The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Although the initial reception for the Galaxy S9 has been generally positive, recent reports paint a potentially bleak image — some S9 owners are complaining that their new devices have "dead zones" in their displays, which don't register their touch inputs. Luckily, there are steps you can take to fix this problem.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

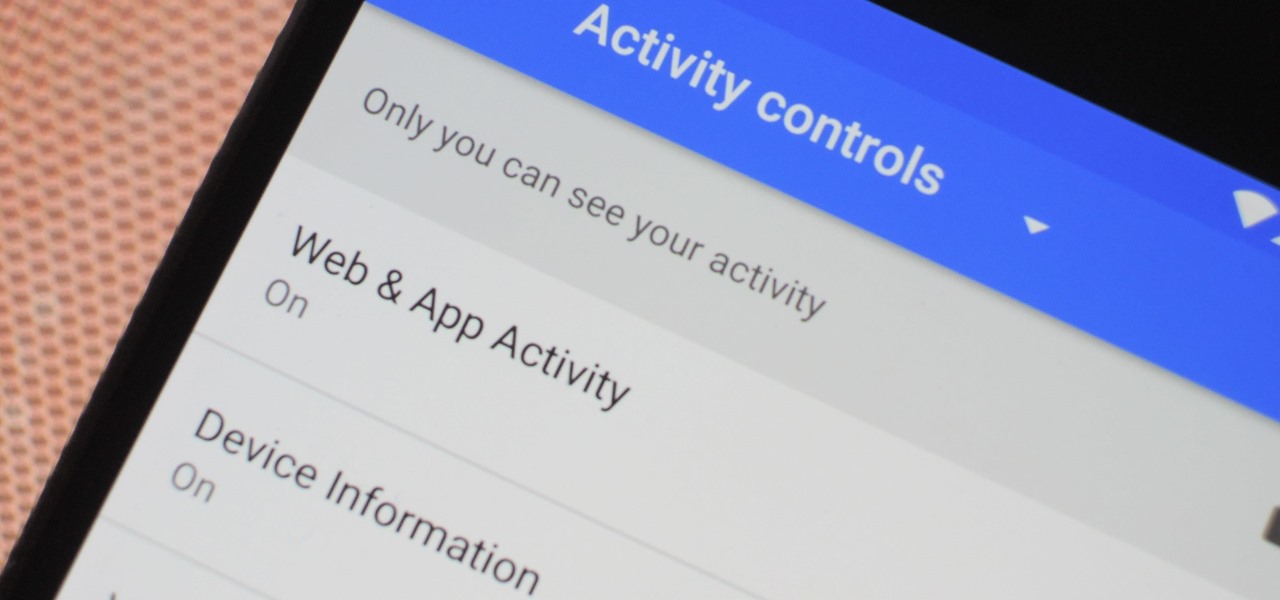
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

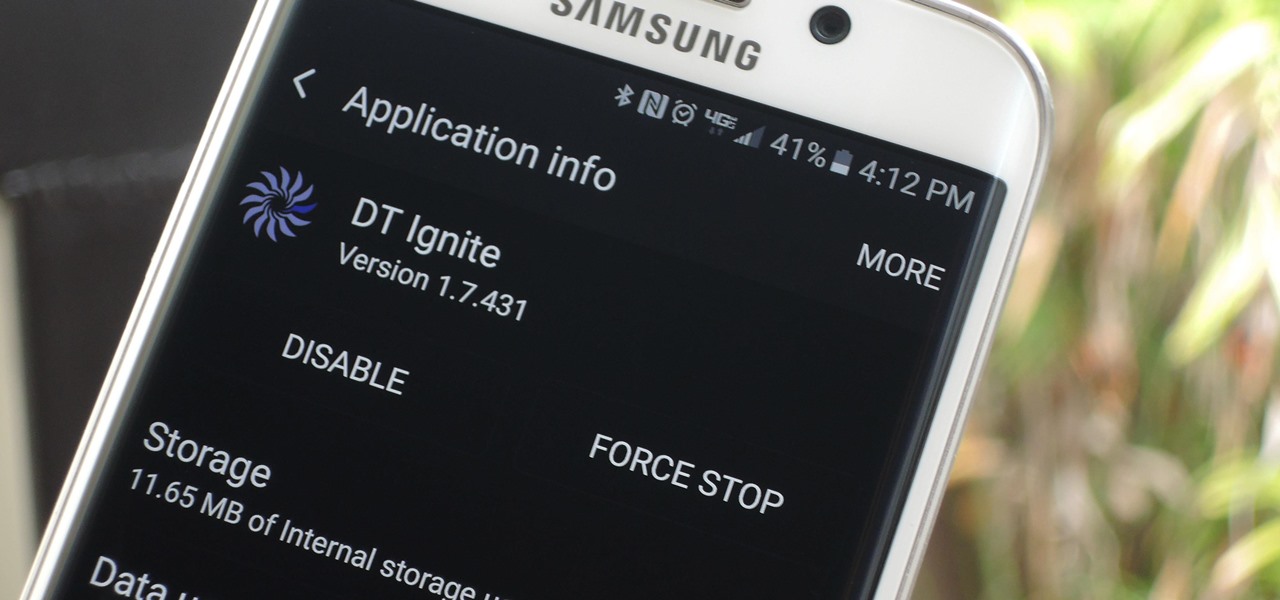
A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

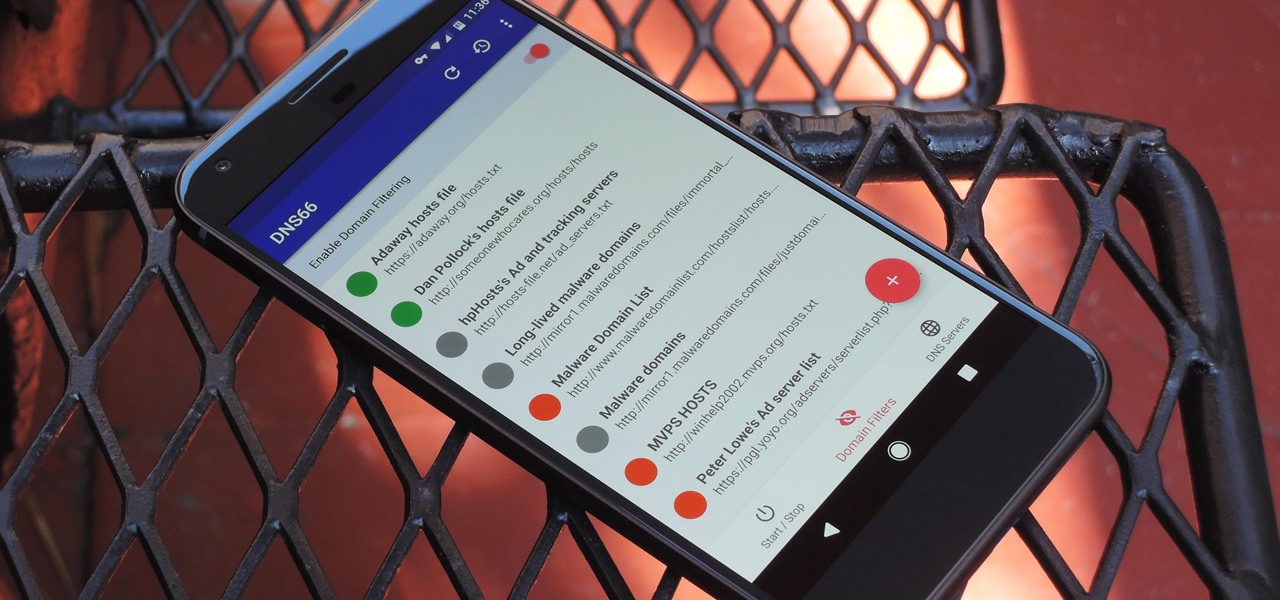
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

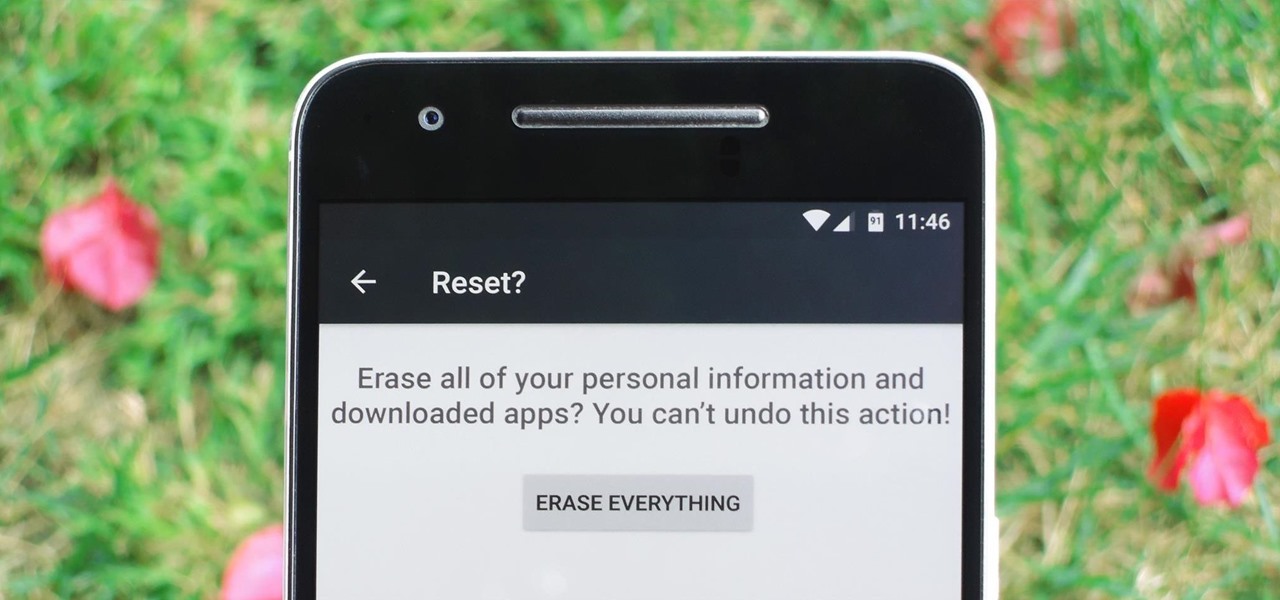
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad.

It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

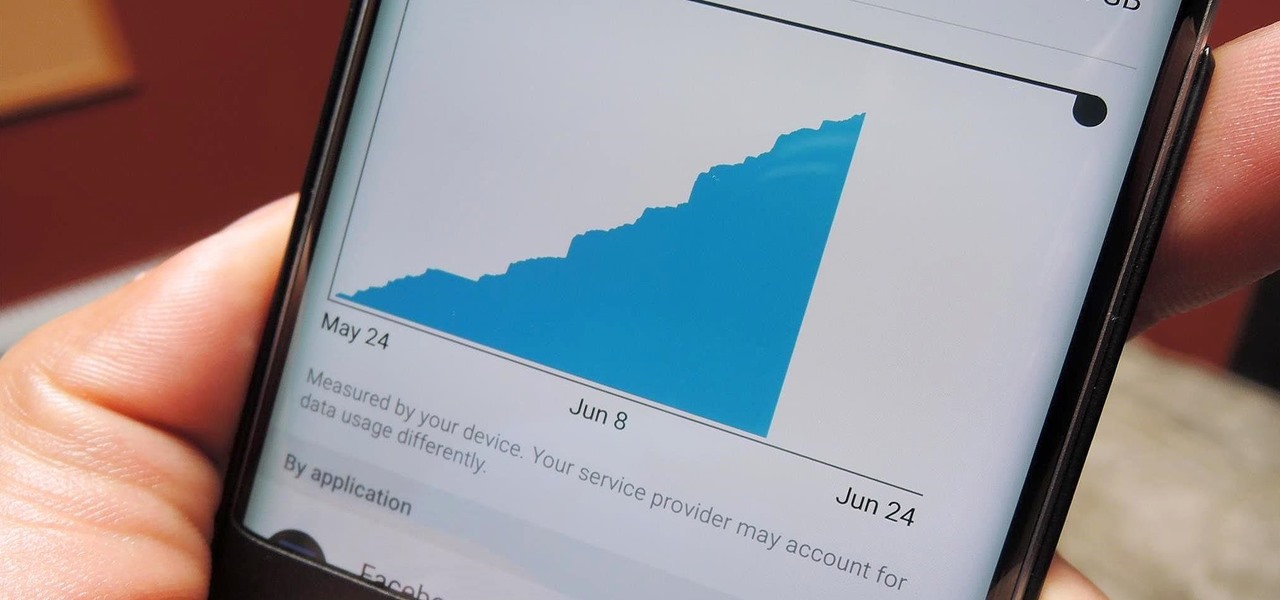
When you're not using your phone, it doesn't make much sense that it would be wasting power by maintaining an internet connection for the inside of your pocket or purse. Well, perhaps you need a little bit of intermittent data here and there so that apps can update themselves in the background and still post notifications, but it doesn't need to be constant.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

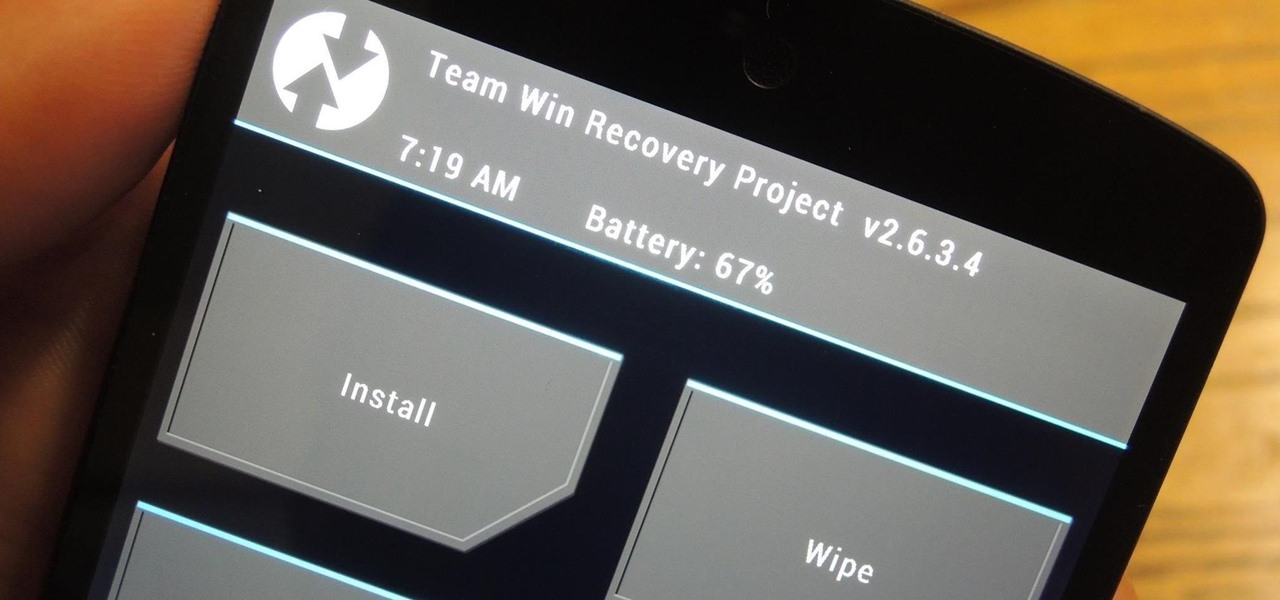
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

This is for all you vegans out there who crave the taste of key lime pie more than Dexter. Traditionally key lime pie is not vegan, so in this inventive recipe I've made it vegan and you won't believe what makes it green!

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

If you want to increase your privacy and prevent iPhone apps from gaining access to data containing your location, take a look at this tutorial on turning off the location services in the settings menu on Apple's iPhone 3G devices and above.

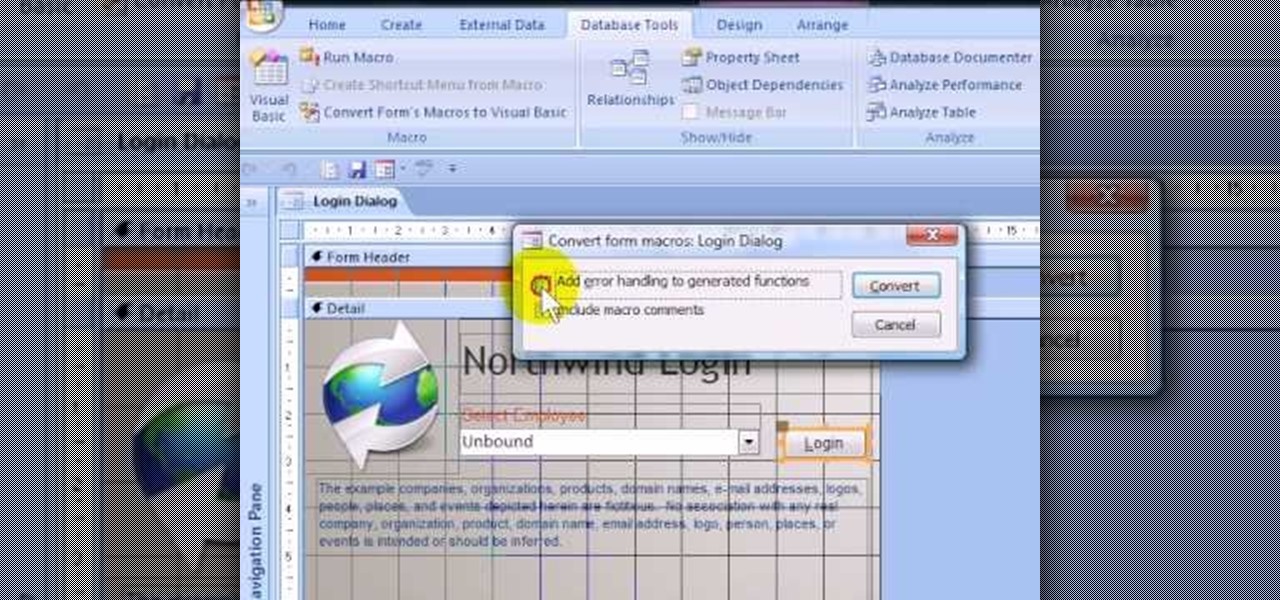
If you want to password restrict some of your data, or just want to know who is doing what in Microsoft Access 2007, you will want to set up a login form for MS Access 2007. This is an easy procedure, and you can create one yourself with just a basic understanding of the structure for MS Access. Watch this video, and Uncle Gizmo will show you how to do a login form and several other forms for MS Access.

Learn the secret to running the FaceTime video phone call app over your iPhone 4's data plan with this hacker's how-to. For all of the juicy details, and to get started making video calls over cellular internet on your own Apple iPhone 4, watch this video tutorial.

If you're having problems with your iPad, sometimes restoring it to factory settings is enough to get it working again. This will erase all your data, so make sure you back up everything. Then you can use these two separate methods to restore your iPad.

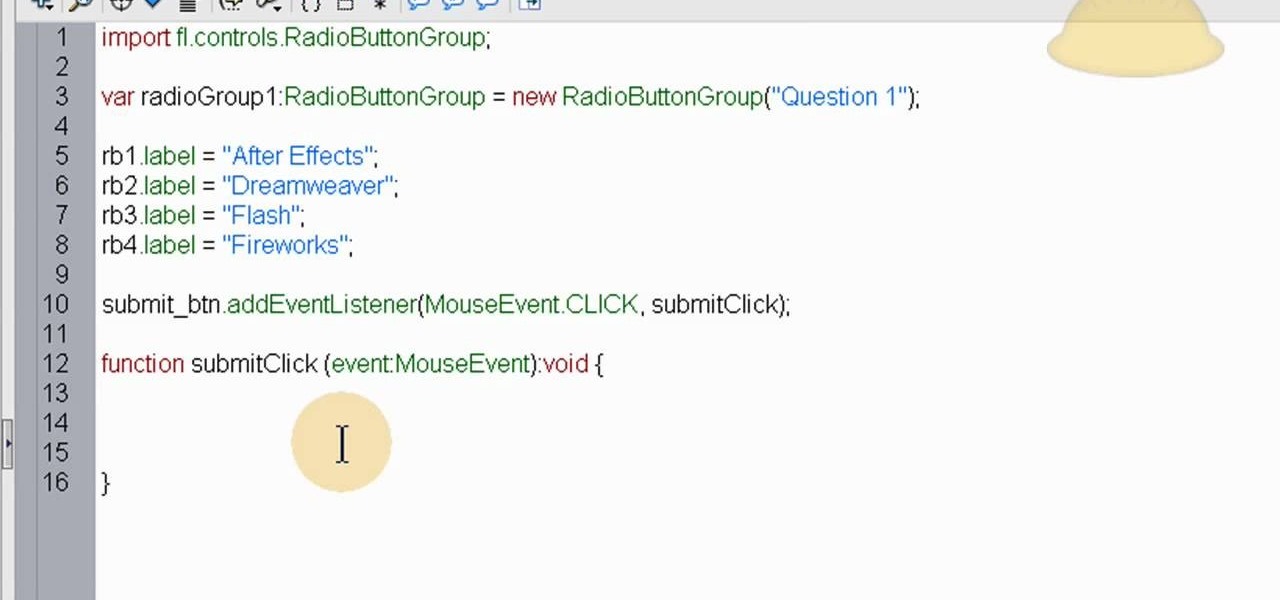
The quiz - a popular and pervasive form of content for websites. They can be just for fun, or to help you collect demographic data on visitors to your website. This tutorial shows you how to use radio buttons to write quizzes, tests and other similar forms in Adobe Flash CS3.

In this clip, you'll learn how to view graphs of statistical data from around the world with Gapminder.com. The website, you'll find, is diverting, often thought-provoking, and easy to use. For more information, including detailed instructions on how to use the site yourself, watch this video tutorial from the folks at Tekzilla.

In this clip, you'll learn how to visual data with charts and graphs in MS Project 2010. Whether you're new to Microsoft's popular project management application or are just looking to better acquaint yourself with the Project 2010 workflow, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

Fring is an app availble through the Apple store which will let you use your iPhone 4 to conduct FaceTime video chats over 3G. You can also use Skype or other chat programs with Fring. Make sure you pay attention to how much data you're using, it's easy to go over!