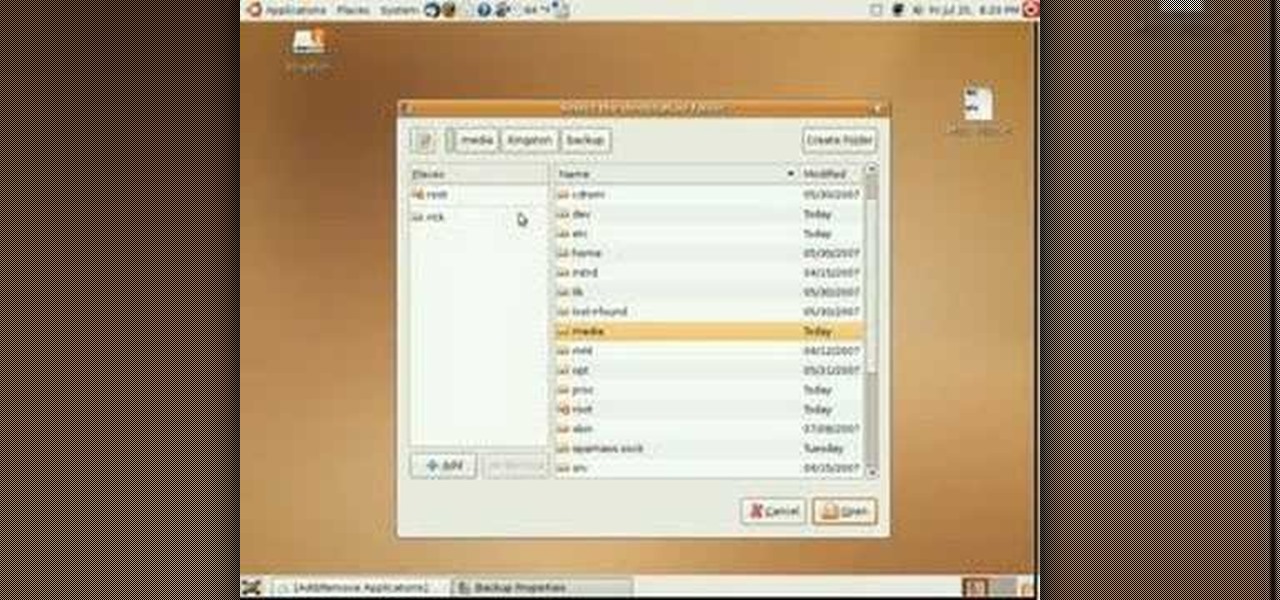
In this video tutorial, users of the Ubuntu Linux operating system will learn how to use the Simple Backup application to either manually or automatically back important data. For more, or to get started using Simple Backup on your own Ubuntu Linux system, watch this handy how-to.

Because of its portability, the acoustic guitar can be wonderful songwriting device. However, having a pocket symphony in your head–or pocket, as it were–does you little good if your hands aren't on board. Fortunately, YouTube user Sawlon is here to help you train your head and hands with his series of free video guitar lessons. In this installment, you'll learn how to use chord substituions in they key of G major on acoustic guitar. Remember, the more you practice and the more theory you kno...

Because of its portability, the acoustic guitar can be wonderful songwriting device. However, having a pocket symphony in your head–or pocket, as it were–does you little good if your hands aren't on board. Fortunately, YouTube user Sawlon is here to help you train your head and hands with his series of free video guitar lessons. In this installment, you'll learn how to play use chord substitutions in the key of E major on guitar. Remember, the more you practice and the more theory you know, t...
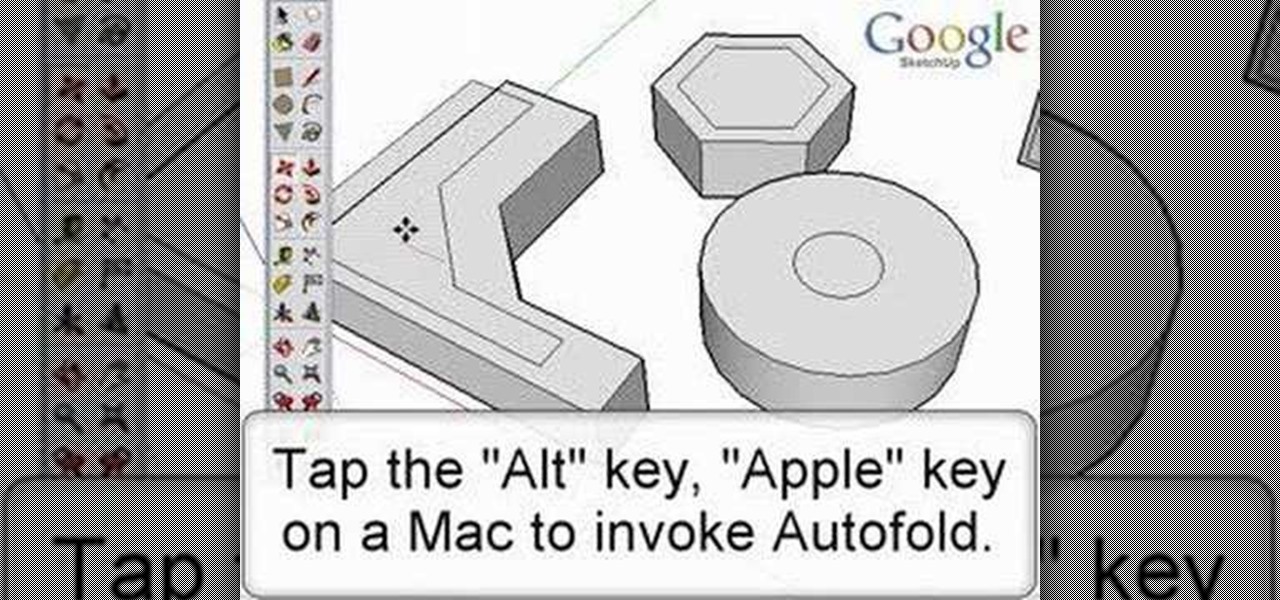
Autofold is part of the move tool and allows you to automatically create folding edges for new geometry. Take a look at this instructional video and learn how to use the move tool to autofold in Google SketchUp. The autofold can be activated by pressing the Alt key on the PC or the Apple key on a Mac. Autofold let's you move a point, edge or surface in any direction automatically creating fold edges as needed to do so.

Outlook is one of those applications that has 100 ways to do the same task. Today I’m going to show you how to automatically extract data from an email and have it populate fields in various modules in outlook (Contacts, Tasks, Calendar)

This cinematography tutorial video provides the basics of working with a photographic light meter as well as how to read the meter. A light and flash meter is nothing expensive. All you need is something that will measure the light and your flash. Most light meters are relatively the same. Metering is a relatively simple process. Just key in the ISO, key in the shuttle speed, push the button, and it gives you the f-stop to use on your professional photo camera.

Watch this software tutorial video to learn how to use HijackThis to find malware hiding in the alternate data stream. This how-to video will make finding hidden malware easy and help you protect your computer.

Do you need some extra cash? Is your clutter piling up on you? The perfect summer solution is a how-to on throwing and attending a yard sale. This week we show you how to prep and carry-out a successful yard sale, and show you how to spot a score. A few key points will help you spot the key piece for your wardrobe or next DIY project, whether it involves a yard sale or garage sale or what.

Look at this video tutorial to see how to remove viruses from your computer if you live in Charlotte, or anywhere else in the world. This will help you remove viruses from your computer yourself, without paying mega bucks to get it fixed. You'll see how to get a free virus scanner, for virus removal. This could take up to an hour or two, depending upon the data information on your PC.

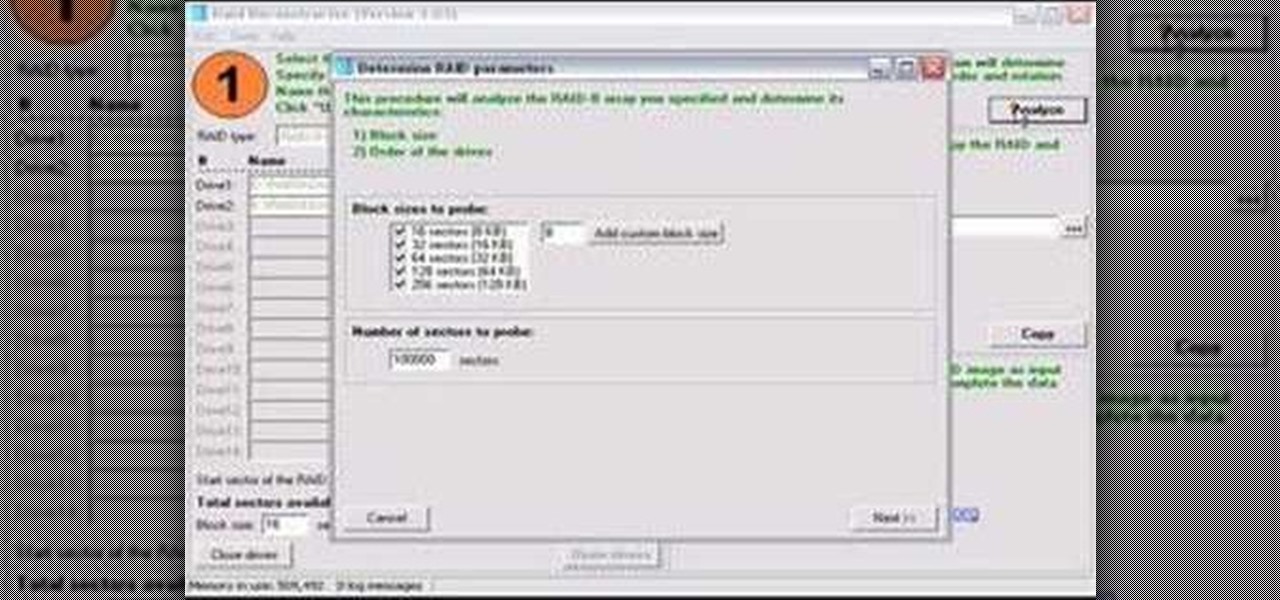
Check out this video tutorial on how to use the Runtime RAID Reconstructor software to create a destriped image with a two drive RAID 0. So, get your data back with this copy of your RAID to have recovery options for your computer. This program will collect, sector by sector.

This video gives a ten minute tutorial on how to achieve the superimposition effect for web videos with a little props and software.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

In this episode I show you a few of the innumerable uses of Quicksilver. Quicksilver is an unified, extensible interface for working with applications, contacts, music, and other data. The possibilities are endless. These are just a few of the ways that I use Quicksilver on a daily basis.

How to change the alignment of headings in Open Office Calc to fit all your data onto one page.

Larry Jordan explains the advantages and trade-offs of various external drive solutions, compares data rates or FireWire drives vs. SATA drives, what solutions work the best and how to avoid clogging your Final Cut Pro workflow.

Cells in Numbers '08 are the same as in Excel. Basically, they are where you store your data. This tutorial will show you how to use the different functions of cells.

A spreadsheet software wouldn't be much good if you couldn't use formulas and functions on your data. This tutorial goes over how to use them in Numbers '08.

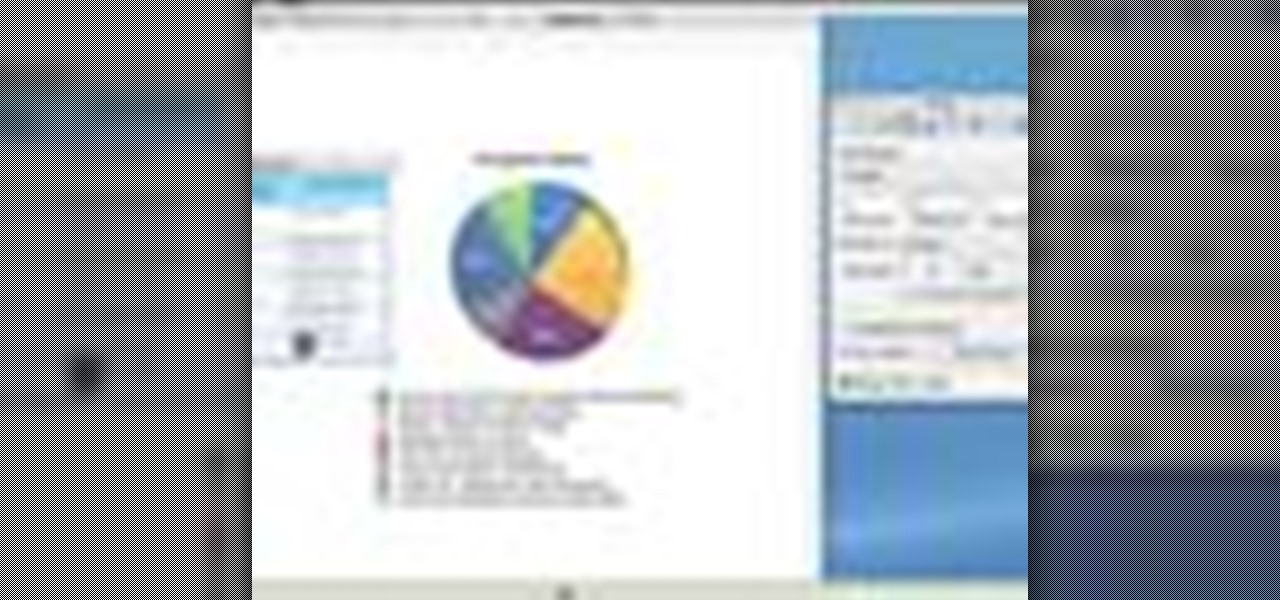
It's often best to use a graphical representation of the data you've assembled or calculated. This tutorial shows you how to create charts to visually show your results.

In Numbers '08 you can enter data dynamically with interactive buttons and sliders known as cell controls. This tutorial goes over using check boxes and sliders.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

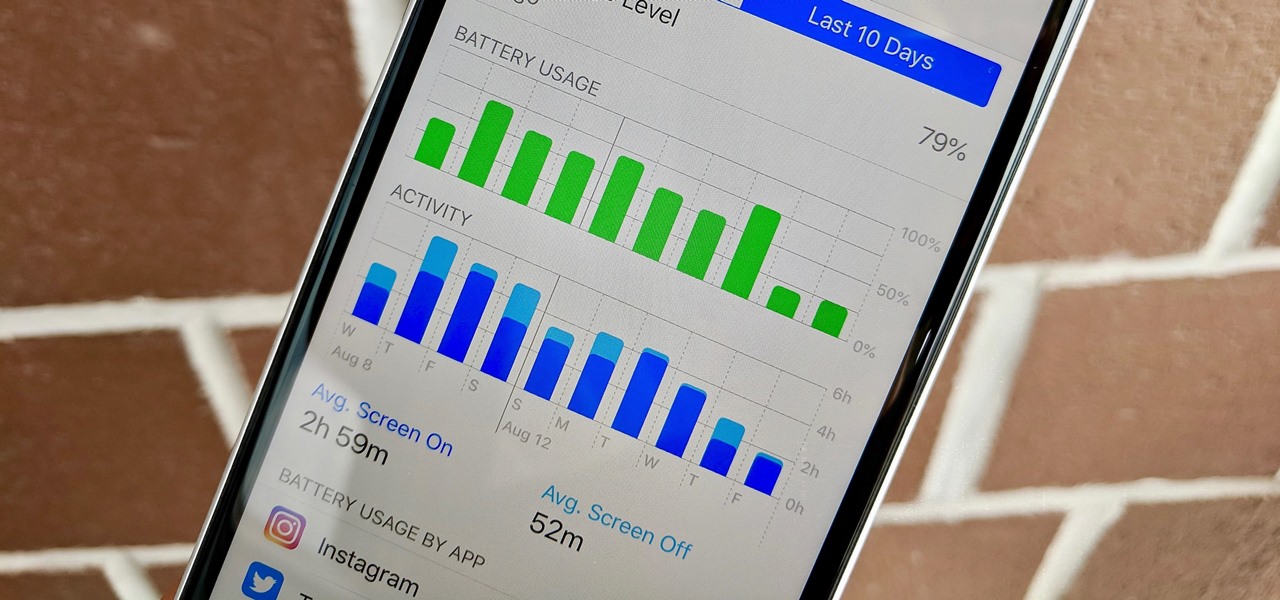
Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Another day brings another Apple ARKit demo, this time for a first-person role playing game that inserts villagers, vendors, and villains into real world locations.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

The new Google phones, which are rumored to ditch the Nexus moniker for Pixel, will most likely come with an Android feature that 7.0 Nougat doesn't currently have—a new set of navigation keys.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.