In this first of a two-part video tutorial on the Clone Stamp tool in Photoshop. Learn to use the "Alt" key to sample. Beside removing blemishes, you will learn that you could use Clone Stamp tool to create objects in your image.

The key to understanding download speeds and if it's possible to improve yours, is really to understand that you want to increase your bandwith. Check out this video and see how to learn about bandwith, kilobytes and kilobits per second and improve your own download speeds.

Jeff Schell demonstrates how to use the Write-On video effect in Adobe Premiere Pro CS3 to create the illusion of text being "hand written" on the screen, one letter at a time. The key to this effect is animating the position of the Write-On effect, by creating keyframes in the Effect Controls panel.

Learn to Pick a lock in less than 5 minutes with this how-to video! You will need a half-diamond pick, a rake pick, a tension wrench and a pin tumbler lock. A lack of morals doesn't hurt either, unless you're just trying to break into your own lock that you've lost the key for. Watch this video tutorial and learn how to pick a lock.

Nobody wants to look at plain text when you're giving a presentation so adding images, movies, audio or any other visuals is key to a good presentation. This tutorial shows you how to add these to your Keynote presentations.

Lars explains how to use a tumbleweed compost bin. A very quick and easy process is key into creating compost for your garden. Watch video for best results.

Learning a proper handstand can be key to developing good parkour technique. This video shows both real time and slow motion handstand demonstrations to help improve your free running.

In this Photoshop tutorial you'll learn how to make interlocking patterns with perfect symmetry, for example holes cut into metal or reptile skin. Of course, the key to this is the interaction with light.

Hockey coach Tom Martin discusses and shows drills on how to win faceoffs in both the offensive and defensive zones along with faceoff strategies. Sidebars are shown summarizing each set of drills, and tips are shown in the form of pop ups throughout the video. Practice is of course the key!

This video shows unrivaled faith in Chef Paul by unplugging his bread machine and allowing the master teacher to reveal the best way to make bread. Chef Paul rewards such resolve by crafting Lean Italian Bread, Braided Rich-Egg Bread and Sausage and Cheese Bread. Tom’s only complaint? The lack of preservatives will force him to make bread again real soon. "Cooking Key" Focus: Yeast «

This video demonstrates how to trick people into buying you a drink by using the three cups trick. To do the trick, you have to flip all three cups face up by flipping over two cups at the same time. The key lies in setting the cups up differently for the mark.

This video lesson will teach you a few standard riffs using the blues scale. Let's review the Blues Scale in the key of A. Remember you can use this scale over major or minor chords. It all depends on the sound you are going for.

This short video shows you how to make a chicken. It is set to music and includes inserts along the way to demonstrate the key steps.

This short video shows the meaning of various key tarot cards. For an initiate this can be a helpful how to video, for others it's an interesting tutorial and a few moments of entertainment.

Get ready to learn how to make this classic beachside rum beverage, the Mai Tai. The key to this big liquor, big flavor drink? You need to use almond liqueur.

Need to make your house more burglar proof? Here are some easy instructions on installing a deadbolt. This lock also is equipped with a key entry.

In this video, we learn how to service a Mavic Freehub on your bicycle wheel. To begin, disassemble which requires a 10 mm and 5 mm Allen wrench. Then, remove the end cap and use the wrenches to pry the nuts and bolts from the middle of the wheel. Remove the free hub after this, then set on a cloth to the side. After this, you can remove the spring and slide it out. After this, you will clean the parts off and then reinstall your parts back on the bike. Put them on how you removed them and th...

Jim Kukral with Ask the Blogger demonstrates how to make money off of your blog and how to, in essence, become a professional blogger. Making money off of your blog takes a lot of up front knowledge and a lot of learning. Use the service Six Figure Blogging because it is a complete blueprint for your blogging success. Six Figure Blogging is a training guide to teach you everything you really need to know about blogging. If you want to learn about blogging quickly from professional bloggers ch...

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

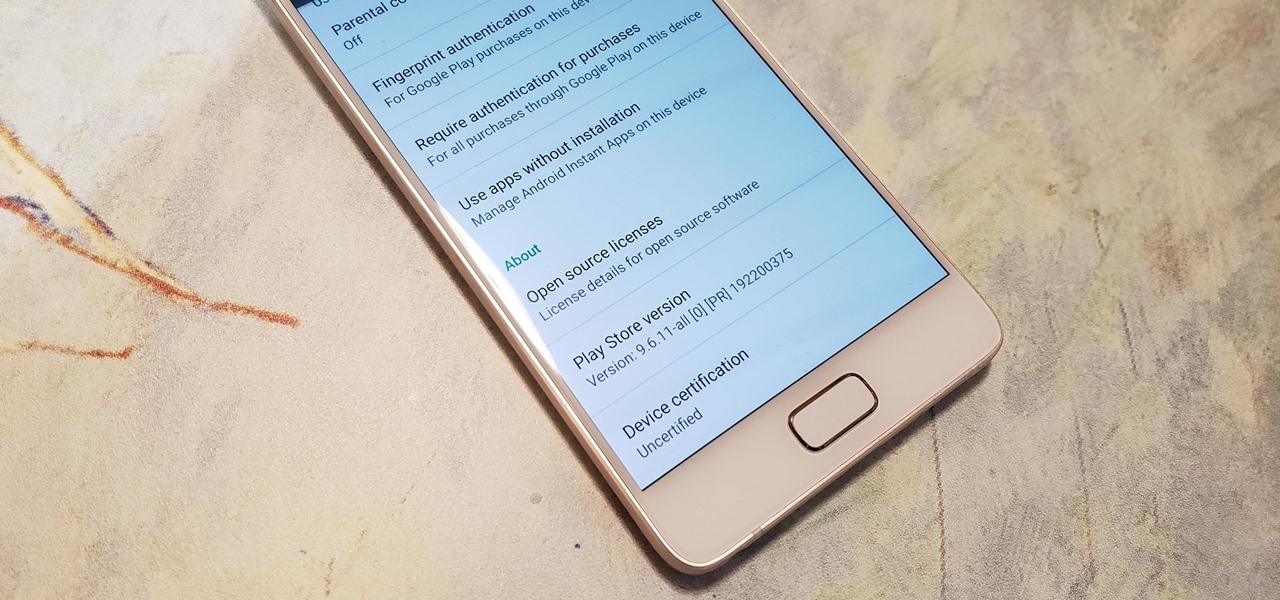
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Speakers have been an integral part of smartphones since the beginning. Razer's concept Project Linda even uses the speakers from the Razer Phone to power the faux laptop's audio system. But what if Google's next Pixel phone didn't even have speakers? What if it didn't need them in the first place?

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

There was big news today from Google, Apple, Volvo, and Nvidia regarding their self-driving efforts.

Delphi Automotive PLC has announced it is partnering with Transdev Group to develop on-demand driverless transportation systems, a deal that shows promise for autonomous development on a global scale.

The list of HoloLens applications continues to grow as more companies discover ways to enhance their operations using augmented reality. Air New Zealand is the latest to show interest in the technology, demonstrating their vision for AR in a new concept video.

An expert in the driverless market has earmarked Porsche as the company to watch in the automated car race.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

Apple is planning to completely overhaul its Apple Music streaming service this summer, and is expected to unveil the changes at its Worldwide Developers Conference in June, according to reports from Bloomberg and 9to5Mac.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

If you're going exercising, either at the gym or outside, you're going to need a backpack, gym bag, or pockets to hold your water bottle, wallet, keys, smartphone, and anything else you've got on you.