If it's an emergency, sometime you just don't have enough time or energy to pick up your mobile phone and call 9-1-1. Sometime you just can't move and the only thing still working is your mouth. Ford's new SYNC system provides an option for hands free 911 Assist. In a crash involving airbag deployment, 911 Assist places a call directly to a 911 operator. Your bluetooth phone must be on and stored somewhere inside the vehicle.

Sometimes pairing your mobile phone with your car is a difficult and unwritten chore to accomplish. But now with Ford's new SYNC system, you can easily pair your cell phone. It's as easy as pressing the Phone button. Let it search for already stored bluetooth devices, and if none are stored, simply press the Arrow buttons until you see the Add Bluetooth Device option. It's that easy!

To make sure your car is healthy and up to par with required maintenance, you can use Ford's new SYNC system to get vehicle health reports for you car. It gives you vehicle diagnostics, scheduled maintenance, recall information, and more. You just need to go online to your owner's account and set up your reports.

What if you're in the middle of a call before you enter your car? Ford's new SYNC system has a solution. As long as your cell phone is paired with SYNC, you can continue the conversation uninterrupted. See how to use hands free calling with Ford SYNC.
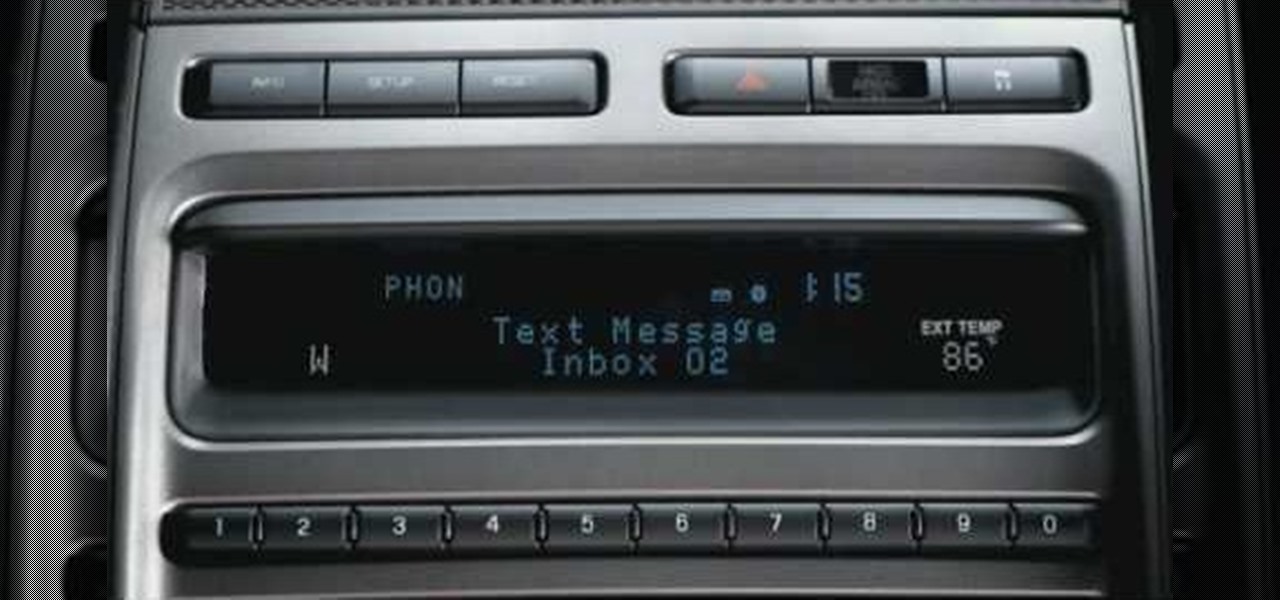
Texting is one of the biggest problems in automobiles today. It's very dangerous and distracting. Ford's new SYNC system makes texting safe for everyone, with audible texting. If you receive a text message on your mobile phone, SYNC can read the message to you out loud with the touch of a button. It can even translate LOL and smiley faces. See how!
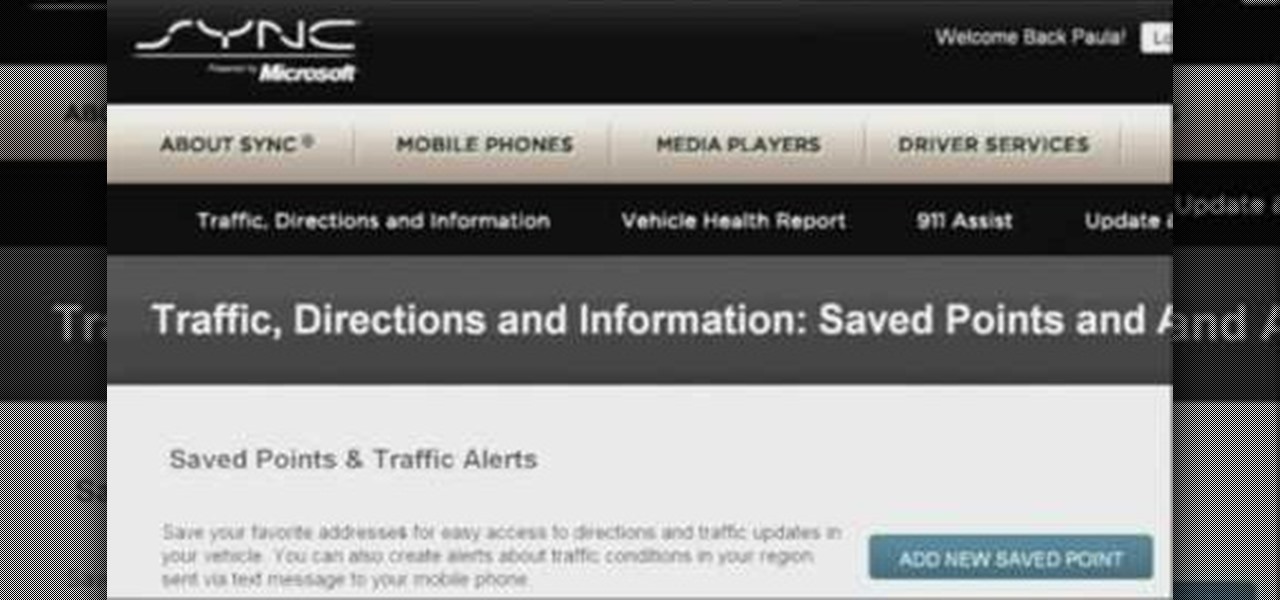
Customizing your user account online for Ford's new SYNC system is a cinch. Simply go to the website and customize news and sports, vehicle health reports, and your personal favorites. You can even start out by adding your favorite destinations for turn-by-turn directions later. Learn how to customize your Ford SYNC online user account.

Ford's new SYNC system makes it easy to receive personalized alerts, including weather, news, and sports alerts… hands free! You only have to go to your owner's account online and set your favorite alerts for your SYNC system. Then just press the Voice button and select your service.

Turn-by-turn navigation is easy with Ford's new SYNC system. Cities, businesses, your favorite places - name your destination and SYNC returns with your turn-by-turn directions. To add your favorite locations, you simply need to visit your owner account online, then you're ready to find your favorite directions, or any other directions needed.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

The ship in a bottle is an age old puzzle. The key to its mystery is pre-assembly, attention to detail and patience. Learn from a master craftsman and bottle ship builder the ins & outs of this art. Follow these step by step instructions on how to put a ship inside of a bottle.

Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

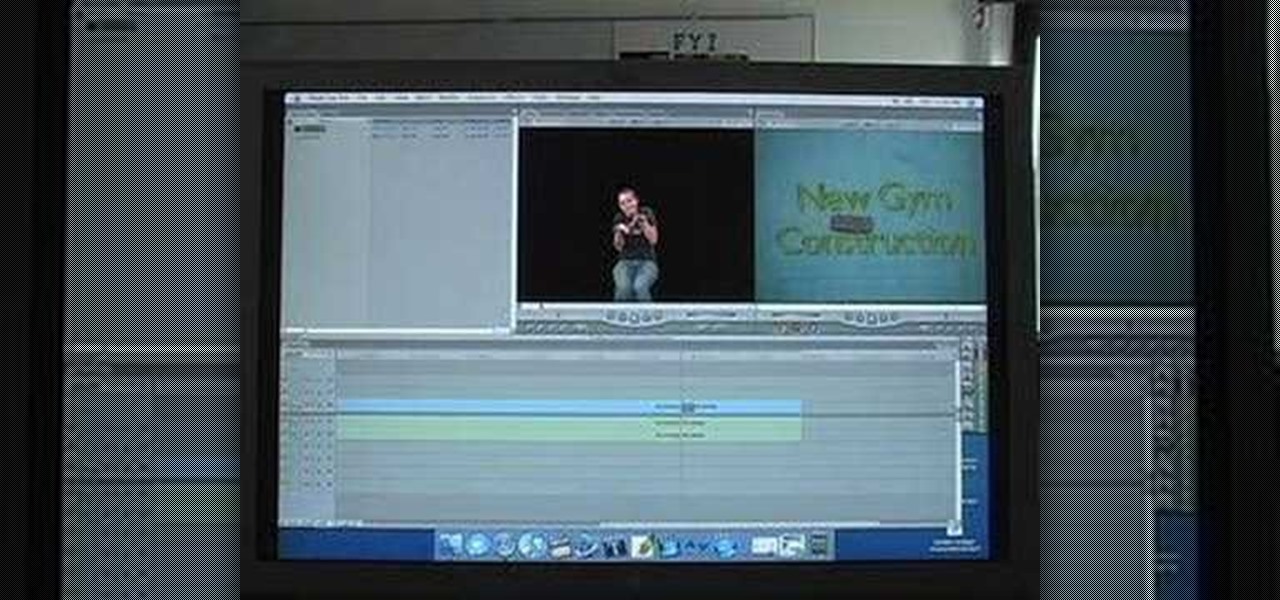
Here is a Final Cut Studio software suite tutorial on how to use the green screen function in Final Cut Pro. Footage that has been shot on a green screen can be brought in and isolated with Chroma Key settings. Once you have your subject removed from the green screen background, you are ready to apply hundreds of effects and transitions in Final Cut Pro.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

In this video tutorial, Chris Pels will show how to create a web service in ASP.NET and then call the service from another ASP.NET web site. First, learn how to create an .asmx component which represents a web service in an ASP.NET web site. When creating the web service learn how to control several aspects of the web service functionality with web service attributes. Next, see how to test the web service in the Visual Studio web service test page. Then learn how ASP.NET allows many .NET data...

A little slack key tutorial for a popular song. Left hand chords are basic and static, so remember to just keep that right thumb alternating and focus on those right hand picking fingers.

Charles Sedlak shows you how to master the 12-bar blues and a moveable 12-bar pattern. We will begin in the key of G. Pay attention and you'll never need another lesson, ever again (just kidding, you'll need more, much, much more).

James (The Amazing) Randi speaks on spoon/key bending and hidden picture reproduction. These were tricks pulled by Uri Geller to show he had psychic powers. Arthur C Clarke was one of many who spoke out against Geller and sought to distance the paranormal studies from Geller's bogus performances.

The key to this lamp is creating the luminescent shapes which represent electronic circuits or magic spells on the lamp surface. You could also do this on coffee tables or other objects you can make out of plexiglass - get creative!

Instructional video on how to make a real masterlock masterkey.

See how a simple rubber band can become a hidden answer key for a school test.

Learn to perform a Jiu Jitsu Ude Garami,also known as a key lock or hammer lock. This technique is done from a hook punch.

Matt, the Shirtless Apprentice, advises viewers on the proper procedure for lighting a green screen. The successfully implemented chroma key technique can significantly raise the production value of any video podcast. He gives specific advice on how to separate the light that falls on the subject from the light on the greenscreen, a traditionally tricky technique.

Being able to double or triple lift is key to performing a wide range of card tricks. This tutorial will teach you how to do it.

This how-to video shows how to build your own electric motorcycle; a nice way to change from gas to batteries to save the environment. There is lots of welding, but the key to welding is dropping the piece and checking if it stays together. Spindles and sprockets must align and then you are set. Check out this video customization tutorial and learn how to convert a motorcycle to electric power.

While Apple is full steam ahead on iOS 18, which is expected to drop sometime next month, it hasn't forgotten about iOS 17, which still dominates most users' iPhones. On Aug. 19, Apple issued a rerelease of its iOS 17.6.1 software for iPhone.

If you've ever used your iPhone's hidden Field Test mode to view your signal strength in decibel-milliwatts, locate the tower you're connected to, or find out the radio frequency in use, you no longer have to dig through all of the confusing-looking data every time you need to check. Apple updated Field Test's interface in iOS 15, and one improvement gives you more control of the Dashboard.

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.

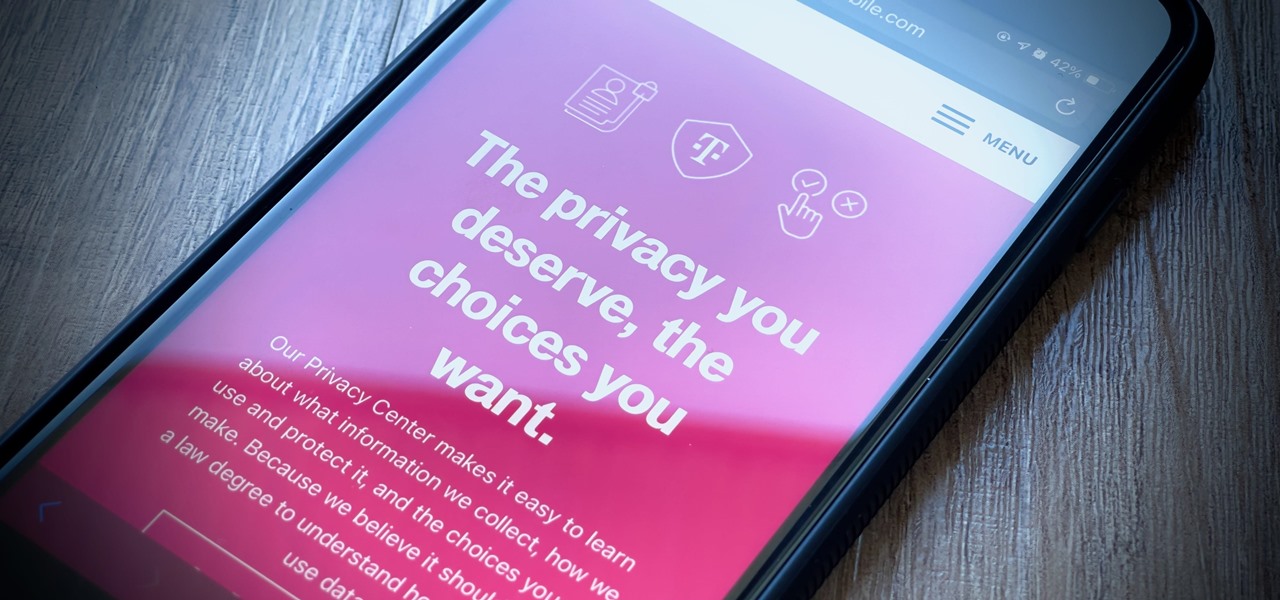
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Just as predicted (but perhaps with less fanfare than usual), Apple has made the move of adding a depth sensor to the rear camera of its latest edition of the iPad Pro.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

If you've been paying attention to the smartphone industry, you've certainly noticed a rise in dark mode lately. With most phones now sporting OLED panels, which use less power to display darker colors, users have been begging developers to include a dark theme in their apps. Lately, Google has been happy to oblige.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.