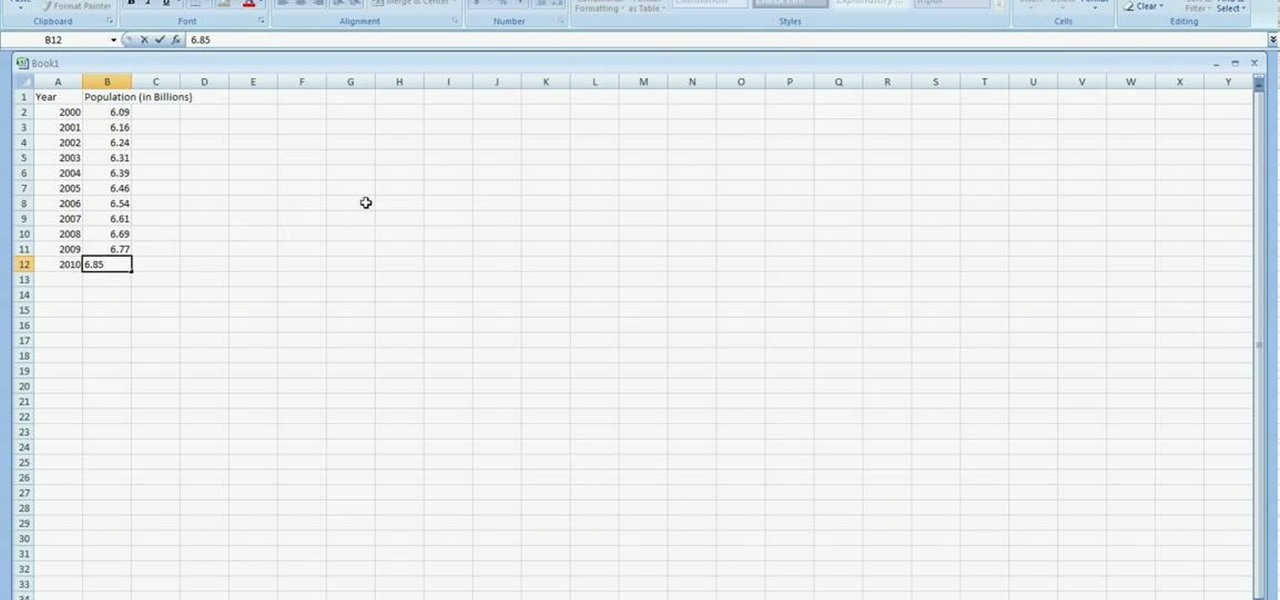
In excel a left click is made on box A1 and the X title is typed in as year. In A2 the year 2001 is typed and in A3 the year 2002. Both A2 and 3 boxes are highlighted and the bottom right hand corner is used to drag the work into a copied sequence down to A12. In B1 "population in billions" is typed. From the web site the data is copied and typed in as it appeared and the numbers are rounded off. A click is made on the "insert" tab and line is selected from the menu which appears. The upper l...

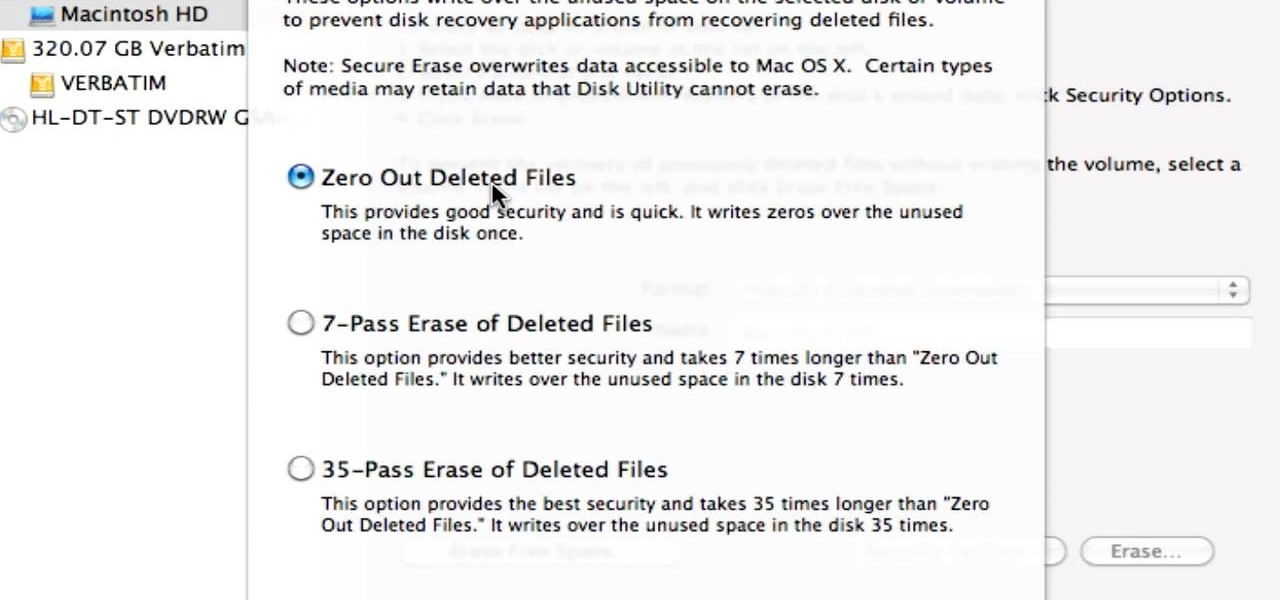
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

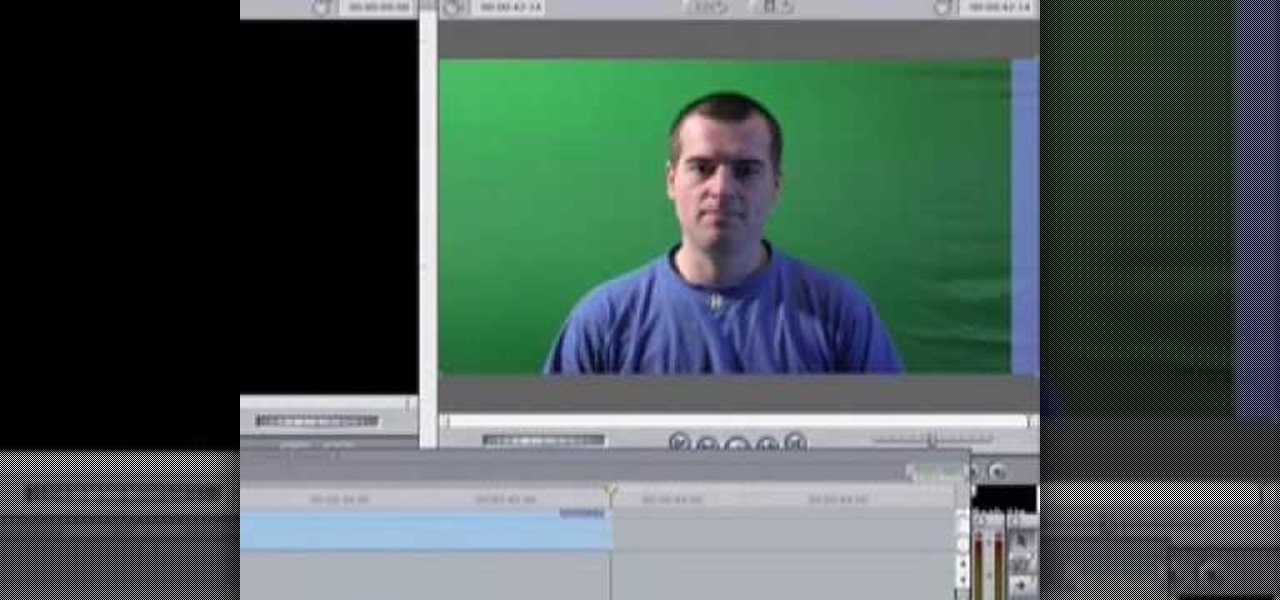
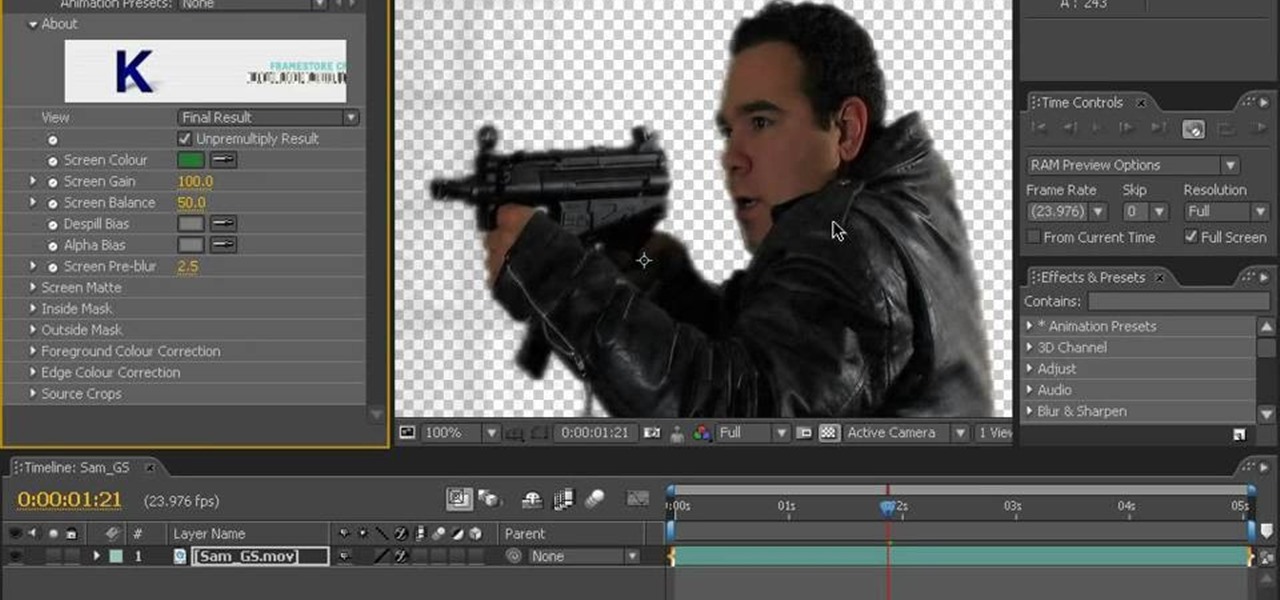
This Final Cut Studio software tutorial teaches you how to key out a green screen using Final Cut Express. This is also known as Chroma Keying. Once you have keyed out your green screen, you will be able to add effects and filters to your footage and create great movies in Final Cut Express.

Love key lime pie? Then you'll totally flip over these key lime flavored cupcakes. Key lime flavored cake paired with key lime custard give you (almost) more lime-y goodness than you can handle.

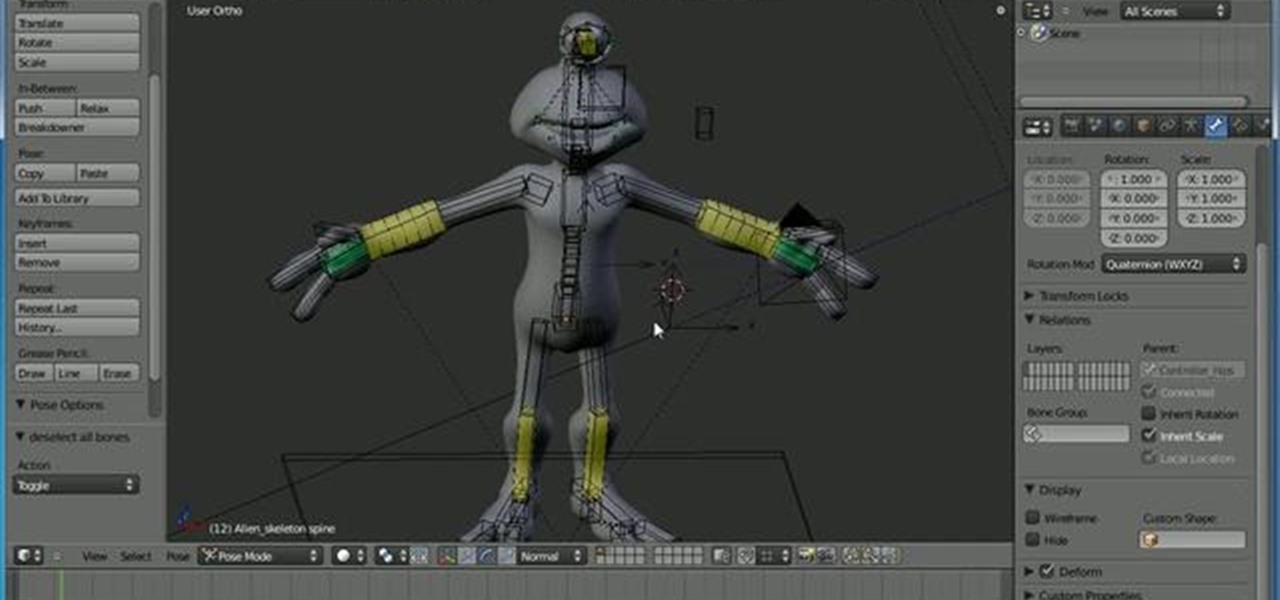
This tutorial goes over creating shape keys (or shapekeys) within Blender and goes on to apply drivers to the shape keys so that the armature can control the them. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information, including step-by-step instructions...

Green screens are clever devices that have saved movie studios millions of dollars in production fees because of their ability to let you tack on any background you desire digitally.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use the keyboard on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

This instructional video explains the basics of Chroma Keying in Final Cut Pro. This is used when you want to remove or key out a specific color from a scene. Created as a component in the Temple University Instructional Video Database.

This video demonstrates how to make a bump key, a key that will open any lock. To do this, just file down the key, add some bumpers, put it into a lock, tap it, and turn the key.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

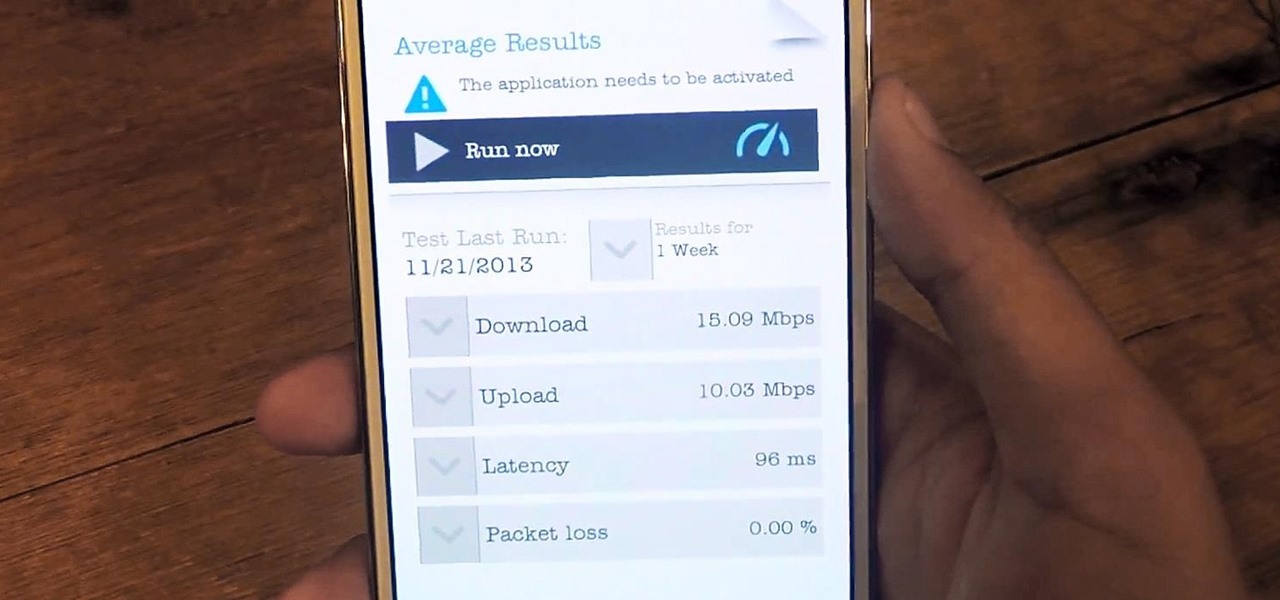
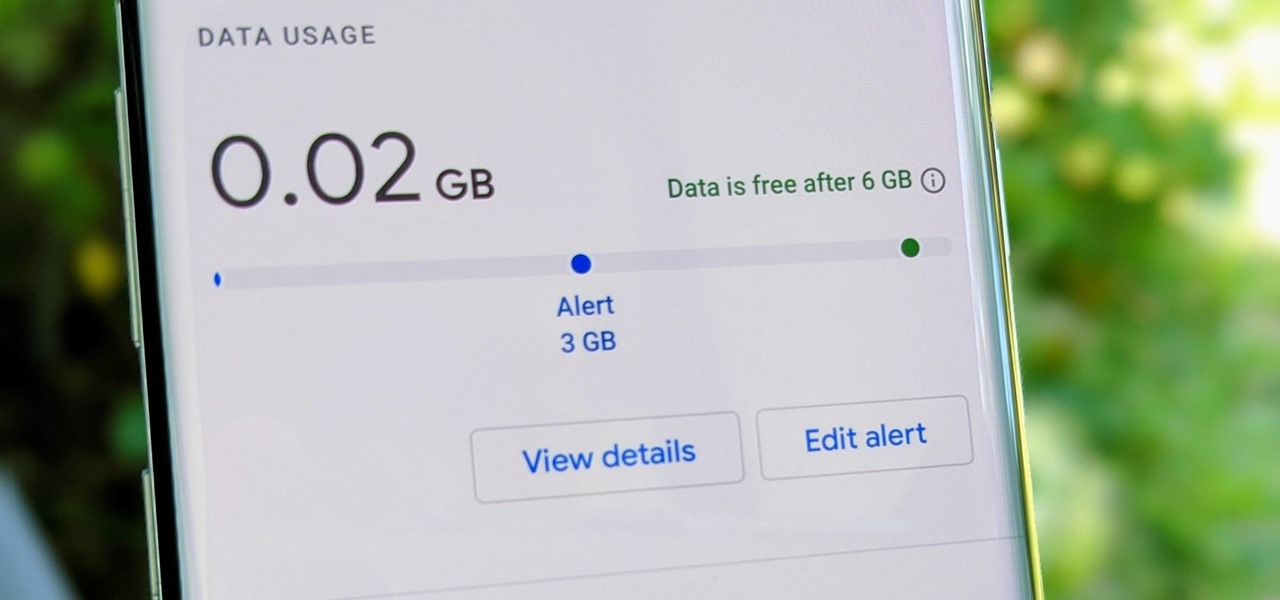
Google Fi Is a great wireless carrier alternative and can be quite beneficial when used correctly. If you don't require much data, you can easily get away with a $30 or less bill. However, if you wanted to crank out more data during your current billing cycle, there's a setting you should use to keep your data in check.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.