In this video the man describes of the circuit bending of Yamaha pss 140 synthesizer. This is a good model it's a FM synthesizers. It got many songs , many cool rhythms,nice trumpets and it is working real nice.Here he states that it is important for power supply or else we don't need batteries.First thing we have to do is open the case and we can see the wires related to battery supply but he doesn't need batteries. Keep the case aside so that you can get free space. Remove the screws so tha...
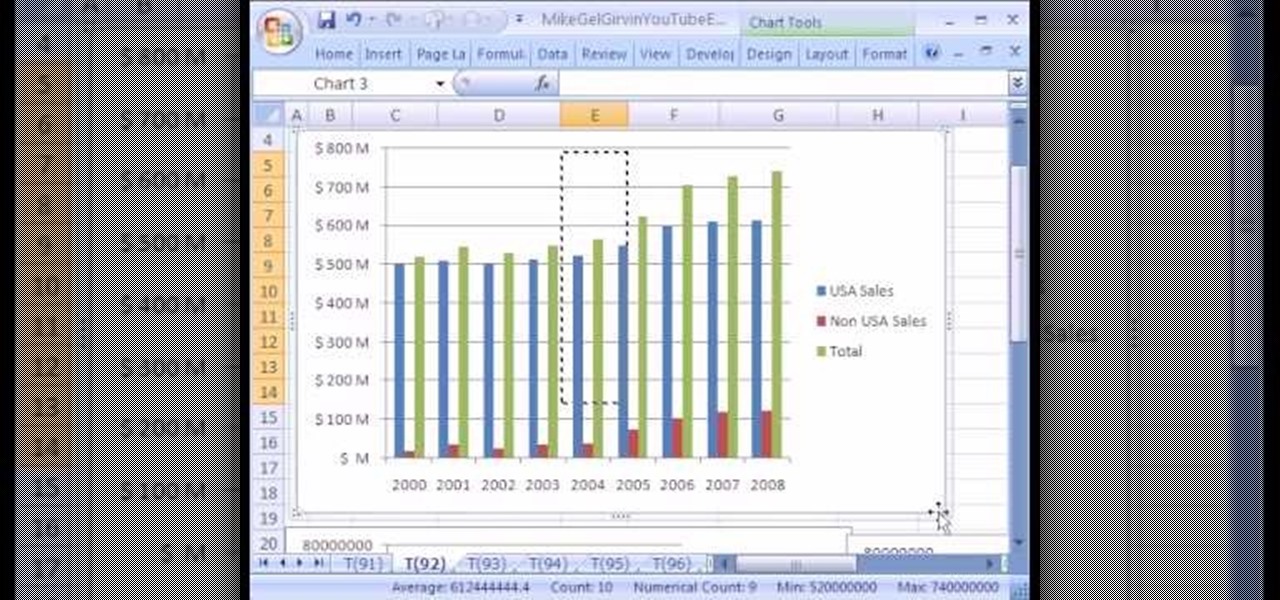
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 92nd installment in their series of digital spreadsheet magic tricks, you'll learn how to add data series to a chart, change the chart type for just one data series and see an excellent copy data to chart trick.

Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can also use Windows built in compression client to encrypt information. To use this feature you need not install any software and it is a fairly simple process. So select a file that you want to encrypt, right click on it ...

This video shows you how to easily copy data to and from your Motorola Droid. The first step is to connect your Motorola Droid to PC, using the data cable. Now, simply drag down the bar in the upper side of the screen and select USB Connected. Then, click on Mount in the popped up window. This will allow your PC to see the SD Card in your Motorola Droid and browse through it. Now, open My Computer, in your PC and open the Removable Disk that appeared. Easily click and drag or copy-paste the f...

Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

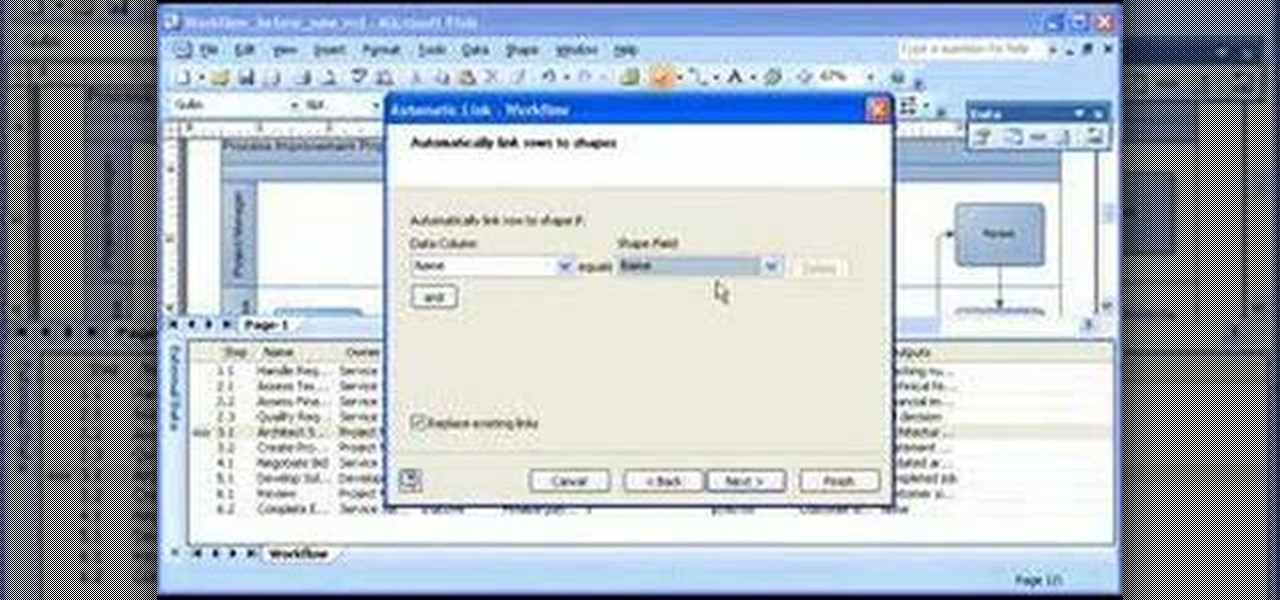
Take a look at this instructional video and learn how to analyze how a process or other area is actually performing by connecting data to the shapes in your diagram with Microsoft Visio 2007. You can also add different visual effects based on the data values. For example, you can link sales data from an Excel workbook to the shapes it relates to. When a phase of the sales process takes longer than guidelines recommend, the shape for that phase changes color or shows an icon that alerts you to...

In this video tutorial, Chris Pels will show how to group items when displaying data in a ListView control. First, see the basics of item layout in the ListView control with the LayoutTemplate and the ItemTemplate. Then, learn how the GroupTemplate relates to the LayoutTemplate and ItemTemplate within a ListView to establish a group of data. See how to use floating DIV elements to create a flexible tabular layout since any of the templates used with the ListView can contain any HTML. This pro...

While mobile data caps are larger than they used to be, many of us still have limits to contend with. If you find yourself up against that ceiling month after month, your iPhone itself might be to blame. Luckily, there's an easy fix to stop your iOS device from burning through data in the background.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

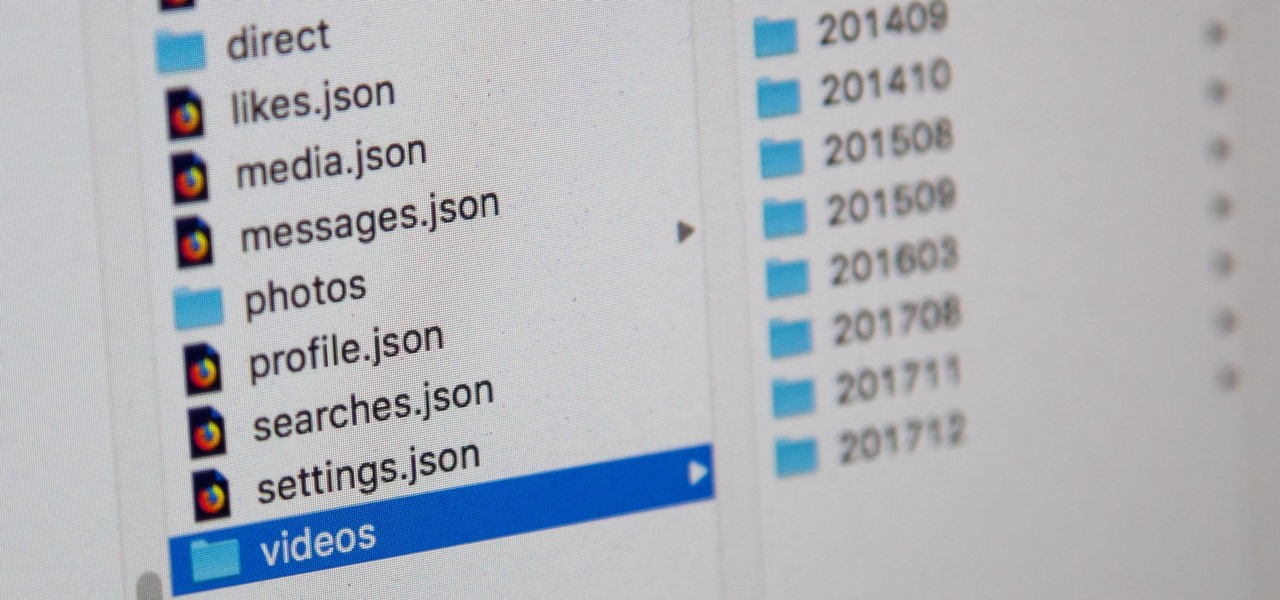
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

While I do enjoy the vanilla Android Lollipop experience that comes with the Google Play Edition HTC One, I do miss the sweet camera that ships with Sense. Luckily, the people behind Liberty ROMs found a way to port that camera over and now we can enjoy the best of both worlds... well, sort of.

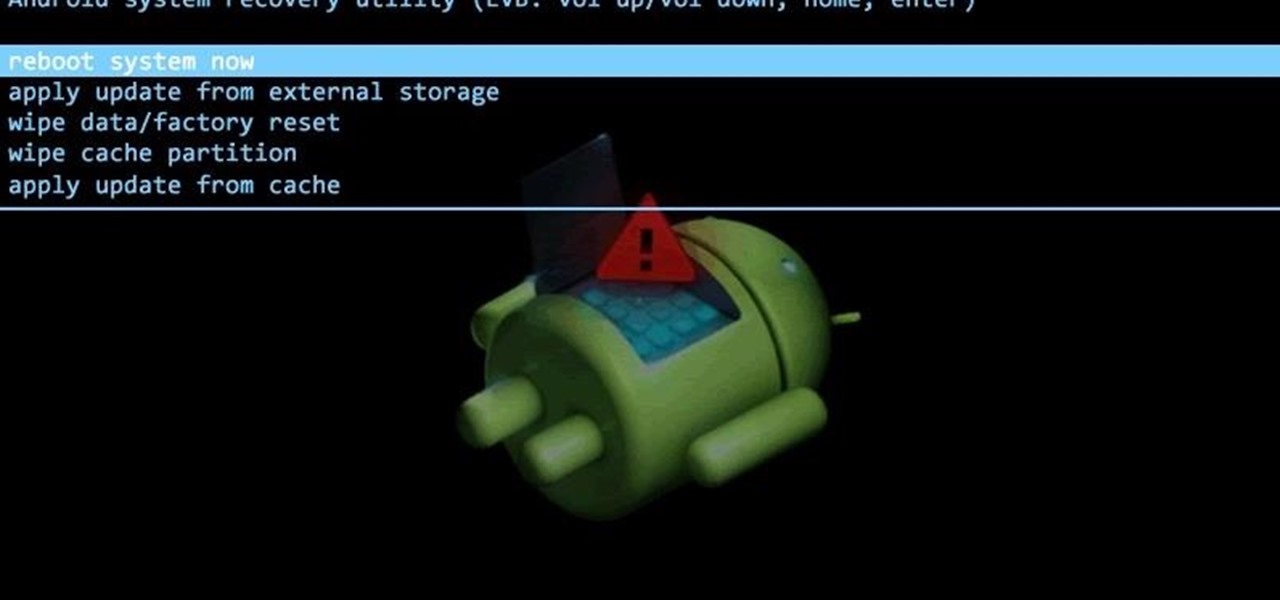
It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

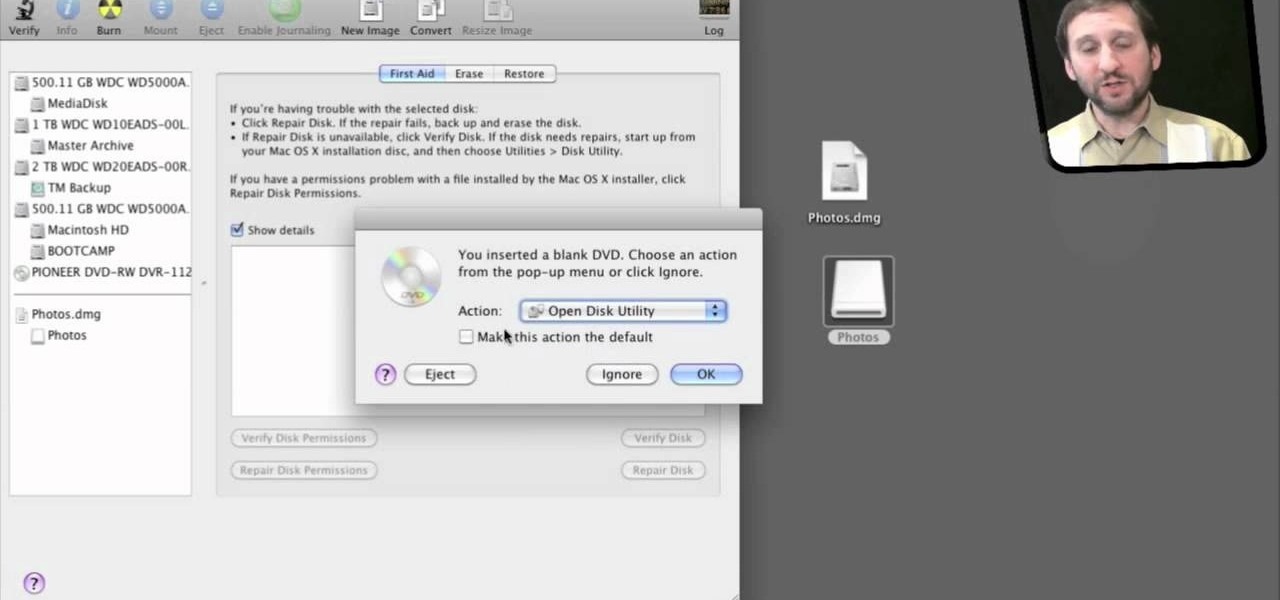
Here's something everyone needs to know: how to copy a data disk (CD, DVD) using disk utility on OS X when you only have one optical drive. You will need to create a temporary disk image on your hard drive. Then use that disk image to create physical copies of your disc.

Back up your computer data and save your time, money and valuable information using these helpful tips. There are several options to backing up and storing your important data, ranging from tiny keychain USB drives to backing up your files online. This informative and lighthearted video from Kipkay shows you how.

If you want to import data or recover files from your AppleTV back to iTunes on your computer, this shows you how. First you are shown how to gently take apart your Apple TV to access the hard drive, then hook it up to a Macintosh, and you can access your files and data structure from there!

Want to know how to use Google Data? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Looking for a guide on how to enter data into nonadjacent cells in MS Excel 2010? This clip will show you how it's done. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned professional looking to become better acquainted with the features and functions of Excel 2010, you're sure to benefit from this free video software lesson. Take a look.

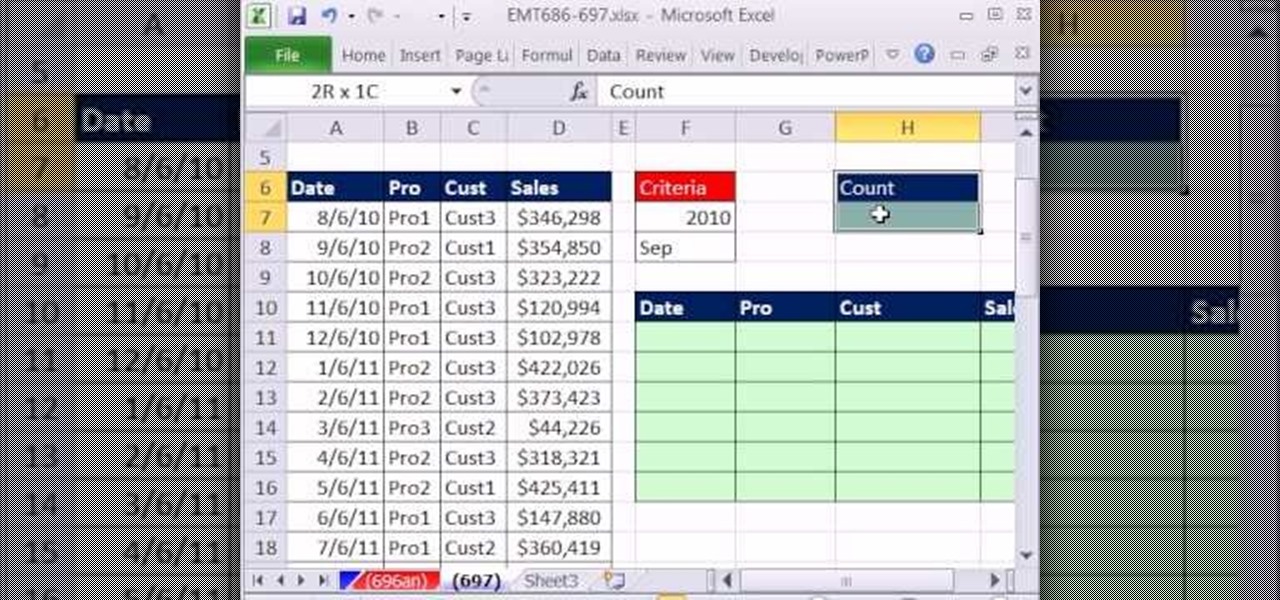
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to extract month and year data from transactional records by filtering, array formula and non-array formula.

This is a basic lesson with an intro for arrays in the C# programming language. You'll learn how to create and declare and add date to a C# array. An array is a data structure, or object, that contains several variables of the same type. Learn all about it!

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 675th installment in their series of digital spreadsheet magic tricks, you'll learn how to do data validation using a custom logical formula with 2 VLOOKUP functions that will change when different products are entered. For example, if shirt product is entered, the data validation will let only values between $50 and...

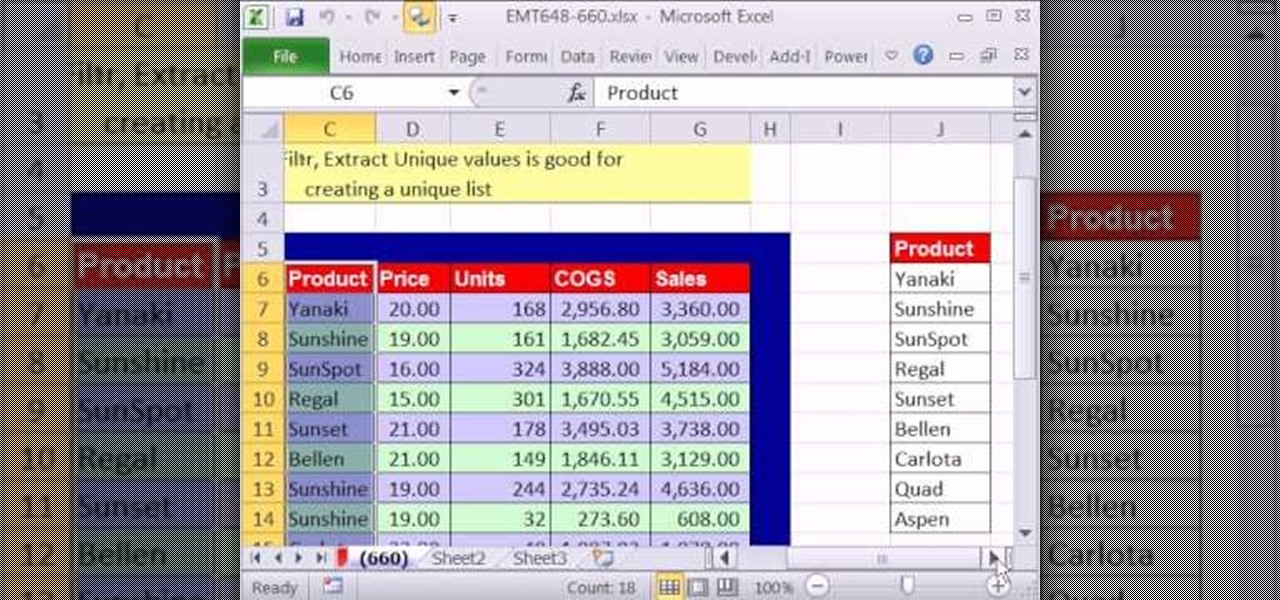
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 660th installment in their series of digital spreadsheet magic tricks, you'll learn how to extract a unique list from a data set using Advanced Filter.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 648th installment in their series of digital spreadsheet magic tricks, you'll learn see the functions ROWS, COLUMNS, and CHAR in a formula that will create a data set.

Need a little bit of help figuring out how to build custom data entry form components in Flash Builder 4? This clip will show you what to do. Whether you're new to Adobe's popular Flash IDE (previously titled Adobe Flex Builder) or simply wish to become better acquainted with the program, you're sure to find benefit in this free video software tutorial. For more information, including specific, step-by-step instructions, take a look.

Learn how to quickly import data into Microsoft OneNote 2010 with the Quick Filing tool. Whether you're new to Microsoft's popular note-taking application or a seasoned MS Office professional just looking to better acquaint yourself with the OneNote 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started quickly importing data into your own OneNote projects, watch this free video guide.

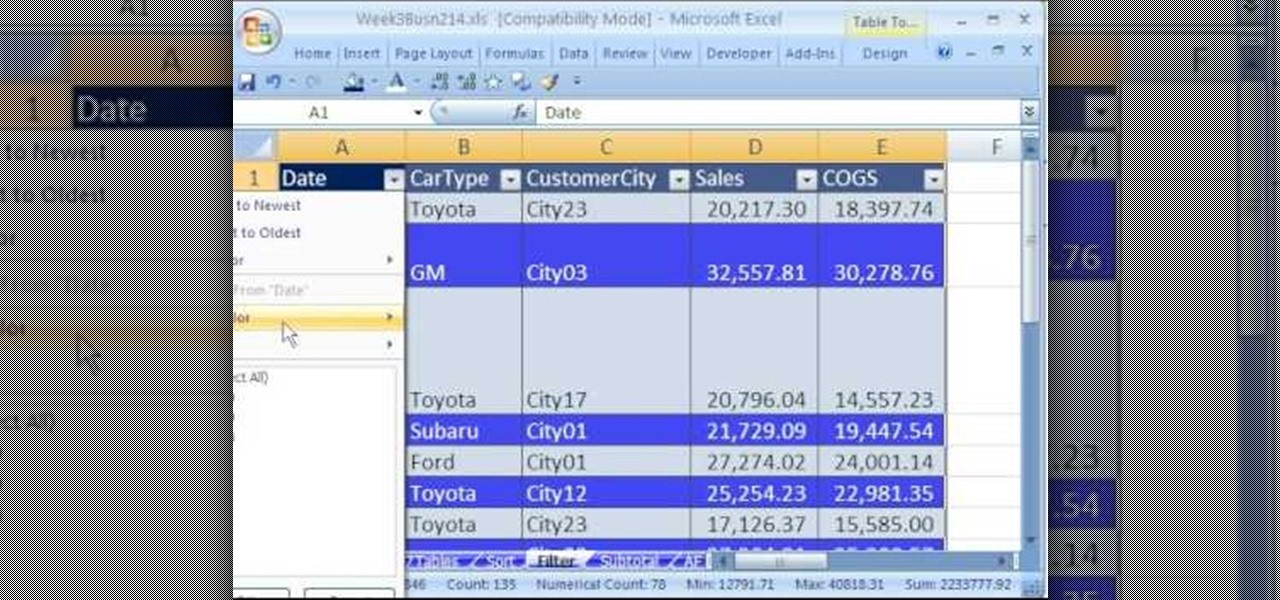
hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 17th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to filter spreadsheet data using eight different methods.

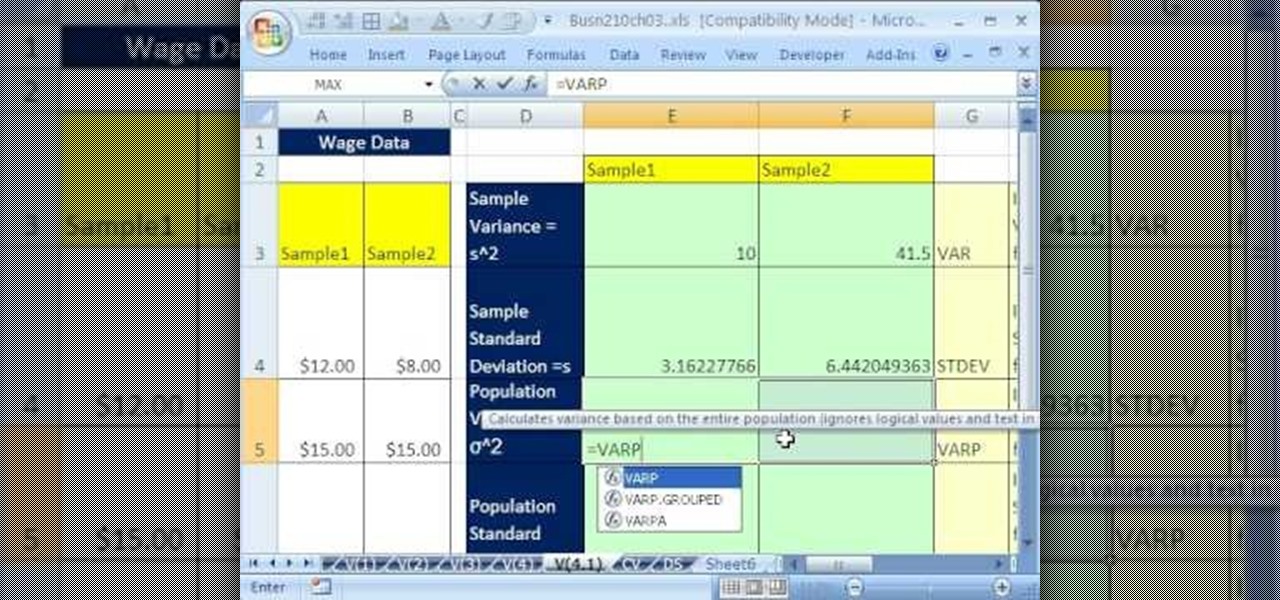
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 41st installment in his "Excel Statistics" series of free video lessons, you'll learn how to calculate deviations, variance and standard deviation for a sample and a population using Excel tables and the VAR, S...

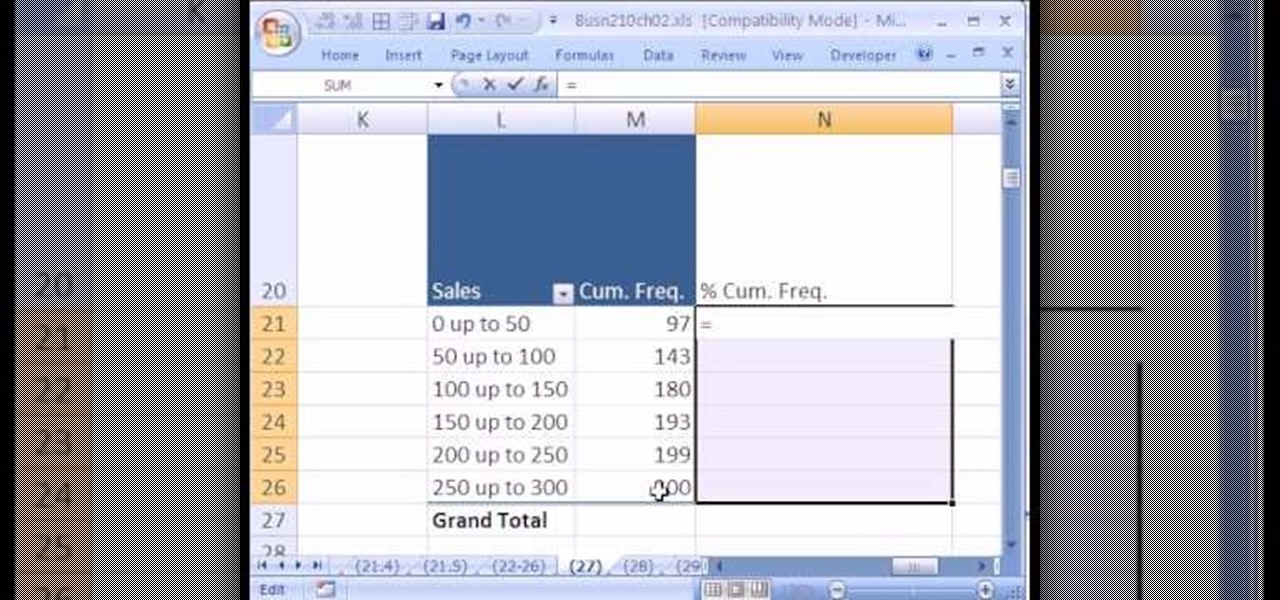
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 26th installment in his "Excel Statistics" series of free video lessons, you'll learn how to create quantitative data cumulative frequency distributions with pivot tables.