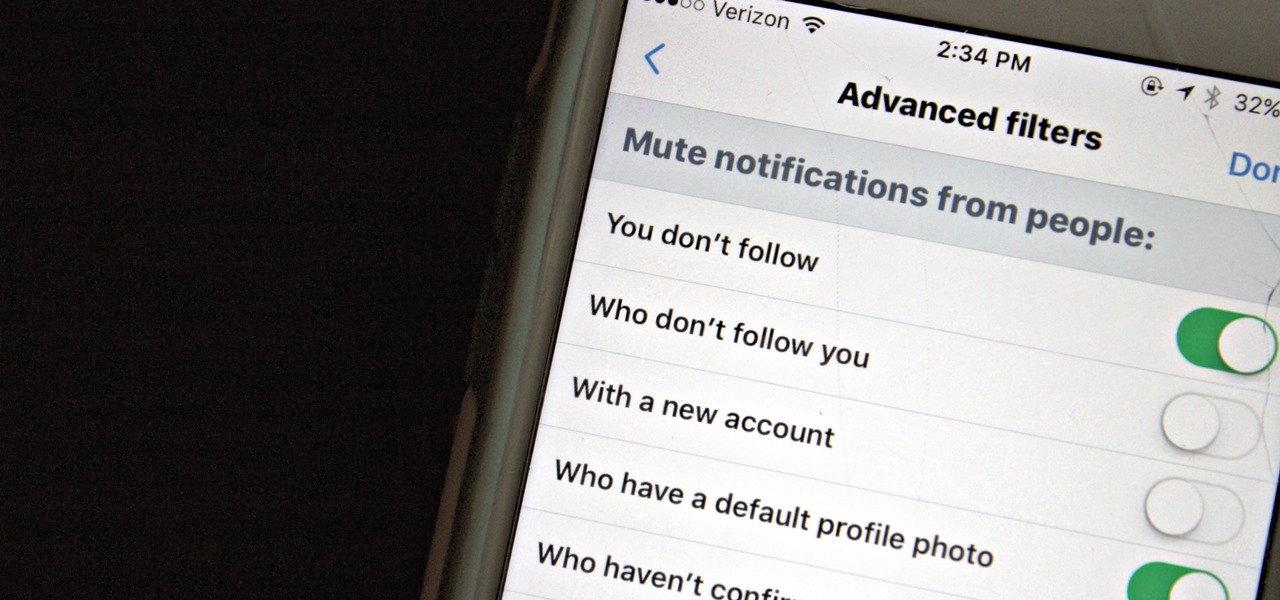
Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

If you know that ticks spread Lyme disease, you may already know you might also catch a bunch of other infections from them. One of the lesser-known diseases spread by ticks is infection with the bacterium Anaplasma phagocytophilium, called anaplasmosis.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

A dangerous bacterial disease is infecting dogs in northern New Jersey, forcing owners to keep their pets inside.

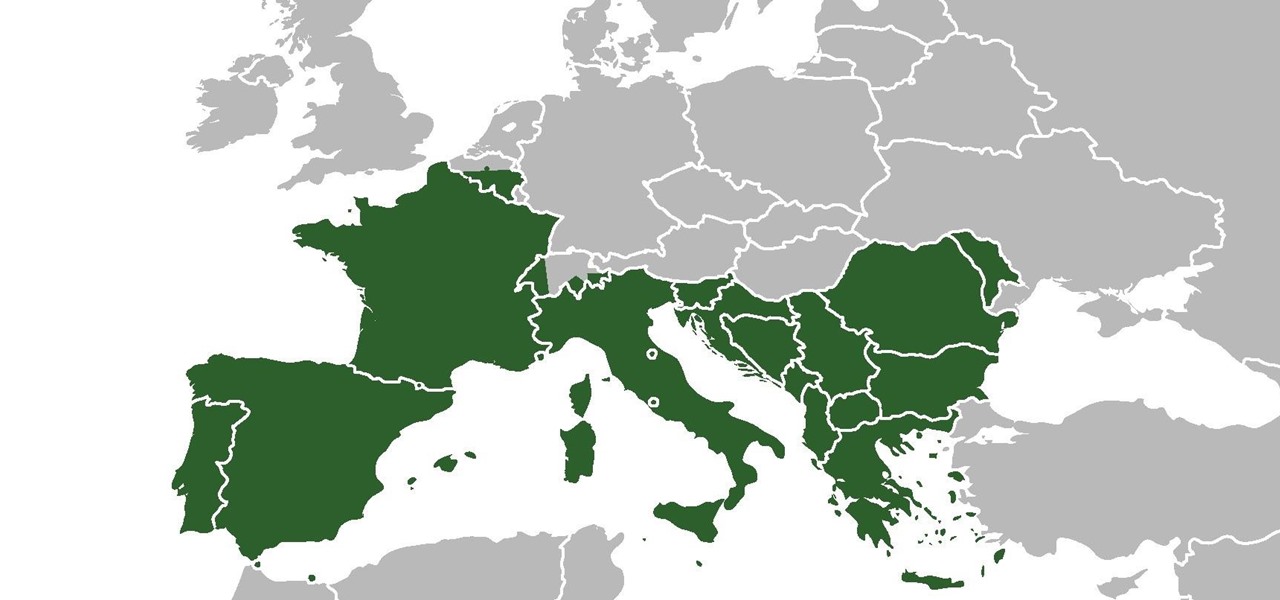
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

In the past, infection with human immunodeficiency virus (HIV) commonly led to dementia as the virus made its way to the brain. Even in effectively treated people, HIV can hide out and replicate in places like the brain, where it's tough to detect. That's why it's very concerning that half of all HIV-infected patients still report cognitive problems.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

Lenovo, the company that now owns Motorola, just announced two new entries in their wildly successful midrange Moto G series. The Moto G5, and its bigger brother, the Moto G5 Plus, were both shown off in detail at Mobile World Congress 2017 in Barcelona, Spain.

The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

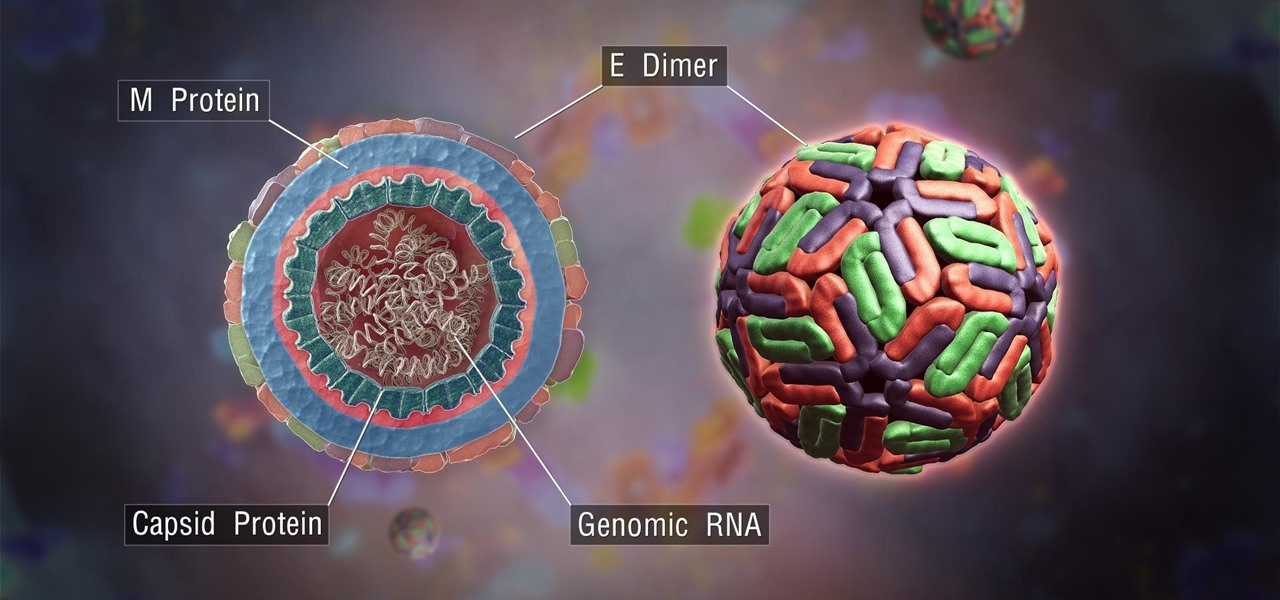
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

Video: . This video will show you how to secure your kayak to a J bar roof rack carrier.

Many people who use braided line complain that it gets wind knots which may have to be cut off and expensive line discarded. Almost all "wind knots" have nothing to do with the wind and are caused by user error. This video explains how to avoid those knots and start taking advantage of braided fishing line.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Samsung's Galaxy series of devices have one common design theme that ties them all together—the physical home button at the bottom of the phone. This button can wake the phone, take you to your home screen, and even scan your fingerprint to securely unlock your device.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

If you need to control a software like Ableton Live while you play guitar then you need a foot switch. In that video I will show you how it is easy to build a foot switch with an old keyboard. Then you will need to configure your software to map the keys to specifics functions like Play, Next, Pause, etc. Enjoy !

Beautiful Macrame Bracelet. This video tutorial is intended for people who know a little bit about macrame :)

Hi again! :) Many people have been asking me to do a lesson about what to say when you visit the doctor in Lebanon, so here's that lesson. So if you're sick, I hope you get well, and I hope you enjoy this lesson and find it useful.

How to make a Macrame Lagoon Earrings. A good accessory to wear everyday and for any occasion. (This video tutorial is intended for people who know a little bit about macrame)..

If you're still looking for that perfect prank to pull off on people on April 1st, here are 5 simple yet funny practical jokes you can get your friends and family with. Most require household items which you should already have, so you won't need to go out and purchase any additional stuff. Check out the video tutorial to start pranking right away!

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.