For the majority of phones, Android's volume rocker is wrong. A large vocal part of the Android community wishes the volume buttons' default control was the media volume, not the ringer. Although the Galaxy Note 9 is in the "wrong" camp, Samsung has included multiple ways to change it.
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."
Look, we all like getting things for free. That's why we can stomach things like advertisements and optional purchases in freemium apps and games — we're willing to pay for our mobile experiences in every way but currency. Although freemium seems to be the model for the future of iPhone entertainment, it looks like a different scheme might win out in the end.

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

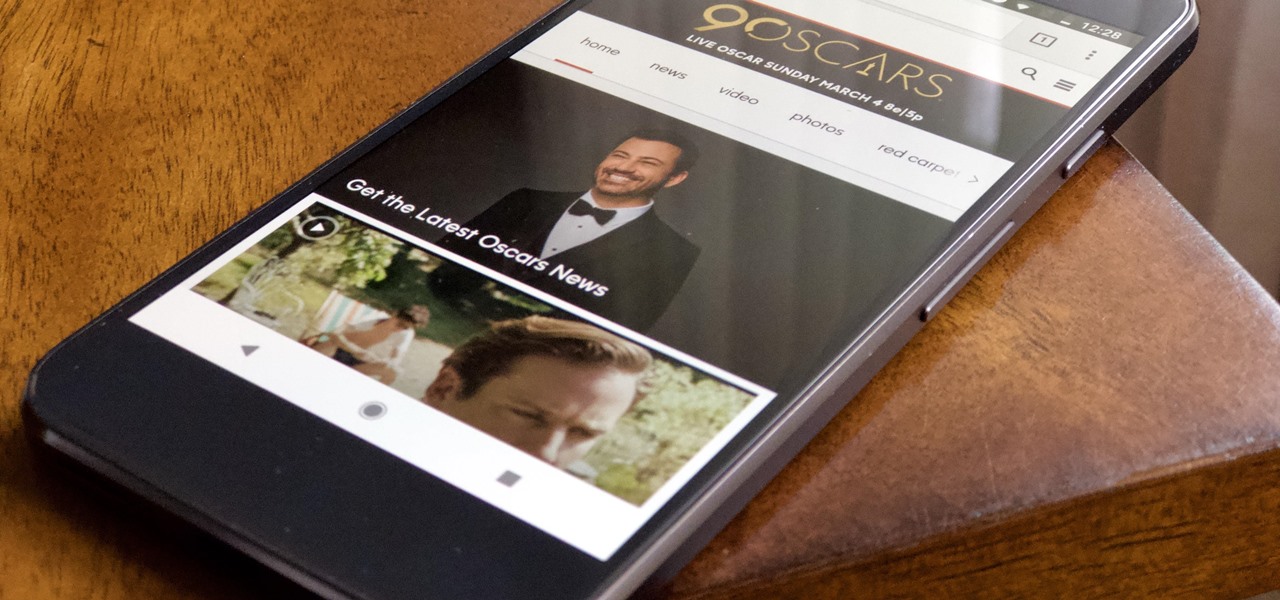
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

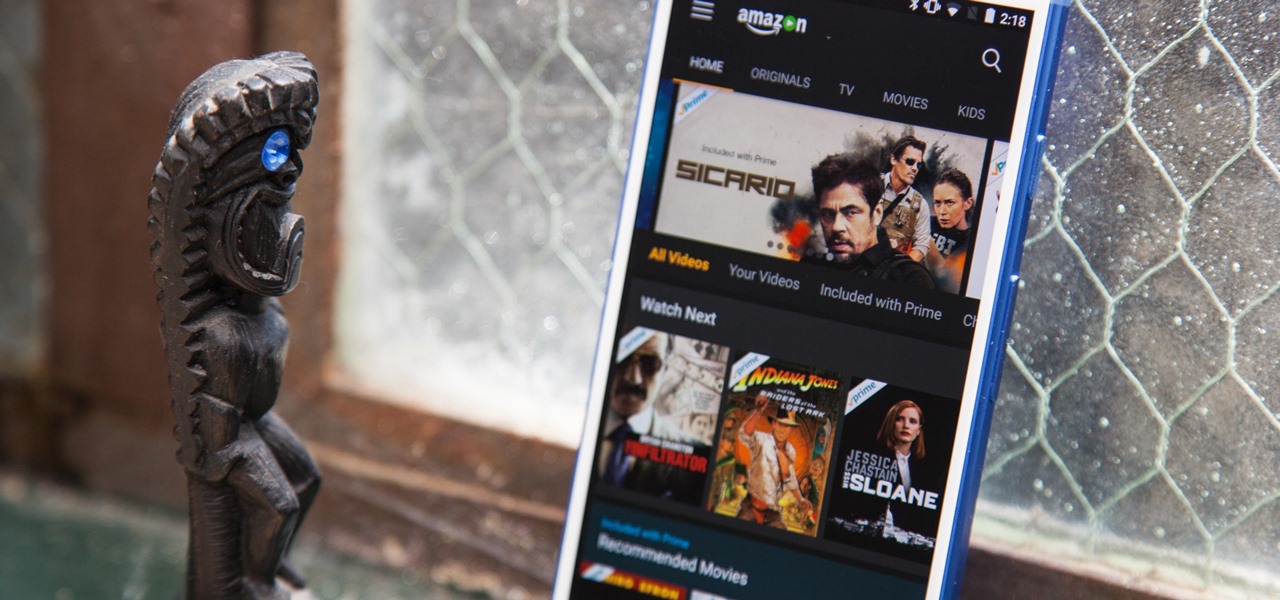
When it comes to watching movies and TV shows in Amazon's Prime Video service on an iPhone, it's as simple as installing the Amazon Prime Video app, signing into it, then playing content. However, on an Android phone, it's a lot more complicated.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Google quickly learned over five years ago electric vehicles (EVs) were the powertrain of choice for its then fledging driverless car program and the industry has since followed its lead.

For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play.

The roll-out of T-Mobile's hotly anticipated 'Digits' service is now underway. For those unfamiliar with what could be the un-carrier's next killer app, 'Digits' is basically a combination of Google Voice and AT&T NumberSync. With it, T-Mobile customers can use their number across any phone, tablet, wearable, or PC. That means you can give out your phone number and answer the call on any device you like.

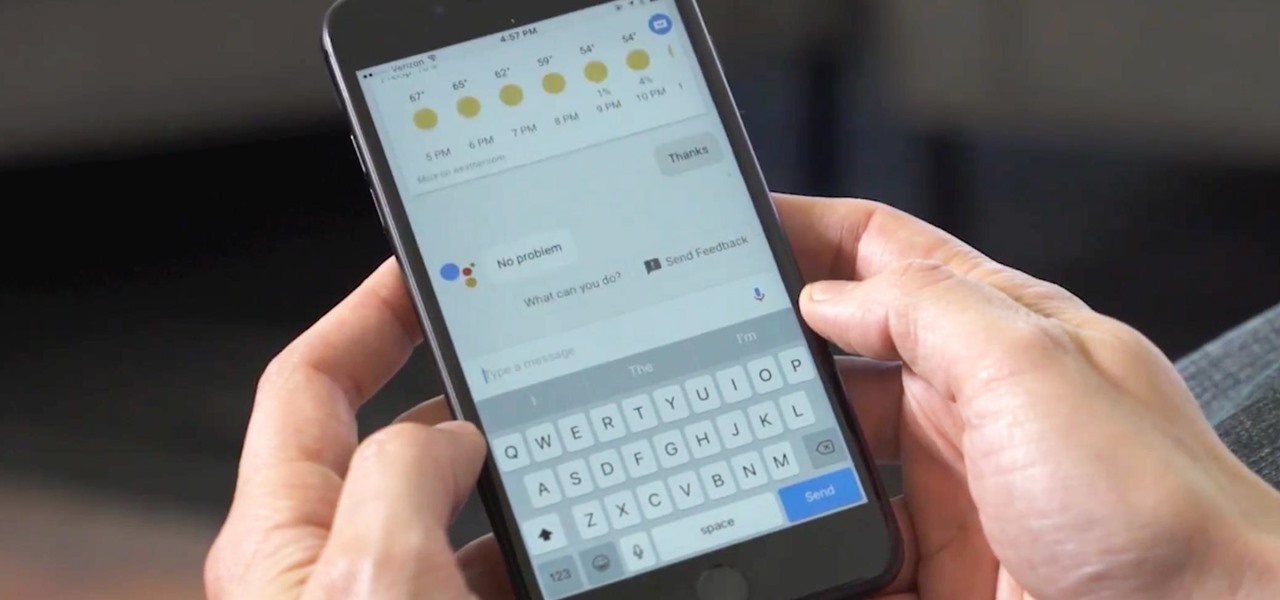
As we've said before, Siri has some major competition moving into its own playground, and Google just announced at its I/O event that Google Assistant is available on the iPhone, starting today.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

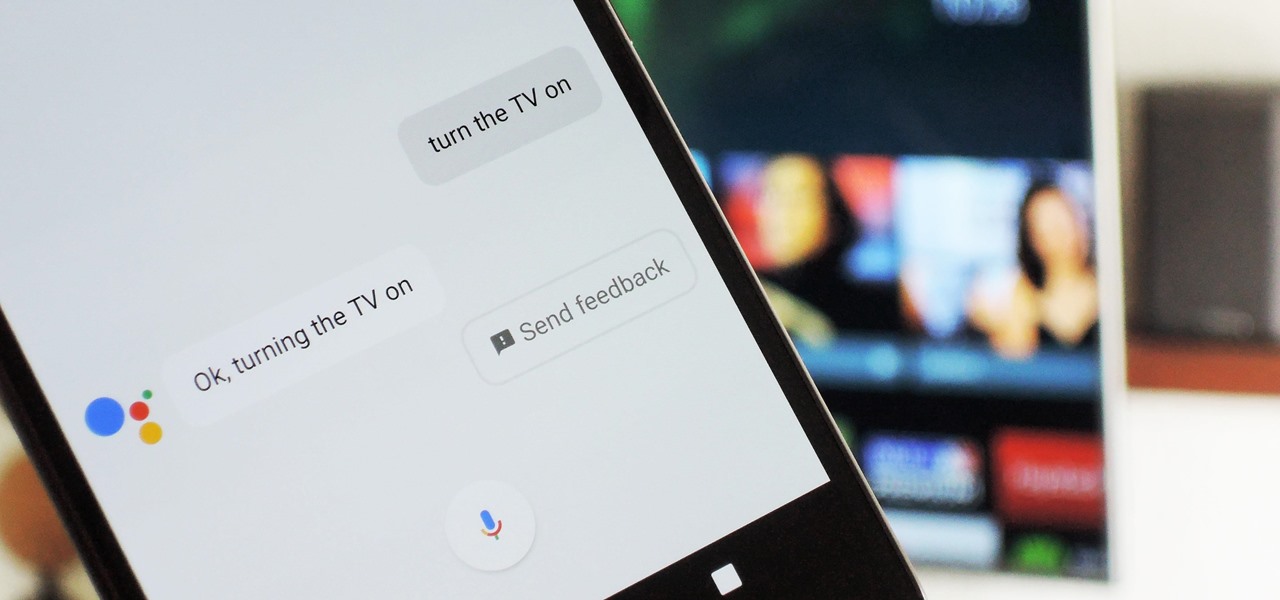
Google Assistant just got a lot more powerful thanks to IFTTT. The automation platform, whose name stands for If This, Then That, connects your favorite online services and smart devices to one another, allowing for a seamless experience with many different gadgets—and Google Assistant is officially supported.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

A couple days back we told you about the 30-day free trial for people interested in YouTube Red, and now Google is running a concurrent promotion that really sweetens the deal, especially if you're a first-time subscriber and own or plan to buy a Chromecast.

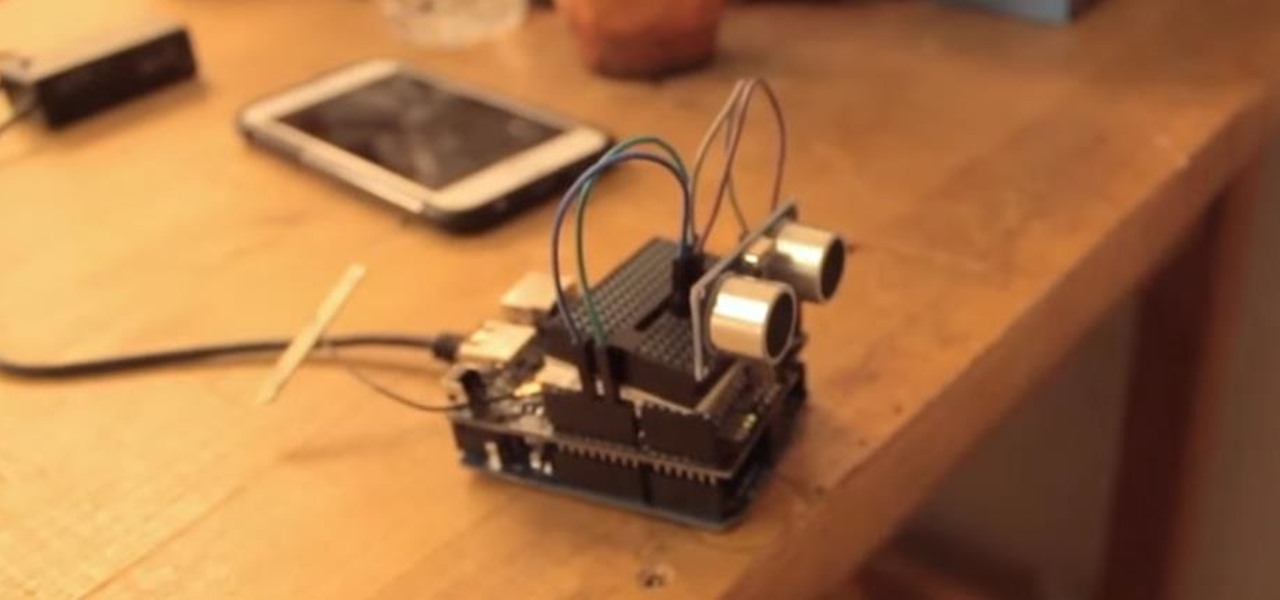
This tutorial shows you how to create an intruder alarm that sends you text message alerts when motion is detected. This may sound complicated but I am pretty confident any beginner with electronics should be able to do this just fine. The range sensor senses motion and tells your Arduino board to send the text (SMS). So you can leave the intruder detector at home, connected to your network, and still receive the SMS alerts, no matter where you are, as long as you have cell phone service.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.