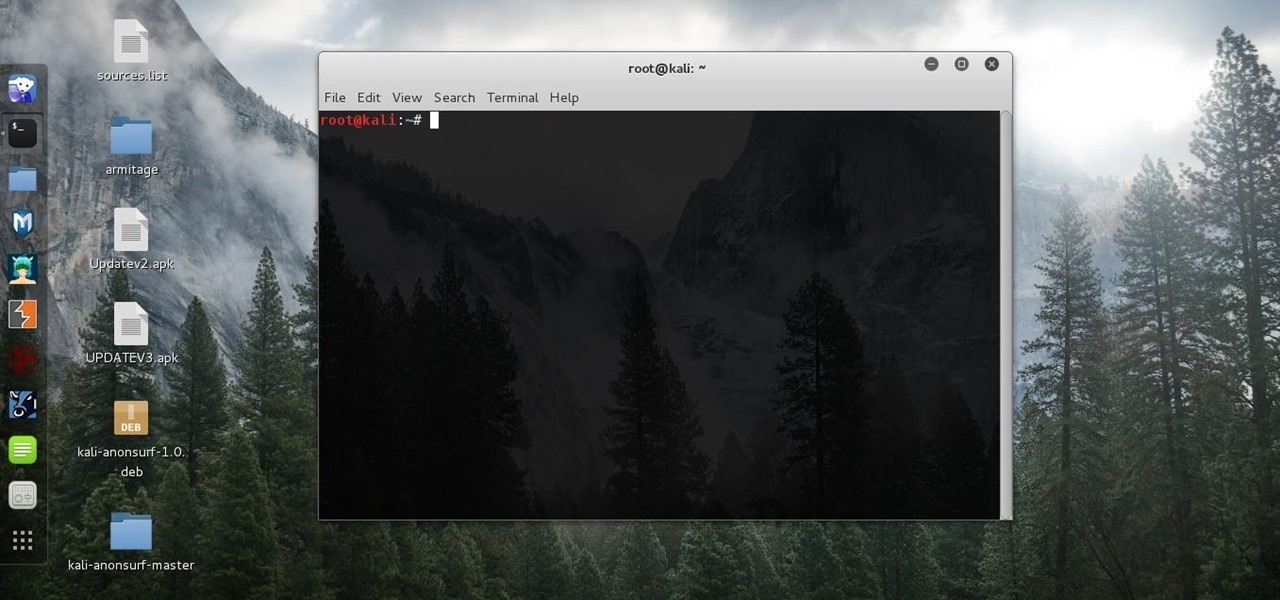
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Augmented reality optics maker WaveOptics has just infused its operations with a fresh round of funding to facilitate its objective of bringing consumer-grade smartglasses at a $600 price point to market in 2019.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

Based on its continued research, it appears Microsoft recognizes that the next HoloLens needs a wider field of view (FoV). Based on a recently-revealed documentation, the company's research team has found another way to accomplish that objective.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

With smartphone screens getting bigger by the generation, one-handed mode mods are becoming rather prevalent. Most of these function by shrinking the screen to a more manageable size, but this is actually kind of boring when you think about it.

This video will guide you top 10 windows shortcut key which is very useful in everyday computing. Watch the video and follow the steps to know top 10 windows shortcut key.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Macrame Owl - Decoration for keys / key ring or necklace / How to / DIY Video: .

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Video: . In this tutorial I show you how to get a perfect Chroma Key using After Effects.

It has happened to everyone at one time or another, but if you work in an environment with cars, it may happen much more often.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

"After driving onto frozen river, man locks keys in car, engine melts ice." - Detroit Free Press. Avoid such a fate.

If you're new to Google+ and want to know how photos that are uploaded by Google+ users can be browsed or viewed, take a look at this tutorial. You can use the arrow keys to navigate the Google+ photo galleries, or simply click on the photos at the bottom of the lightbox.

What better way to enjoy the beauty of the blocky world of Minecraft than by flying across the land? If you want to fly in the new release of Minecraft 1.8, take a look at this tutorial on how to download and install the Fly Mod, a part of Zombe's mod pack, with the help of MC Patcher HD. The guide will also inform you on how to bind keys to the different flying controls.

Marvel vs. Capcom 3 is a frenetic modern fighting game, and learning how the combo system works and being able to apply that knowledge on the fly is the key to arcade success in the game. This video will teach you how the combo mechanics in MvC3 work and how you can use them to come up with new combos on the fly and beat any character, as any character, any time.

The Recon character class in Battlefield Bad Company 2: Vietnam is a thinly veiled sniper, and utilizing their target-spotting functionality is key to effective sniping in this game. This video is a complete guide to effective Recon play, teaching you about all your abilities, guns, and how you can spot targets to make yourself much more effective from much further away.

Measure twice cut once applies to filmmaking as well as construction or any other complex process really, and that's why preproduction is they key to actually finishing your film on time and budget. This video will help you with several preproduction tasks, including storyboarding, making a shot list, lining / timing your script, and scheduling the actual production of the film.

Nuketown has emerged as one of the most popular multiplayer maps in Call of Duty Black Ops, so knowing it is key to ranking up fast in the game. Watch this video for an inside-and-out guide to the map and way to get more kill in it while playing Deathmatch.

Once you've unlocked Dead Ops Arcade in Call of Duty: Black Ops on the Xbox 360 (and PC), you can start earning some more achievements, and this video will show you how to get the "Easy Rhino" achievement. The key to earning this one is to NOT kill any of the zombies until they're in a large group, then point at them and press the Right Trigger (RT) to burst and that's it.

As a beginner in pool, learning basic breaks are key to increasing your skills! One of them is a nine ball break. Understanding this break is the beginning to other tactics! In this video you will get a full tutorial on how to approach a nine ball break properly!

Practice is the key to success in any sport, and tennis is no different. If your forehand is lacking in power, accuracy, or consistency, watch this video to learn about some easy drills you can perform to improve your forehand shots.

The key to a good standing backflip is looking confident and feeling loose. If you're rigid, it will look sloppy and force, but if you're loosened up and feeling comfortable, it will be the best backflip ever. Superstar gymnast Andrea Catozzi shows you how he performs an acrobatic backflip from standing. This is a high aerial backflip, so be careful.

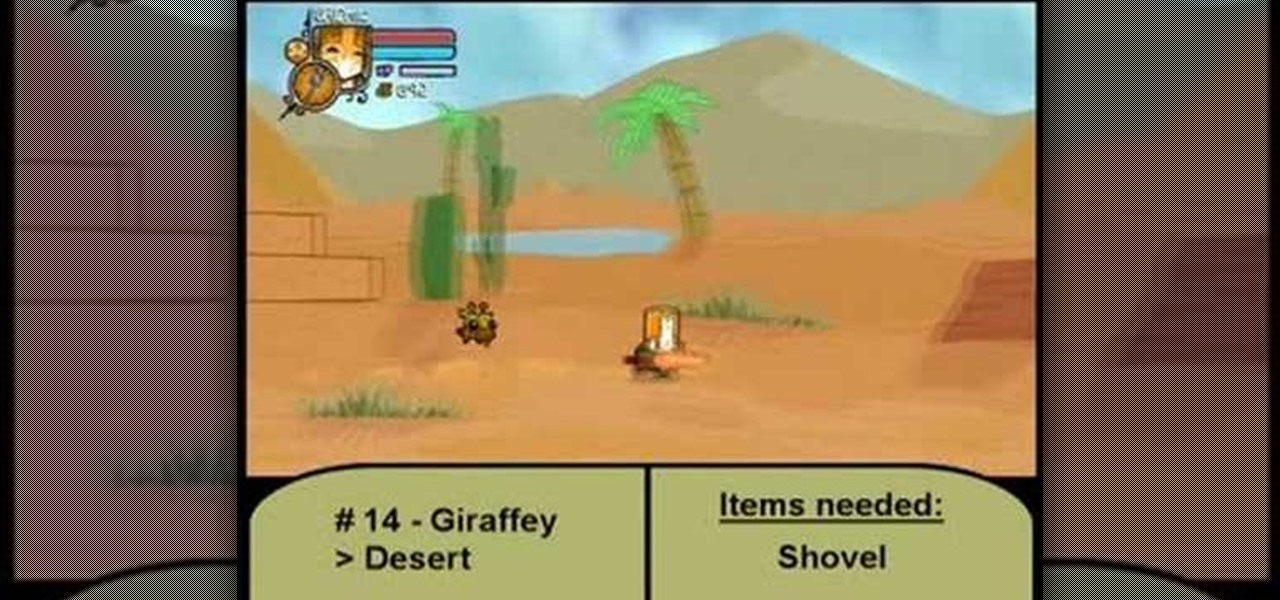
For all you achievement hunters, getting absolutely everything is key, and some of the pets in Castle Crashers are hard to find if you don't know where you're going. Let this video show you the way! It'll give the locations, and items needed, of all 26 animals that you will need to get the "Animal Handler" achievement and a cool 20G!

Having a successful rushing attack is the key to good offense both in real football and virtual. If you play Madden NFL 11 and are having trouble running the ball, this video will give you all sorts of great tips and tricks to help you out getting your offense moving and scoring touchdowns.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.