This tutorial series shows you how to put up an Adobe Air Flex 3 Encryption System. One of the weak points of Adobe AIR and Flex is there is no encryption system built in, making your data and applications vulnerable. But that's ok, because this tutorial will show you how to remedy the problem by adding an AES encryption system.

Want to learn the principles beyond Boyle's Law in a way other than just hitting the books and getting bored to death? Then a science experiment is key.

In this Super Smash Bros Brawl (SSBB) for the Nintendo Wii video, I showcase how Pit and Metaknight work, including their move properties and what I believe will be key strategies to learn with them in the long run. I came into this video with a plan, written on paper, so I showcase practically everything about these characters!

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

If you've just finished your paint job on your vehicle, then you're not done yet— you still have to clean up, and making sure the paint gun you used is properly cleaned is the key to successful future spray painting. This video shows you how use clean the spray gun with a paint gun washer.

Did you know that you can zoom in on your Mac laptop just as easily as you can on the iPhone? All you need is your fingers, your mouse and to activate the zoom function on your computer. Check it out!

Why type everything twice? If you don't know how to copy and paste you are missing out on an incredible time saver. Check out this tutorial and learn how to speed up your work.

Hello! My name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss the game can you read my mind. This game has a little bit of mystery flavor to it. You'll see what I mean. In this game, you need to utilize 2 rooms. In the first main room, you have all the guests of your party. Then later we'll instruct the guests we're going to play a game called can you read my mind and the goal...

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

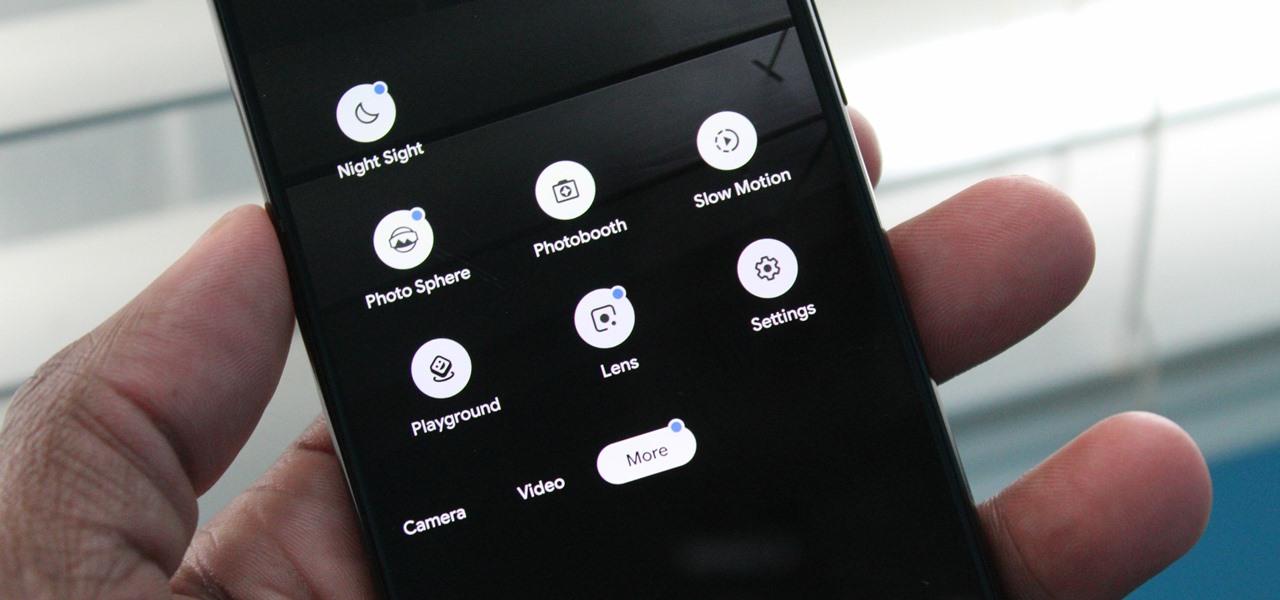
Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Now that we finally have vertical plane recognition in ARKit (at least on a developer level until the spring iOS 11.3 release), the real promise of mobile augmented reality is beginning to come into focus on iOS. But a new report indicates that a major near future advancement of ARKit that could change everything has been put on hold by Apple.

Scary movies seem to be a natural fit for augmented reality experiences, with the latest example coming from the Insidious film franchise.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

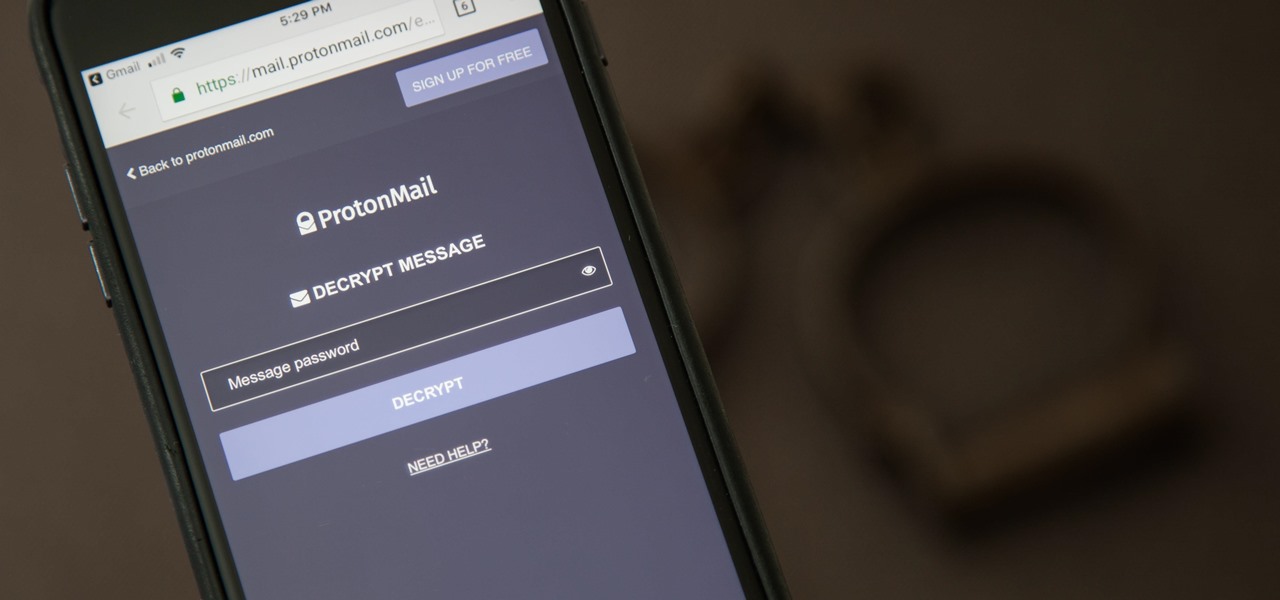
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

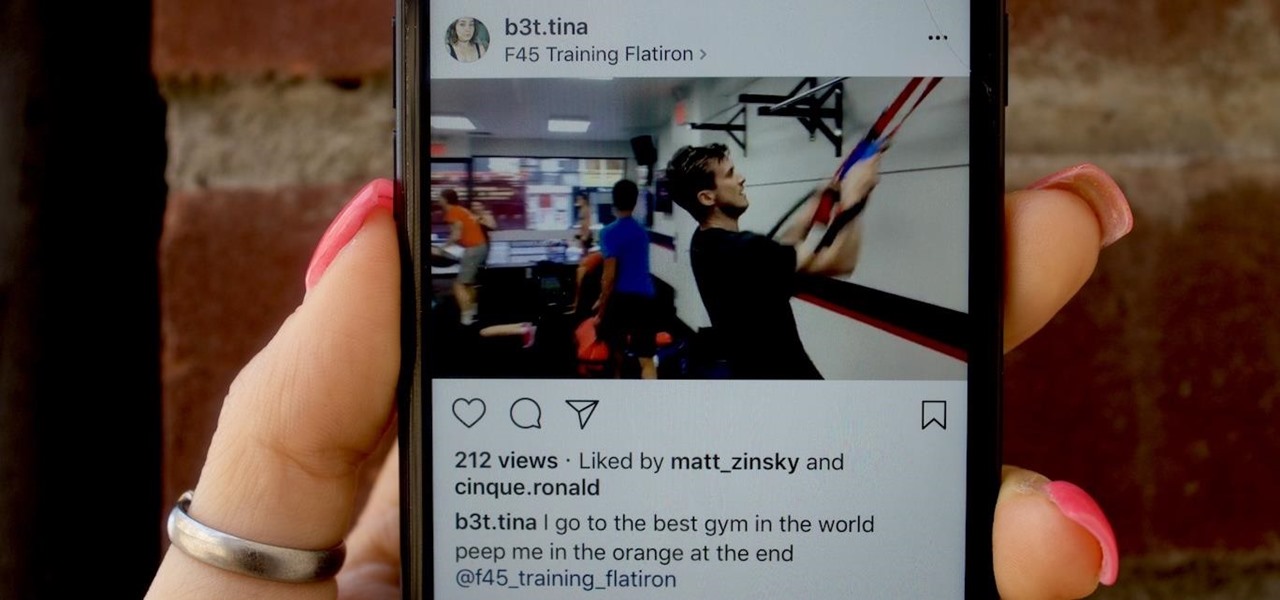
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

With many of the companies working in augmented and mixed reality focused on the Augmented World Expo, the finance side of the industry has been relatively quiet.

Are you looking for a little microbe magic? Think composting. Composting is a great way to reuse food and plant waste that you would otherwise throw into the trash, which would just end up in a landfill somewhere. During the composting cycle, microbes reduce this organic waste until it can be fed back into the soil as rich, crumbly compost. When returned to the soil, compost feeds plants and improves the nature of life underground. Sound like a great idea? It is — and it's easy.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Augmented reality could come in very handy for those of us prone to losing things—namely, our wallets. Pixie Technology, a company from Los Altos, California, has developed a way to locate your lost wallet and keys using AR technology and tracking chips, a platform they call the "Location of Things."

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

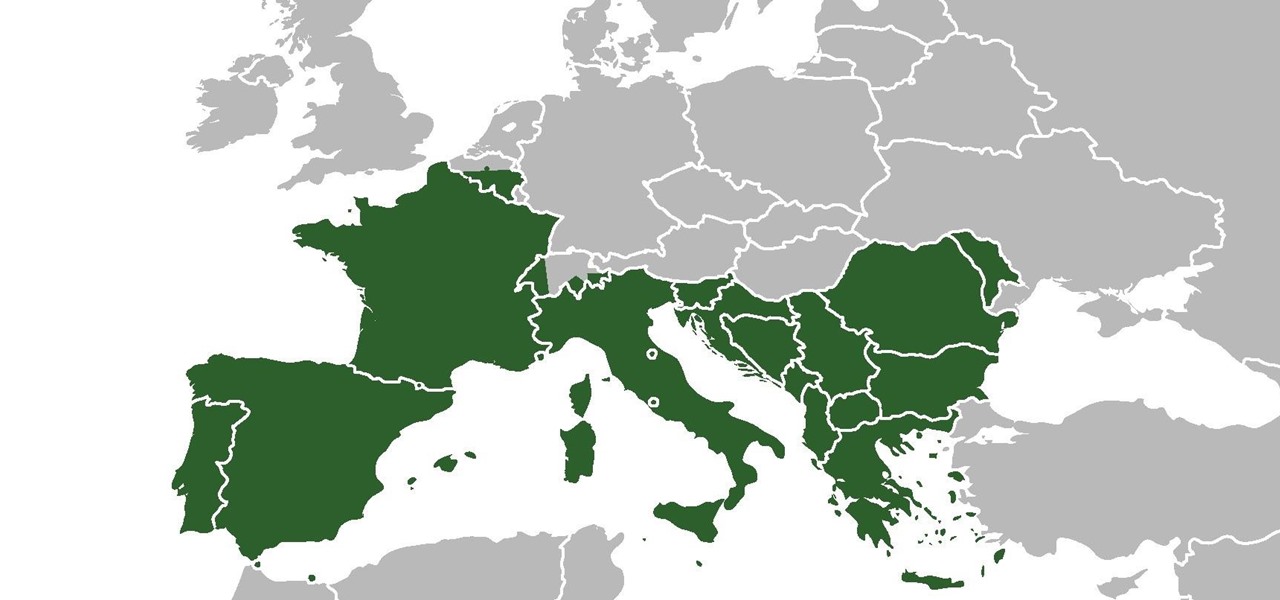
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

I had the opportunity to speak with the COO of Osterhout Design Group, Pete Jameson, shortly before the announcement of the company's R-8 and R-9 smartglasses models at CES in January. And while I sadly could not make it to CES to test the smart specs out right away, ODG invited me to do just that while I was in San Francisco for the Game Developers Conference.

With the death of Google's Nexus line, the market for phones with top-notch specs at midrange prices is now wide open. OnePlus is apparently ready to fill this void, as they've just announced the OnePlus 3T, an iterative update to their OnePlus 3 flagship only five months after initial release.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

You've likely seen light-up musical keyboards that teach you how to play a song with visual cues, but few of those devices exist and have a limited number of songs you can actually learn. But Karl Baumann and his HoloLens Hackathon team figured out that in mixed reality, you can learn music with visual cues with any piano.

It looks like Apple is finally going to do something to address all of the complaints about their unremovable stock apps clogging up people's home screens. While bloatware is a bigger problem on Android where you have to deal with apps from Google and carriers, an iPhone can still get pretty cluttered with all those stock Apple apps. I mean, just look at all this crap... AppAdvice noticed two new keys in the iTunes metadata that strongly suggest that you'll be able to get rid of stock apps on...
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.