No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?
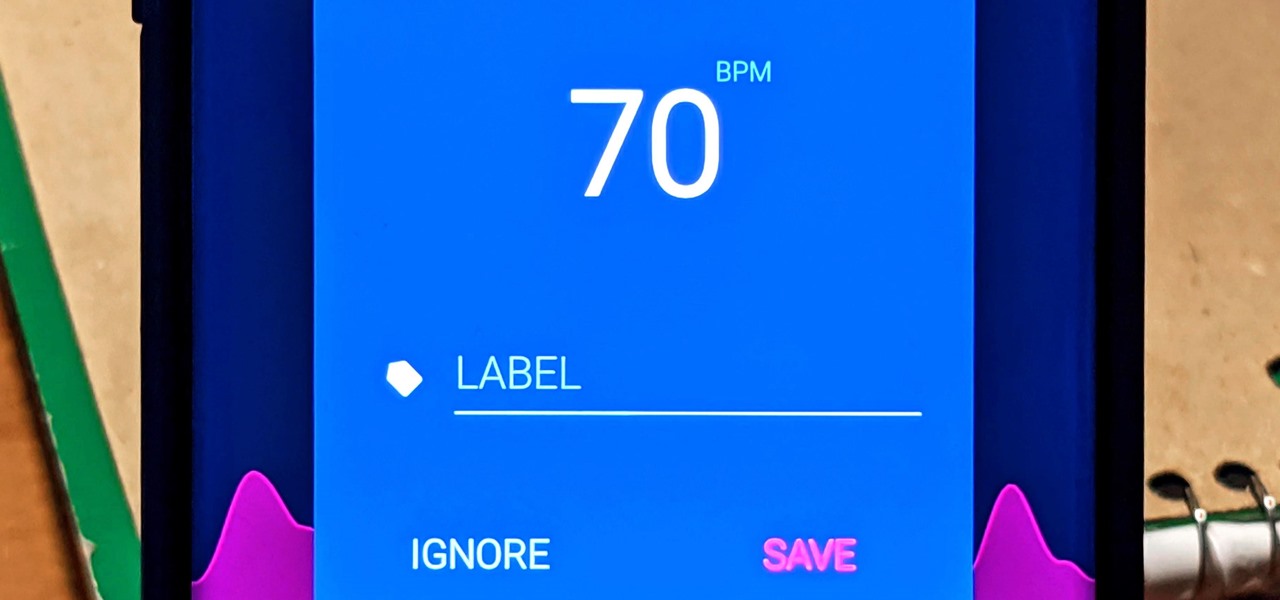
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.
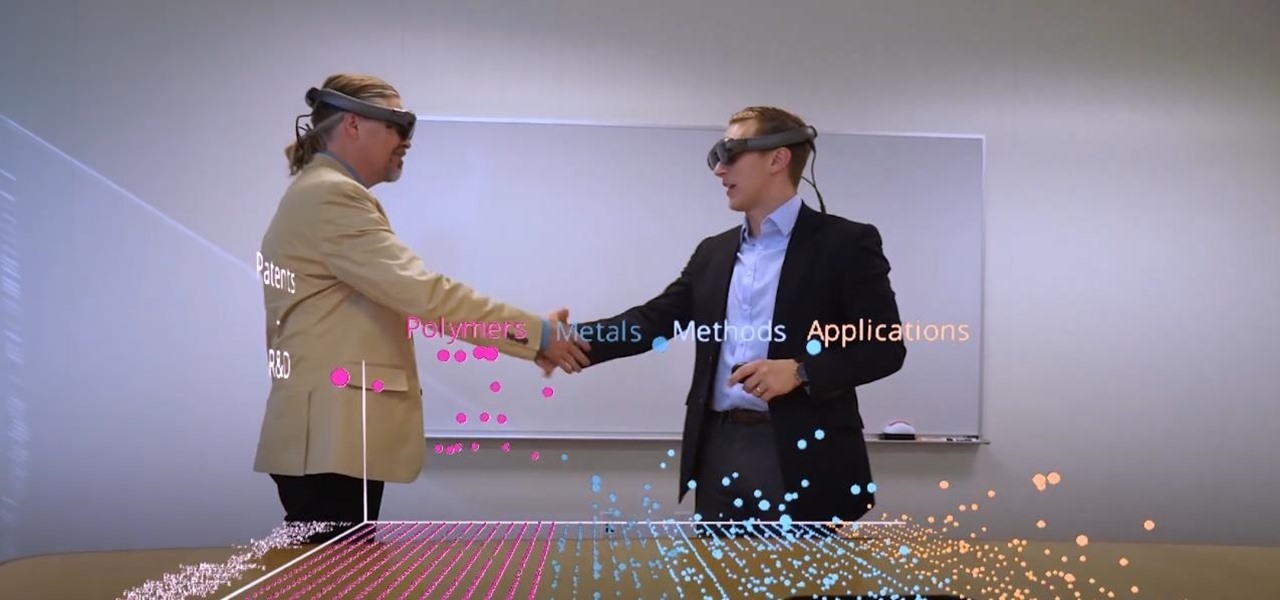
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

While the eyes and ears of the iPhone world are singularly fixated on iOS 13 and its suite of over 200 new features, Apple was actively piloting iOS 12.4 in tandem with the big iPhone update, in preparation for the release Apple Card. Today, Apple has finally seeded iOS 12.4 stable, 116 days after its first beta version, and there's still no concrete evidence that Apple Card itself will show its face.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Apple's goal with iOS 12 is to smooth out the problems with its famously flawed predecessor. Of course, change isn't for everyone, and by iOS 11.4.1, Apple had a pretty stable thing going. If you're not digging all the bugs and new features included in iOS 12, here's how to downgrade your iPhone back to iOS 11.4.1.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

In the arms race between ARKit and ARCore, Google scored a big win with the announcement of its Cloud Anchors shared AR experiences platform at Google I/O on Tuesday.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

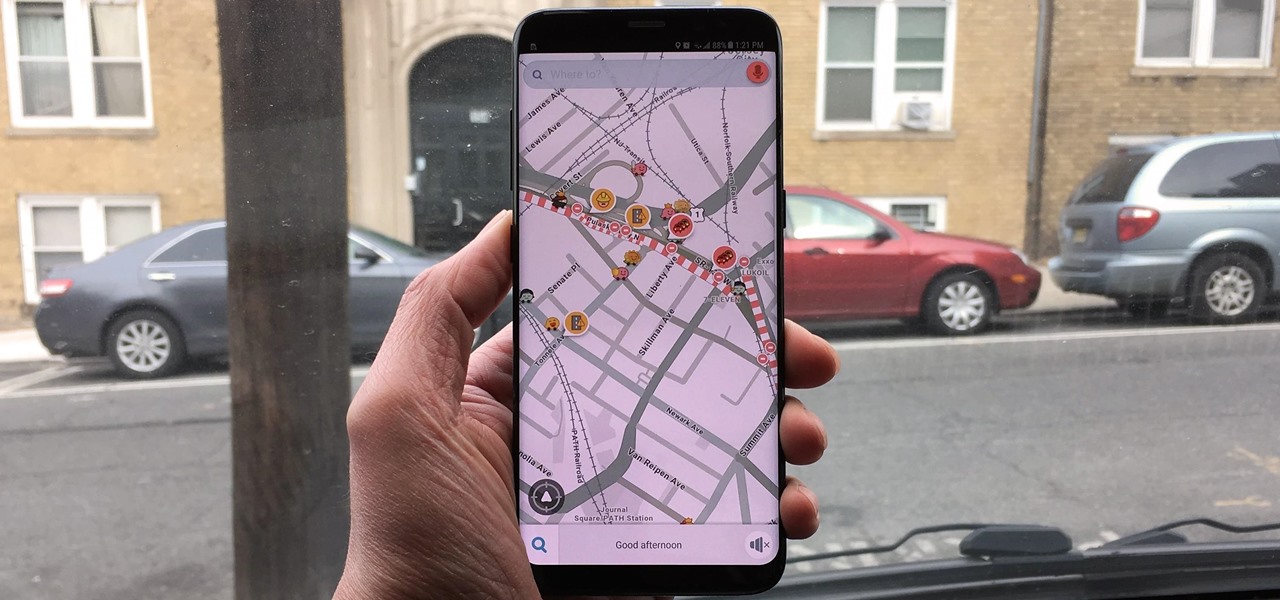
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

One of the best parts of being an Android user is the countless awesome features. Many of these features are well-known and user-facing, like custom icon packs and launchers, but some get lost in the shuffle. Back at Google I/O 2016, Android Instant Apps were introduced to developers and enthusiasts. Since then, the feature has seen a wider rollout, but few users are aware of it.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

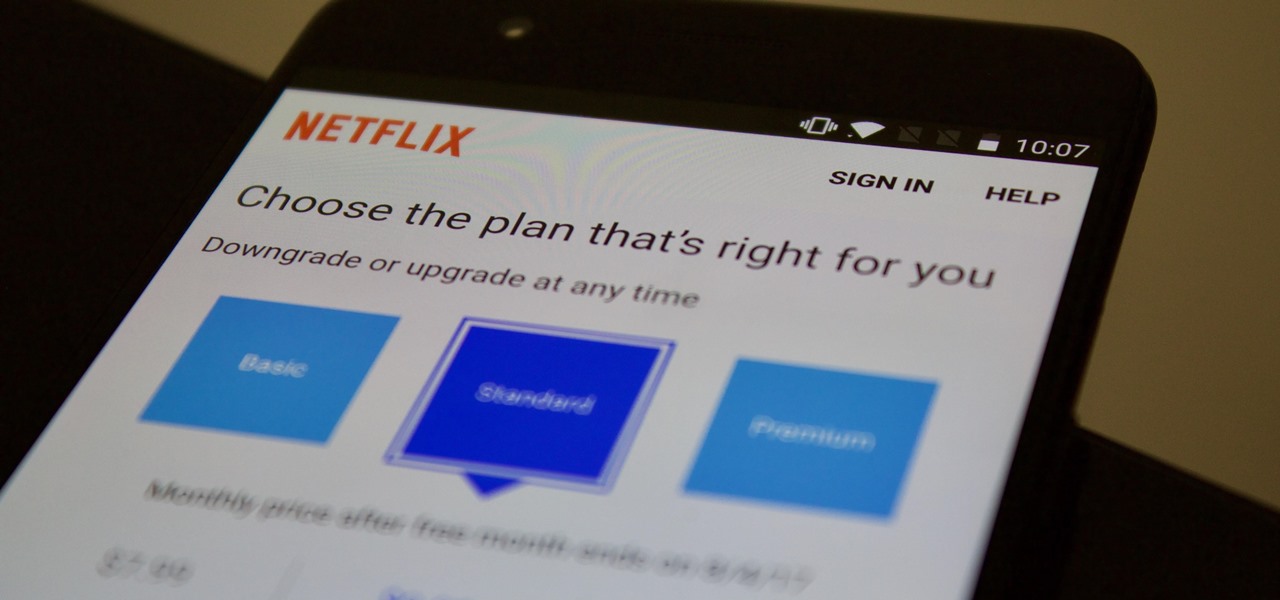
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.

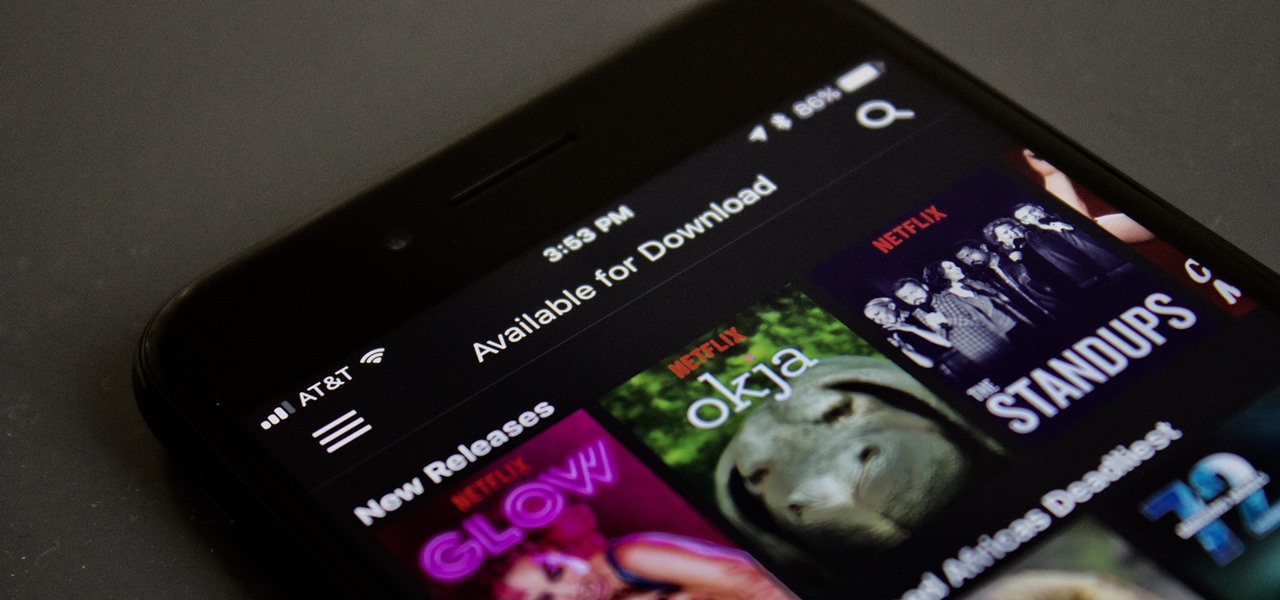
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.