
How To: Boot Windows XP from a CD
The following are the steps to be followed to boot Windows XP from a CD: 1. The first thing to do is switch on your computer. Before your computer starts loading windows, you need to hit the F12 key.


The following are the steps to be followed to boot Windows XP from a CD: 1. The first thing to do is switch on your computer. Before your computer starts loading windows, you need to hit the F12 key.

First make sure that you have a boot able disc and insert it to your optical drive. Shut down your PC And start it up again making sure to press the special key to enter the setup dialog. Go to the boot sequence and select the CD ROM as the first bot device as shown. Save the settings and exit the setup console. Wait for the PC to boot up and during the loading hit any key to boot from the CD.

Do you know how to cook beef short ribs? How about a point off natural brisket? In this video, Andrew Zimmerman, offers simple and easy recommendations on his favorite methods of preparing and cooking various cuts of steak. Zimmerman lets you know what kinds of steak work best with a sweet marinade or a saltier one. He also lets you know about different methods of cooking steaks such as pan frying, grilling, and even poaching. Zimmerman's key to a perfect steak, however, is its rest time. He ...

This video tutorial from TutVid shows how to create a simple movie poster text effect in Adobe Photoshop CS4.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Are you thinking about upgrading your iPhone this year? Apple sure wants you to. Of course, that's no different than any other year, but Apple really wants you to upgrade this year. How do we know this? The rumors point to not three, not four, but five brand new iPhones in 2020, with two very different release schedules. All this begs the question what the hell is Apple thinking?
If you've been paying attention to the smartphone industry, you've certainly noticed a rise in dark mode lately. With most phones now sporting OLED panels, which use less power to display darker colors, users have been begging developers to include a dark theme in their apps. Lately, Google has been happy to oblige.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.
When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

The future of forests looks dreary in the face of a warming climate, but scientists are exploring the relationship between soil microbes and the ability of trees to move to higher altitudes, a key component of their survival.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.
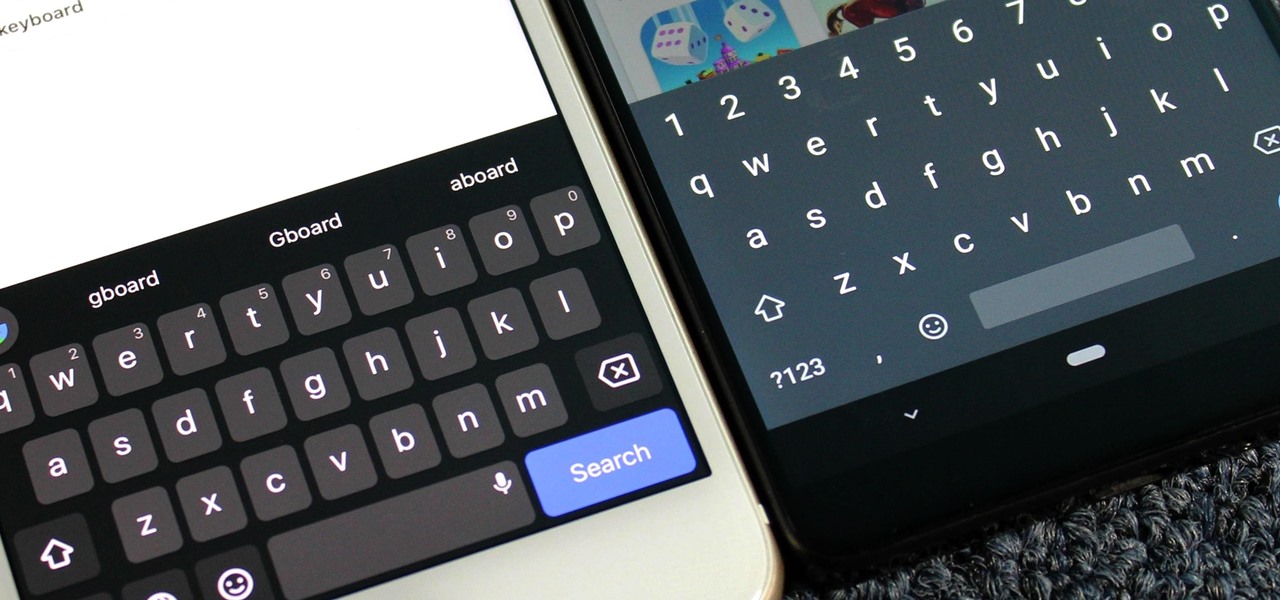
One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

Compressor 3 is part of the Final Cut Studio package and sports a brand new interface. So if you're new to the software, or haven't played with the newest version, you're sure to learn some good hot keys and interface tips.
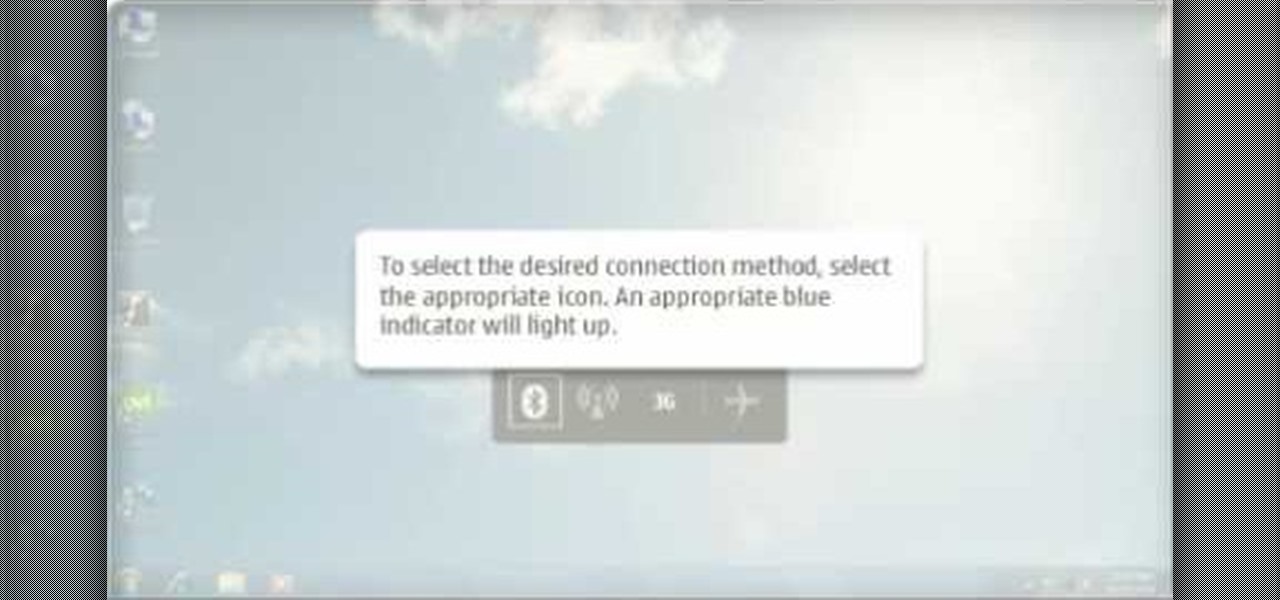
If you hit the FN + F10 keys on your Nokia Booklet 3G, you'll see the available internet connections methods for your netbook including Bluetooth, wifi, and 3G.

Grab a thin tension wrench and a thicker tension wrench, combine them with your favorite pick, and you'll be ready to unlock that 700 series American Lock that you, or someone you know has lost the key to.
The key to building a great Minecraft world is efficiency. This video will show you the most efficient way to kill mobs, a four-way mobvator that attracts mobs to spawning pads and elevates them to a killing mechanism so you can capture the loot. This is up to date for Minecraft beta 1.6.

Check out this video to learn how to get the Wunderwaffe in Call of the Dead, the zombie map from the COD: Black Ops Escalation map pack. Whether you play on Xbox 360, PS3, or PC, this video has the key to picking up the Wunderwaffe, one of the best guns in the game.

Are you playing Minecraft on a Mac? Would you like more functions and better performance from chat? Check out this video, you'll need to download Modloader and improved chat. You'll be able to bind keys, so that your most used commands are only a single keystroke away!

Live in a place with severe winter? You may eventually find that your car door lock has frozen solid. You can try jiggling the door handle, but if that doesn't work, then bring out a butane lighter and heat up your car key. Take care to not get burned!

The key to getting a perfect synchronization on this level is being able to complete it in less than eight minutes. This video shows you a walkthrough for this level so you can complete the entire thing in the time allotted.
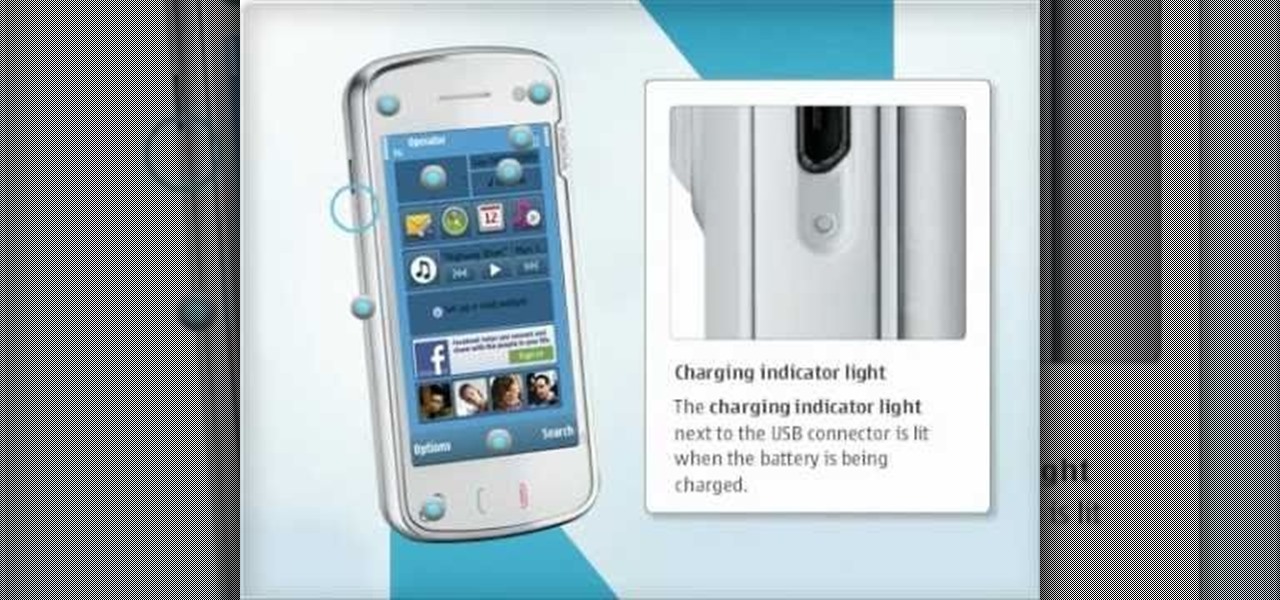
Get familiar with the keys and parts of the Nokia N97, and with the elements on the home screen. It's an easy process. And this clip will teach you everything you need to know. For all of the details, including complete, step-by-step instructions, watch this brief, official N97 owner's guide from the folks at Nokia!

Beware of large rooms! The key to defeating the first boss in Dead Space 2 is to shoot the yellow markers on its arms. As long as your aim is good, you'll defeat it easily. Also learn more about Isaac's lack of memory.
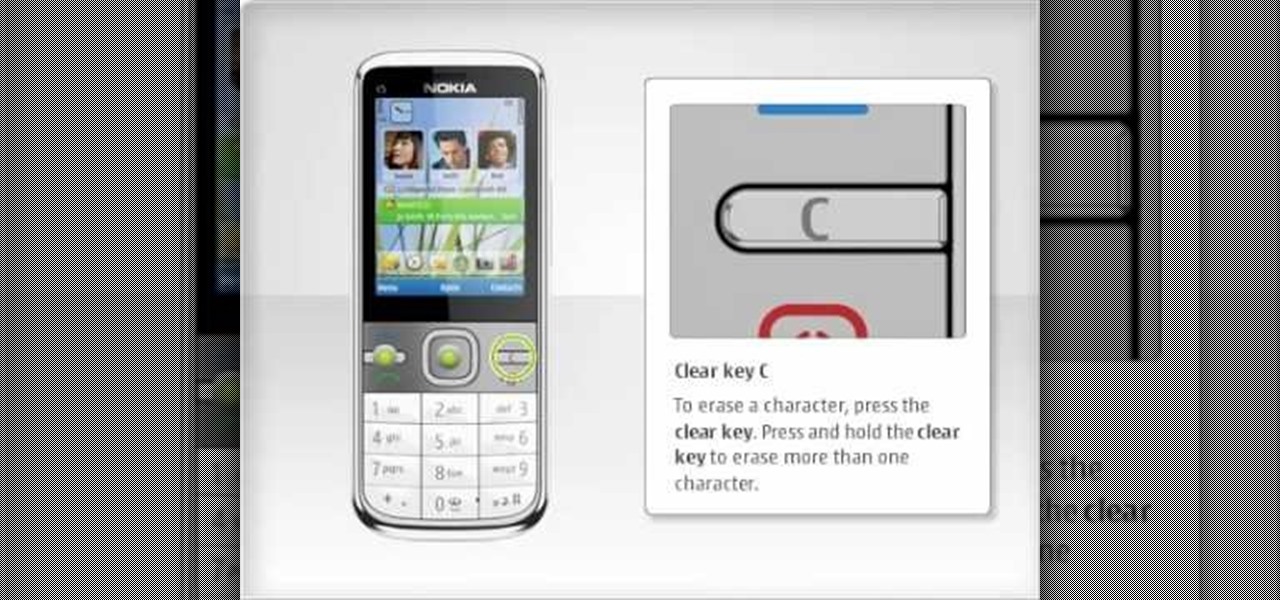
In this clip, we learn how to use the Nokia C5's various buttons and ports. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

The key to being a good PvP (player vs player, or player versus player) character in World of Warcraft boils down to one thing: resilience. Here is how to be a good PvPer in WoW without turning into a griefer.
Even if you're just a new player, or a casual player, you can still earn this achievement. It's one of the first achievements in the Shadowfang Keep heroic on World of Warcraft. The key is in having a spare tank in your party.
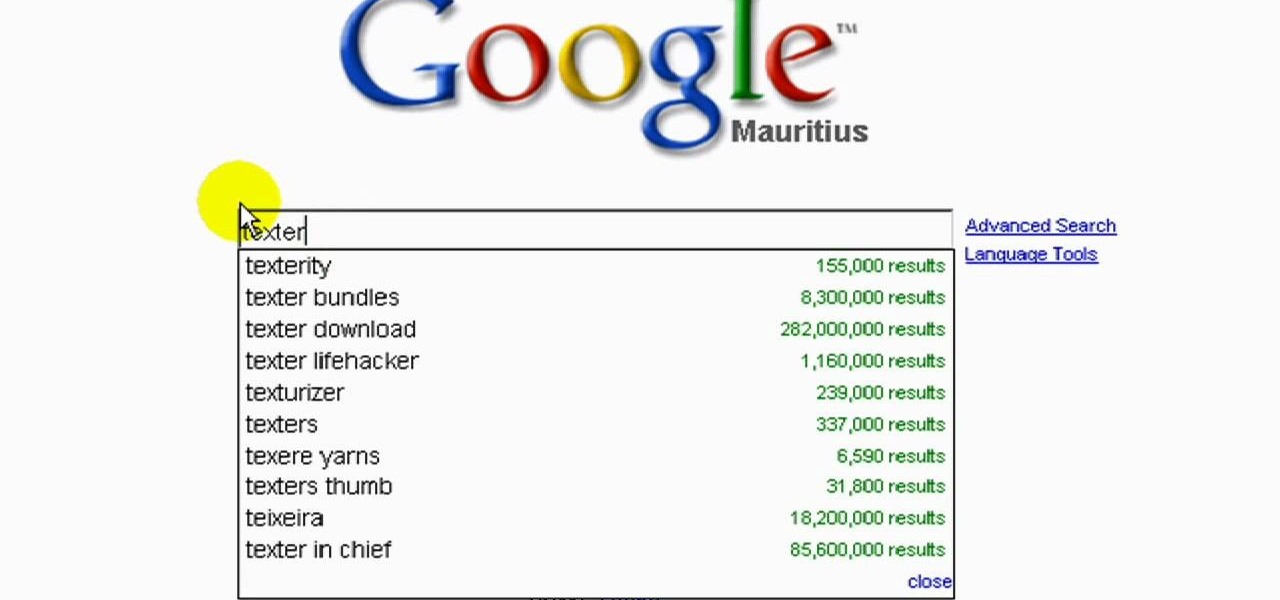
Speed is essential to being a successful programmer, and this tutorial shows you how you can easily and quickly double your coding output. The key is in a program called Texter, which you can easily download and install completely for free.

This tutorial shows you how to do two basic macrame ties, which you can use to make keychains, bracelets, chokers and other types of jewelry. Add beads, charms and other decorations to your projects - macrame is cheap, easy and fun!
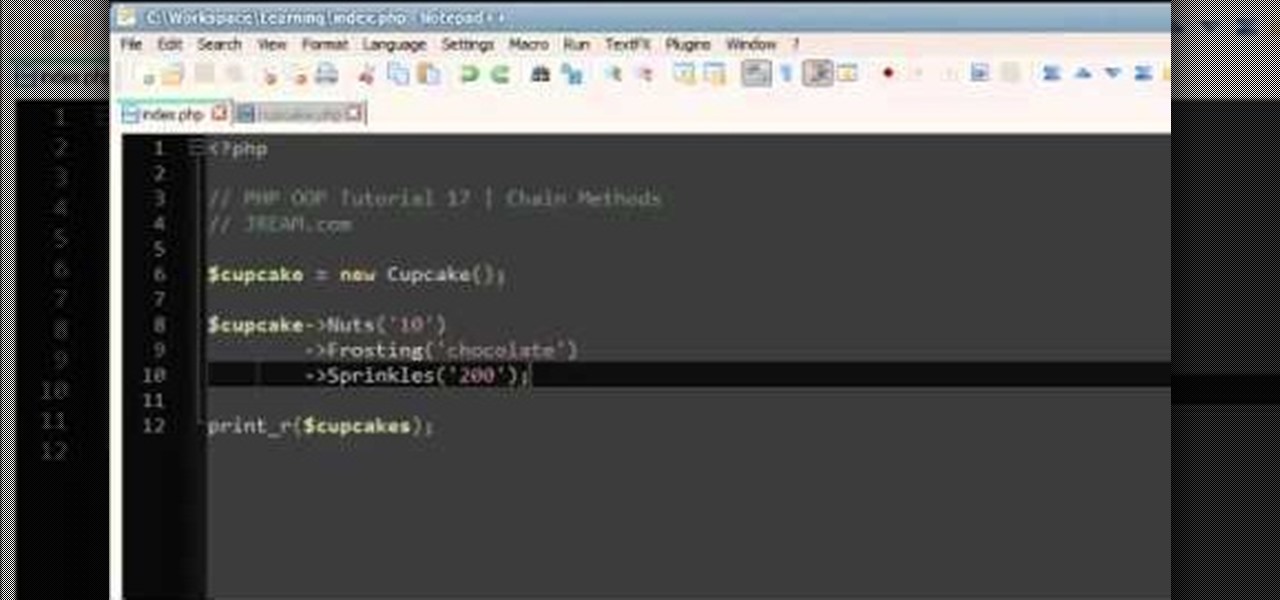
Chaining methods in PHP can be simple and straightforward if you follow along with this informative video tutorial on PHP OOP methods from JREAMdesign. The key action is to return the object after running the function so that you can run another function to the object directly afterwards.
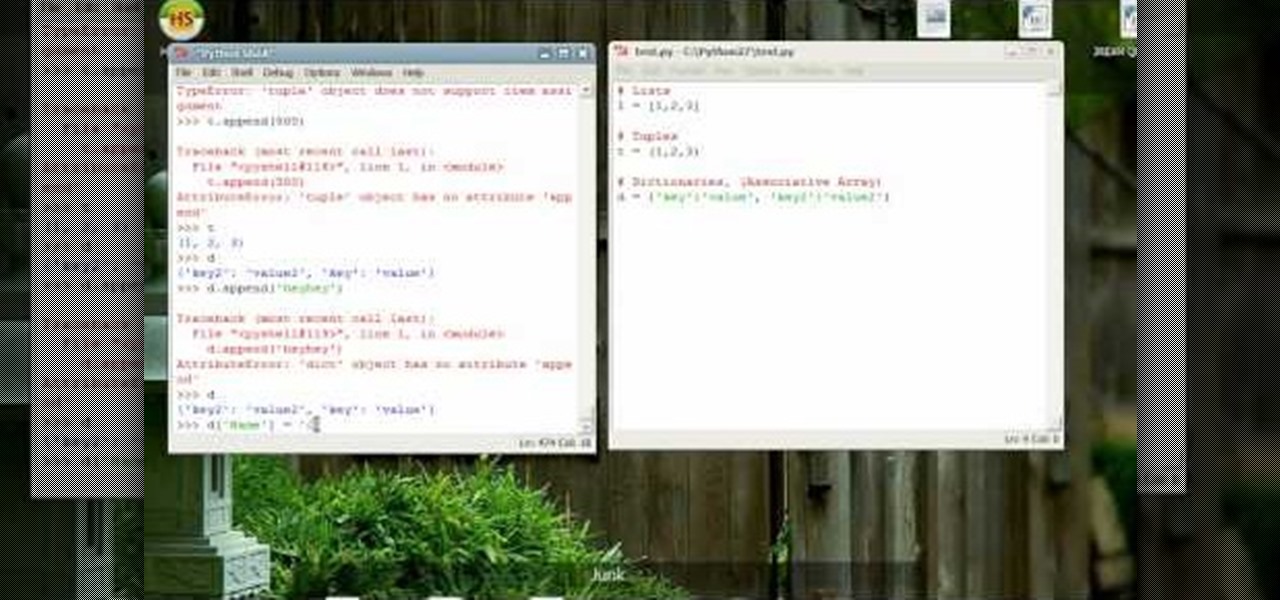
A tuple's value cannot be changed at all within your Python-based program, whereas a dictionary is more like an associative array where every item has a key and a value. Here is how you can use both tuples and dictionaries within your Python program.