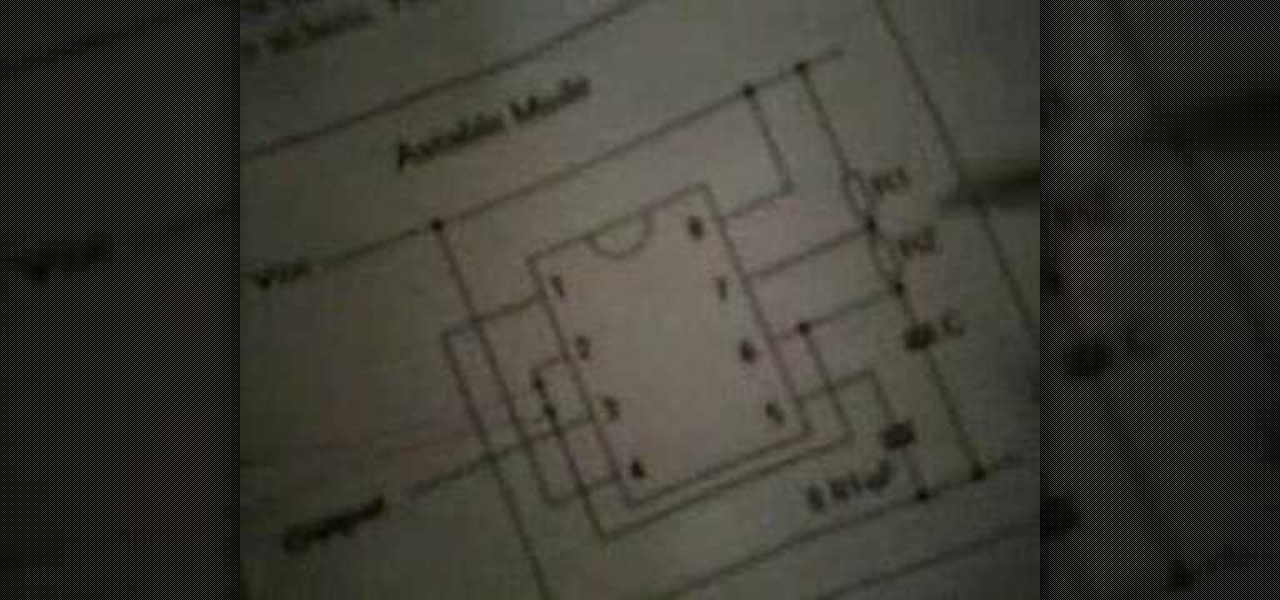
This demonstrates how to wire a 555 timer chip for Pulse Width Modulation. Items used: solderless breadboard, 555 chip, 510 ohm resistor, 100k ohm variable resistor, 1 RGB LED at 20-25ma, wires, and 9v battery. And those vertical lines are what i mean in terms of what you can see only on the camera. You can see the led light of course without the camera.

Chef John and his mother show us how to make her key lime pie.Here is the recipe:it will make enough for two pie crusts. You need salt, flour,shortening,ice water.The filling requires 3 eggs,3 limes, sweetened condensed milk, green food coloring whipped cream, and lime zest.

Israel Hyman shows yow how to use the sun as a key light for film, video, and photography, including how its angle affects your subject’s look.

This is a tutorial on basic chroma keying with Adobe Premiere .

Learn how to make a cool monogram key chain that holds post-it notes.

See how to use chroma keying in Photoshop. This technique is most often used to remove green screen backgrounds from images.

In this video Benny teaches you how to say "I like shopping" in Mandarin. He also goes over other terms that will be useful when you are shopping like credit card and discount. You'll be shopping like a pro in no time!

Do your videos lack emotional impact? Do you wonder about the framing options that could be use to produce a better video image? This episode of Izzy Video covers the Framing Terms for different types of shots and how to use them.

This tutorial tells you how to use pitch and speed in GarageBand '08. In GarageBand '08, they work independently from each other to allow for greater control of key and tempo.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

This video explains electricity as the flow of atomic particles called electrons. Animations demonstrate electron flow. Batteries are described as chemical devices designed to create electron flow. Terms covered in video include Volts, current and Amperes

Are you not quite sure what slow playing mean in poker terms. You should only slow play when your hand is very strong and the odds of the next card giving your opponents a stronger hand very small. Master the art of slow playing and win more hands than before.

All-American Skeet Champion Todd Bender explains how the game of skeet shooting is played and some of the terms used in enjoying this fun sport.

Learn a stunning effect by just remembering one card. The key card! Follow along as our British headless magician teaches you how to perform this basic magic trick.

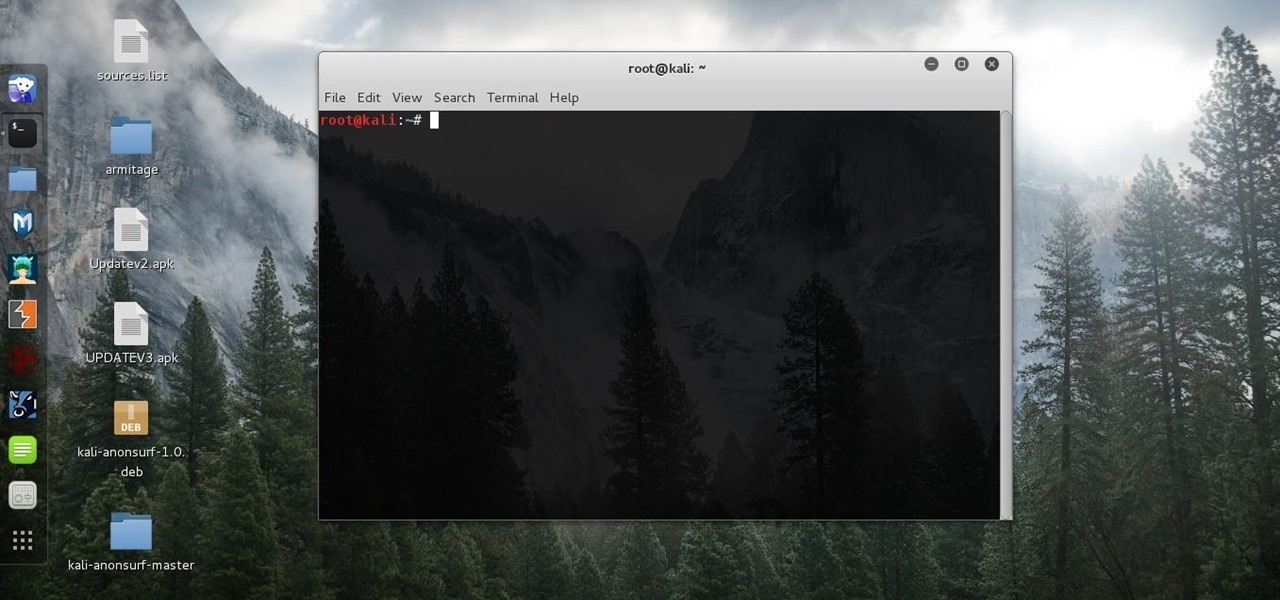
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Having pushed more than two million downloads of its Bait! game for the Gear VR and Daydream platforms, VR developer Resolution Games is bringing the virtual fishing fun to augmented reality.

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

A new survey of game developers paints a somewhat less than rosy future for augmented reality gaming, but there's still some hope for its long-term prospects.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

It was nice while it lasted. Samsung users who managed to get their hands on the Galaxy S8 or S8+ early enjoyed the ability to launch any app through the dedicated Bixby button. Unfortunately, Samsung wasn't all that down with us using the Bixby button for purposes other than its intended use — to provide quick access to Samsung's new virtual assistant.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

This video will guide you top 10 windows shortcut key which is very useful in everyday computing. Watch the video and follow the steps to know top 10 windows shortcut key.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Macrame Owl - Decoration for keys / key ring or necklace / How to / DIY Video: .

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Video: . In this tutorial I show you how to get a perfect Chroma Key using After Effects.

It has happened to everyone at one time or another, but if you work in an environment with cars, it may happen much more often.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.