As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.
This video will guide you top 10 windows shortcut key which is very useful in everyday computing. Watch the video and follow the steps to know top 10 windows shortcut key.

Macrame Owl - Decoration for keys / key ring or necklace / How to / DIY Video: .

Video: . In this tutorial I show you how to get a perfect Chroma Key using After Effects.

It has happened to everyone at one time or another, but if you work in an environment with cars, it may happen much more often.

What's a penny worth these days? Not much. But could there be some free energy hidden inside your spare pennies? You'd be surprised! See how I hack together stacks of pennies into makeshift batteries that can drive small-current devices like LEDs and calculators.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?

Opening doors with keys is boring and for the lockpicking illiterate. Inject some mischief into your life by watching this video on how to open a lock and break into a house using everyday objects you have lying around.

The key to a successful indoor hydroponic garden is in both irrigation and lighting. This video can't help much with the irrigation, but if you want to decide what the best lighting systems are, this video is for you! There are a wide variety of bulbs and power sources that you can choose from when constructing your own hydroponic grow operation. The key is wattage, and the more wattage you can get out of your bulbs, the better your garden will be.

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Gary Clark shows you what it takes to hang a beautiful new chandelier in your home, and believe it or not, the installation is simple! No matter what kind of hanging light fixture you're installing in your ceiling, the process is generally the same, where you first need to cut a hole in the drywall and run some wire to the panel. Then make sure you have a junction box that can support the weight of the fixture.

Three point lighting can be used to achieve professional studio results. For this, you will need: a key light, a fill light, and a backlight.

This video tutorial is in the Computers & Programming category where you will learn how to use caret browsing. Caret browsing is a method of selecting text on any web page. You can activate caret browsing by pressing the f7 button on your computer. It is available in Internet Explorer and Firefox browsers. Normally, for selecting text on a web page, you highlight the text by clicking and dragging the cursor and then you can copy and paste it in to a text editor. While doing this, if there are...

In this tutorial, we learn how to use the zoom feature in Mac OS X Leopard. First, go to system preferences, then universal access. Find the zoom category, then turn it on of off. You will also see the keys that you can press which will make it appear. If you go to the options menu, you will be able to maximize or minimize the zoom. Test this out by zooming in on a page and holding the control key along with the tracking ball on your mouse. When you do this, everything will become far more zo...

In order to prevent accidental CAP LOCKS, you can use a number of new, innovative and free software solutions. With your Windows 7, there are functions available to assist you.

This video demonstrates the four keys to a powerful freestyle. The first is internal shoulder rotation. Rather than holding your arms out straight, rotate the shoulder inward to bring the elbow up. Point your fingers downward and catch the water with your entire forearm.

Have you locked yourself out of your car? Well, as long as you have a shoelace, you may be able to get back in.

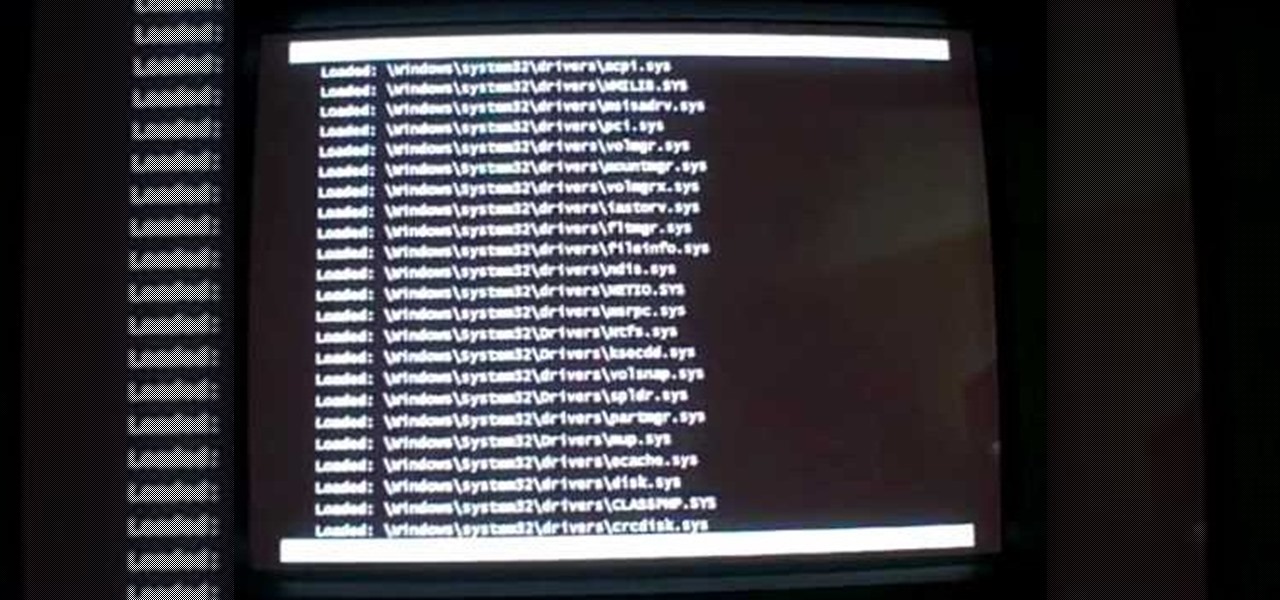
In this video tutorial, viewers learn how to start a Microsoft Windows computer in safe mode. Begin by turning on your computer. As your computer starts up, press F8 before Windows launches. Tap the F8 key slowly (about 1 second apart) as soon as the computer starts up. Keep tapping until the Windows Advanced Options Menu appears. The use the arrow keys to select the appropriate safe mode option and press ENTER. You may need to log into your User account. This video will benefit viewers who u...

Prius models that are equipped with tilt-slide moon roof have a remote control button on their smart keys for the remote air-conditioning system. Before leaving the vehicle, make sure the headlights are switched off or set to auto. All windows are closed and check the temperature setting of the AC system. As you return to the Prius, press the remote AC button on the smart key remote to activate the air conditioning system. The cabin will cool to the pre-set temperature without turning on the ...

GetConnectedTV shows you how to multitask during phone calls on your Blackberry. You do not have to hang up your Blackberry in order to look up information. This works well if you are using an earpiece, Bluetooth, or the speaker function on your phone. When a call is made to you and you need information, hit your convenience key and it should take you to a home screen where you can look the information up. You can flip through the other applications on the home-screen as well. When you are do...

This video illustrates how to make a vase out of old light bulbs. Materials:

Interviewing lighting basic training tutorial provides easy to follow instruction in this step by step video. Set up the interview area to allow the best camera angles. Place your lights in key, fill, and backlight positions. Use back lighting spillover to fill subject area without camera spillover. Check your setup with the subjects and make any necessary adjustments to your camera or lighting angles. Place your crew and your ready for your interview. This scenario using key, fill, and back-...

In the GetConnected TV show BlackBerry expert Darci Larocque from Swirl Solutions gives an easy tip on how to call voicemail directly with one (1) key. This option can be seen in other cell phones also, but in a BlackBerry you can set a password for this. Hold the green button or call log , go to menu - Voice Mail, set your password, click escape and save. Now when you dial No.1 or hold it down you go directly to your voicemail.

Creating a motion tween in Flash CS4, which is moving one image from one position to another position.

Have you ever had to close an application with private info in order to let someone else use your PC? LockThis! is a windows application that lets you secure individual programs without the hassle of having to save your progress and closing the program. To use LockThis! just hold the control key and click on the application that needs to be locked and simply enter your password on the dialog that pops up and your done. Now anyone can use your pc without you having to look over their shoulder....

You can get an expensive ticket for driving with a busted tail light. But that's not all. Driving with a faulty brake light can be dangerous. Replacing the bulb is a simple task that takes only a few minutes.

Daniel Martin, a magician and escape artist, explains his technique for getting out of thumbcuffs. Disclaimer: We're pretty sure it's not illegal to know HOW to escape from thumbcuffs... but we're 100% sure it's illegal to actually escape when detained by law enforcement (just sayin').

Grafting, also known as "top working," is simple-but-essential technique that enables you to change the variety of fruit a tree bears. In this tutorial, Stephen Hayes of Fruitwise Apples Heritage demonstrates the rind grafting technique, a useful method for grafting over a sound-but-unwanted apple or pear tree.

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

Many have tried to prove (or disprove) that tennis ball lock picking really works, but it still seems up for debate. Mythbusters have supposedly debunked this technique (watch the video). Someone over at the Auto Blog also has tested this car lock method with failed results (watch the video).

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

Everyone seems to be talking about Elon Musk's new futuristic Tesla Cybertruck, the vehicle that either looks like a cool moon rover or an outlandish video game replica, depending on your tastes.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Another day brings another Apple ARKit demo, this time for a first-person role playing game that inserts villagers, vendors, and villains into real world locations.