How To: Create an account and avatar on IMVU
If you're looking to try your hand at a virtual existence, IMVU is the world to go to. Start out by creating your very first account on IMVU. See about building your avatar.

If you're looking to try your hand at a virtual existence, IMVU is the world to go to. Start out by creating your very first account on IMVU. See about building your avatar.

A math story problem in which you seem to come up a dollar short in the solution...but not really. Here's the trick with an explanation.

Carved wood figures always present an aura of mystery. From the fearsome tribal masks of Africa to the towering totems of British Columbia, indigenous peoples have long created wooden guardians to channel their spirits and protect their peoples. Puppets can even move like us, mock us, or in the case of Pinocchio, come alive. Be careful wood carvers, for in your hands you possess the power of the gods, the power to create, the power to give life, and hopefully the power to make a cool sculptur...
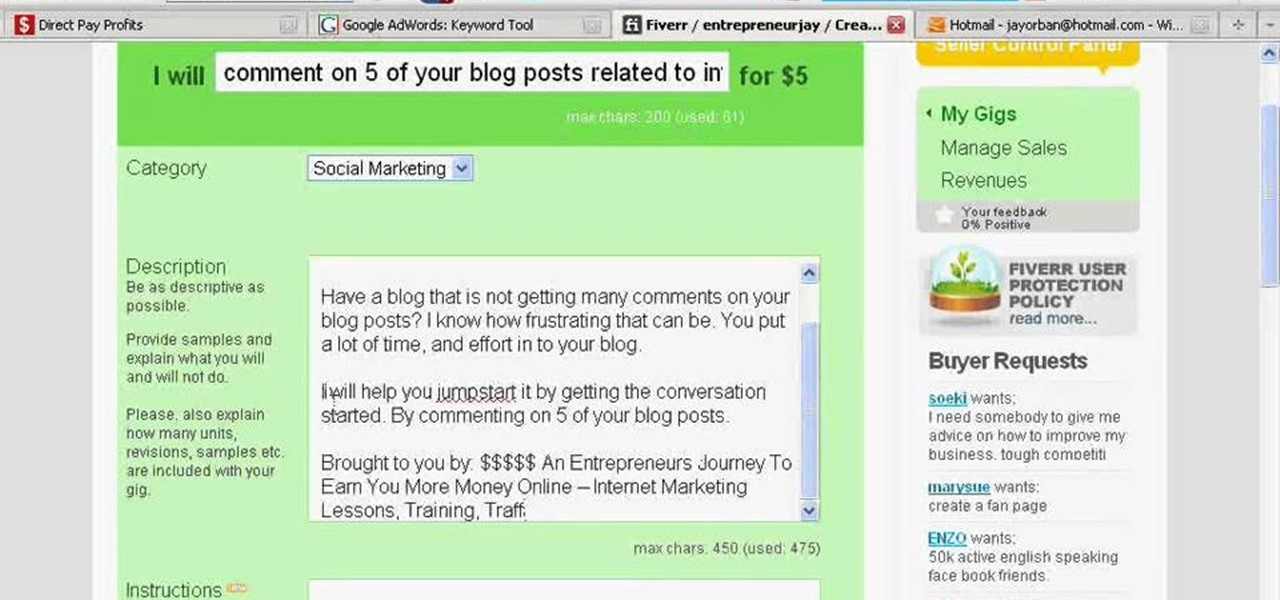
Fiverr.com is a website that allows people to offer different services for $5. If you are interested in making some of your unique skills or talents available online for $5, this video explains how to take advantage of Fiverr.com and start earning money online.

In this video tutorial, viewers learn how to lose belly fat without having to do crunches. The exercises provided in this video are: push-ups, squats and dumbbell squat raises. These exercise don't just work on the abdominal muscles. It is recommended to do each exercise until failure. These exercises use the abdominal muscles as stabilizers. The key to losing fat is to push yourself hard to do the exercise. Abdominal muscles are not designed to flex. Crunches do not help lose belly fat. This...

On the 2010 Lincoln Navigator there's a handy feature called the deployable running boards, which are essentially step bars that automatically deploy when the car door is opened, to help you step inside your vehicle. This video demonstrates how they work, and how you can shut them on or off, because not everybody will find these useful — tall people definitely won't.

Imagine, never needing to unlock your car door with a key. Actually, it's been around for a while, and it's called keyless remote entry, but on the 2010 Lincoln MKS, it's not remote… it's built directly into the side of the car door. It's a number pad with a programmable security code. This video will show you how to unlock your vehicle without even reaching into your pocket! If you have a MKS.

This will hack speed on Typing Maniac. Sometimes slowing down the process is the only way you'll win. If that's the case, then use Cheat Engine to slow down time and become the ultimate typer.

This is just a quick video to help you replace your iRiver Digital MP3 Player's battery. Patience is key in completing this disassembly and replacement, using just a small screwdriver and a few minutes of your time. This step-by-step video demonstration will show you the procedure for replacing the battery in your iRiver H320 or H340. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

Cheat your way to the top of Typing Maniac with Cheat Engine. Cheat Engine solves all of your playing woes by doing all of the work for you.

With the growing popularity of buying local, many people are rediscovering the benefits of preserving fruit at home. Concerns over food origin, additives and preservatives are driving this trend and in just 20 minutes you can enjoy fresh produce all year long. Watch this how to video to learn more about picking fresh food and the preservation process.

Some people may think that vegan and vegetarians do not eat protein. This how to video is an informative episode about protein, some easy protein snacks, and a comparison between ground beef and textured vegetable protein. Watch and learn how to get protein into your diet when you are a vegan or vegetarian.

Dr. Benjamin Weeks explains how vitamin C plays a role in the central nervous system health, especially in elderly people, and how it relates to Parkinson's Disease.

The sensory input of our environment may strongly affect our emotions, if we let it. The senses can be used in a positive way, by creating an agreeable, uplifting atmosphere, which is a lot more important than people often think.

The breakdown - 5 cool new channels without too many new subscribers. What's the best way to expose them to more people?

Many people have seen backflip tutorials, but some might be unsure of how to move their arms while flipping. This video will teach you how to move your arms properly while doing a backflip.

Do you suffer from a lack of little origami people in your life? This origami demonstrational video will show you how you can fold your own sumo wrestler.

Dr. Parris Kidd explains how the dietary supplement GPC (GlyceroPhosphoCholine) can benefit the brain health of people of all ages, from children to adults. It can also help those recovering from brain damage.

Learn how to use a site: http://www.copyscape.com to check if people are stealing content from your website.

This Premiere tutorial shows you how to make cool voices for people in your videos - Star Wars voices and more.
Need a hair lift in IMVU? No problem, get some bad hair day advice with this vid. You just need a little Photoshop skills to get your IMVU avatar looking good.

People always want to know the difference between cherry pitters and olive pitters. This how to video should help a bit. Yes, a cherry pitter will pit olives--if you're careful. But if you want to do a bunch of olives fast, the olive pitter is much easier to use. An olive pitter will not, however, pit cherries--they usually smoosh them.

If you want to see what it really looks like to make rice crispy treats with regular people and people in the kitchen just like you probably have then this video will do just that. RKTs are easy to make but can be a little tricky if you don’t know where you keep the pans.

This tutorial will show how to use GPG and the FireGPG plug-in to encrypt and decrypt messages in Gmail. GPG is an open source implementation of OpenPGP (Pretty Good Privacy) , a public-key-encryption system. With public key encryption you don?t have to give away the secret key that decrypts data for people to be able to send you messages. All senders need is the public key which can only be used to encrypt, this way the secret key never has to be sent across unsecured channels. Encrypt Gmail...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Attention cheapskates and locksmith apprentices, this key copying solution is stunningly simple. We've really mulled over this one. As you can read in the comments below, people struggle with executing this successfully. But it can and will work. You just have to modify your key to fit your needs.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

Apple got rid of the iPhone's home button and assigned its long-press action (Siri) to the power button. Since it now did more than sleep and wake the screen and bring up the power off dialog, they renamed it the "Side button." Well, Samsung just removed the Bixby key, and they're taking the same approach.

Put simply, SEO = more organic traffic. And more traffic is always good for a web page / website (unless of course, you are an underground drug-dealer selling drugs worldwide via a spooky website whose URLs are as search engine unfriendly as possible, so that no one accidentally discovers your page and informs the police, sending to heaven both an exciting career opportunity and the likely Al Capone's successor).

Google+ launched their API for public data today. For now it provides read-only access to public data in the form of People & Activities. Here are some links to get you started:

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

The biggest struggle with flashing DVD drives on Xbox 360s has been the price tag of the probe to extract keys on some drives. The probe and kit is required to extract the DVD key, which is needed to perform a drive repair, flash, or backup of any kind. Who wants to pay big bucks for the "pro" kit and then get added to a huge waiting list behind a million other people looking to buy the same product? We can hack the same thing together at home!

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

One of the most exciting new features announced by Google+ was the ability to broadcast hangouts live via YouTube, which was recently demonstrated with the very first Google+ Hangout On Air with +will.i.am of the Black Eyes Peas.

Sound Keys is a keyframe generator plug-in for Adobe After Effects. Learn how to visually select parts of an audio track and convert that audio into keyframes. TrapCode Sound Keys After Effects plugin is great for audio-intensive animations. See how to use it in this tutorial. Use Trapcode Sound Keys After Effects plugin.
Learn how to use the SpectraMatte Key Effect in Avid Media Composer Adrenaline HD and Avid Symphony Nitris to adjust and fine-tune color keys and and eliminate shadows and color spill. This can also be used to create green screen effects. Use the SpectraMatte Key Effect in Avid.

In this After Effects tutorial, Creative Cow leader Aharon Rabinowitz shows you how to be an AE road warrior by changing the keyboard shortcuts to account for missing keys on a laptop - such as the Ram Preview key or the Audio Preview key. Learn to customize your shortcuts in After Effects and improve your workflow. Change shortcuts in After Effects.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Take a look around the next time you open up the File menu and slowly scroll through your editing options. Are your coworkers quietly cringing? Your kids running for the other room? Sounds like you need a few good keyboard shortcuts up your sleeve. Memorizing the right combos can transform you into a super speedy Windows superstar. Forget the mouse. Keyboard shortcuts are the new black.

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.