The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

Many game developers have finally realized that in order for their games to be successful, they have to support Android. To really win Android users over, they should also accommodate us hardcore gamers who have OTG cables with the ability to hook up controllers to our devices.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.
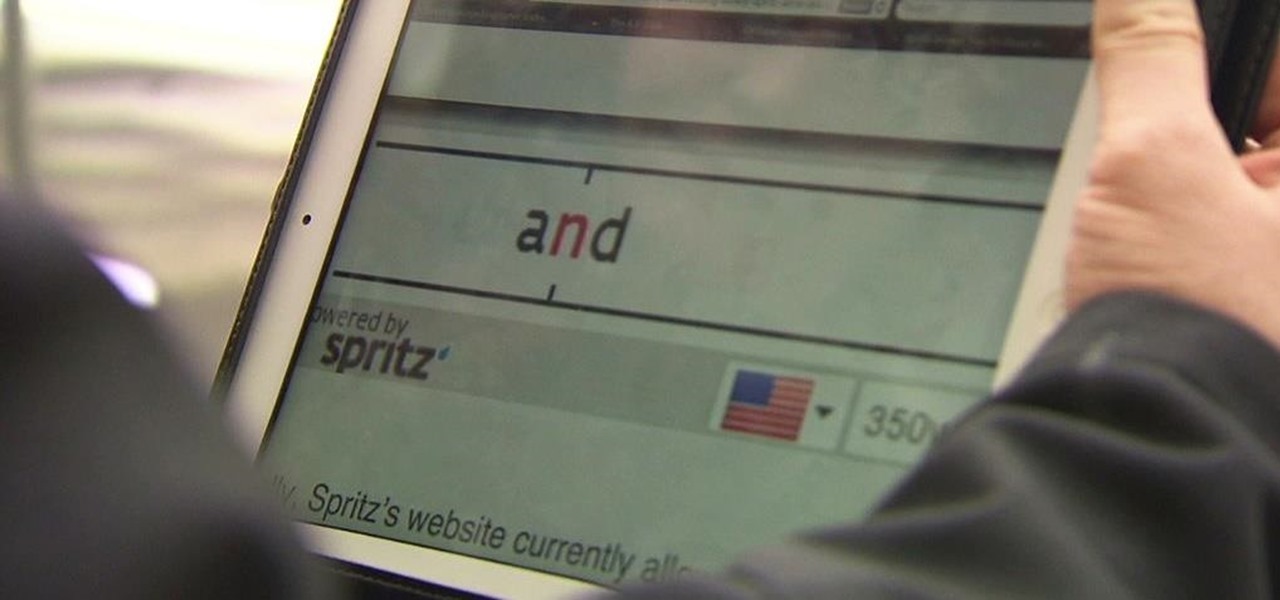
Reading is no longer a leisure activity—it's an on-the-go activity that requires speed and less attention. That's why speed reading apps are growing in popularity. As smartphones and tablets increasingly take over the traditional book market, reading skills need to be adjusted accordingly, so you can cram in 5 pages in-between texts and emails.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Hey, coffee drinkers—your morning cup of joe is killing your metabolism.

Erudite. Barbiturate. Cacophony. Denouement. Okay, that last word is technically French, but words like these make the average person sweat, and it turns out that the key to learning how to pronounce them once and for all just might be getting them wrong.

Welcome back, my greenhorn hackers!

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

I have a theory that chocolate chip cookies are the gateway drug to cooking. The recipe is easy, no special equipment is required, and at the end, you get warm, fresh-from-the-oven cookies that are simply irresistible. It's how I got hooked on baking and cooking, and anecdotal evidence (i.e. me asking my other kitchen-obsessed friends and a few culinary students) supports me.

As fellow softModders, I'm sure you strive to find any and every way to make your phone unique. Wallpapers and icon packs are great to get started, but to really stand out from the rest, try changing your HTC One's boot animation.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

When you think of nail polish, it's probably almost always in the context of a manicure. I mean, that's what it's made for, right? But there are plenty of other things you can use clear or colored nail polish for besides painting your nails.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated.

I can definitely say that my MacBook is one of my best friends, but I was still very disappointed when I realized that the only game my laptop came with was chess. For starters, I'm not very good at chess. I haven't even beat the computer once, which really grinds my gears. But, it has come to my attention that chess isn't the only pre-installed game on my Mac—there seems to be some hidden gems that I simply wasn't cool enough to know about. For some of you, this may be old news, but for me, ...

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

I love my Mac just the way it is. Well, minus the fact that I accidentally deleted iPhoto and would now have to pay $14.99 to get it back. Other than that, my Mac is pretty sweet.

I know what you're thinking—taking a screenshot is super simple. While that is partly true, taking of a screenshot of the Start Screen in Windows 8 is little bit tricky, unless you're on your Surface.

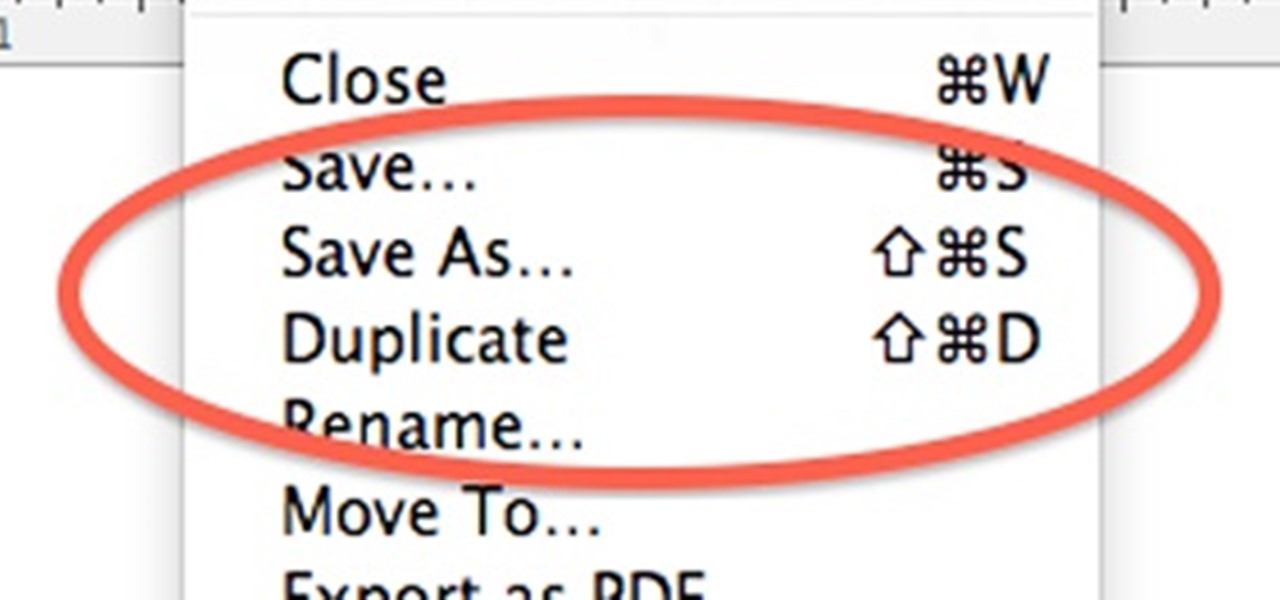
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

Most cars have them… keyless remote entry systems, and the newer Lincoln model cars have them, too. The Remote Keyless Entry System lets you unlock the doors and liftgate by simply pushing a button on the key fob. There is also a panic alarm on the key fob that flashes the parking lamps and sounds the horn. No more fumbling with car keys! Watch this video to see how to use the key fob on your 2010 Lincoln vehicle.

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

In this video tutorial, viewers learn how to pick the lock of a garage door. It is not recommended for users to learn this technique to use to open other people's garage doors to break in someone's home or steal their possessions. The tools needed for this technique are a L-key and a diamond pick. Put the L-key at the bottom of the lock hold and fiddle around with the diamond pick on the top part of the hole. Do this until your able to rotate the lock. This video will benefit those viewers wh...

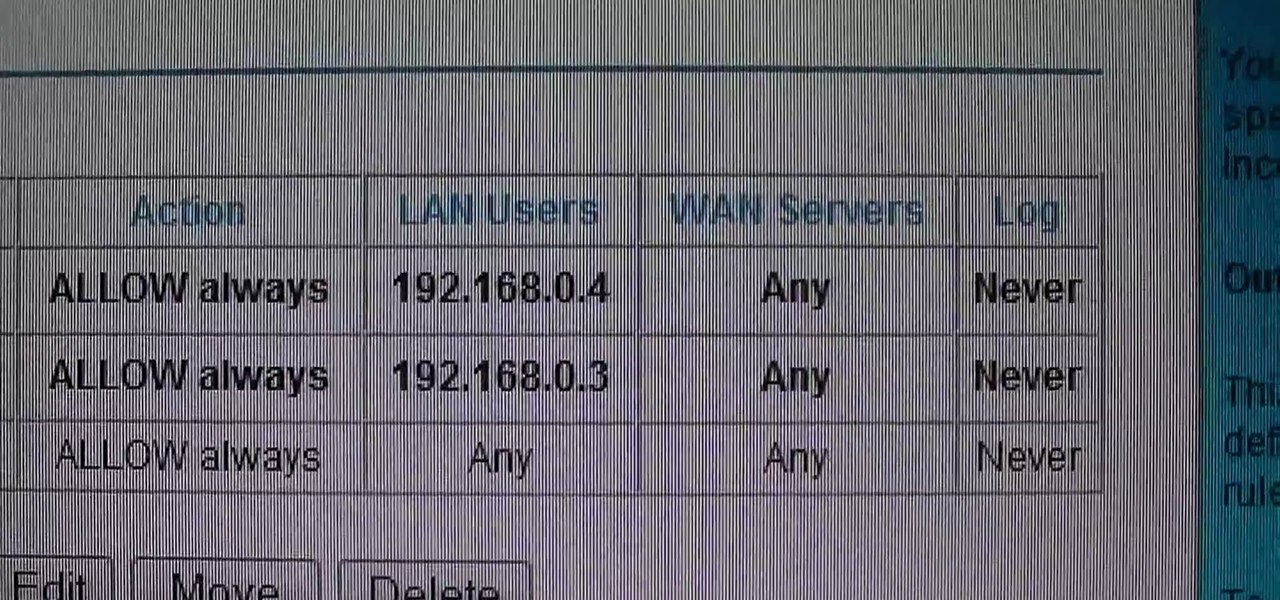
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

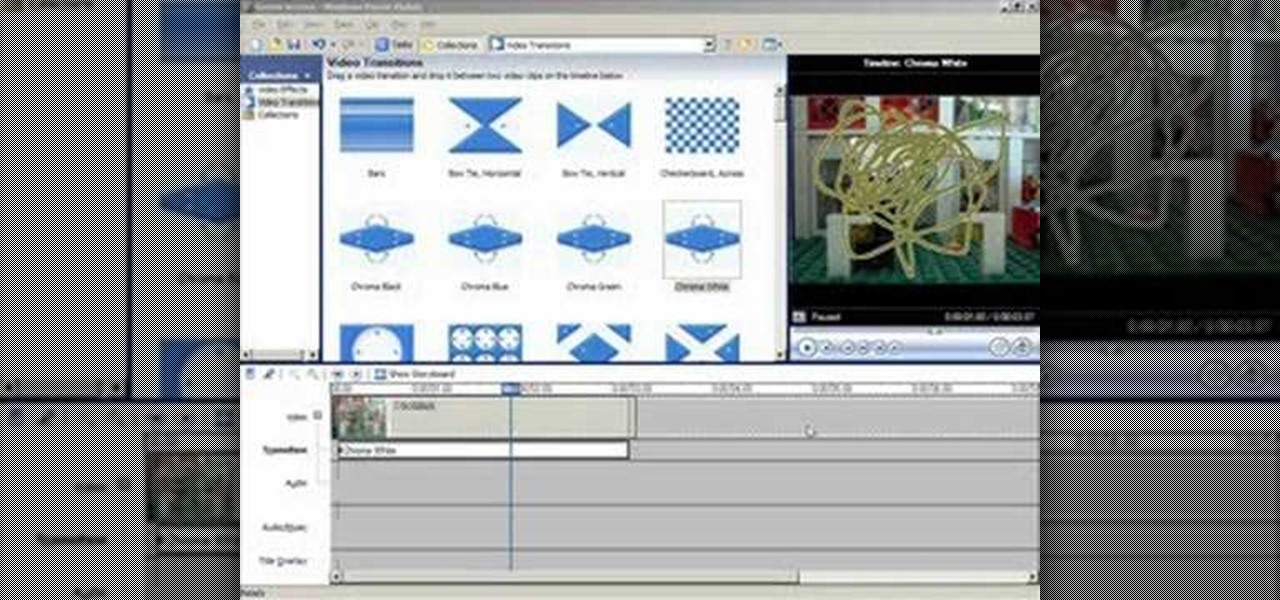
Open windows movie maker and take any video which has the background of same color. Drag and drop the video on to the time line. Then go to tools > video transitions and take the chroma key and drop it between the two videos. The chroma color should correspond to the background color of the video. After this, save the movie file. To pick the right color for the background, download Debug mode wax. This will help in creating some home videos with special effects.

If you don't have room for a full-scale compost heap, you can always employ the services of some worms. In this handy vermiculture how-to, you'll learn how to build your very own wormery.

With all the documents ready, we need to fill our wallet with money for the travel. This video discusses various ways of filling the pocket. That is how to prepare the money for international travel. Over the years credit cards have been widely used by many travelers, which is safer than carrying cash. In this case we need to contact the credit card provider well in advance and notify them about the travel. Also we need to learn about the various fees applicable to international purchases. Th...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.