If you need a dolly for your movie masterpiece, you don't need to go with a professional dolly system. You can save that money for your expensive actors and actresses by building your own DIY camera dolly on the cheap. You'll need some nuts and bolts, PVC pipes, scrap wood, drill bits and a drill, inline wheels and a hammer. This homemade camera dolly will cost you around 65 bucks.
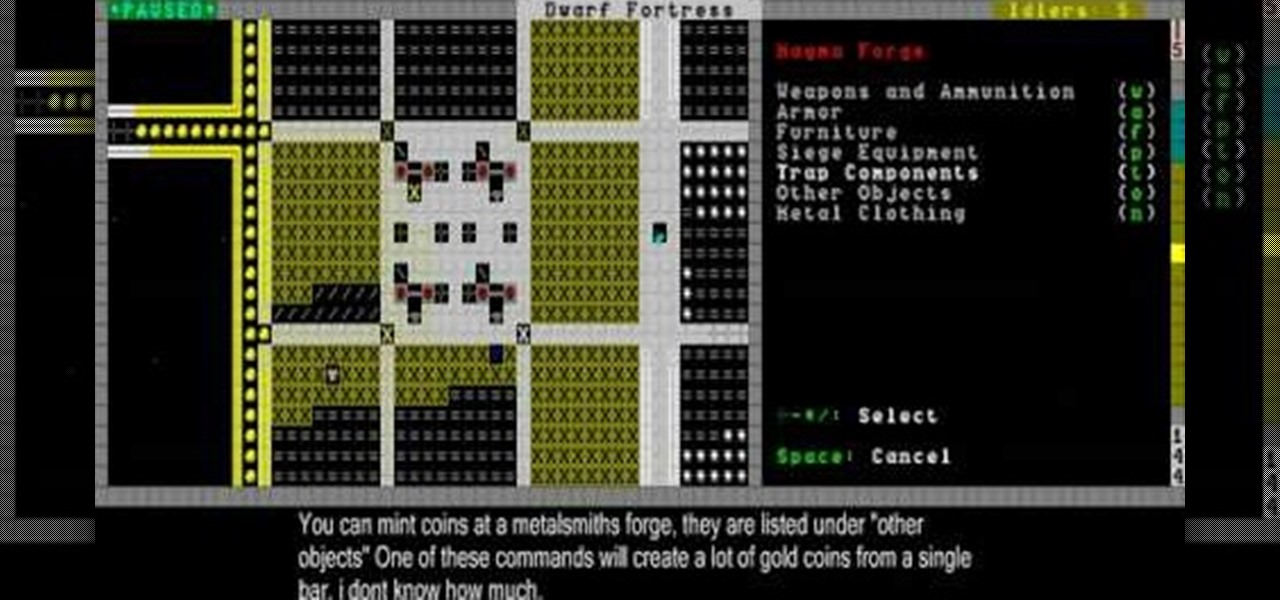
In this video you will see the results of the creator's preivous attempts to use a cave-in to trap demons in their peculiar chamber, then learn how the Justice and Economy systems work in Dwarf Fortress.

The XBox 360 console, especially the older models of it, is not very well-made. There are all sorts of different design errors that can effectively shut your system. This video will teach you how to deal with just one, the unplayable disc error that plagues the disc drives included in the system. You will learn how to fix this error on the Hitachi DVD drive included in many consoles, saving you money and helping you get back to playing games as quickly as possible.

The temperature control onto hot and the fan is turned off. A bleeder is loosened with a 12mm screwing object. A funnel attachment is placed onto the cooling system and the actual funnel placed ontop. A pre-mixed liquid is poured into the funnel. The bleeder valve is then tightened. Another set of liquid is poured into the funnel and some is poured into a reservoir at about 3/4. The vehicle is started and druiven a few steps back and left on, to run at about 2500 rpm until the cooling fan com...
Have you ever gotten a new computer and it works great the first few weeks that you use it? And then after only a few weeks of use it suddenly starts to respond very slow and sluggish. A very common complaint among users of Microsoft's Windows XP operating system for the PC is that it can be a slow operating system. In this video the author shows us numerous tips, tricks, and tweaks on how to substantially speed up a Windows XP computer.

The Wood Whisperer is Marc J. Spagnuolo, a professional and passionate furniture maker, who also contributes to Fine Woodworking and Popular Woodworking. In this video, Spagnuolo shows us how to build a French cleat storage system. It's a very versatile unit, and gives you plenty of storage space without cluttering up a room.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to fix low volume in video with Avidemux on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

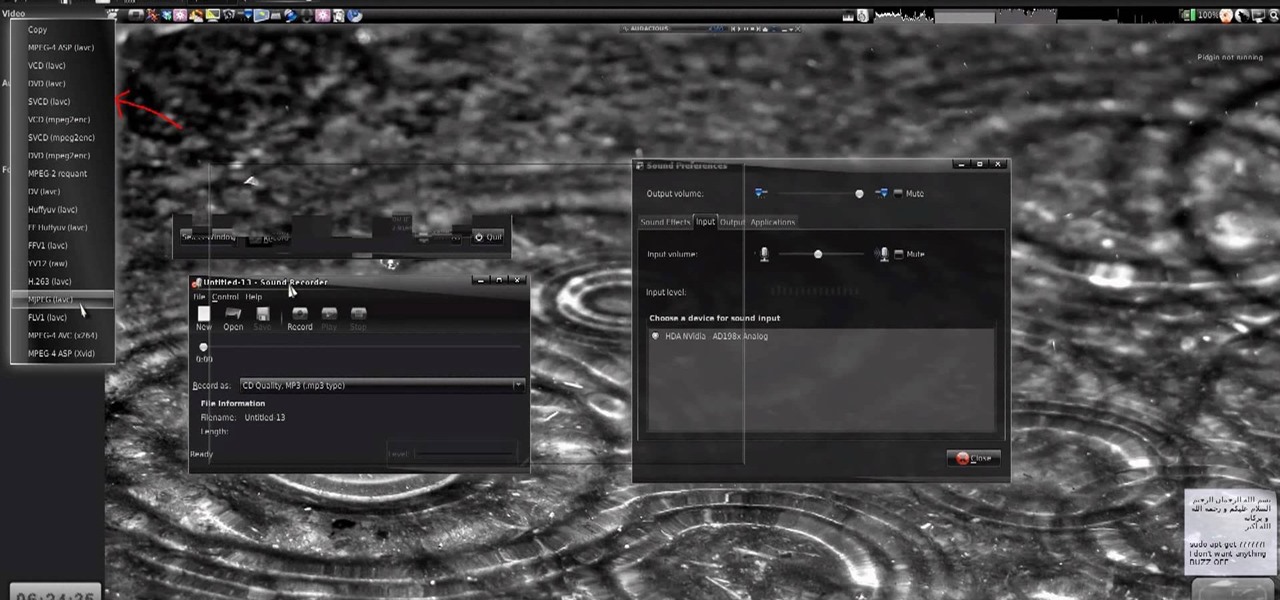
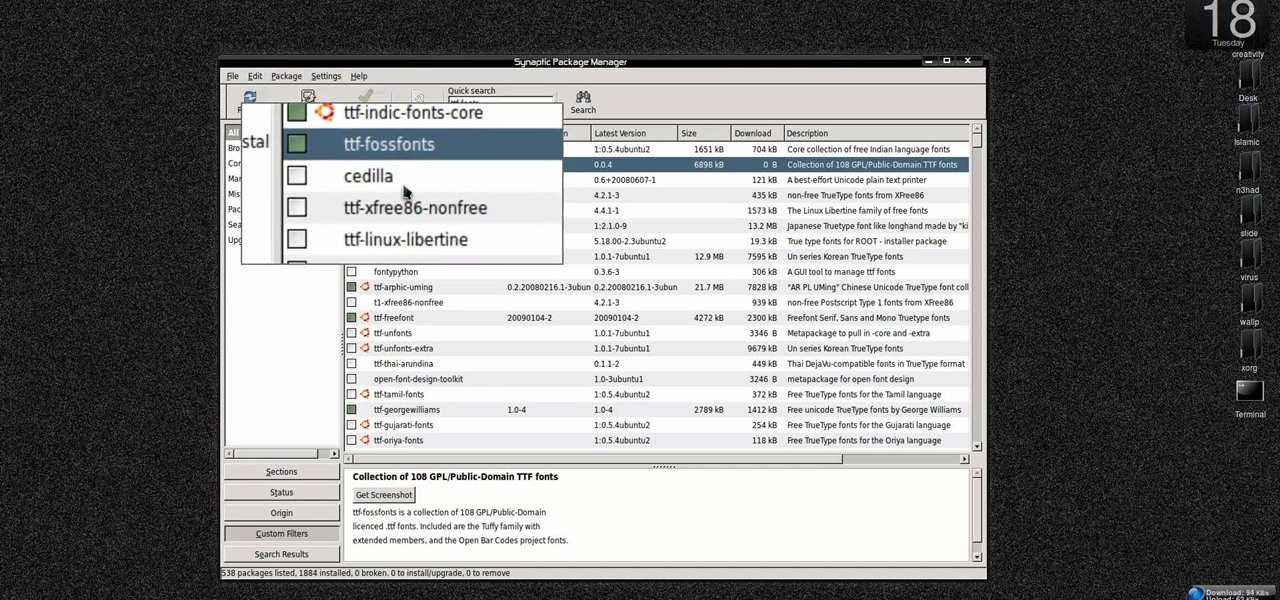
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install 200+ screensavers on Ubuntu Linux.

Build a mineral oil computer aquarium. It cools the system while giving you something to look at.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

For the first time since its inception, the famously hidden System UI Tuner has to be unlocked in a new way. No longer can you long-press the gear icon (found in Quick Settings) until it spins and reveals the hidden settings option. With Android 9.0 Pie, there's a new workaround to reveal the menu.

While some in the augmented reality space are tweeting about future amazing immersive experiences and others are showing off cool experiments, Microsoft continues to move forward with tangible business solutions right now that show how the HoloLens can improve business.

The Galaxy S9 is now available worldwide. We ran through several Android P features already on the Galaxy S9 and even took a look at a few hidden things you might not know about. While you're likely loving your new phone, there are a few concerns with any new device. One possible issue is the new persistent Android System notifications on the Galaxy S9.

It looks like Magic Leap is getting its ducks in a row to launch its Magic Leap One: Creator Edition as the company's name is once again showing up in US Patent and Trademark Office (USPTO) filings.

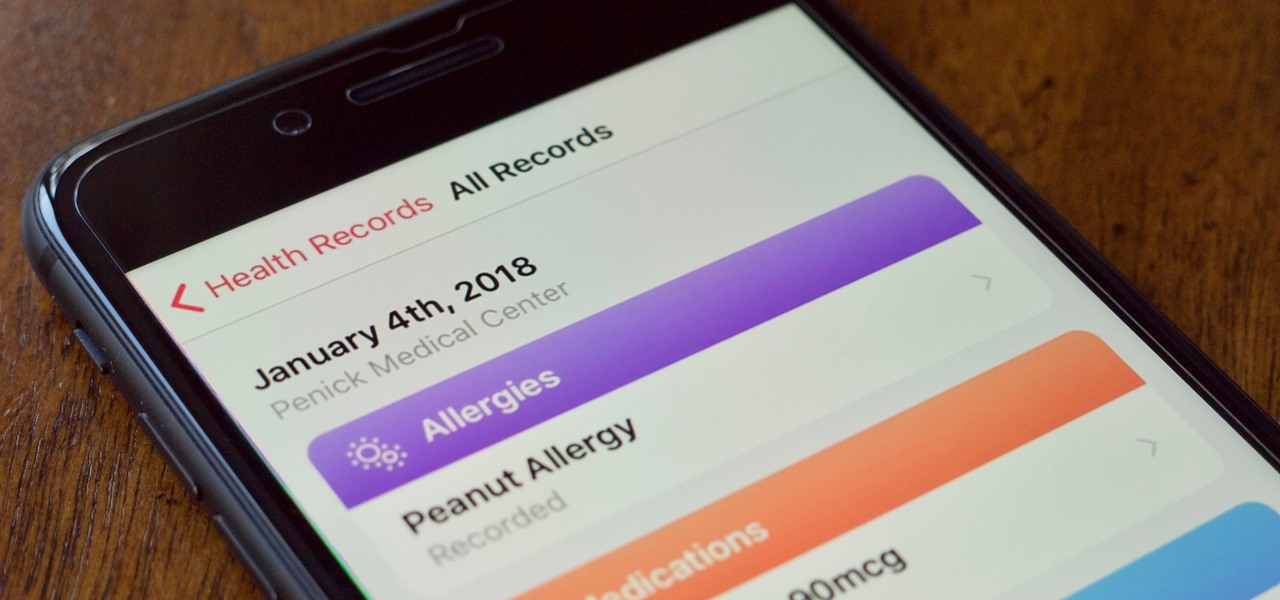
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the carriers themselves have technical difficulties that can result in your phone's clock being minutes or even hours out of sync.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Five Phases of Hacking:- The five phases of Hacking are as follow:

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
Welcome back Hackers\Newbies!

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.