You already know the mechanics of DJing, but you want to be an international celebrity -- or at least drink for free while showing off your music collection. Here's how to spin your hobby into a career. Watch this video to learn how to become a professional club DJ.

Do you want strong, healthy nails? With just a little time and basic care you will find that you have fingernails that others admire. Growing strong, healthy fingernails can be done with just a little time and care. One of the keys to healthy nails is to make sure you get enough protein in your diet. Take time to think about your nutrition. Are you eating enough protein? Even if you are a vegetarian you can get plenty of protein with beans, nuts and tofu. Also, are you drinking enough water? ...

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

Apple released the third iOS 14.6 beta today, Monday, May 10. The update fixes a bug that could cause your iPhone to experience performance issues after startup.

Apple seeded public testers the second iOS 14.6 beta today, Friday, April 30. The update (build number 18F5055b) comes three hours after Apple released the second 14.6 developer beta, four days after the launch of iOS 14.5, which introduced over 60 new features and changes to iPhone, and eight days after the first 14.6 beta hit developers' iPhones.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

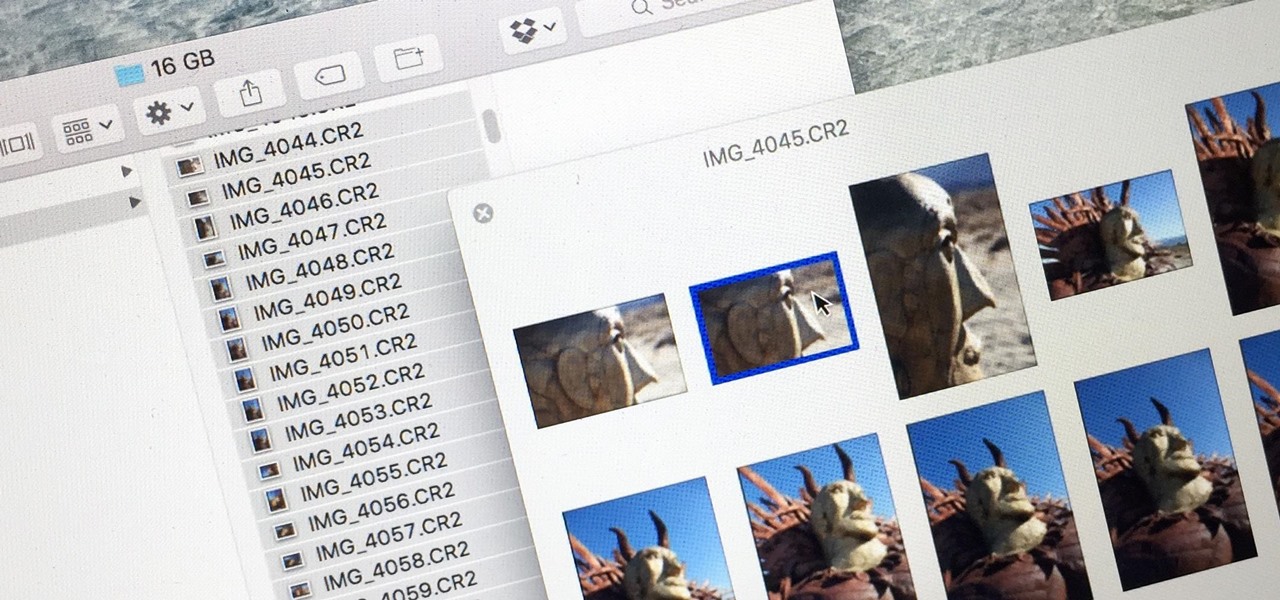
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.

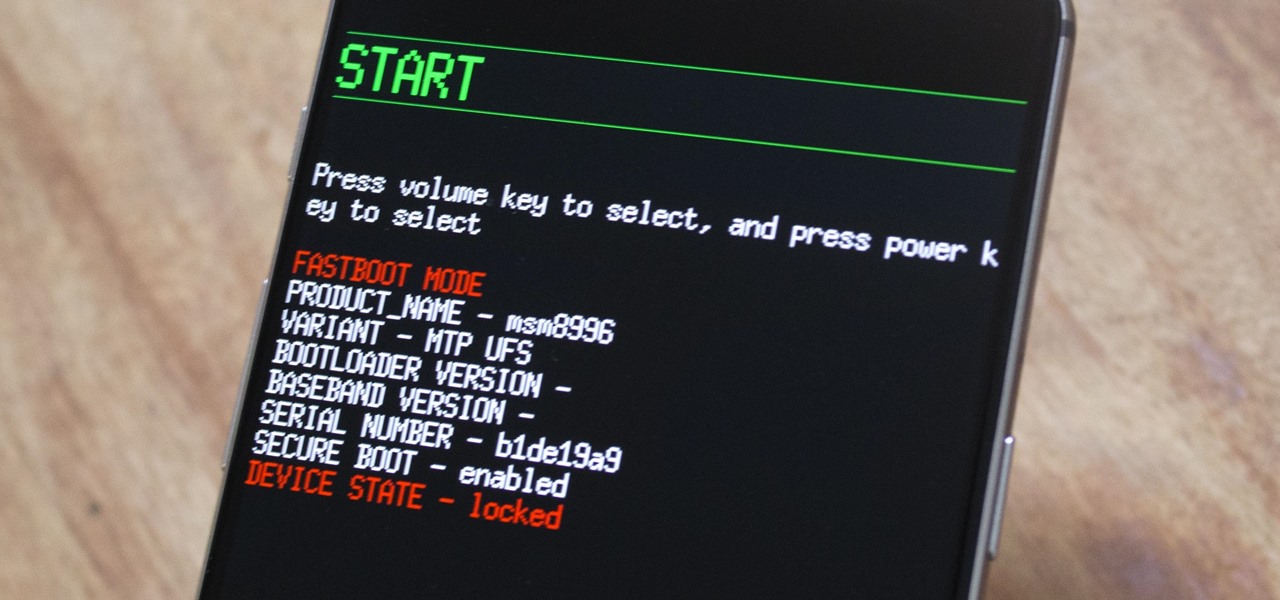
Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows.

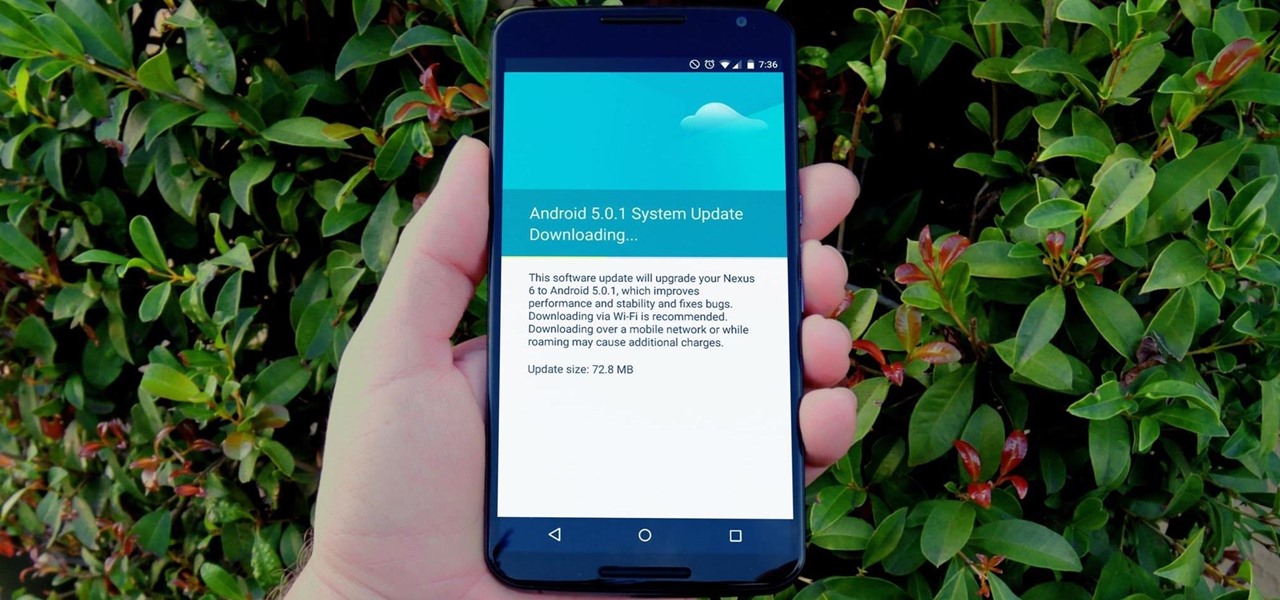
One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

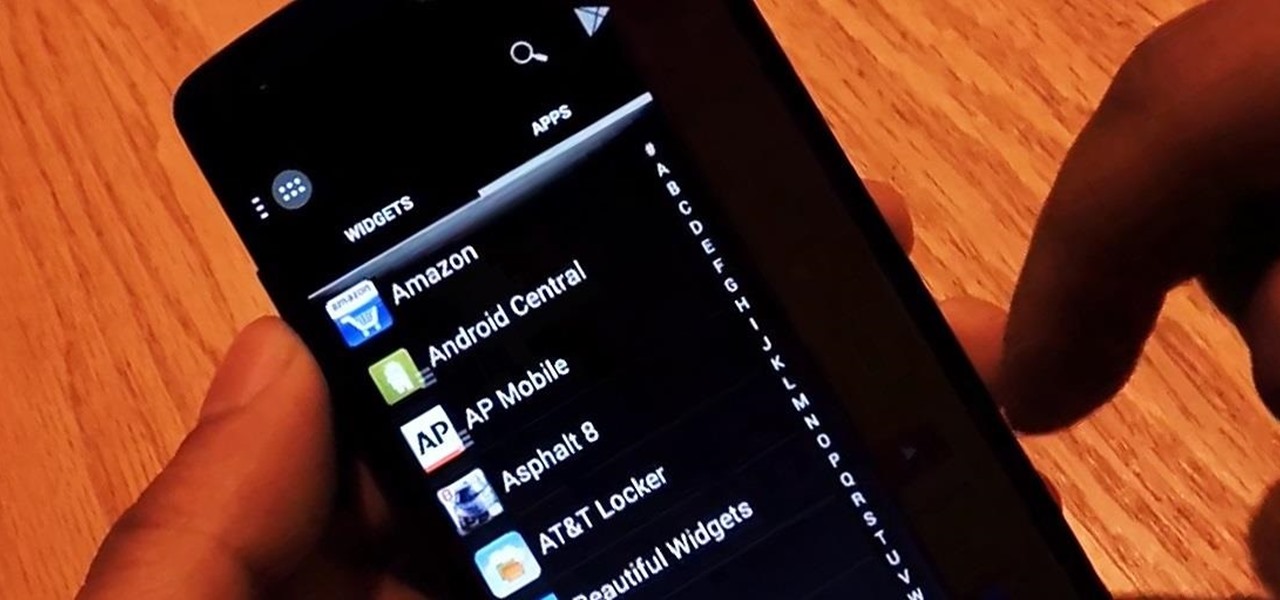
One thing almost every Android launcher has in common, from stocks to skins, is the way they handle organizing and launching apps and widgets. Tap an app icon to open the app. Drag apps together to create a folder. It's simple, it works, and it's what we know.

The Nexus 5 is the current Google flagship packed with the latest and greatest of all things Android, but what if you never made the leap from your Nexus 4 smartphone?

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

The key to getting good grades on your tests is being able to improve your study skills, including reading comprehension - the ability to understand what you've just read. Use these practices to improve your ability to read and comprehend your textbooks at a higher level.

Hitting a high golf shot is easier to do with a nine iron or pitching wedge, and the key is to move a ball forward in the golf stance. If you are ready to learn this shot, follow this tutorial. This helpful video will allow you to create backspin when elevating a golf ball and improve your swing. The clip will show you a quick step by step to get you started..all you have left to do is practice!

Here's a low-key way to take advantage of someone's trust. Gain access to a friend or frenemy's iPhone and add curse words as separate new contacts to their contacts page. Sit back and wait for your friend to text someone. Enjoy.

Using simply 2 bobby pins and a tension wrench, you should be able to open up a padlock without needing the key. When properly wiggling the pins around, with the right tension, you should be able to break right in. Remember, only pick locks that you own, otherwise it could be considered illegal.

If you discover that your Guitar Hero guitar is having some difficulties, check out this video for instructions on how to rectify the problem! This is especially useful if you discover that your keys stop working, or something of the like.