It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.
When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

Learn how to change a flat tire. Many people belong to a roadside-assistance service, but if you're stuck in a remote area, you'll want to know what to do. You will need:
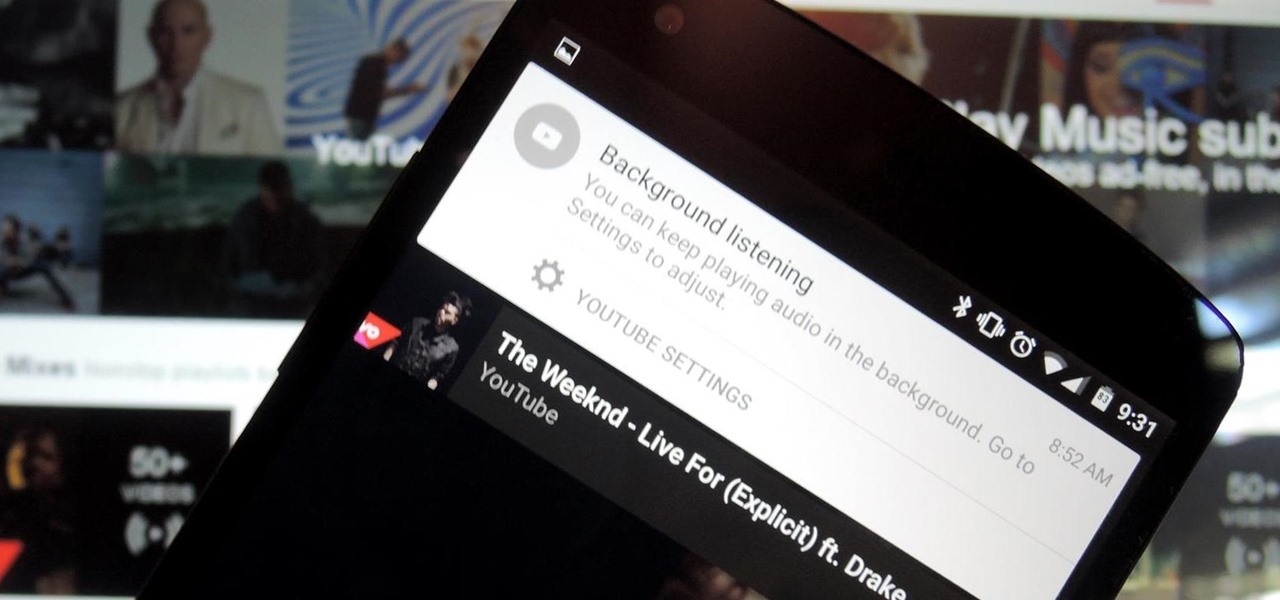
We recently showed you YouTube's new music streaming service, YouTube Music Key, with it's promise of ad-free music complete with background listening and offline play. Well, if you check your YouTube app, there's a good chance that Google flipped on the service for you. Activate the Service

Mac keyboards are great when listening to music or watching a movie, since you can control what's playing without going back into iTunes or QuickTime Player. However, when you're using an app like Photoshop that uses the F7, F8, and F9 as shortcuts, it gets pretty annoying to have to hold down the Fn key. Why can't you just hit the back, play/pause, and skip buttons alone?

Android apps check your system locale settings to determine which language they should display. For the most part, it's a seamless experience—except for those times when an app has not been translated into your language of choice, in which case the app will usually default to English.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

The primary purpose of hot keys in StarCraft 2: Wings of Liberty, is so that you can control the command card in the bottom-right portion of your screen, without using a computer mouse. But the hot keys have other uses, too. The first video covers the basics, and the second video covers using these shortcuts to building control groups. The third video shows you the other remaining hotkeys available for StarCraft 2.

In this clip, learn how to use the Swype Key while texting with Swype on your cell phone. The Swype key is where all of your options are like dictionaries, tips and tricks, help menus and everything else you may need.

One of the biggest hurdles for making touchscreen text input easy on the user has been finding a simple way to move the cursor around. With all the advancements in mobile technology, we're still left fumbling around with tiny arrow indicators or magnifying glasses when we need to add a letter to a word we've already typed. But thankfully, developer Ouadban Youssef has found a better way.

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Google debuted YouTube Music Key in November, and for $10 a month, this essentially turned YouTube into a music streaming service. With ad-free music videos and background audio playback, YouTube serves as a viable alternative to Spotify or Pandora for Music Key subscribers.

Master your tennis serve progressions. Be sure to click on all the video chapters to view the entire tutorial.

Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

In this ten-step video tutorial, you'll learn how to quickly copy keys using a camera, printer and Dremel tool. With this ten-step process you'll learn the necessary steps to copy almost any key... even if you only have access to it for a brief period of time.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

This video is specifically for the C530 Slate cell phone from AT&T, though this procedure will probably work on similar models of phone. You can hack, or jailbreak, your phone to allow you to use third party apps or switch to a different service provider. You will need a non-AT&T sim card for this hack to work (T Mobile is shown in the video). Then turn it on, hit the unlock key and then enter in your unlock code. Make sure you get it right!

Woodturning is creating items out of wood on a lathe. Learn how to create key chains and light pulls from a woodturning expert in this free crafts video series.

Samsung has the Bixby key, Pixels have the Google Assistant squeeze gesture. It's nice having a hardware button just for your assistant so you don't have to say "OK Google" or press an on-screen button. If your phone doesn't have such a shortcut, though, you can remap an existing hardware button to trigger the Google Assistant.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Mystery shopping is a great way to make money on the side while getting a chance to shop, check out new stores and restaurants, and over all improve the quality of service at these locations. The key is to not let them know that you are there evaluating them. If you think you've got a knack for blending in, then check out this video. In it you will learn the process of signing up and becoming a secret shopper, what to expect, and some tips for how to carry out your jobs.

In this video tutorial, viewers learn how to use the Sticky Keys feature in a Mac OS X computer. The Sticky Keys feature is found in the Keyboard tab in the Universal Access menu. To turn on the sticky keys, check the On option. Underneath, users are able to set some options for how the modifier keys are treated. Sticky Keys will allow users to press the keys in a sequence, instead of all at once. This video will benefit those viewers who use a Mac computer and would like to learn how to conf...

In just a few simple steps, you'll have your piano keys sparkling like new. You Will Need

Always losing your keys? A big bulky key chain might feel annoying in your pocket, but it's not likely to get lost in your purse or in all that trash you carry around. This video tutorial shows a real simple key chain ring you can make and keep those keys easy to find. All you need is the key ring, two shoelaces, a pair of scissors, and a lighter.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

The Sanctuary menu system in Fable 3 has spawned some controversy, but it's pretty novel when you consider that there are a hidden Gold Chest and Gold Key right there in your pause menu! Watch this video to learn how to unlock and find the Gold Key and then the Gold Chest in your sanctuary.

The Gold Keys in Fable 3 are needed for unlocking all sorts of fun legendary weapons and such, but finding them all is appropriately challenging. If the tedium of searching for them has gotten to you, watch this video to learn where to find and unlock each and every one of the gold keys.

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

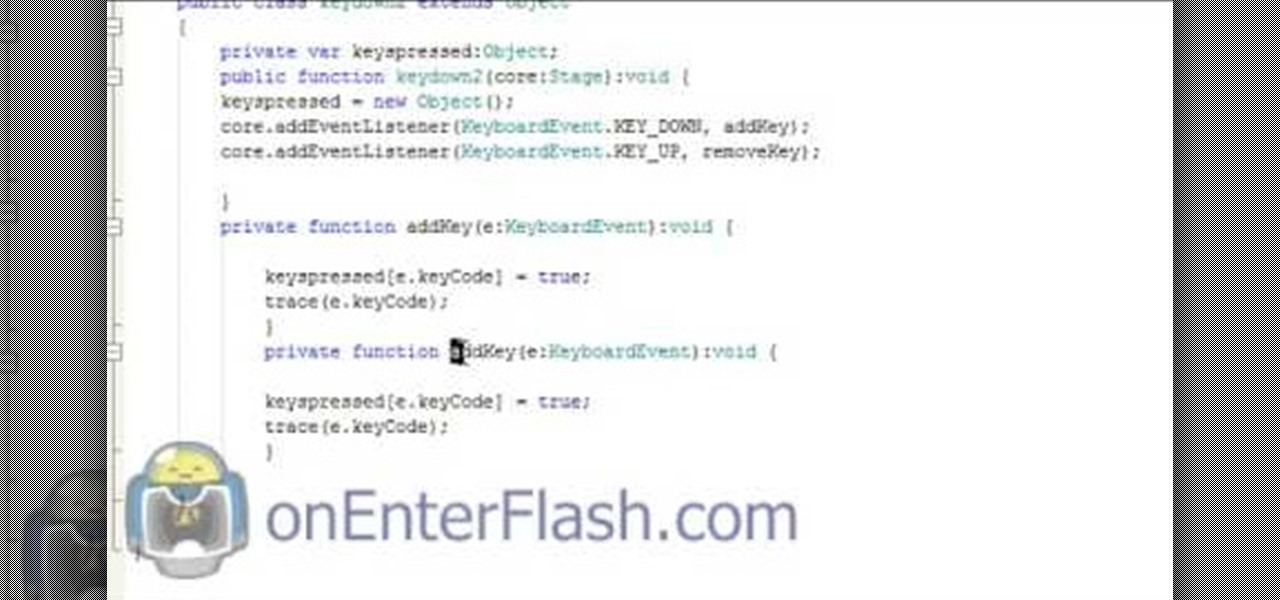
Flash Actionscript 3 is a wonderfully powerful, but somewhat obtuse, tool for creating websites. This video will teach you how to use one particular function in the language, creating a class that has multiple key detection enabled. This will allow you to create a website where users can key in multiple inputs and the website will respond appropriately.

A bump key is a method crooks use to pick locks. This idea is not new, professional theives have been using it for years, and now you can make your own.

In this video tutorial, viewers learn how to use the Slow Keys access tool in a Mac OS X computer. The Slow Keys feature is located under the Keyboard tab in the Universal Access window. Once Slow Keys is turned on, users also have the option of using key click sounds as additional feedback when a key is pressed . Users are able to set the Acceptance Delay to determine how this feature behaves. The delay of the sound can be set from long to short. This video will benefit those viewers who use...